After completing asset identification, vulnerability identification, and threat identification, we can use appropriate methods and tools to determine the possibility of threats using vulnerabilities to cause security incidents. Comprehensive security incidents affect asset value and severity of vulnerability, and judge the loss caused by the incident and its impact on the organization, that is, security risk. 
one
Risk Calculation Form and Key Links
The normal form of the risk calculation principle is as follows:
Risk value=R(A,T,V)=R(L(T,V),F(Ia,Va));
Where: R identifies a security risk calculation function. A stands for asset; T stands for threat; V stands for vulnerability; Ia stands for asset value; Va stands for severity of vulnerability. L represents the possibility that threats exploit the vulnerability of assets to cause security incidents. F represents the loss after the security incident.
There are three key steps in risk calculation:
Possibility of security incident = L (threat frequency, asset vulnerability) = L (T, V);
Loss after a security incident = F (asset value, vulnerability severity) = F (Ia, Va);
Risk value = R (possibility of security incident, loss after security incident) = R (L (T, V), F (Ia, Va))
At present, risk calculation in the industry uses two-dimensional matrix or multiplication method to calculate risk. This article does not introduce too much calculation method.
two
Risk result judgment
In order to facilitate risk control and management, risks can be divided into multiple levels (eg: 5 or 3), the higher the level, the higher the risk. Example table below: 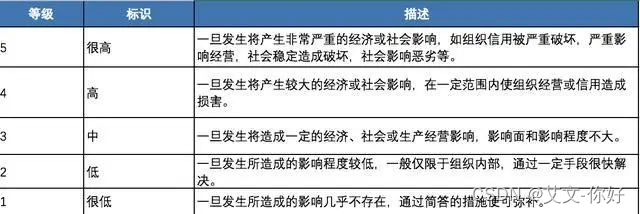
3
Risk treatment
For unacceptable risks, a risk treatment plan should be formulated according to the vulnerability of the risk. The risk treatment plan should clearly define the measures taken to make up for the weaknesses, expected effects, implementation conditions, progress arrangements, responsible departments, coordinating departments, etc. Security measures should be carried out from two dimensions of management and technology, and management can be used as a supplement to technical measures.
The purpose of risk treatment is to reduce vulnerability or reduce the possibility of security incidents.
Four
risk assessment
Risk reassessment should be carried out after the risk disposal is completed to determine whether the residual risk after the implementation of security measures has been reduced to an acceptable level.
The general risk assessment methods are divided into two categories: self-assessment and inspection assessment.
Self-assessment: initiated by the organization, with the purpose of discovering the existing weaknesses of the system and implementing security management. It is suitable for self-identification and evaluation of security risks, and selection of appropriate risk disposal measures to reduce the security risks of assessed assets. Periodic assessments can be included in data security management specifications and management methods. Since the self-assessment is limited by the internal personnel of the organization, it may lack the professional skills of assessment, resulting in a lack of depth and accuracy, and a certain lack of objectivity. Therefore, risk assessment service technical support units are usually entrusted to carry out the assessment.
Inspection and evaluation: Initiated by the higher-level competent authority or business organization of the evaluated organization, it is an important measure to strengthen safety through administrative means, usually a regular and sampling evaluation mode, aimed at checking whether the safety risks of key areas or key points are within the acceptable range . Inspection and evaluation mainly include:
Examination of self-assessment methods;
Self-assessment process record check;
Follow-up inspection of self-assessment results;
Existing data security checks;
Data control checks during the data life cycle;
Inspection of emergency response measures;
Data integrity, availability, confidentiality checks;
Data audit and desensitization inspection in the data life cycle;
five
Summarize
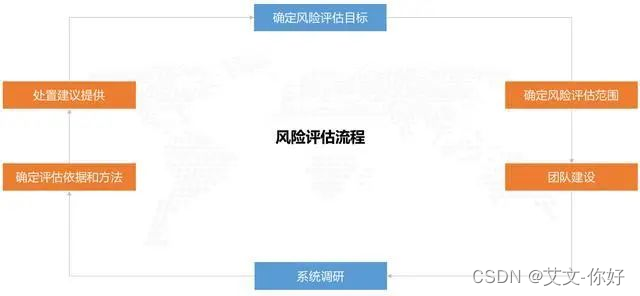
Data security risk assessment and risk assessment of information system should be the relationship between son and parent. Data security risk assessment can be integrated into it or can be operated independently from the existing risk assessment system. The preparatory work before the implementation of the risk assessment is consistent with the risk assessment of the information system, which can be carried out from 6 aspects and form a closed loop.