Project 7 HDLC Encapsulation of Router in Wide Area Network
In order to keep the connected routers in the company network in a confidential and safe state and avoid external interference, Xinke Company decided to configure HDLC encapsulation of the routers. The network topology is shown in Figure 3-23 .
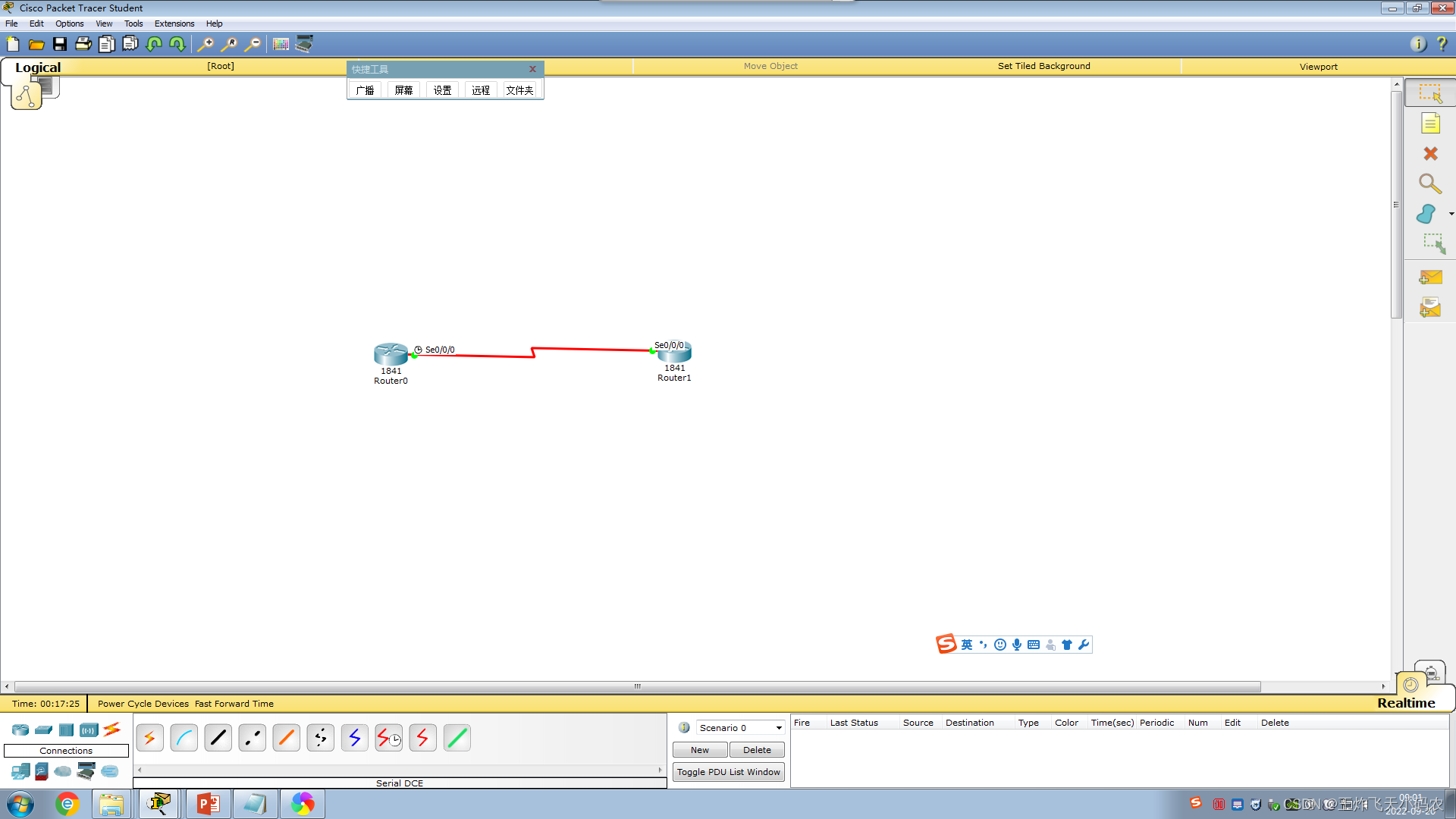
The specific operations for configuring HDLC encapsulation in the router WAN are as follows:
Step 1 Configure the IP address of the router interface, as shown in Table 3-7 .
Table 3-7 IP addresses of router interfaces
| router |
interface |
IP address |
| Router0 |
S0/0/0(DCE) |
192.168.1.1/24 |
| Router1 |
S0/0/0(DTE) |
192.168.1.2/24 |
Step 2 Configure Router0 , the code is as follows
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int s0/0/0
Router(config-if)#ip add 192.168.1.1 255.255.255.0
Router(config-if)#encapsulation hdlc
Router(config-if)#clock rate 64000
Router(config-if)#no shut
%LINK-5-CHANGED: Interface Serial0/0/0, changed state to down
Router(config-if)#exStep 3 Configure Router1 , the code is as follows
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int s0/0/0
Router(config-if)#ip add 192.168.1.2 255.255.255.0
Router(config-if)#encapsulation hdlc
Router(config-if)#no shut
Router(config-if)#
%LINK-5-CHANGED: Interface Serial0/0/0, changed state to up
Router(config-if)#ex
Router(config)#
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up
Step 4 Test network connectivity, the code is as follows
Router#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/3/7 ms
Router#PPP encapsulation of task eight routers
In order to realize the security of the connection with the ISP , Xinke Company adopts the PPP protocol to encapsulate the communication link. The network topology diagram is shown in Figure 3-23 . The specific operations are as follows:
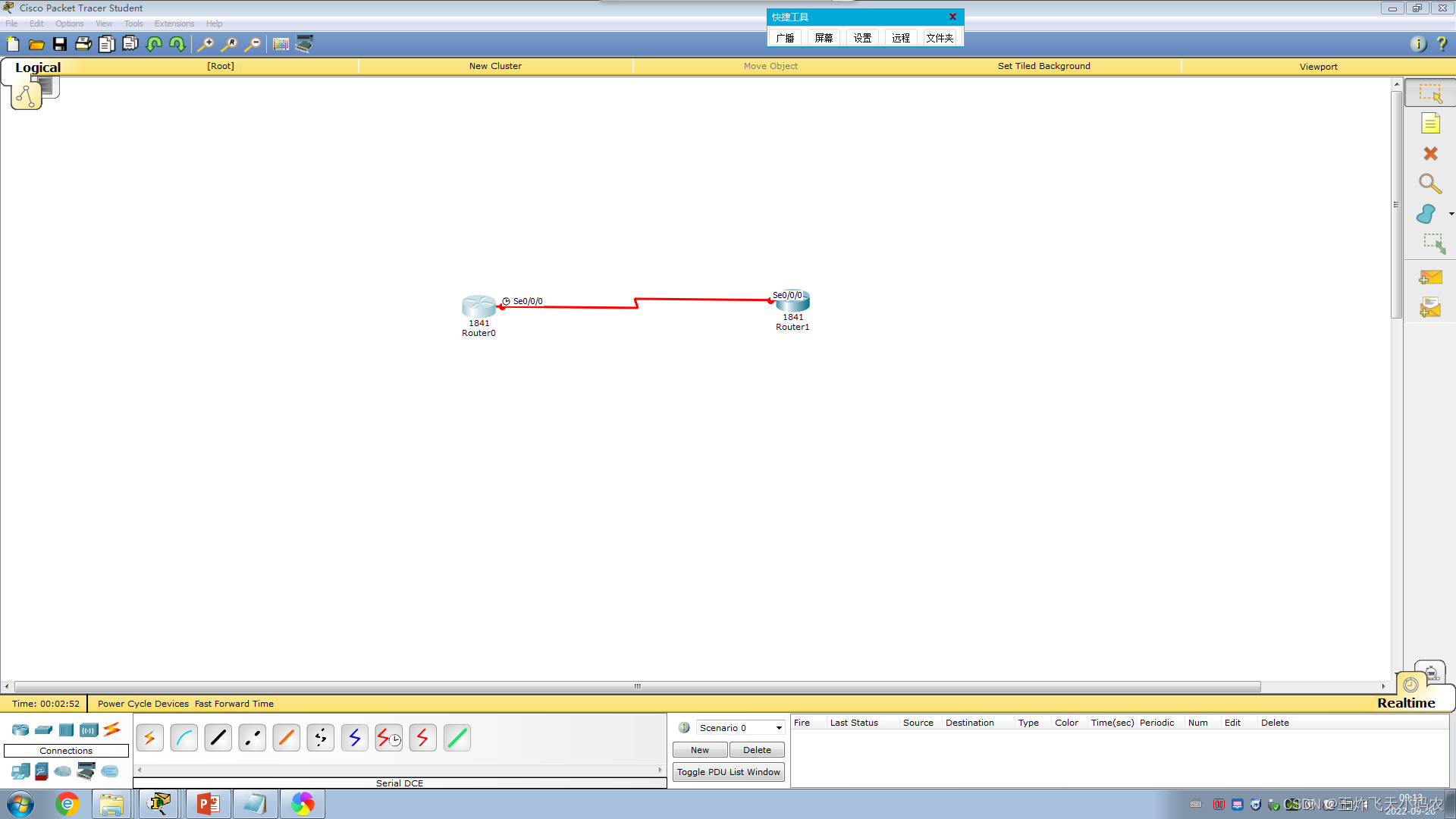
Step 1 Configure the IP address of the router interface, as shown in Table 3-7 .
Table 3-7 IP addresses of router interfaces
| router |
interface |
IP address |
| Router0 |
S0/0/0(DCE) |
192.168.1.1/24 |
| Router1 |
S0/0/0(DTE) |
192.168.1.2/24 |
Step 2 Configure Router0 , the code is as follows
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int s0/0/0
Router(config-if)#ip add 192.168.1.1 255.255.255.0
Router(config-if)#en
Router(config-if)#encapsulation ppp
Router(config-if)#cl
Router(config-if)#clock ra
Router(config-if)#clock rate 64000
Router(config-if)#no shut
%LINK-5-CHANGED: Interface Serial0/0/0, changed state to down
Router(config-if)#^Z
Router#Step 3 Configure Router1 , the code is as follows
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int s0/0/0
Router(config-if)#ip add 192.168.1.2 255.255.255.0
Router(config-if)#en
Router(config-if)#encapsulation ppp
Router(config-if)#no shut
Router(config-if)#
%LINK-5-CHANGED: Interface Serial0/0/0, changed state to up
Router(config-if)#
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up
^Z
Router#Step 4 Test network connectivity, the code is as follows
Router#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/5 ms
Task 9 WAN PPP encapsulation PAP verification of the router
In order to meet the ever-increasing business needs, Xinke Company has applied for dedicated line access. The company's client router needs to verify its identity when negotiating links with the ISP . Now it needs to configure the router to ensure link establishment and communication security.
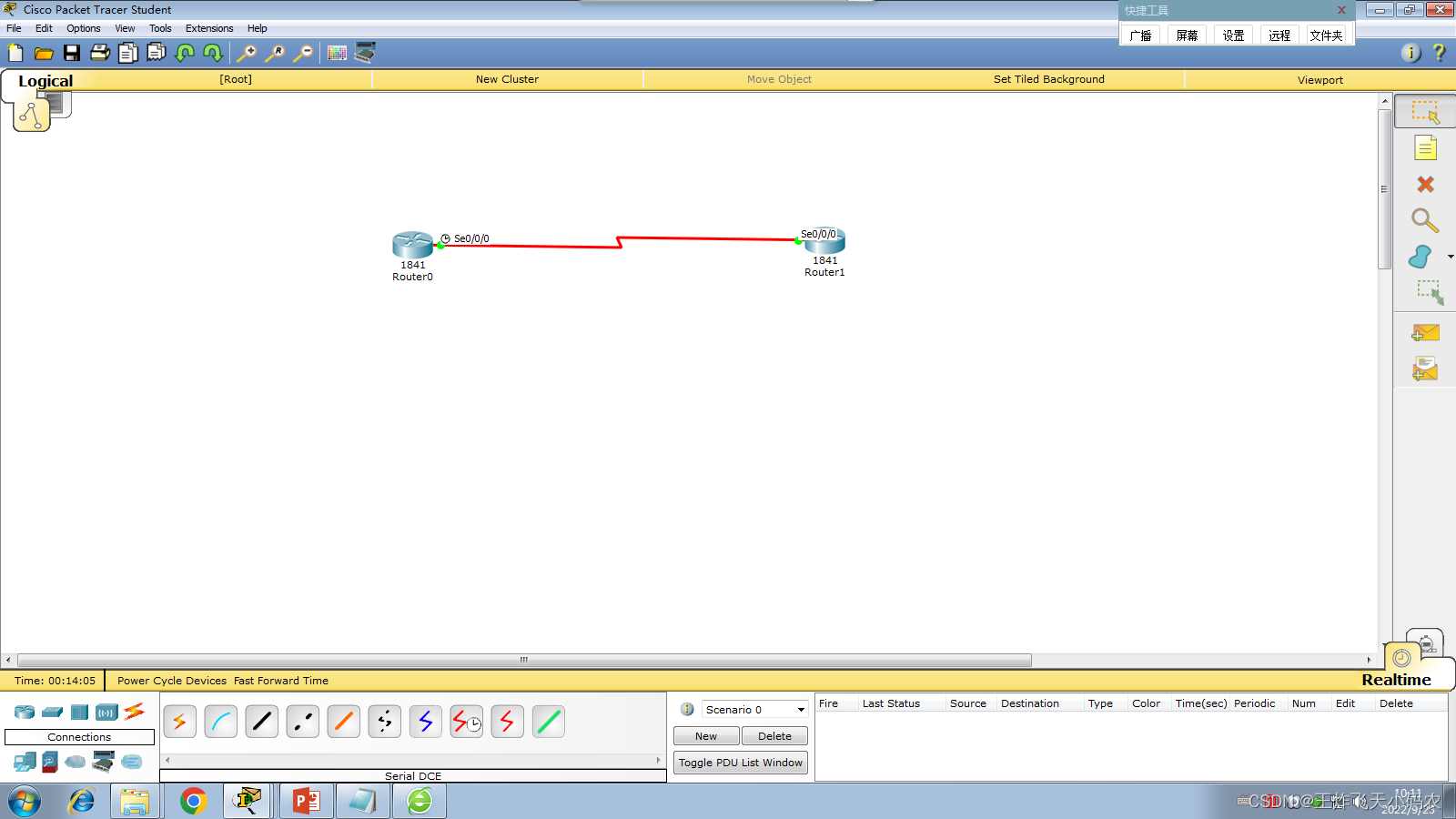
In order to achieve the security of the connection with the ISP , Xinke Company adopts the PPP protocol to encapsulate the communication link, and after the communication link is established, the PPP session password authentication protocol - PAP is enabled . The network topology is shown in the figure 3-23 . Table 3-8 lists the relevant configurations of WAN PPP encapsulation with PAP .
Table 3-8 Basic configuration of PAP authentication for PPP encapsulation
| router |
parameter |
|
| RouterA |
Interface: S0/0/0 |
IP address: 192.168.1.1 |
| Account: RouterA |
Password: 888A |
|
| RouterB |
Interface: S0/0/0 |
IP address: 192.168.1.2 |
| Account: RouterB |
Password: 888B |
|
The specific operations for configuring PPP encapsulation on the router WAN and performing PAP authentication are as follows:
Step 1 Configure the S0/0/0 port IP of Router0 , the code is as follows
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int s0/0/0
Router(config-if)#ip add 192.168.1.1 255.255.255.0
Router(config-if)#clock rate 64000
Router(config-if)#no shut
Router(config-if)#exStep 2 Configure the S0/0/0 port IP of Router1 , the code is as follows
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int s0/0/0
Router(config-if)#ip add 192.168.1.2 255.255.255.0
Router(config-if)#no shut
Router(config-if)#ex
Step 3 Name Router0 as RouterA, the code is as follows
Router(config)#ho RouterAStep 4 Name Router1 as RouterB, the code is as follows
Router(config)#ho RouterBStep 5 Configure on router0, set a username and password for router 1, the code is as follows:
RouterA(config)#username RouterB password 888BStep 6 Configure on router1, set a username and password for router 0, the code is as follows:
RouterB(config)#username RouterA password 888AStep 7 Configure on router0, enter the S0/0/0 port, perform PPP protocol encapsulation, and set authorization as PAP login, the code is as follows:
RouterA(config)#int s0/0/0
RouterA(config-if)#encapsulation ppp
RouterA(config-if)#
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to down
RouterA(config-if)#ppp authentication papStep 8 Configure on router1, enter the S0/0/0 port, perform PPP protocol encapsulation, and set authorization as PAP login, the code is as follows:
RouterB(config)#int s0/0/0
RouterB(config-if)#
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to down
RouterB(config-if)#encapsulation ppp
RouterB(config-if)#ppp authentication papStep 9 Configure router0 to send the user name and password for PAP login, the code is as follows:
RouterA(config-if)#ppp pap sent-username RouterA password 888A
RouterA(config-if)#Step 10 Configure router1 to send the user name and password for PAP login, the code is as follows:
RouterB(config-if)#ppp pap sent-username RouterB password 888BStep 11 Perform a connectivity test on router0, the code is as follows:
RouterA#p 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/10 ms
RouterA#Task ten router WAN PPP encapsulation CHAP authentication
In order to meet the growing business needs, Xinke Company applied for dedicated line access. In order to realize the security of the connection with the ISP , Xinke Company adopted the PPP protocol to encapsulate the link and adopted PAP authentication.
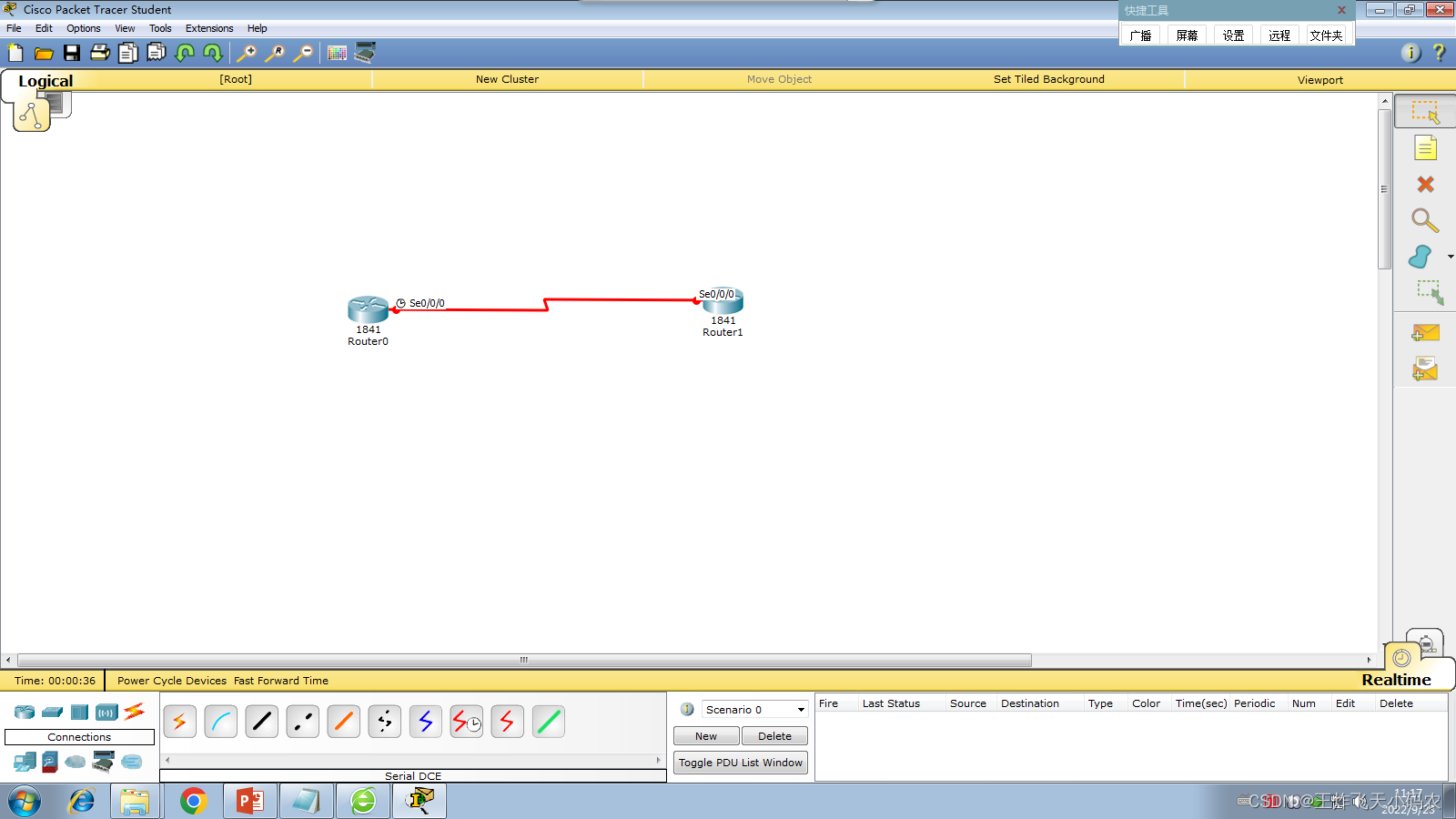
Since the information is transmitted in clear text when PAP verifies the user's identity, the verification information is likely to be stolen by a third party during the verification process. The company does not want this phenomenon and puts forward higher security requirements . Therefore, the network administrator decided to adopt the CHAP authentication protocol in the PPP protocol. The CHAP authentication protocol uses encryption authentication during the authentication process, so it can better ensure the security of the network. The network topology is shown in Figure 3-23 . Table 3-9 shows the basic configuration of PPP encapsulation CHAP authentication .
Table 3-9 Basic configuration of PPP encapsulation CHAP authentication
| router |
parameter |
|
| Router0 |
Interface: S0/0/0 |
IP address: 192.168.1.1 |
| Account: RouterA |
Password: CH888 |
|
| Router1 |
Interface: S0/0/0 |
IP address: 192.168.1.2 |
| Account: RouterB |
Password: CH888 |
|
The specific operation of configuring the router WAN PPP encapsulation CHAP authentication is as follows:
Step 1 Configure the S0/0/0 port IP of Router0 , the code is as follows
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int s0/0/0
Router(config-if)#ip add 192.168.1.1 255.255.255.0
Router(config-if)#clo
Router(config-if)#clock rate 64000
Router(config-if)#no shut
%LINK-5-CHANGED: Interface Serial0/0/0, changed state to down
Router(config-if)#
%LINK-5-CHANGED: Interface Serial0/0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up
Step 2 Configure the S0/0/0 port IP of Router1 , the code is as follows
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int s0/0/0
Router(config-if)#ip add 192.168.1.2 255.255.255.0
Router(config-if)#no shut
Router(config-if)#
%LINK-5-CHANGED: Interface Serial0/0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up
Step 3 Name Router0 as RouterA, and set a username and password for Router1, the code is as follows:
Router(config-if)#ex
Router(config)#ho RouterA
RouterA(config)#user
RouterA(config)#username RouterB password CH888Step 4 Name Router1 as RouterB, and set a username and password for Router0, the code is as follows:
Router(config-if)#ex
Router(config)#ho RouterB
RouterB(config)#use
RouterB(config)#username RouterA pass
RouterB(config)#username RouterA password CH888Step 5 Configure on router0, enter the S0/0/0 port, perform PPP protocol encapsulation, and set authorization as CHAP login, the code is as follows:
RouterA(config)#int s0/0/0
RouterA(config-if)#encapsulation ppp
RouterA(config-if)#
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to down
RouterA(config-if)#ppp authentication chap
RouterA(config-if)#Step 6 Configure on router1, enter the S0/0/0 port, perform PPP protocol encapsulation, and set authorization as CHAP login, the code is as follows:
RouterB(config)#int s0/0/0
RouterB(config-if)#
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to down
RouterB(config-if)#encapsulation ppp
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up
RouterB(config-if)#ppp authentication chap
RouterB(config-if)#
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to down
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up
Step 7 Perform a connectivity test on router0, the code is as follows:
(The connectivity test needs to be performed in privileged mode~~~~)
RouterA#p 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/4/9 ms
RouterA#Task 11 Use dynamic NAT to realize LAN access to the Internet
Xinke Company has applied for a dedicated line from the ISP according to business needs, and the dedicated line is equipped with a fixed IP : 202.168.2.1 . Now the company hopes that all hosts in the enterprise can access the external network.
Since the network dedicated line applied by the company only provides a public network address, and there are a large number of hosts in the company that need to connect to the Internet , therefore, the engineer decided to use NAT technology to realize the Internet access for all in the company through NAT address translation technology. Figure 3-24 shows the network topology for this task.
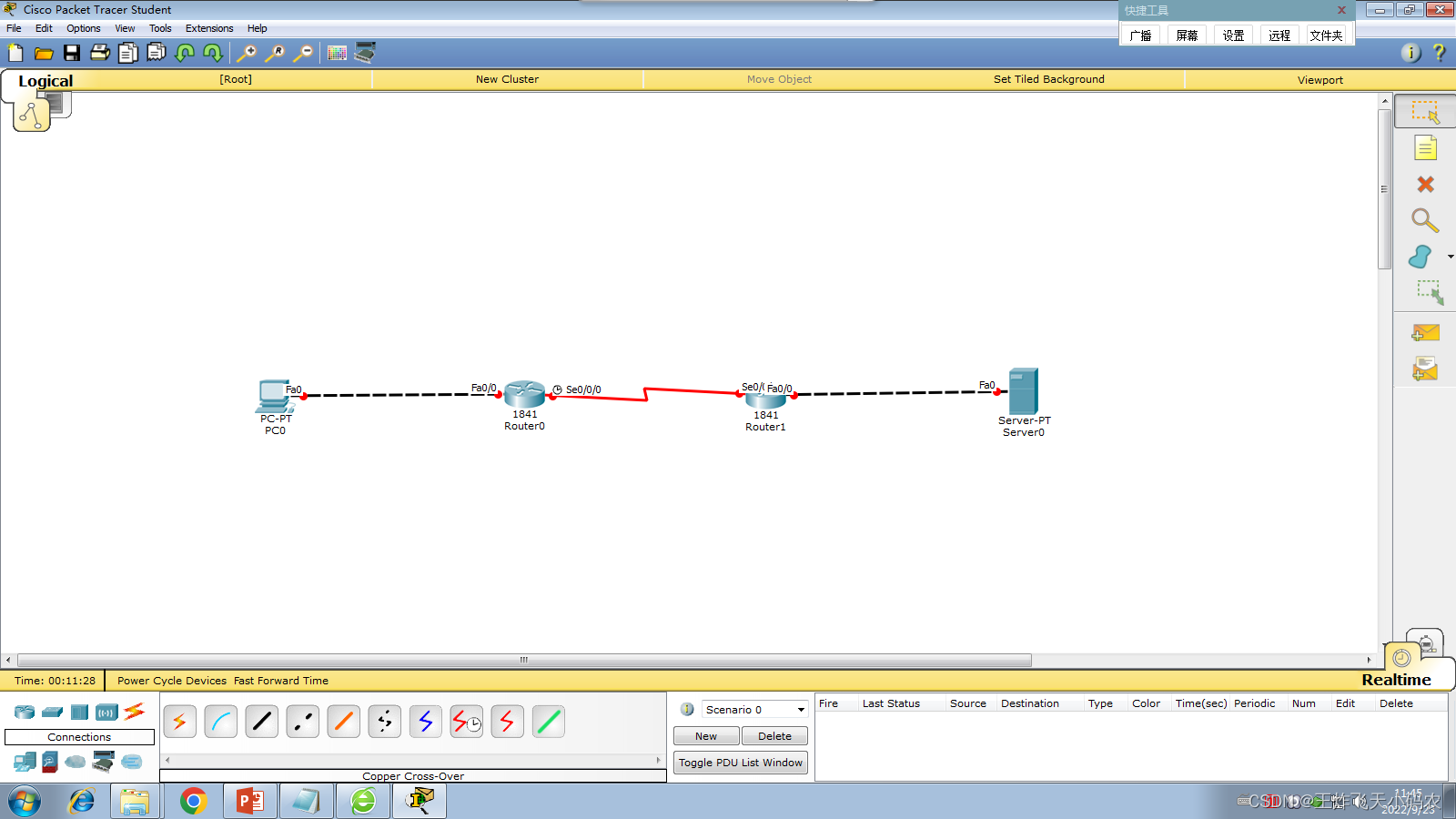
Figure 3-24 Network topology diagram
The specific operation of using dynamic NAPT to realize LAN access to the Internet is as follows:
Step 1 Configure the router interface and the IP address of the computer according to the contents of the previous tasks and Table 3-10 , and perform a connectivity test.
Table 3-10 IP addresses of routers and computers
| equipment |
interface |
IP address |
gateway |
| RouterA |
S0/2(DCE) |
192.168.1.1/24 |
|
| F0/0 |
192.168.0.1/24 |
||
| RouterB |
S0/1(DTE) |
192.168.1.2/24 |
|
| F0/0 |
192.168.2.1/24 |
||
| PC1 |
192.168.0.3/24 |
192.168.0.1 |
|
| Extranet SERVER |
192.168.2.2/24 |
192.168.2.1 |
(1) Set the IP address of each port
Router IP setting instructions:
1)router 0

Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int f0/0
Router(config-if)#ip add 192.168.0.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#
%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
Router(config-if)#ex
Router(config)#int s0/0/0
Router(config-if)#ip add 192.168.1.1 255.255.255.0
Router(config-if)#clock rate 64000
Router(config-if)#no shut
%LINK-5-CHANGED: Interface Serial0/0/0, changed state to down
Router(config-if)#
%LINK-5-CHANGED: Interface Serial0/0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up
Router(config-if)#ex2) Router 1 port command:
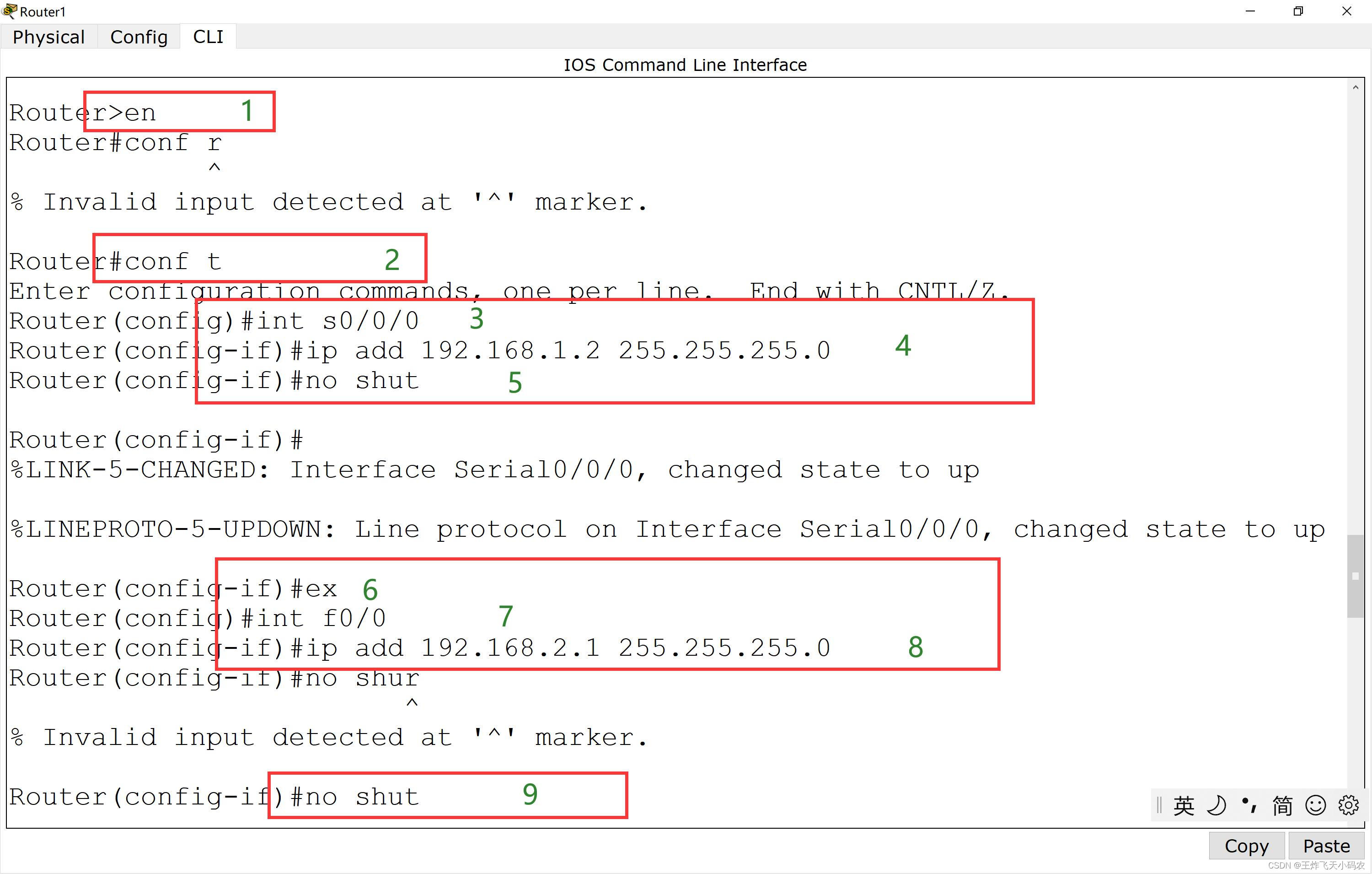
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#int s0/0/0
Router(config-if)#ip add 192.168.1.2 255.255.255.0
Router(config-if)#no shut
Router(config-if)#
%LINK-5-CHANGED: Interface Serial0/0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface Serial0/0/0, changed state to up
Router(config-if)#ex
Router(config)#int f0/0
Router(config-if)#ip add 192.168.2.1 255.255.255.0
Router(config-if)#no shut
Router(config-if)#
%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
Router(config-if)#ex
Router(config)#ex3) PC and server set IP
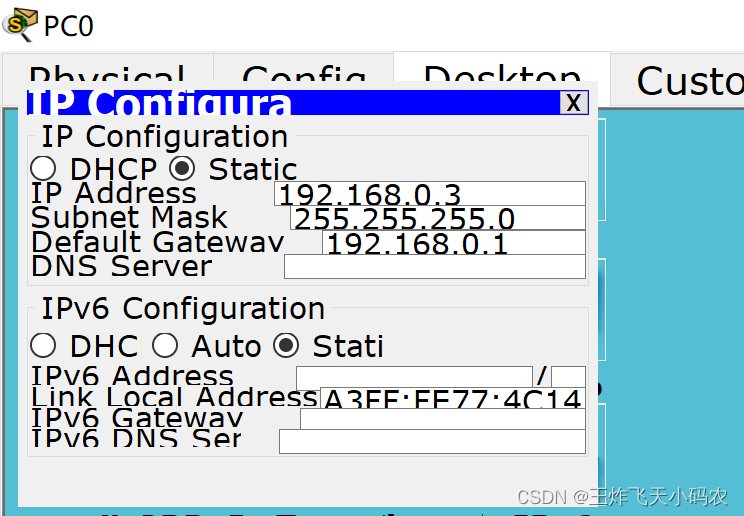

Step 2 This task performs address translation on Router0 , converts 192.168.0.0/24 into addresses between 192.168.1.10 and 192.168.1.20 , and performs port address multiplexing. The code is as follows:
Router(config)#ip access-list standard 1
Router(config-std-nacl)#permit 192.168.0.0 0.0.0.255
Router(config-std-nacl)#ex
Router(config)#ip nat pool overld 192.168.1.10 192.168.1.20 netmask 255.255.255.0
Router(config)#ip nat inside source list 1 pool overld
Router(config)#int f0/0
Router(config-if)#ip nat inside
Router(config-if)#ex
Router(config)#int s0/0/0
Router(config-if)#ip nat outside
Router(config-if)#ex
Router(config)#ip route 0.0.0.0 0.0.0.0 192.168.1.2
Router(config)#ex
Router# 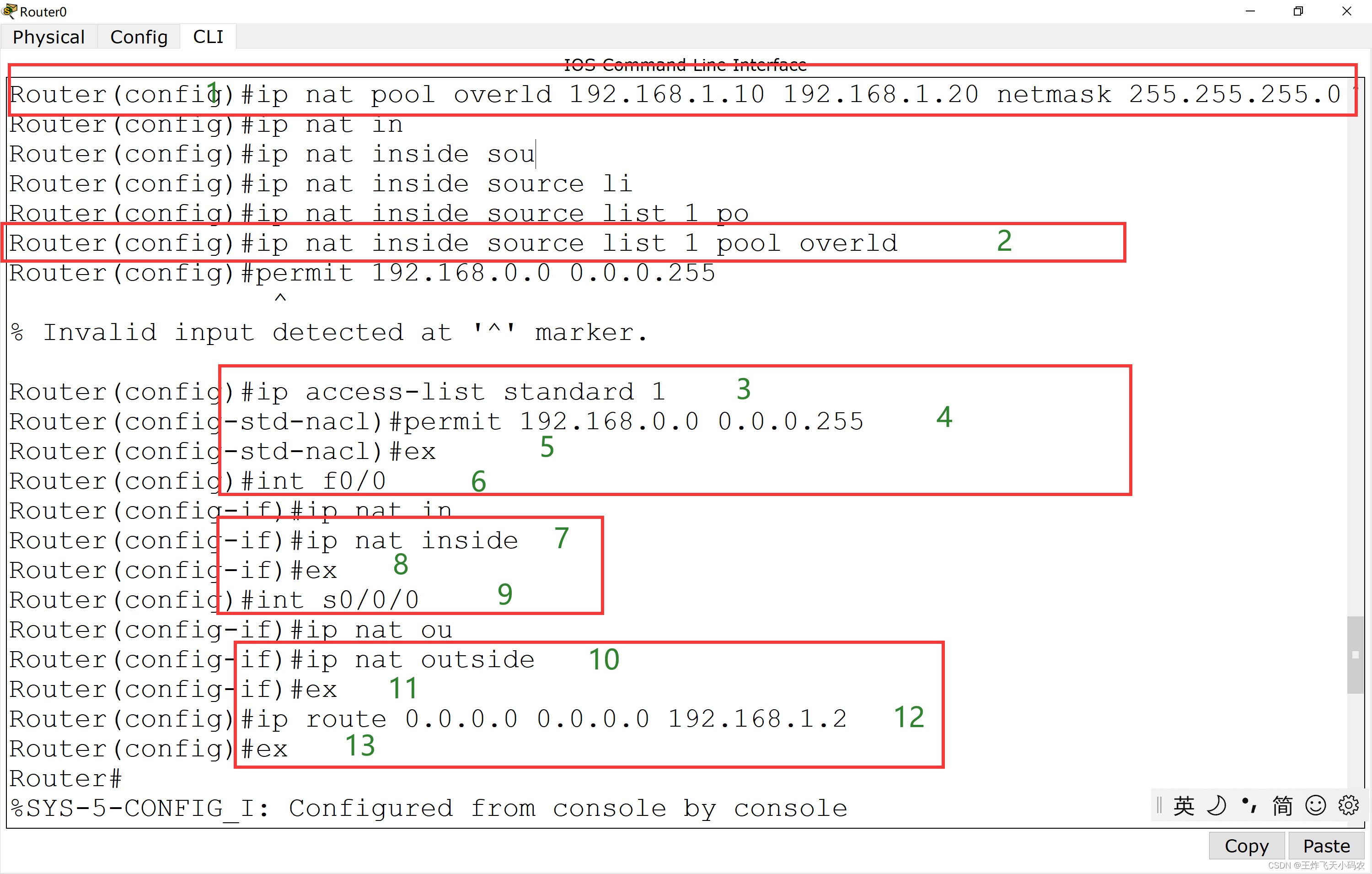
Step 3 View the routing table of Router1 , the code is as follows:
Router#sh ip route
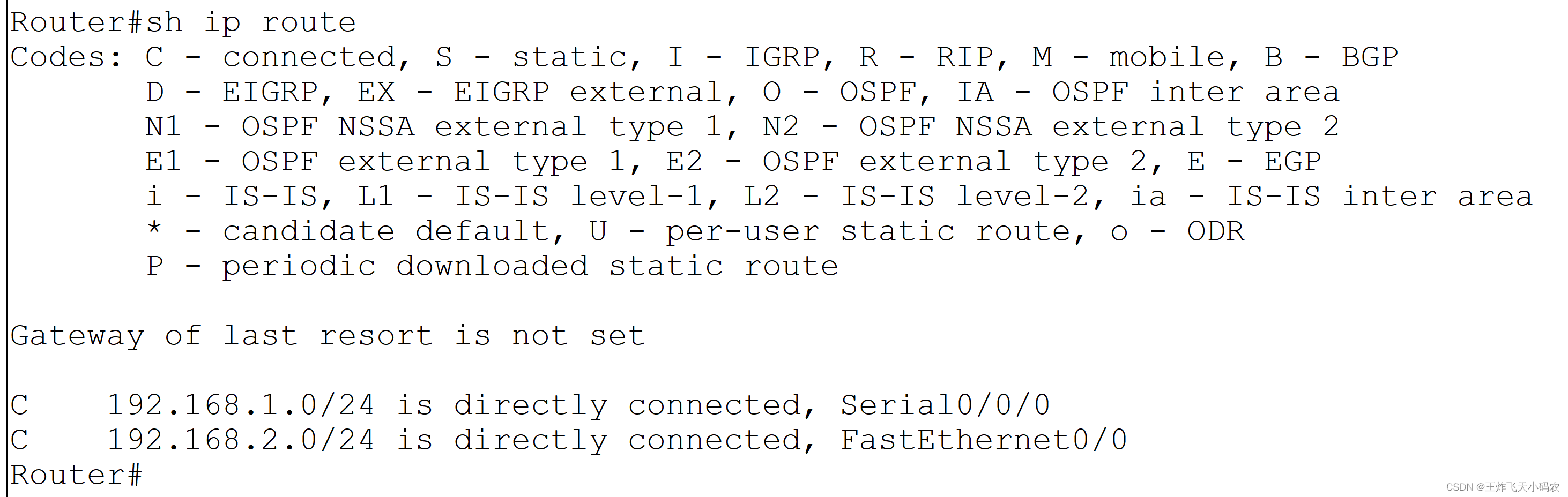
! Note: There is no route to 192.168.0.0
Step 4 Use the Ping command on PC0 to test the network, as shown in Figure 3-25 .
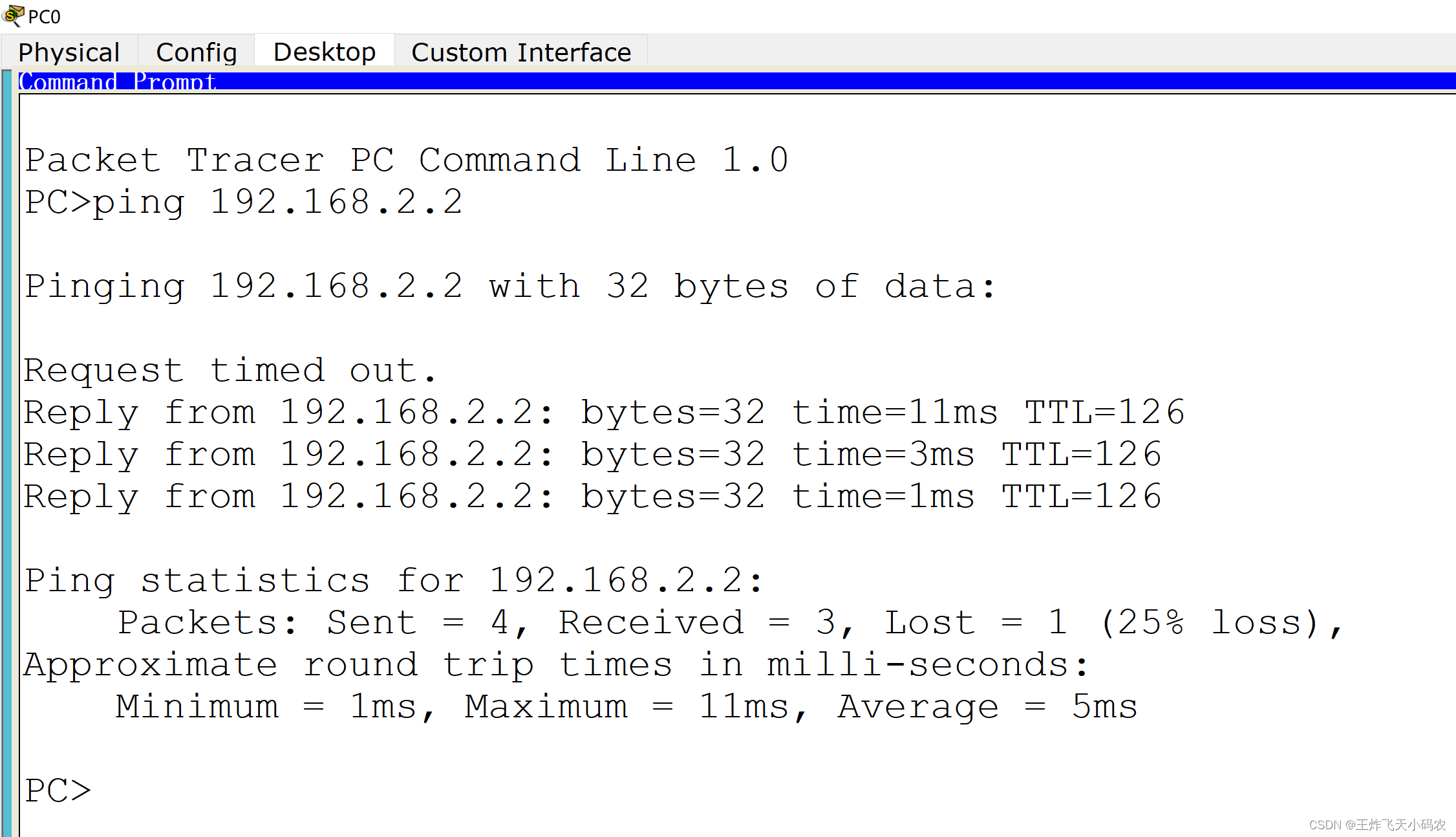
Figure 3-25 Test network
Step 5 View the address conversion table, the code is as follows:
Router#sh ip nat translations 