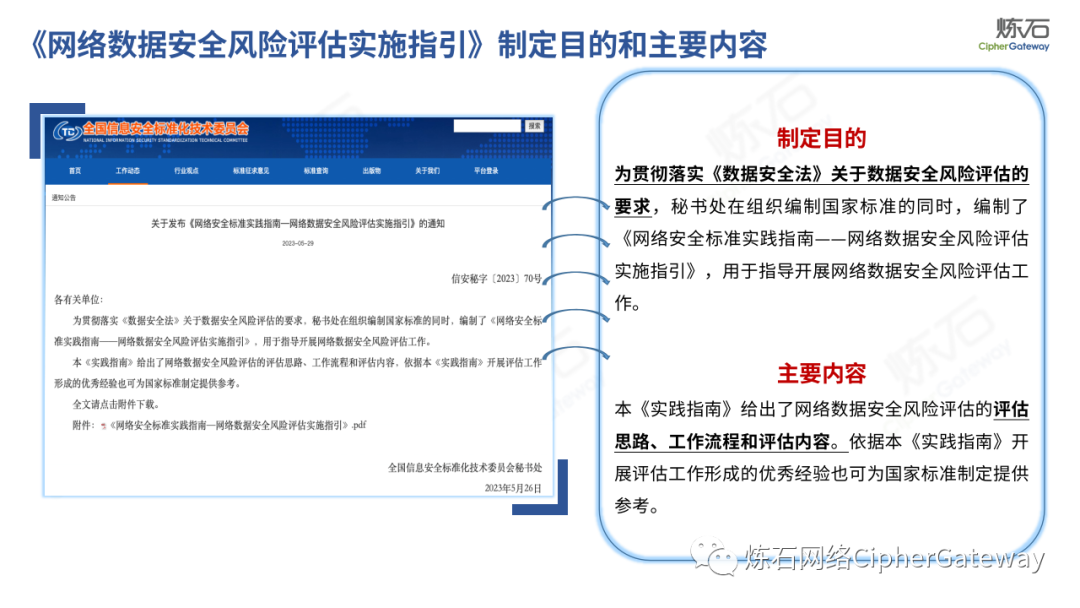
In order to guide the network data security risk assessment work, discover hidden dangers in data security, and prevent data security risks, in accordance with laws and regulations such as the "Network Security Law of the People's Republic of China", "Data Security Law of the People's Republic of China", and "Personal Information Protection Law of the People's Republic of China", refer to National standards related to data security. While organizing the compilation of national standards, the National Information Security Standardization Technical Committee compiled the "Guidelines for the Practice of Network Security Standards-Implementation Guidelines for Network Data Security Risk Assessment" (Xin An Mi Zi [2023] No. 70, hereinafter referred to as "Practice Guidelines"), which are used to guide the development of network data security risk assessment, will be officially released on May 29, 2023.
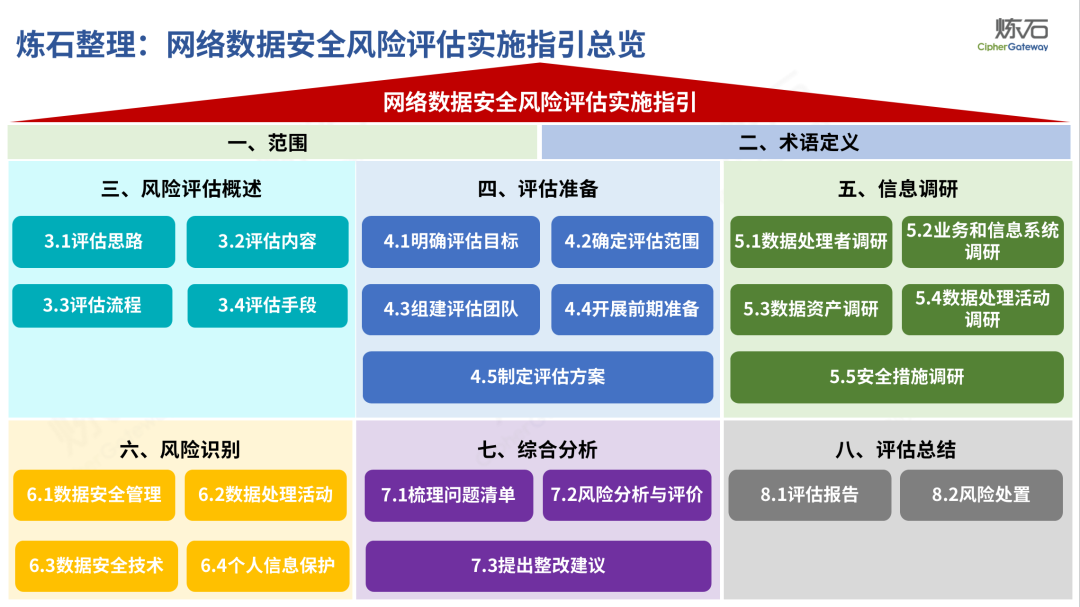
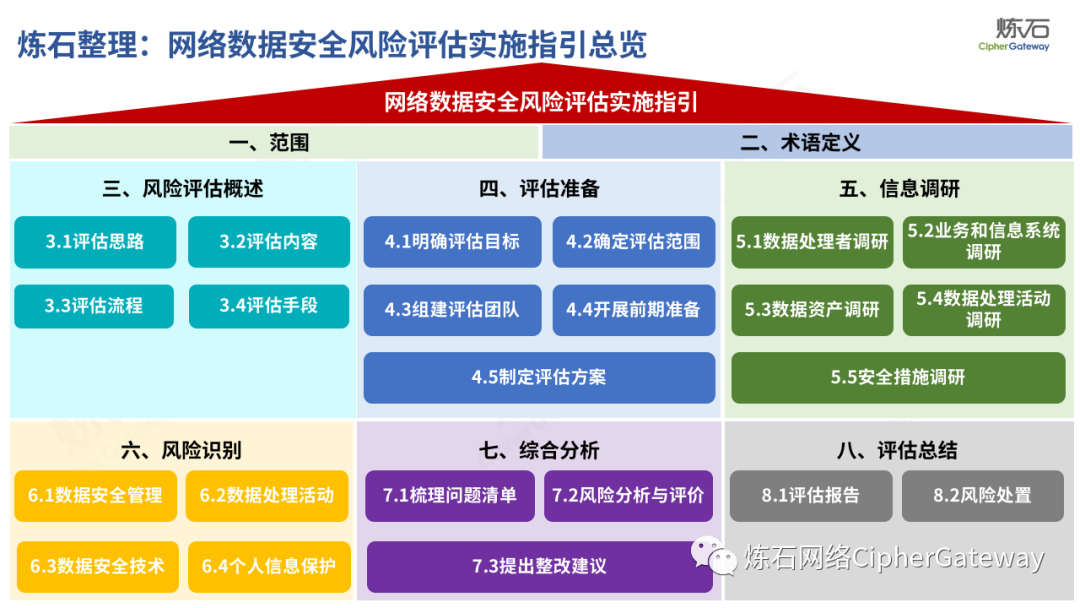
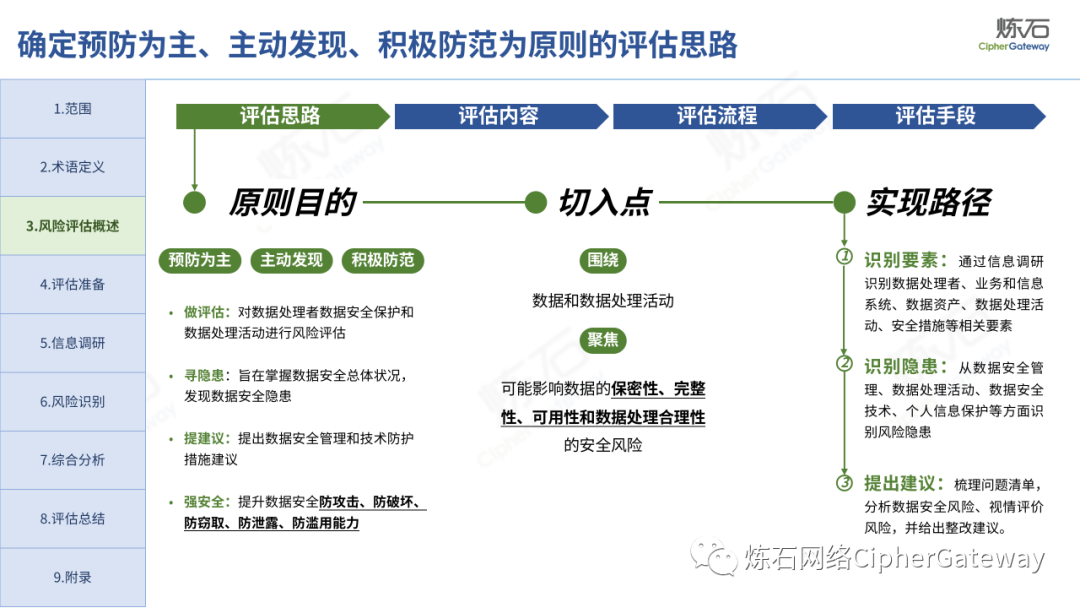
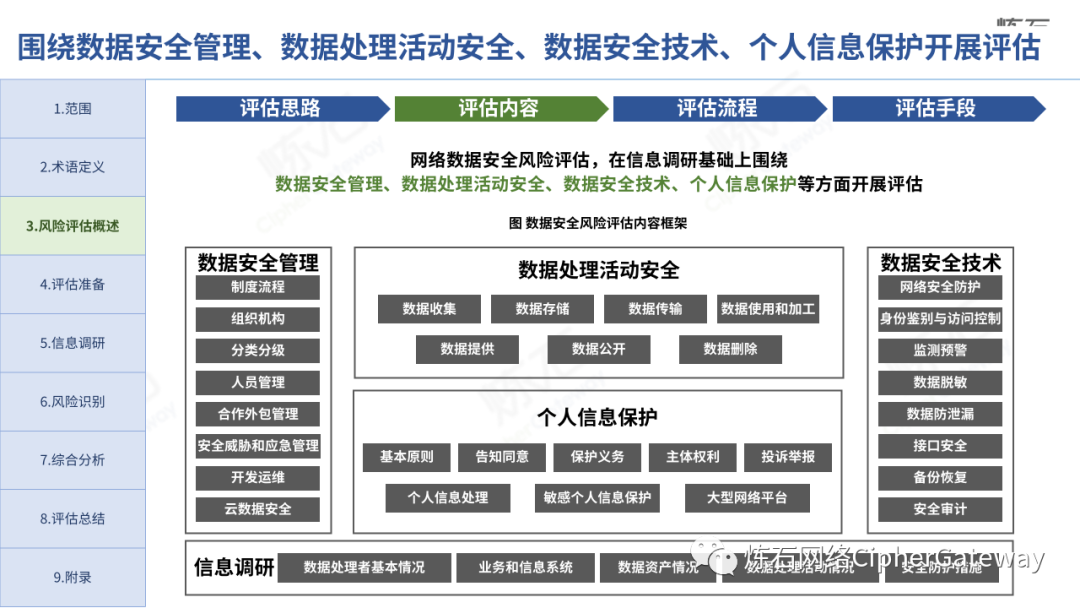
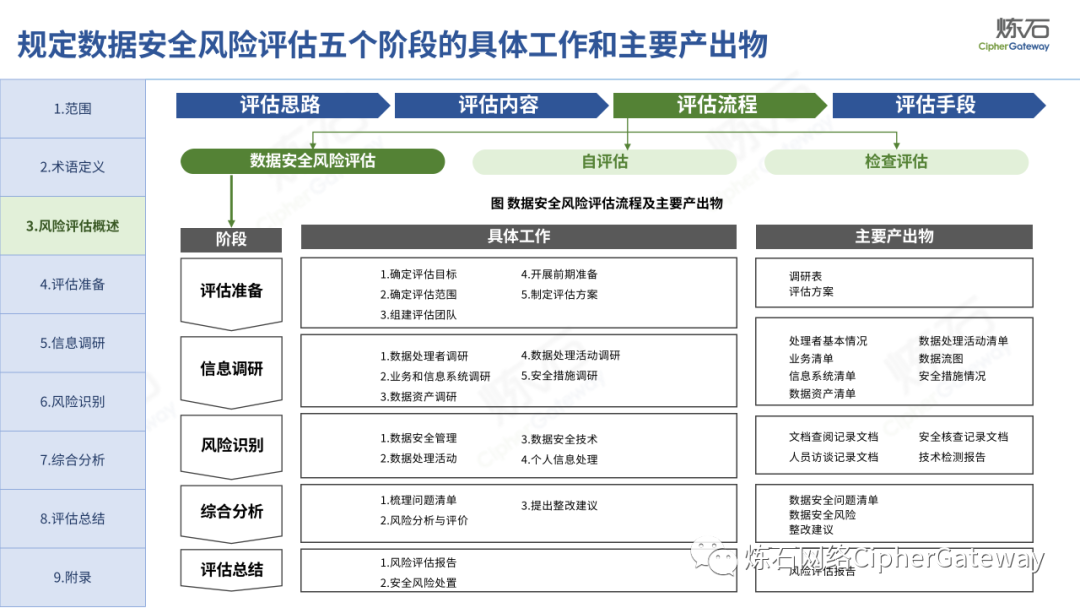
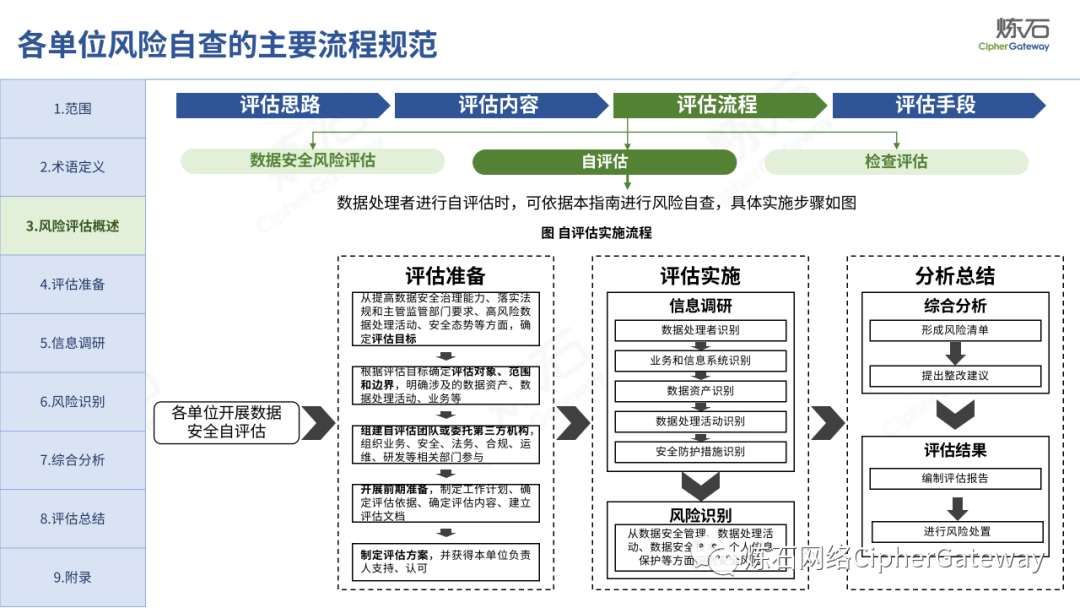
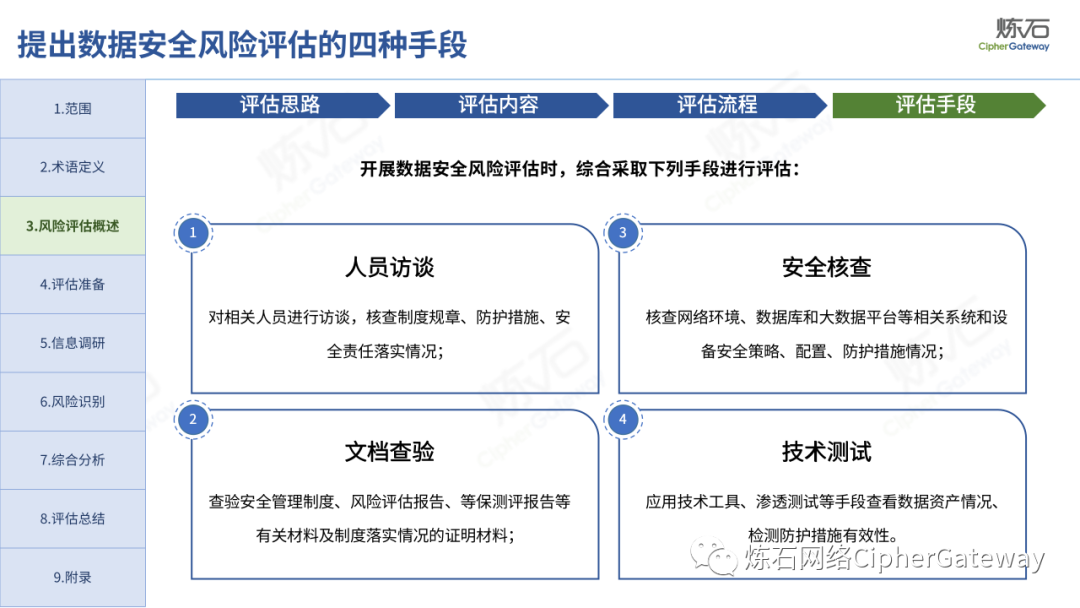
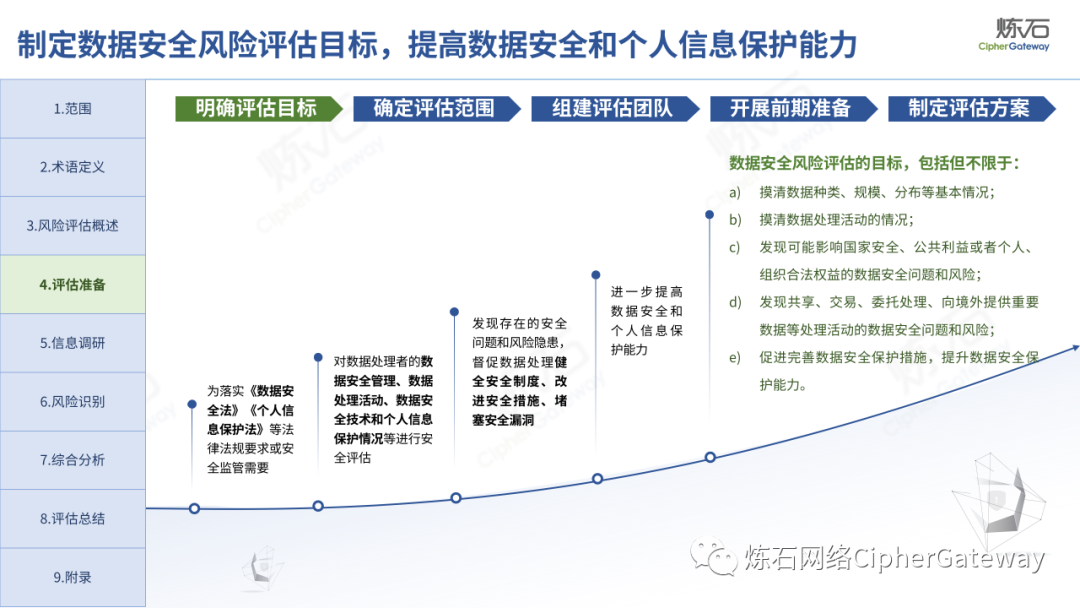
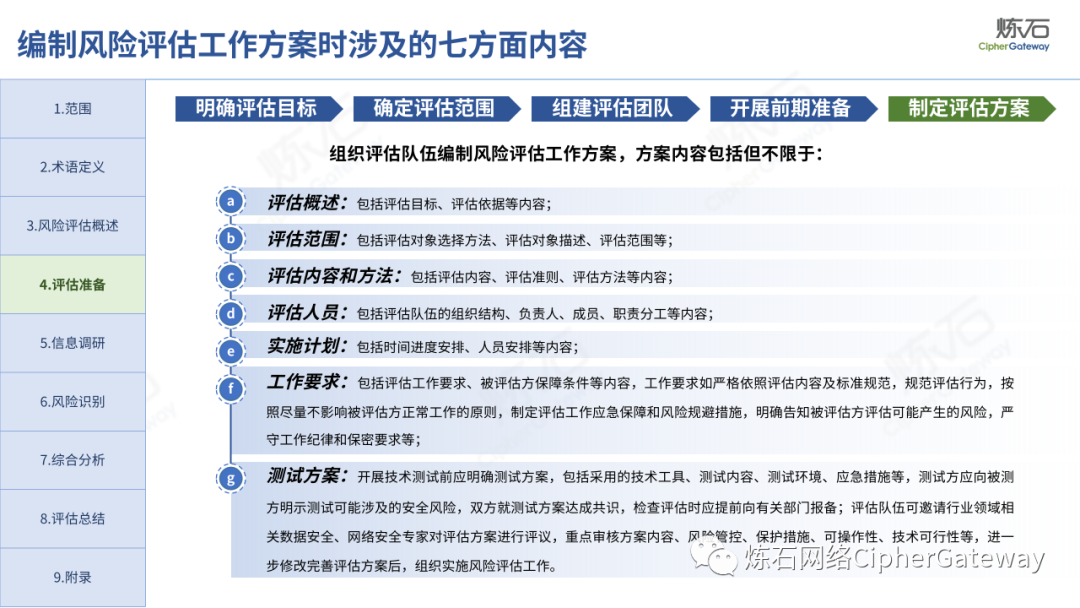
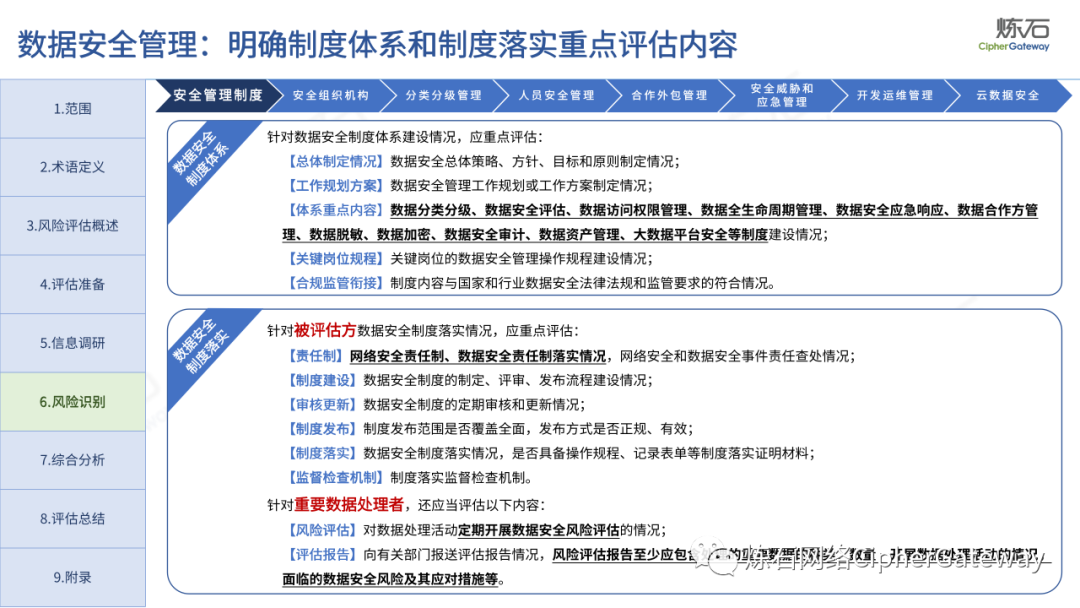
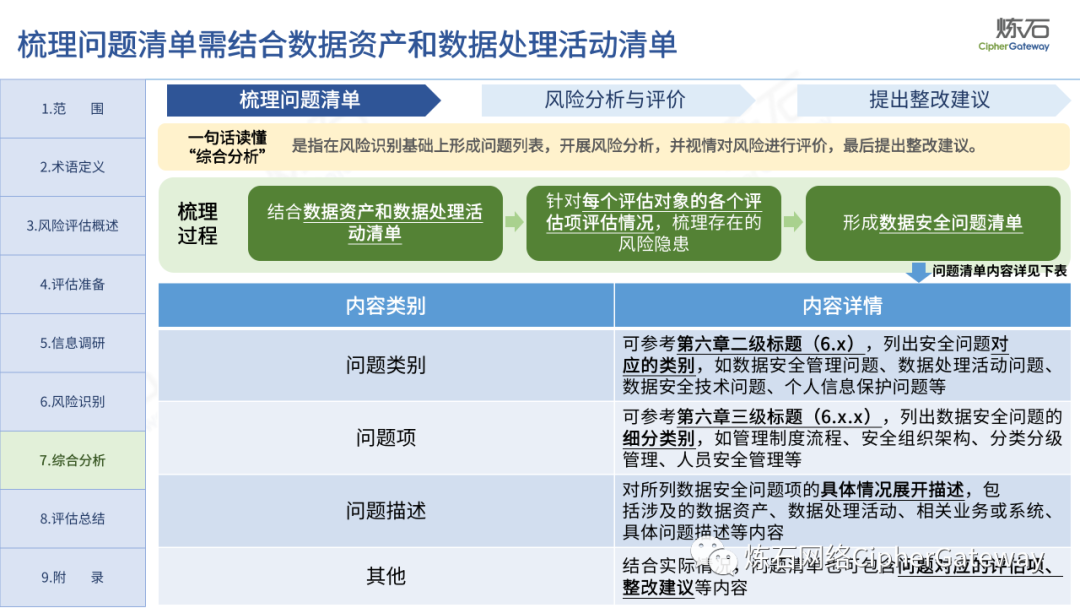
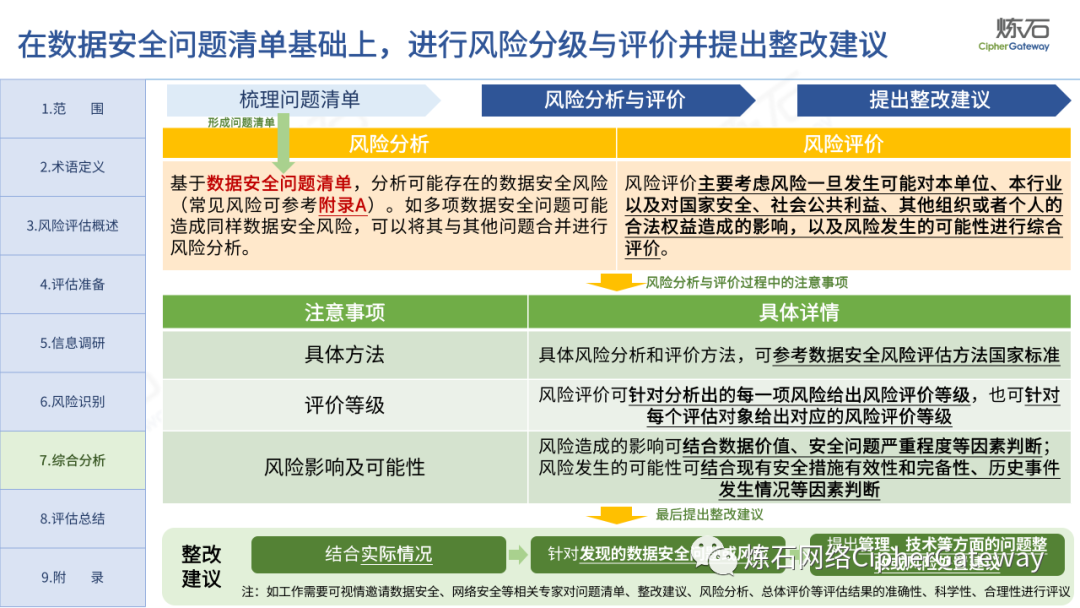
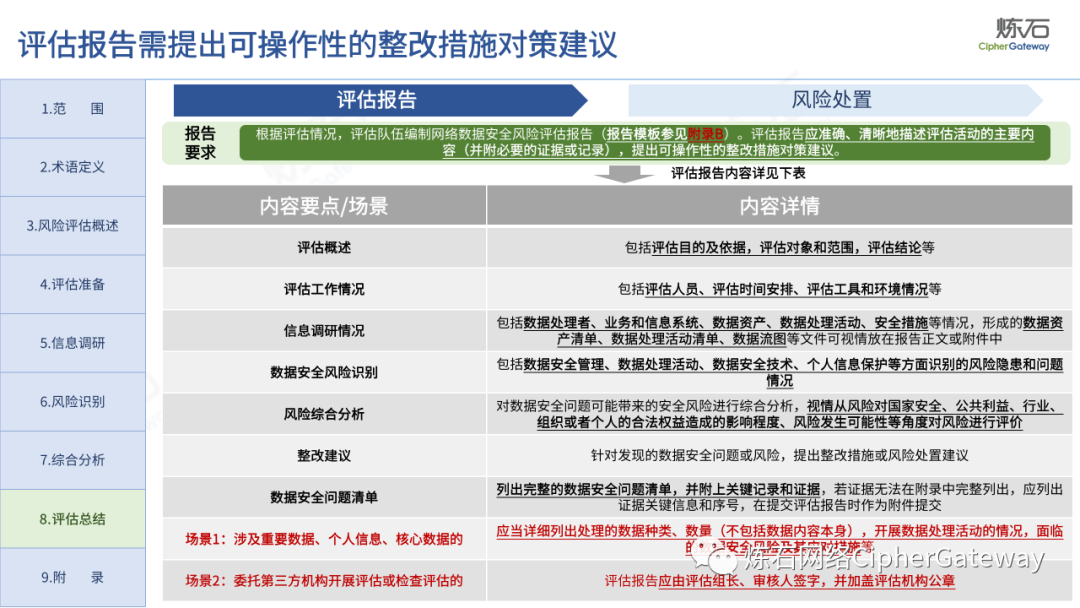
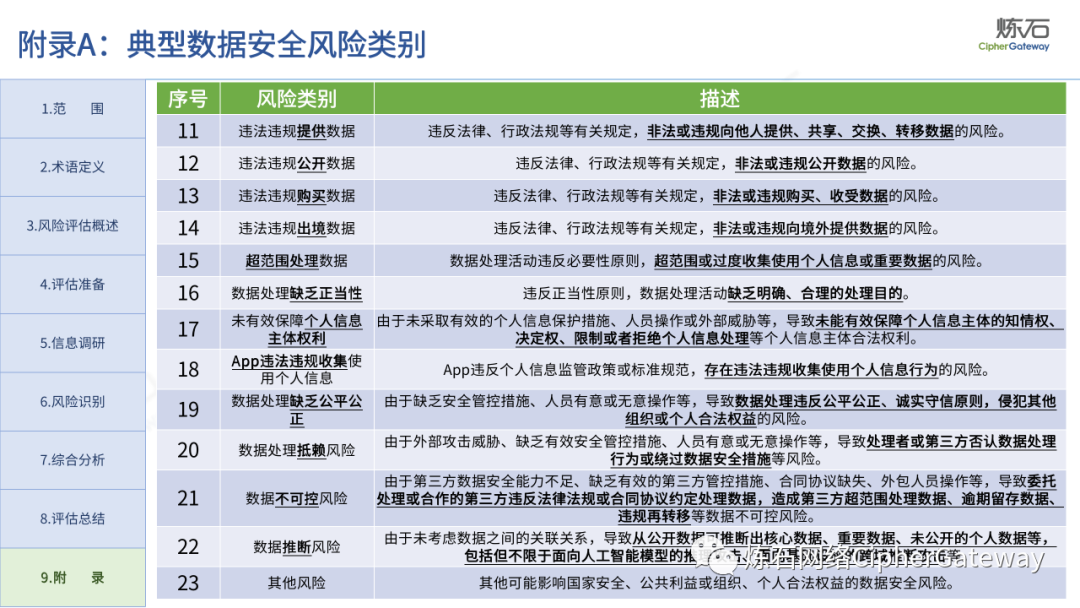
The "Practice Guidelines" adhere to prevention first, active discovery, and active prevention, focusing on security risks that may affect the confidentiality, integrity, availability, and rationality of data processing, and conduct risk assessments on data security protection and data processing activities of data processors , which gives the network data security risk assessment ideas, workflow and assessment content, which can be used to guide data processors and third-party organizations to carry out data security assessments, and can also provide reference for relevant competent regulatory authorities to organize inspections and assessments . Specifically, first identify data processors, business and information systems, data assets, data processing activities, security measures and other relevant elements through information research, and then identify data security management, data processing activities, data security technology, personal information protection, etc. Hidden risks, and finally sort out the list of problems, analyze data security risks, evaluate risks as appropriate, and give rectification suggestions.
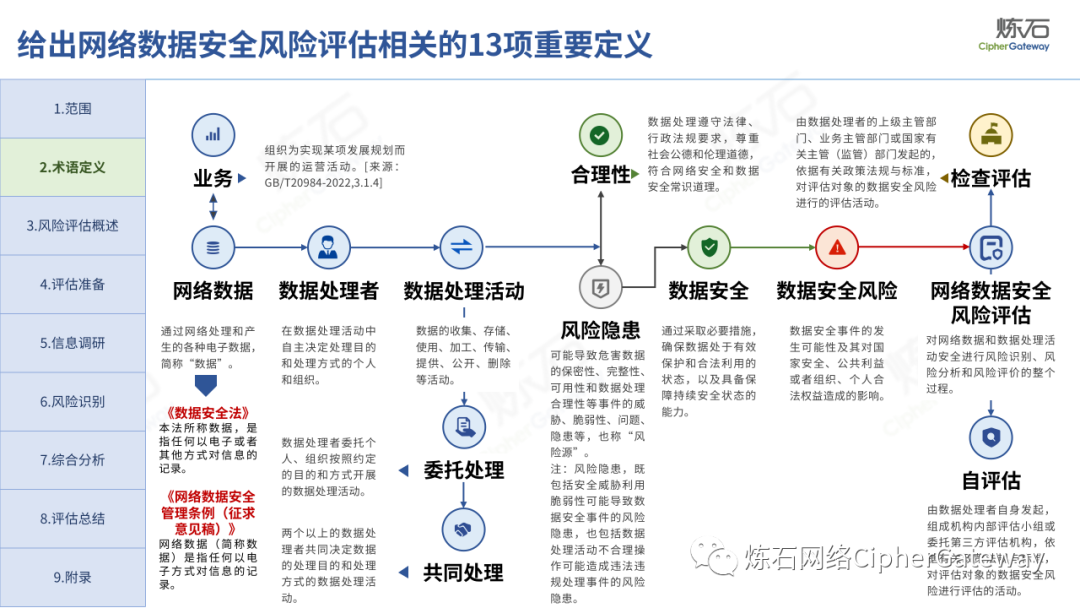
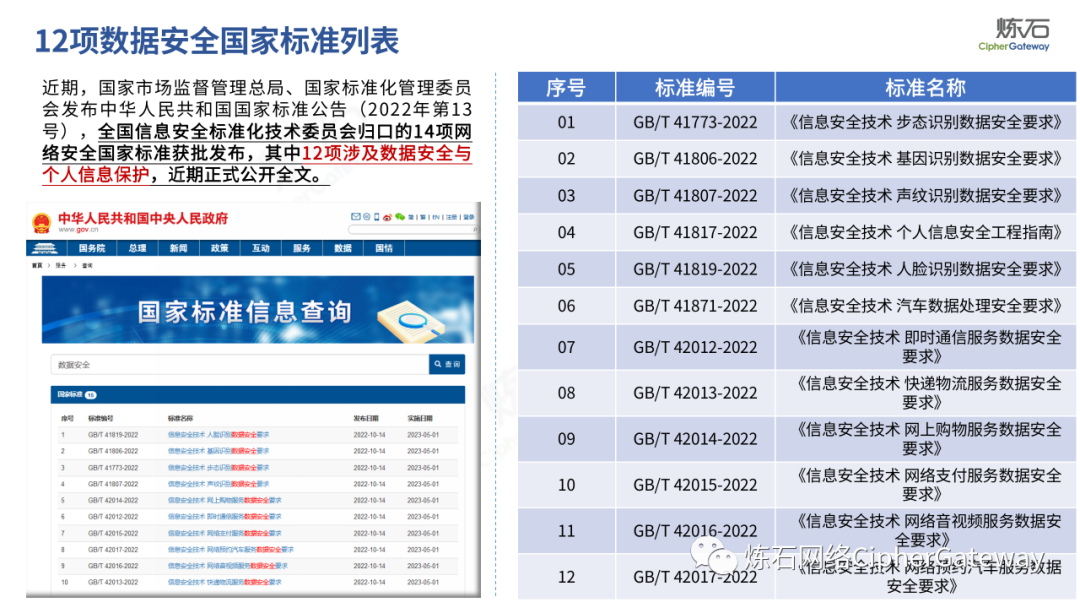
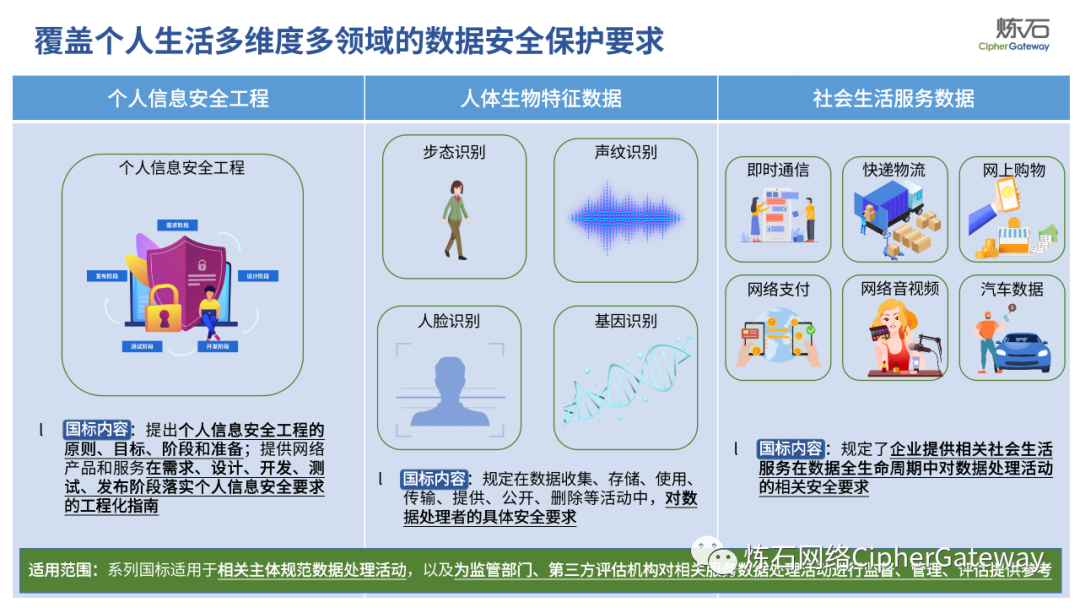
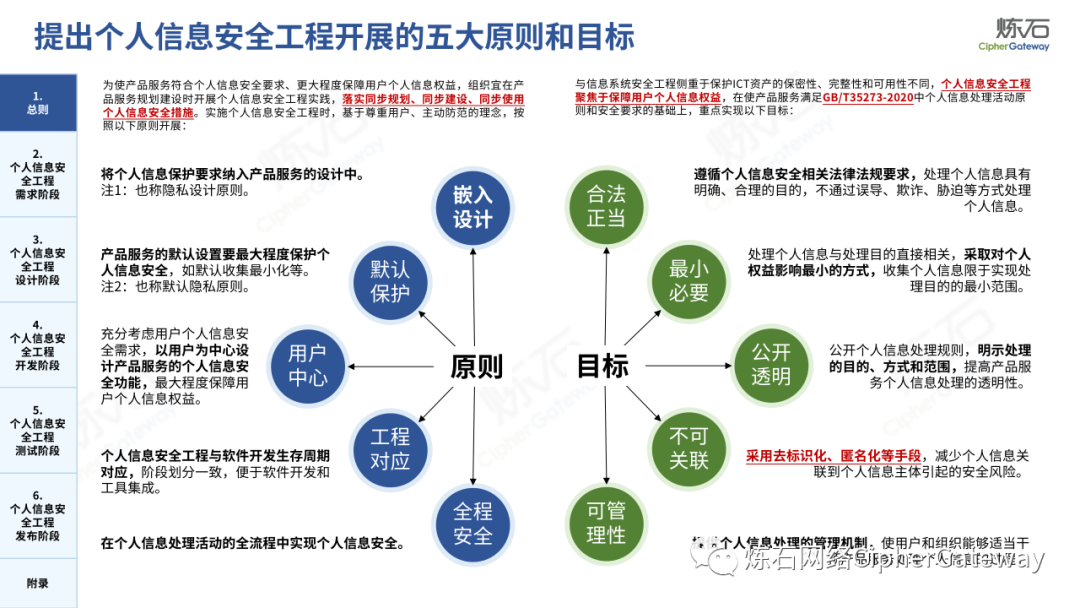
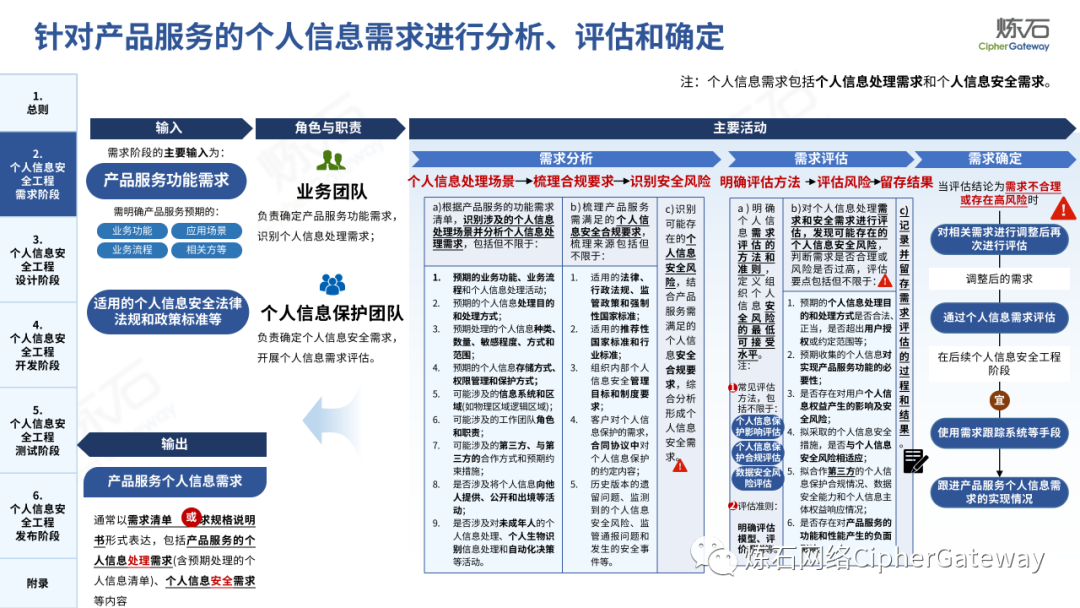
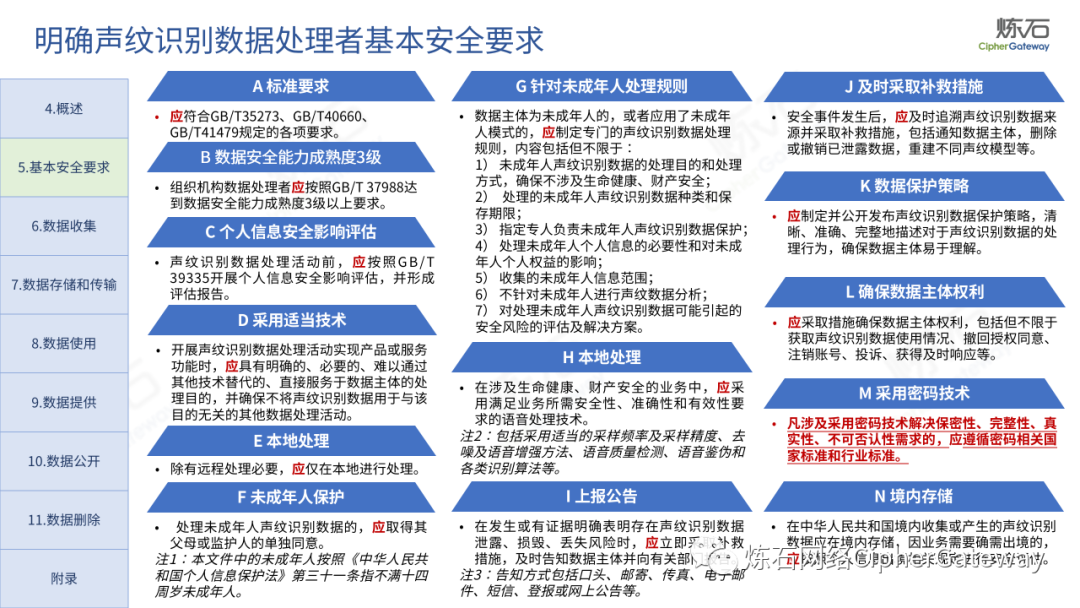
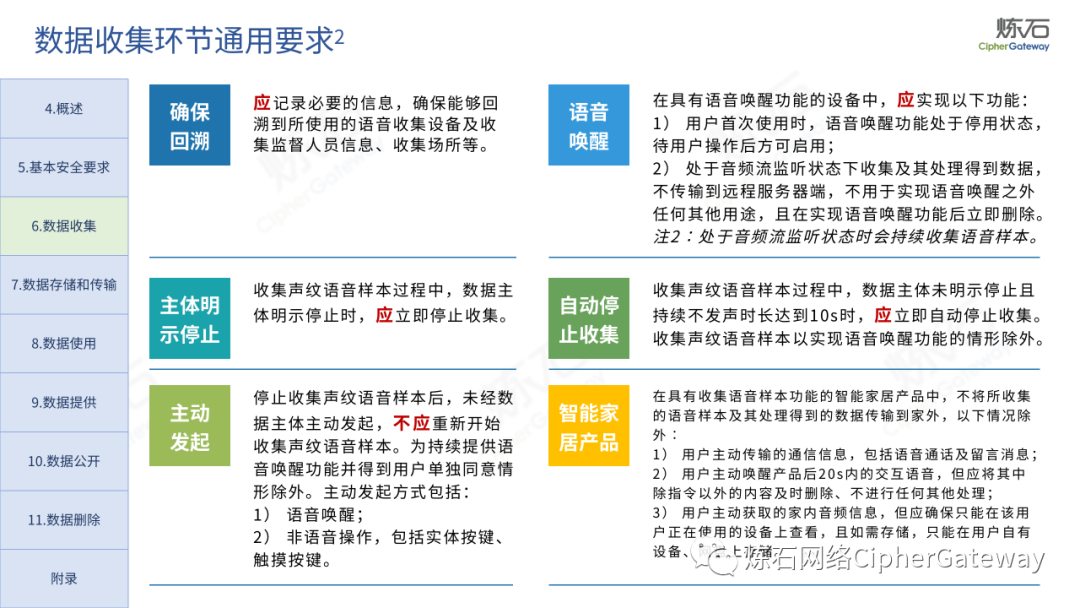
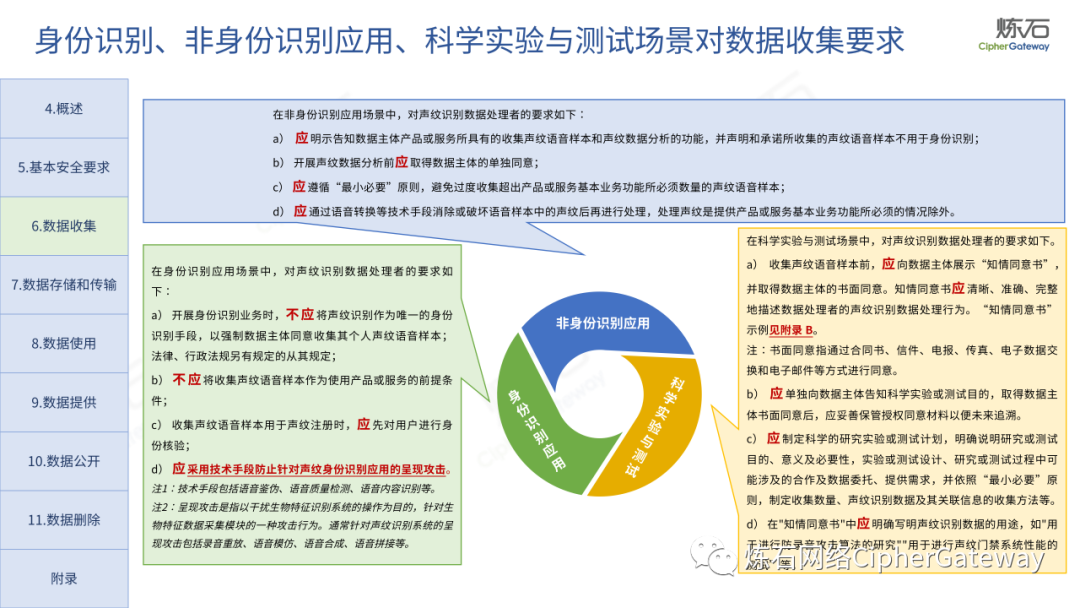
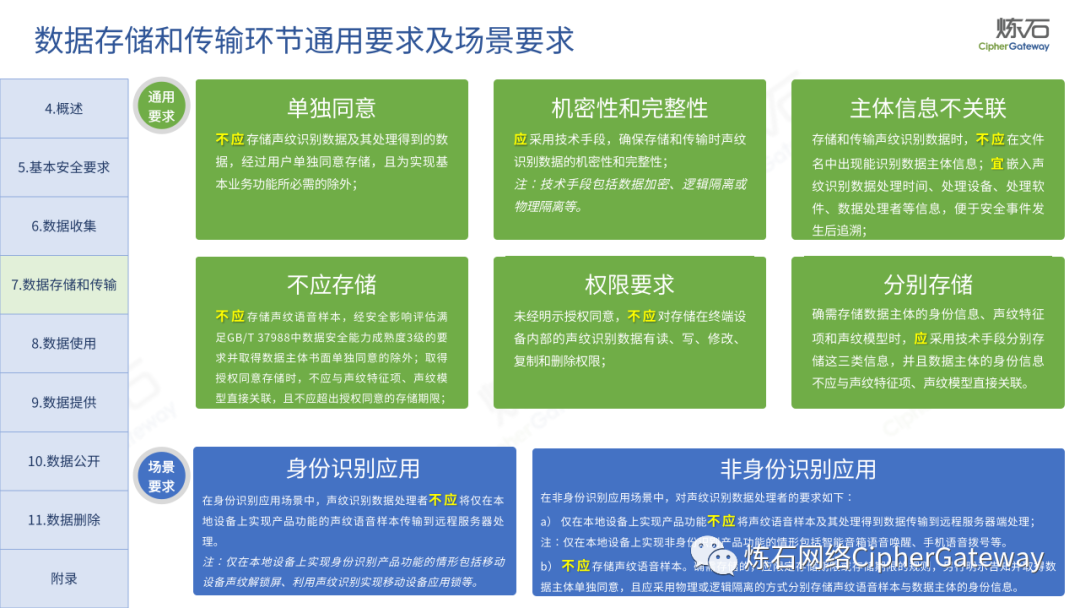
Lianshi interprets the 8 major parts of the "Practice Guidelines", including the scope, term definitions, risk assessment overview, assessment preparation, information research, risk identification, comprehensive analysis, assessment summary, etc. Provide a scientific basis for decision-making, formulate key coping strategies, reflect the importance and premise of "risk assessment", and ensure a safe and stable promotion of the sustainable development of the digital economy. Furthermore, in order to help data processors clarify safety risk protection requirements and operating rules, Lianshi combines gait recognition, gene recognition, voiceprint recognition, face recognition, smart cars, real-time Comprehensive interpretation of national standards for scenarios such as communications, express logistics, online shopping, online payment, online audio and video, online car reservation, personal information security engineering, etc. Due to the limited level of the author, colleagues in the industry are welcome to discuss and improve it together.
Follow this account, send a private message to the editor , and you can package and download the PDF version of the high-definition file and the original text of the " Full Version Illustration "Network Security Standard Practice Guide-Network Data Security Risk Assessment Implementation Guidelines"".
In order to jointly promote the development of the data security industry, colleagues in the industry are welcome to join the "[Alchemy] Data Security Technology Circle" WeChat group to discuss the latest trends and best practices in data security protection.

Statement of originality: The illustrations and pictures in this article are all original, and the copyright is owned by Lianshi Network. If you need to reprint, please follow the official account and reply "reprint", or leave a message at the bottom of the article.
Note: Colleagues in the industry are welcome to give feedback for improvement, joint improvement, exchange and cooperation. For information feedback, please send an email to: [email protected].



















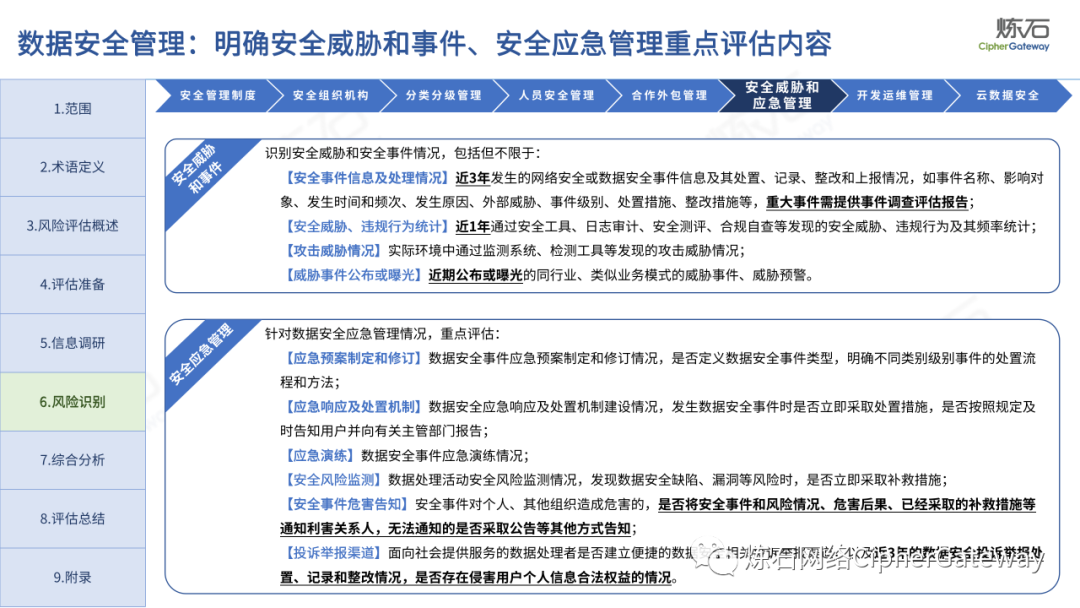
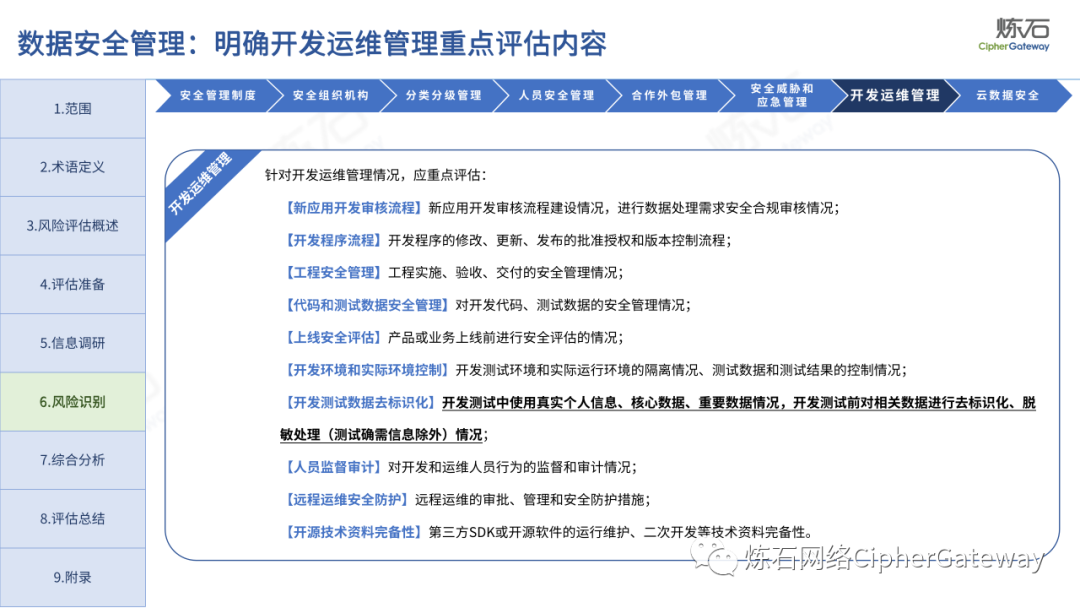


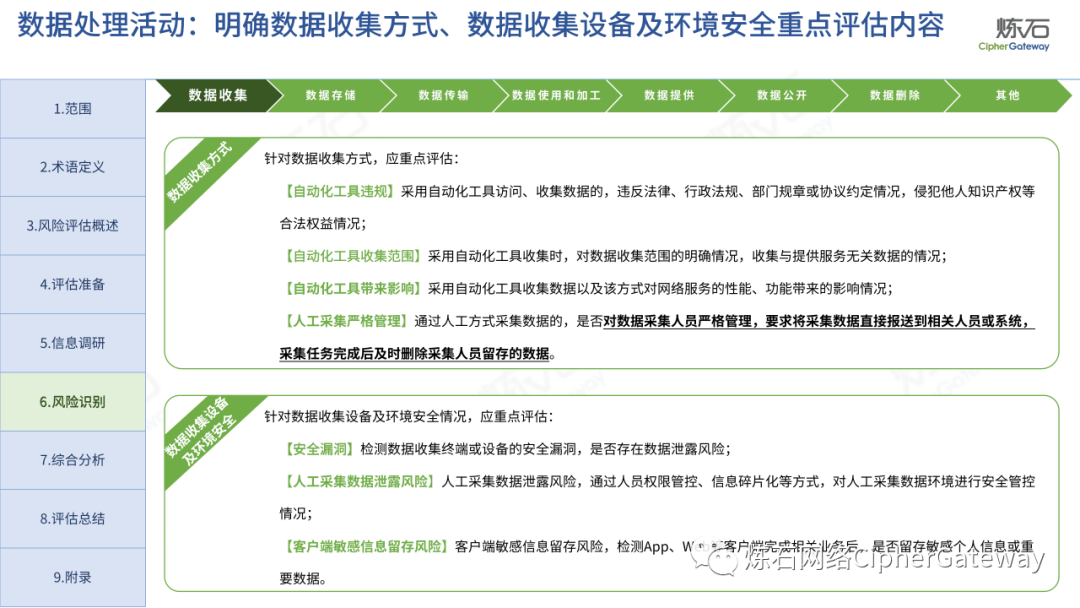





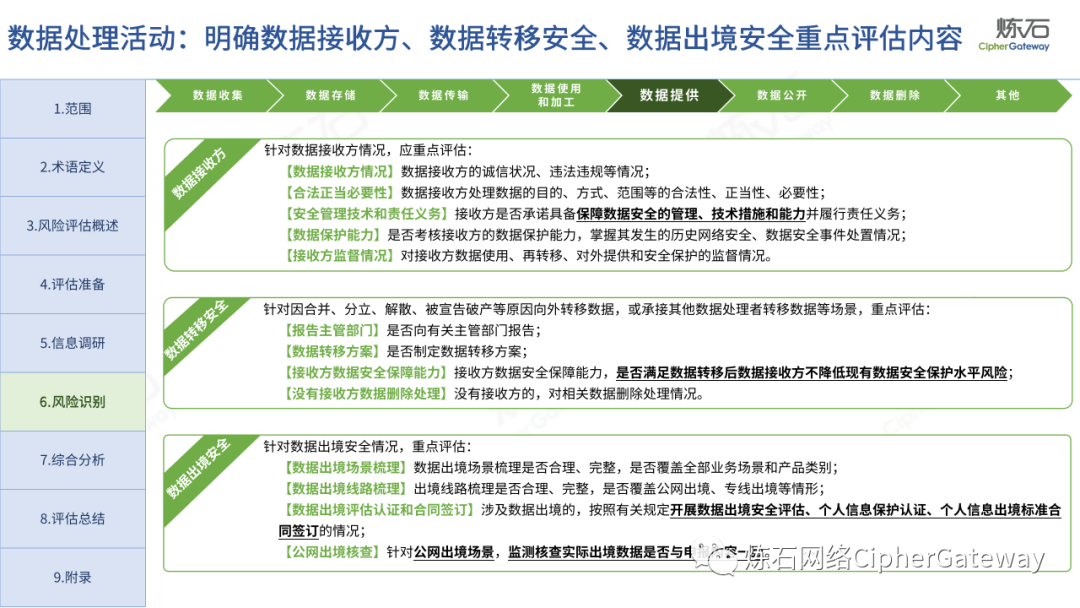

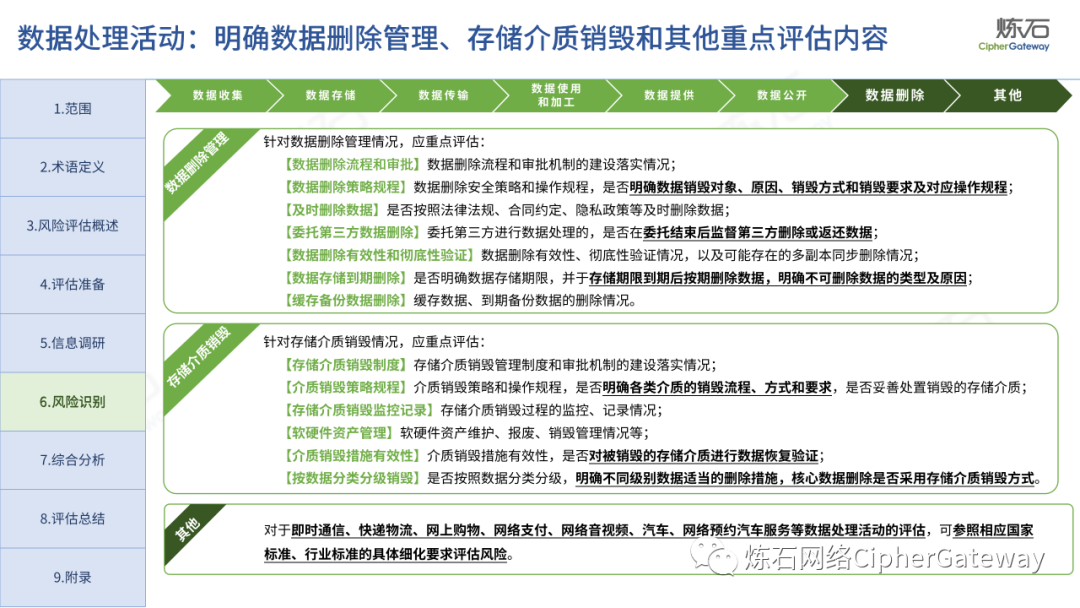
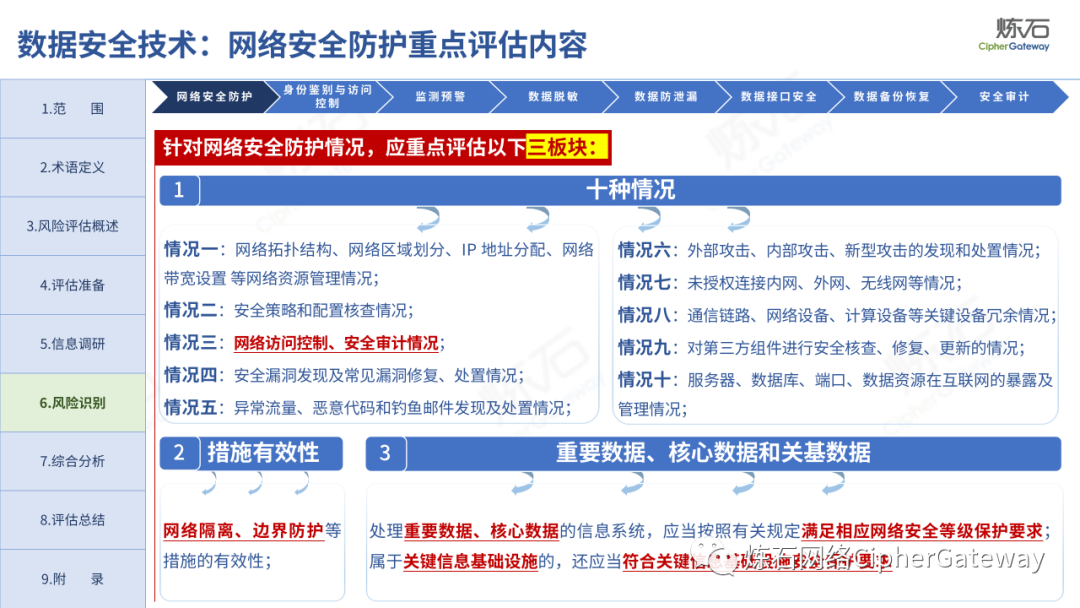

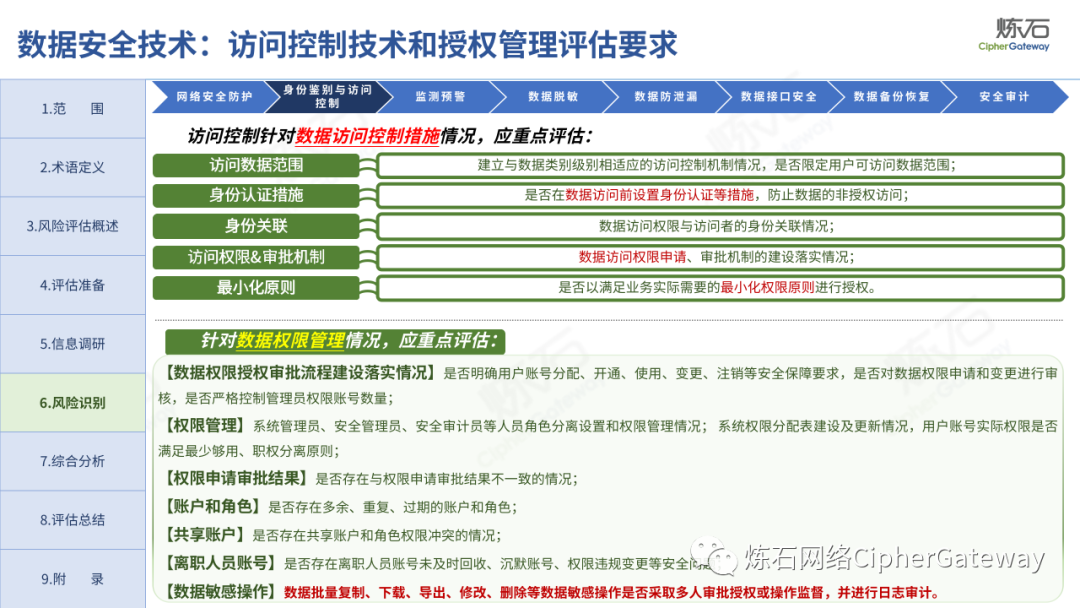
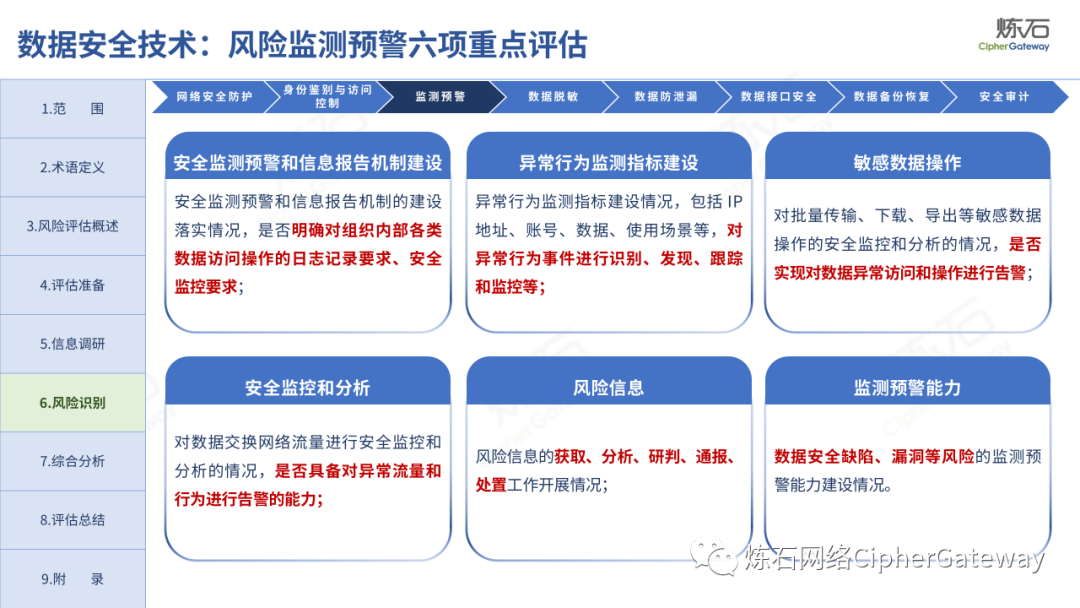
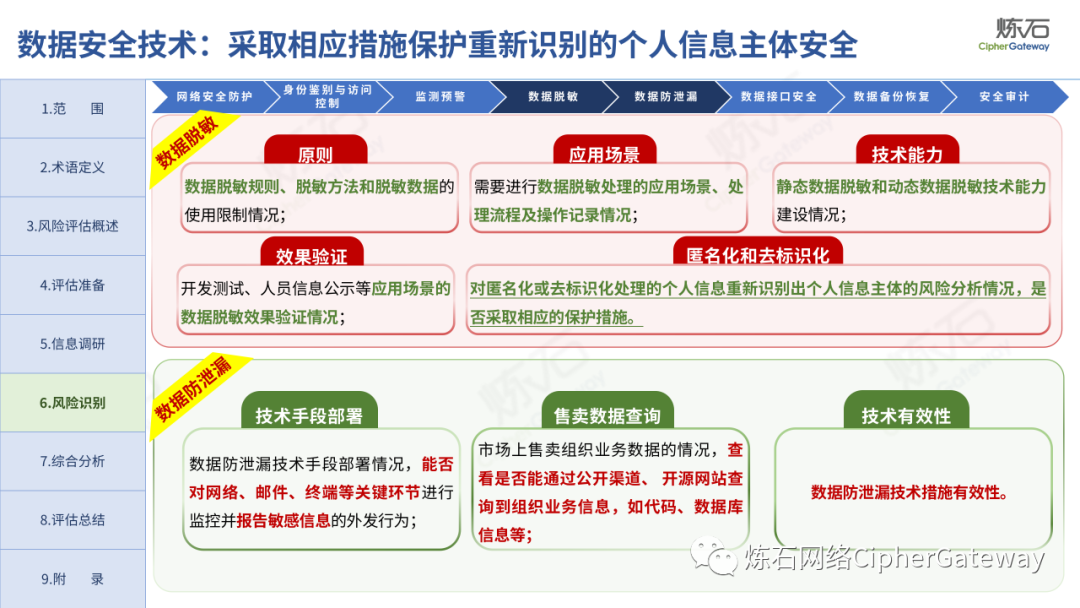




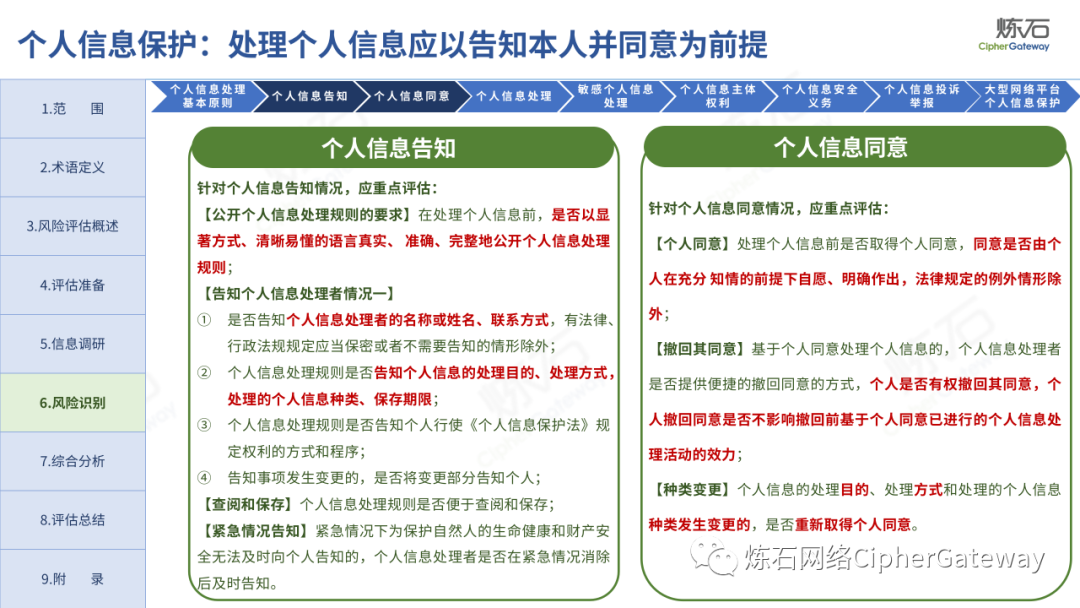


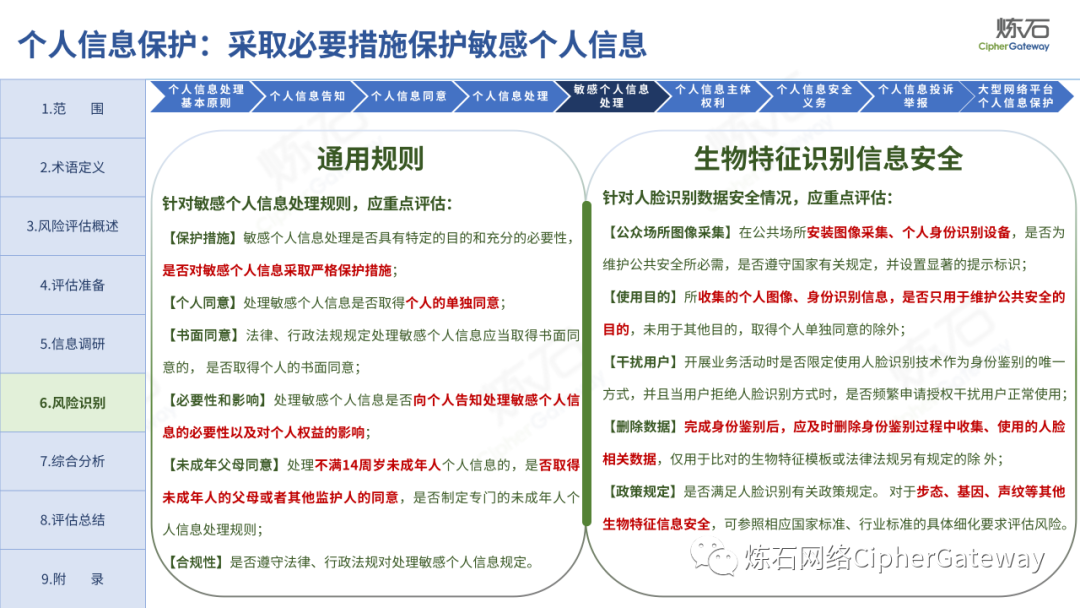
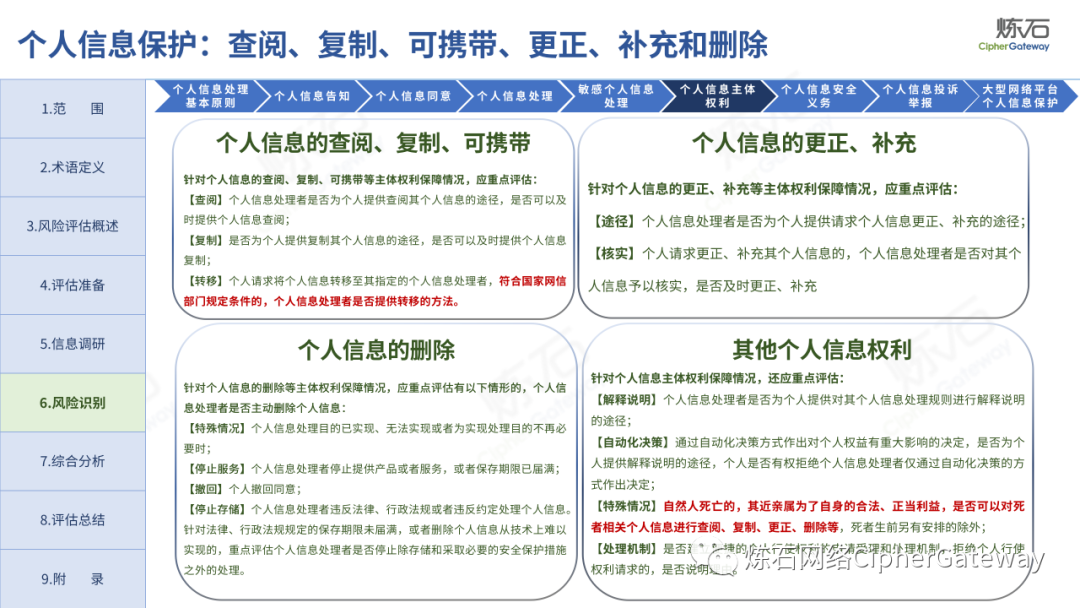













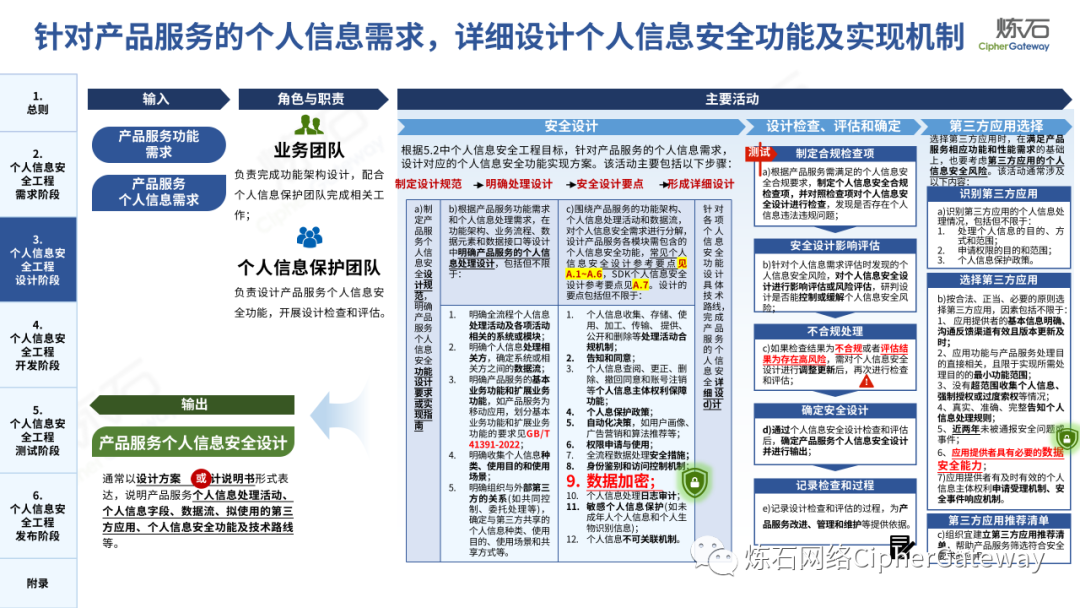
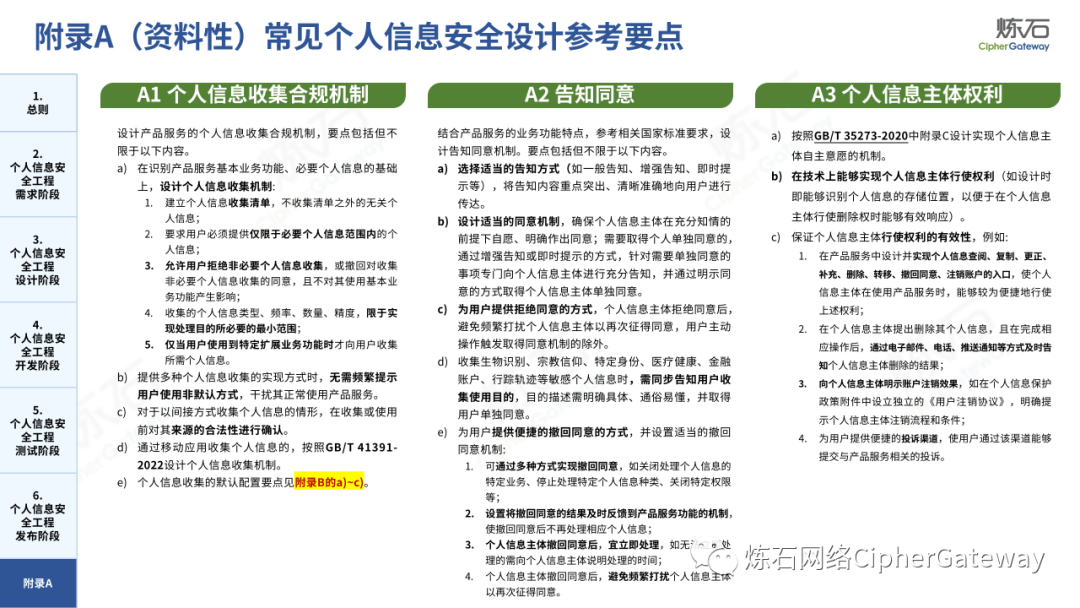


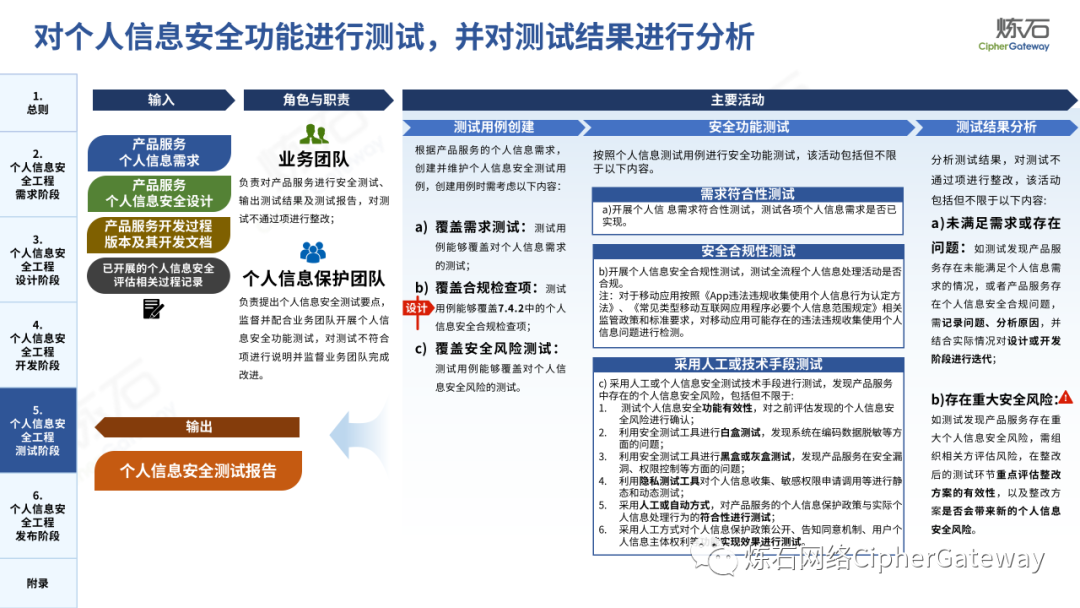




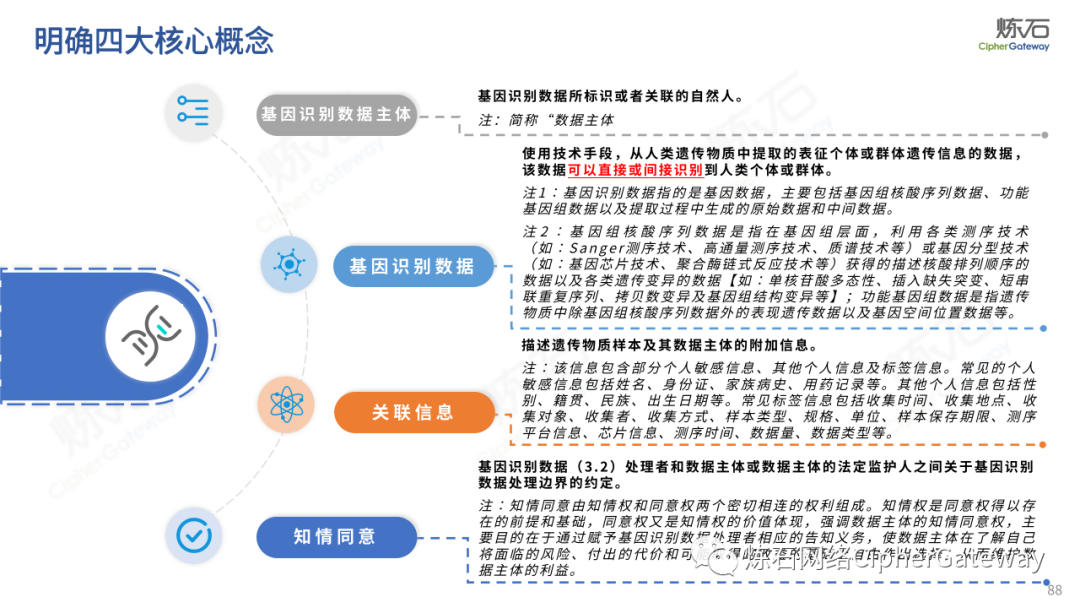
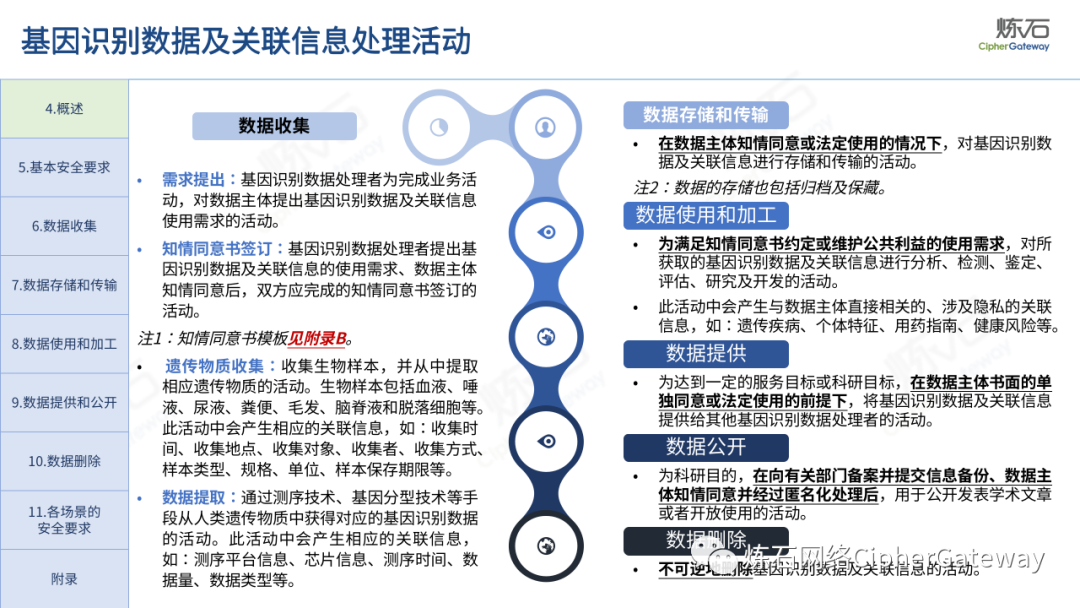

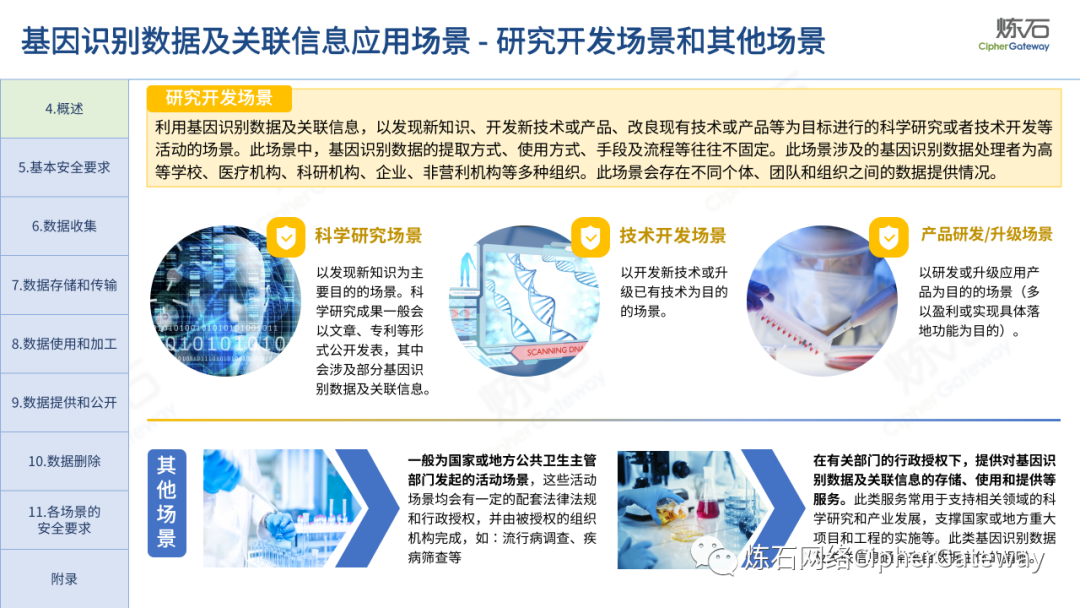


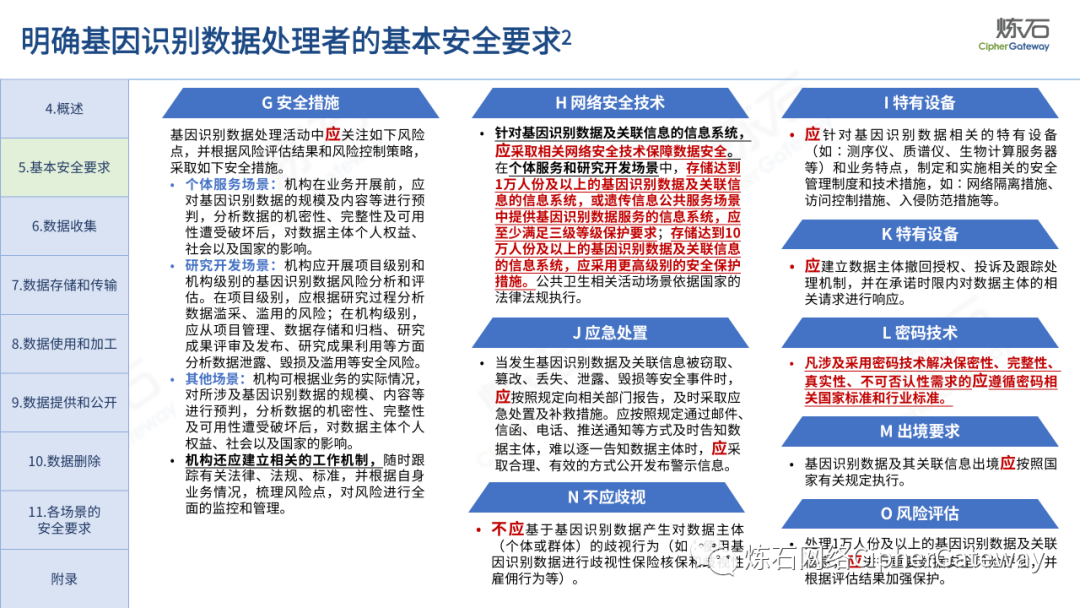
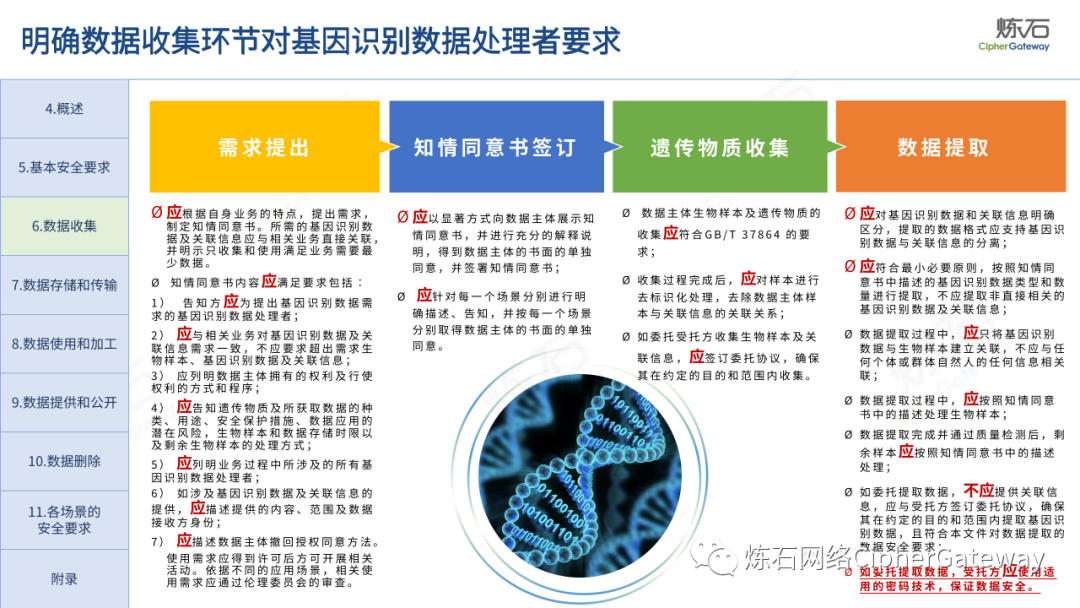



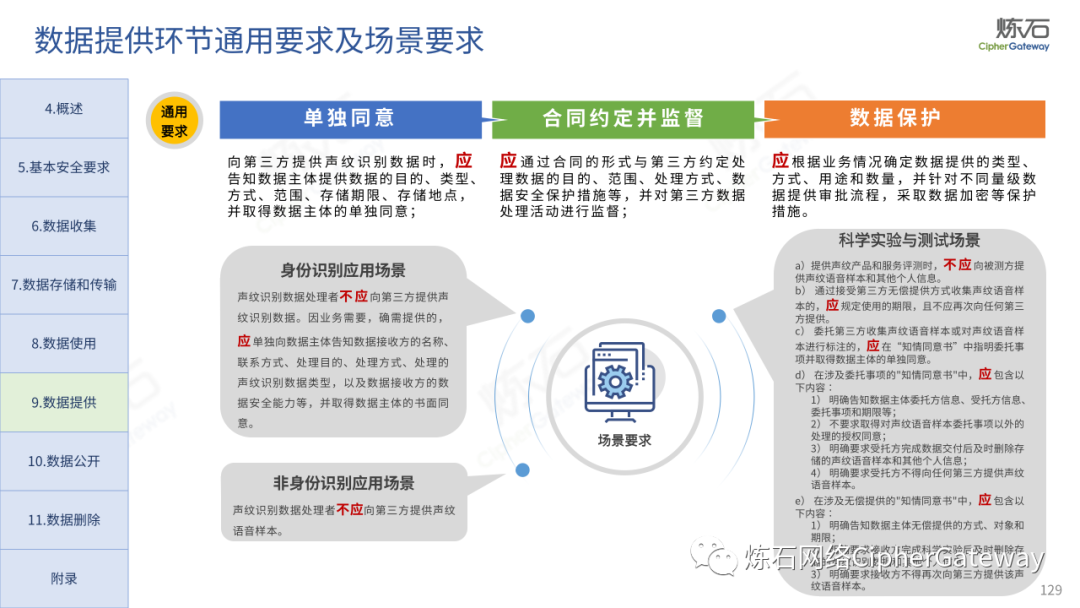

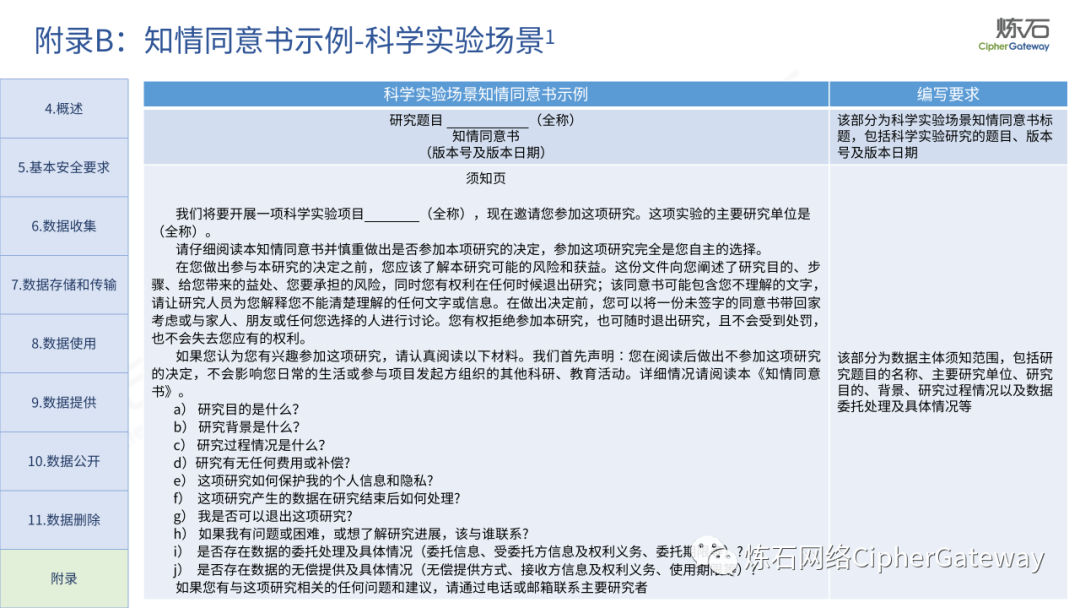

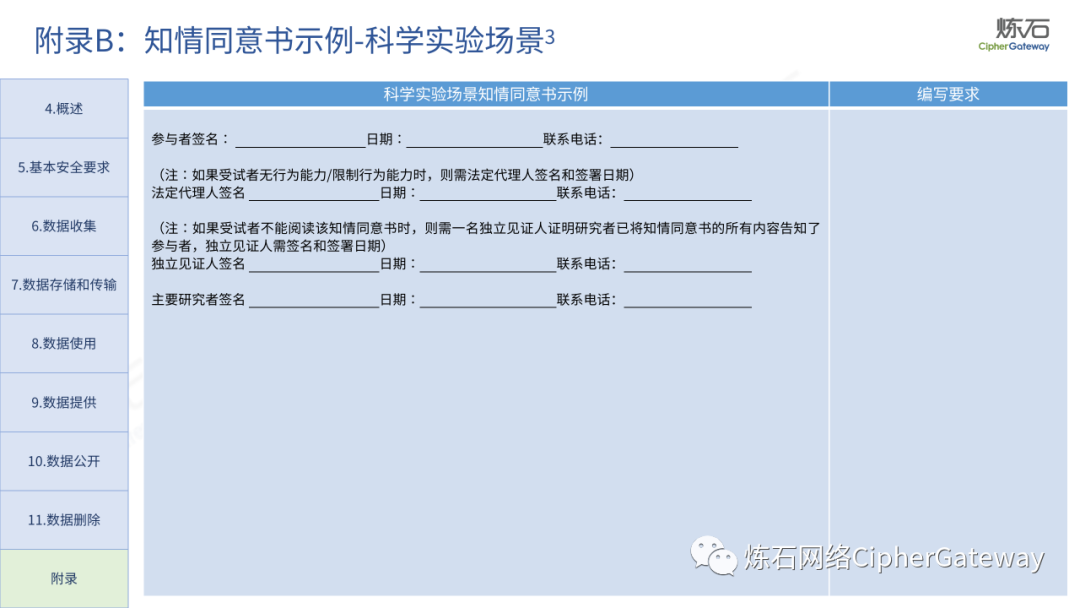
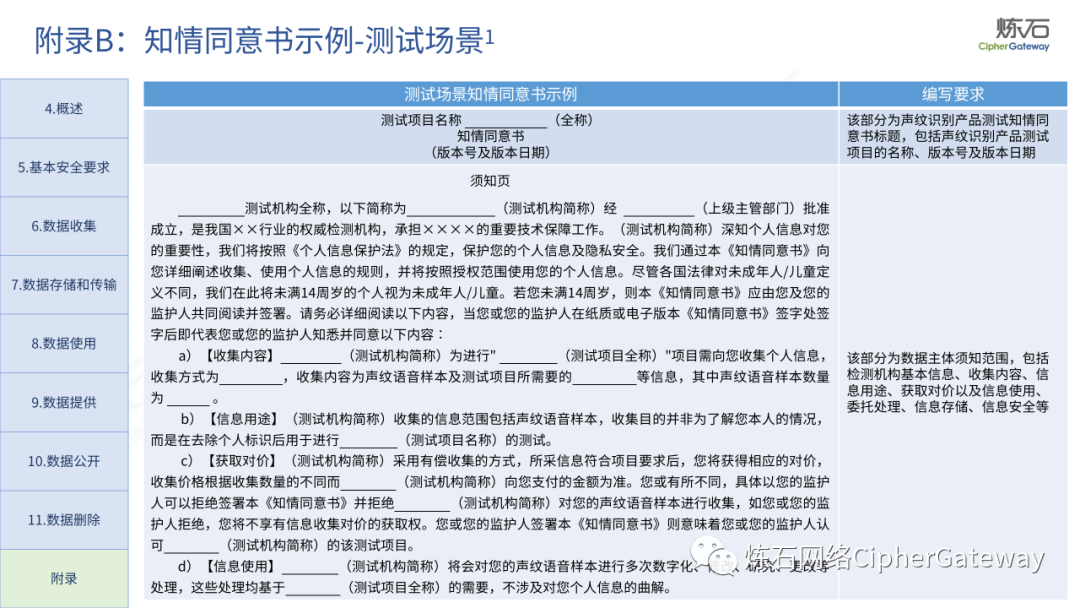

Follow this account, send a private message to the editor , and you can package and download the PDF version of the high-definition file and the original text of the " Full Version Illustration "Network Security Standard Practice Guide-Network Data Security Risk Assessment Implementation Guidelines"".
In order to jointly promote the development of the data security industry, colleagues in the industry are welcome to join the "[Alchemy] Data Security Technology Circle" WeChat group to discuss the latest trends and best practices in data security protection.

Statement of originality: The illustrations and pictures in this article are all original, and the copyright is owned by Lianshi Network. If you need to reprint, please follow the official account and reply "reprint", or leave a message at the bottom of the article.
Note: Colleagues in the industry are welcome to give feedback for improvement, joint improvement, exchange and cooperation. For information feedback, please send an email to: [email protected].