Microsoft Research Center Srinath Setty, a16z crypto research and Georgetown University Justin Thaler, Carnegie Mellon University Riad Wahby 20203 paper " Customizable constraint systems for succinct arguments ".
Preface blogs are:
4. SuperSpartan的Polynomial IOP for CCS
The "SuperSpartan's Polynomial IOP for CCS" discussed in this section is an extension of "Spartan [Set20] polynomial IOP for R1CS". Appendix C shows how to extend SuperSpartan's polynomial IOP to handle CCS+ (that is, CCS with lookup operations).
根据Definition 2.2,假定有某CCS structure-instance tuple with size bounds:
( ( m , n , l , t , q , d ) , ( M 0 , ⋯ , M t − 1 , S 0 , ⋯ , S q − 1 , x ) ) ((m,n,l,t,q,d),(M_0,\cdots,M_{t-1},S_0,\cdots,S_{q-1},x)) ((m,n,l,t,q,d),(M0,⋯,Mt−1,S0,⋯,Sq−1,x))
For simplicity, let m , nm,n in the protocolm,n are all powers of 2 (if not, for each matrixM i M_iMiand witness vector zzZ is zero-padding, extendingm , nm,nm,n is all powers of 2, in the following SNARK protocol, it will not increase the Prover time or Verifier time in SNARK).
The matrix M 0 , ⋯ , M t − 1 M_0,\cdots, M_{t-1}M0,⋯,Mt−1Parsed as a function: { 0 , 1 } log m × { 0 , 1 } log n → F \{0,1\}^{\log m}\times \{0,1\}^{\log n }\rightarrow \mathbb{F}{ 0,1}logm×{ 0,1}logn→F. _ Any{ 0 , 1 } log m × { 0 , 1 } log n \{0,1\}^{\log m}\times \{0,1\}^{\log n}{ 0,1}logm×{ 0,1}logThe input of n format can be parsed as index( i , j ) ∈ { 0 , 1 , ⋯ , m − 1 } × { 0 , 1 , ⋯ , n − 1 } (i, j)\in\{0, 1,\cdots,m-1\}\times\{0,1,\cdots,n-1\}(i,j)∈{ 0,1,⋯,m−1}×{ 0,1,⋯,n−1 } in binary representation. The output of this function is the( i , j ) (i,j)(i,j ) elements.
For Spartan background knowledge, see:
- Blog Spartan: zkSNARKS without trusted setup study notes
- Blog Spartan: zkSNARKS without trusted setup source code analysis
- Vitalik R1CS example SNARK in the blog Spartan proves the basic idea
Extend R1CS in Spartan to CCS representation:

Remark 10:
- O ( qmd log 2 d ) O(qmd\log^2d) in Prover runtime in Theorem 1O ( q m dlog2Item d ) includes the use of FFT to convertddMultiply d different polynomials with a degree of 1. FFT is only suitable for certain finite fields.
Also, the actual CCS/AIR/Plonkish instance, whoseddd rarely exceeds 100, usually as low as 5 or even 2 [GPR21, BGtRZt23]. Therefore, FFT'sO ( d log 2 d ) O(d\log^2d)O(dlog2d ) time is much slower than directlyddO ( d 2 ) O(d^2)for multiplying polynomials with d degree of 1O(d2 )time. Using Karatsuba algorithm instead of FFT, sub-quadratic-in-ddd time algorithm, and is suitable for any finite field.
Theorem 1 proves:
For a certain CCS structure and instance, I = ( M 0 , ⋯ , M t − 1 , S 0 , ⋯ , S q − 1 , x ) \mathcal{I}=(M_0,\cdots,M_{ t-1}, S_0,\cdots,S_{q-1},x)I=(M0,⋯,Mt−1,S0,⋯,Sq−1,x ) and the claimed witnessWWW。令 Z = ( W , 1 , x ) Z=(W,1,x) Z=(W,1,x ) .
As mentioned earlier, you can:
- The matrix M 0 , ⋯ , M t − 1 M_0,\cdots, M_{t-1}M0,⋯,Mt−1Parsed as a function: { 0 , 1 } log m × { 0 , 1 } log n → F \{0,1\}^{\log m}\times \{0,1\}^{\log n }\rightarrow \mathbb{F}{ 0,1}logm×{ 0,1}logn→F。
- General ZZZ parses as a function:{ 0 , 1 } log n → F \{0,1\}^{\log n}\rightarrow \mathbb{F}{ 0,1}logn→F。
- Put ( 1 , x ) (1,x)(1,x ) parsed as a function:{ 0 , 1 } log n − 1 → F \{0,1\}^{\log n-1}\rightarrow \mathbb{F}{ 0,1}logn−1→F. _ [At this time, it is assumed thatZZZ中witnessWWW and( 1 , x ) (1,x)(1,x ) have the same lengthn/2 n/2n/2。】
Function ZZZ的MLEZ ~ \tilde{Z}Z~表示为:
t i l d e Z ( X 0 , ⋯ , X log n − 1 ) = ( 1 − X 0 ) ⋅ W ~ ( X 1 , ⋯ , X log n − 1 ) + X 0 ⋅ ( 1 , x ) ~ ( X 1 , ⋯ , X log n − 1 ) ( 13 ) tilde{Z}(X_0,\cdots,X_{\log n -1})=(1-X_0)\cdot \widetilde{W}(X_1,\cdots,X_{\log n-1})+ X_0\cdot \widetilde{(1,x)}(X_1,\cdots,X_{\log n-1})\ \ \ \ \ \ \ \ \ \ \ (13) tildeZ(X0,⋯,Xlogn−1)=(1−X0)⋅W
(X1,⋯,Xlogn−1)+X0⋅(1,x)
(X1,⋯,Xlogn−1) (13)
It can be seen that the right side in equation (13) is a multilinear polynomial. For all ( x 0 , ⋯ , x log n − 1 ) ∈ { 0 , 1 } log n (x_0,\cdots,x_{\log n -1})\in\{0,1\}^ {\log n}(x0,⋯,xlogn−1)∈{
0,1}logn , it is easy to check withZ ~ ( x 0 , ⋯ , x log n − 1 ) = Z ( ( x 0 , ⋯ , x log n − 1 ) ) \tilde{Z}(x_0,\cdots,x_ {\log n -1})=Z((x_0,\cdots,x_{\log n -1}))Z~(x0,⋯,xlogn−1)=Z((x0,⋯,xlogn−1)) . (becauseZZThe first half of Z evaluations corresponds to WWW , the second half corresponds to vector( 1 , x ) (1,x)(1,x ) . )
so the right-hand side in equation (13) isZZThe only multilinear extension of Z.
If ( 1 , x ) (1,x)(1,x ) length less thanWWW length (e.g. when converting AIR to CCS according to Lemma 3),xxx padding with zeros to getxpad x_{pad}xpad, so that after padding ( 1 , xpad ) (1,x_{pad})(1,xpad) length andWWSame as W. After padding with zeros, Verifier will calculate( 1 , x ) ~ ( X 1 , ⋯ , X log n − 1 ) \widetilde{(1,x)}(X_1,\cdots,X_{\log n- 1})(1,x)
(X1,⋯,Xlogn−1) time increaseO ( log n ) O(\log n)O(logn ) field addition operations. For example, if unfilled( 1 , x ) (1,x)(1,x ) has length2 l 2^l2l , it is easy to check that has lengthn/2 n/2n /2 padding( 1 , xpad ) (1,x_{pad})(1,xpad)的multilinear extension为:
( X 1 , ⋯ , X log n − 1 ) → ( 1 − X l + 1 ) ⋅ ( 1 − X l + 2 ) ⋯ ⋅ ( 1 − X log n − 1 ( 1 , x ) ~ ) ( X 1 , ⋯ , X l ) (X_1,\cdots,X_{\log n -1})\rightarrow (1-X_{l+1})\cdot (1-X_{l+2})\cdots\cdot (1-X_{\log n -1}\widetilde{(1,x)})(X_1,\cdots,X_l) (X1,⋯,Xlogn−1)→(1−Xl+1)⋅(1−Xl+2)⋯⋅(1−Xlogn−1(1,x)
)(X1,⋯,Xl)
Make the multilinear polynomial for all inputs ( x 1 , ⋯ , x log n − 1 ) (x_1,\cdots,x_{\log n-1})(x1,⋯,xlogn−1) corresponds to the filled( 1 , xpad ) (1,x_{pad})(1,xpad) , which can be considered as filled( 1 , xpad ) (1,x_{pad})(1,xpad) unique multilinear polynomials.
Similar to the Spartan paper Theorem 4.1, the "SuperSpartan's Polynomial IOP for CCS" protocol for CCS converted by Spartan R1CS is: the

sum-check protocol can be applied to the polynomial on the right side of equation (14):
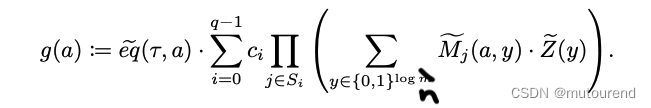
From the Verifier's point of view, this reduces the computation on the right-hand side of equation (14) to "evaluate ggg at a random input r a ∈ F m r_a\in\mathbb{F}^m ra∈Fm ”. And Verifier can itselfO ( log m ) O(\log m)O(logm ) field operations to calculateeq ~ ( τ , ra ) \tilde{eq}(\tau,r_a)eq~( t ,ra) , because it is easy to check:

when Verifier calculateseq ~ ( τ , ra ) \tilde{eq}(\tau,r_a)eq~( t ,ra) value, Verifier calculatesg ( ra ) g(r_a)g(ra) time isO ( dq ) O(dq)O(dq)。对于 i ∈ { 0 , 1 , ⋯ , t − 1 } i\in\{0,1,\cdots,t-1\} i∈{
0,1,⋯,t−1 } :

For this computation,ttt sum-check protocol: To this end, introduce random numbersγ ∈ F \gamma\in\mathbb{F}c∈F,并对 M ~ i ( r a , y ) ⋅ Z ~ ( y ) \tilde{M}_i(r_a,y)\cdot \tilde{Z}(y) M~i(ra,y)⋅Z~ (y)do random linear combination, the weights are[ γ 0 , ⋯ , γ t − 1 ] [\gamma^0,\cdots,\gamma^{t-1}][ c0,⋯,ct−1]。
In the sum-check protocol, Verifier only needs to check the above tt when doing the final checkt polynomialsM ~ i ( ra , y ) ⋅ Z ~ ( y ) \tilde{M}_i(r_a,y)\cdot \tilde{Z}(y)M~i(ra,y)⋅Z~(y) evaluate at r y r_y ry,即意味着Verifier evaluate M ~ i ( r a , r y ) \tilde{M}_i(r_a,r_y) M~i(ra,ry) is sufficient. Such a premise assumes that Verifier has query access toM ~ 0 , ⋯ , M ~ t − 1 \tilde{M}_0,\cdots,\tilde{M}_{t-1}M~0,⋯,M~t−1, according to equation (13), Verifier only needs to W ~ \tilde{W}W~ and( 1 , x ) ~ \widetilde{(1,x)}(1,x) Each query can get Z ~ ( ry ) \tilde{Z}(r_y) onceZ~(ry)。
The pseudocode of the "SuperSpartan's Polynomial IOP for CCS" protocol implemented in this paper is as follows:

In short, the "SuperSpartan's Polynomial IOP for CCS" protocol implemented in this paper has the following properties:

According to the above "SuperSpartan's Polynomial IOP for CCS" protocol pseudocode, it includes two sum-check protocol calls:
- 1) When the sum-check protocol is triggered for the first time in step 3.a, the main workload of Prover is:


- 2) Call the sum-check protocol for the second time in step 3.c, corresponding to log n \log nlogPolynomial of n variables:

the degree of each variable is at most 2. Using the standard linear-time-sum-check technology [CTY12, Tha13] in the sum-check protocol, the time used by Prover isO ( N + t ) O(N+t)O ( N+t)。
5. Avoid preprocessing in uniform IR
When there is a "uniform" structure in the CCS instance (for example, a circuit has multiple identical sub-circuits), in order to achieve succinct verification cost, the preprocessing of the circuit structure should be avoided.
For the uniform CCS instance, this article implements:
- Verifier可evaluate the multilinear extension polynomials M ~ 0 , ⋯ , M ~ t − 1 \tilde{M}_0,\cdots,\tilde{M}_{t-1} M~0,⋯,M~t−1 at any desired point in time logarithmic in the number of rows and columns of these matrices。
5.1 Multilinear extension of "adding 1 in binary" function
Integer { 0 , 1 , ⋯ , D − 1 } \{0,1,\cdots, D-1\} can be{ 0,1,⋯,D−1 } in binary representation. IntegerD − 1 D-1D−An index of 1 can be represented by a vector of all ones, and an index of integer 0 can be represented by a vector of all zeros. In this index notation, the rightmost bit can be thought of as a low-order bit.
For a bit-vector i ∈ { 0 , 1 } log D i\in\{0,1\}^{\log D}i∈{ 0,1}logD,令 to-int ( i ) = ∑ j = 0 log D − 1 i j ⋅ 2 j \text{to-int}(i)=\sum_{j=0}^{\log D-1}i_j\cdot 2^j to-int(i)=∑j=0logD−1ij⋅2j corresponds toiiThe integer represented by i . For integerκ ∈ { 0 , 1 , ⋯ , t − 1 } \kappa \in\{0,1,\cdots,t-1\}K∈{ 0,1,⋯,t−1 },bin ( κ ) \text{bin}(\kappa)bin ( k ) display\kappaκ corresponds to the binary representation.
Define the function:
next ( i , j ) : { 0 , 1 } log D × { 0 , 1 } log D → { 0 , 1 } \text{next}(i,j):\{0,1\ }^{\log D}\times \{0,1\}^{\log D}\rightarrow \{0,1\}next(i,j):{
0,1}logD×{
0,1}logD→{
0,1 }
where:
- i , j i,j i,j is bit-vector input
- This and this integer I = to-int ( i ) I=\text{to-int}(i)I=to-int(i)和整数 J = to-int ( j ) J=\text{to-int}(j) J=to-int(j)满足 J = I + 1 J=I+1 J=I+1 , the function output is 1, otherwise it is 0.
The function can therefore be called the "adding 1 in binary" function:
- The input is 2 bit-vectors, and it is judged whether the second input integer is the first input integer plus 1.
Notice:
- young iii is all 1 vector, then for allj ∈ { 0 , 1 } log D j\in\{0,1\}^{\log D}j∈{ 0,1}logD , all have( i , j ) = 0 (i,j)=0(i,j)=0。
Thus there is Theorem 2:

the actual analysis is divided into 3 situations:

the next is to explain the equation (16) can be evaluated at any point ( rx , ry ) ∈ F log D × F log D (r_x,r_y)\in\mathbb {F}^{\log D}\times \mathbb{F}^{\log D}(rx,ry)∈FlogD×FlogD in O ( log D ) O(\log D) O(logD) time:
- It is easy to see that h ( rx , ry ) h(r_x,r_y)h(rx,ry)可evaluate in O ( log D ) O(\log D) O(logD) time。
- ggEach summation item in g can be evaluated at ( rx , ry ) (r_x,r_y)(rx,ry) in O ( log D ) O(\log D) O(logD) time。
- ggThere are O ( log D ) O(\log D)in gO(logD ) summation terms, so the total time bound isO ( log D 2 ) O(\log D^2)O(logD2)。
- However, if adjacent terms of the sum have nearly identical factors, this runtime can be reduced to O ( log m ) O(\log m)O(logm ) . For example, ifv ( k ) v(k)v ( k ) is the kkthin the summationk items, then:


5.2 CCS converted from AIR
In this section, mmm表示AIR的参数,有 w A I R ∈ F ( m − 1 ) ⋅ t / 2 , z A I R ∈ F ( m + 1 ) ⋅ t / 2 w_{AIR}\in\mathbb{F}^{(m-1)\cdot t/2},z_{AIR}\in\mathbb{F}^{(m+1)\cdot t/2} wAIR∈F(m−1)⋅t/2,zAIR∈F( m + 1 ) ⋅ t /2 . At the same timemmm represents the CCS matrixM 0 , ⋯ , M t − 1 M_0,\cdots,M_{t-1}M0,⋯,Mt−1the number of rows. This section also assumes that m − 1 m-1m−1 is a power of 2, and forM 0 , ⋯ , M t − 1 M_0,\cdots,M_{t-1}M0,⋯,Mt−1Fill with zeros so that the number of rows is a power of 2 (this padding will not increase the Verifier or Prover time in SuperSpartan). That means the filled M 0 , ⋯ , M t − 1 M_0,\cdots,M_{t-1}M0,⋯,Mt−1The number of rows is no longer mmm , but2 ( m − 1 ) 2(m-1)2(m−1 ) .
This processing is convenient for implementation based on the actual domain, and with the help of the multilinear extension of the "adding 1 in binary" function in the previous section, the actual expression of CCS converted from AIR is further optimized.
5.3 Avoiding preprocessing in SIMD CCS
6. Compile Polynomial IOP for CCS to SNARK for CCS

