What is Internet Security?
In my private messages, people often ask:
Is network security technology equivalent to "hacking" technology?
Big leak! ! !
The so-called "hacking" or "infiltration" technology is only a branch of the field of network security and cannot represent its whole picture.
With the rapid development of next-generation information technologies such as artificial intelligence, big data, cloud computing , and the Internet of Things , and the implementation of policies and regulations such as the Network Security Law and Leveled Protection 2.0, the definition and scope of network security are becoming wider and wider . Security is extended to Cyberspace Security, namely "cyberspace security".
Therefore, according to application scenarios or technical implementations, cybersecurity (Cyberspace Security) can be simply subdivided into the following directions =>
• Network Security
• Web Application Security
• Mobile Security
• Cloud Security
• Desktop Security
• Data Security
• Wireless Security
What kind of problems will you encounter when learning the direction of network security?
1. It takes a long time to lay the foundation
2. The knowledge points are not clear enough
3. Knowledge points are unclear
4. The learning of knowledge points is not systematic enough
5. Insufficient ability to solve problems by oneself
6. Insufficient actual combat level
7. Intranet learning is relatively difficult
How to Get Started Learning Cyber Security
Learning network security requires a solid basic knowledge of computers and networks. If you want to engage in research and development positions in the field of network security in the future, you also need to have a solid mathematical foundation . Since the overall amount of knowledge is very large, learning network security should first have its own learning entry point. For those with strong hands-on ability, they can start from the basic knowledge of the network, and then gradually understand the various network security equipment. related information.

Cyber Security Learning Path
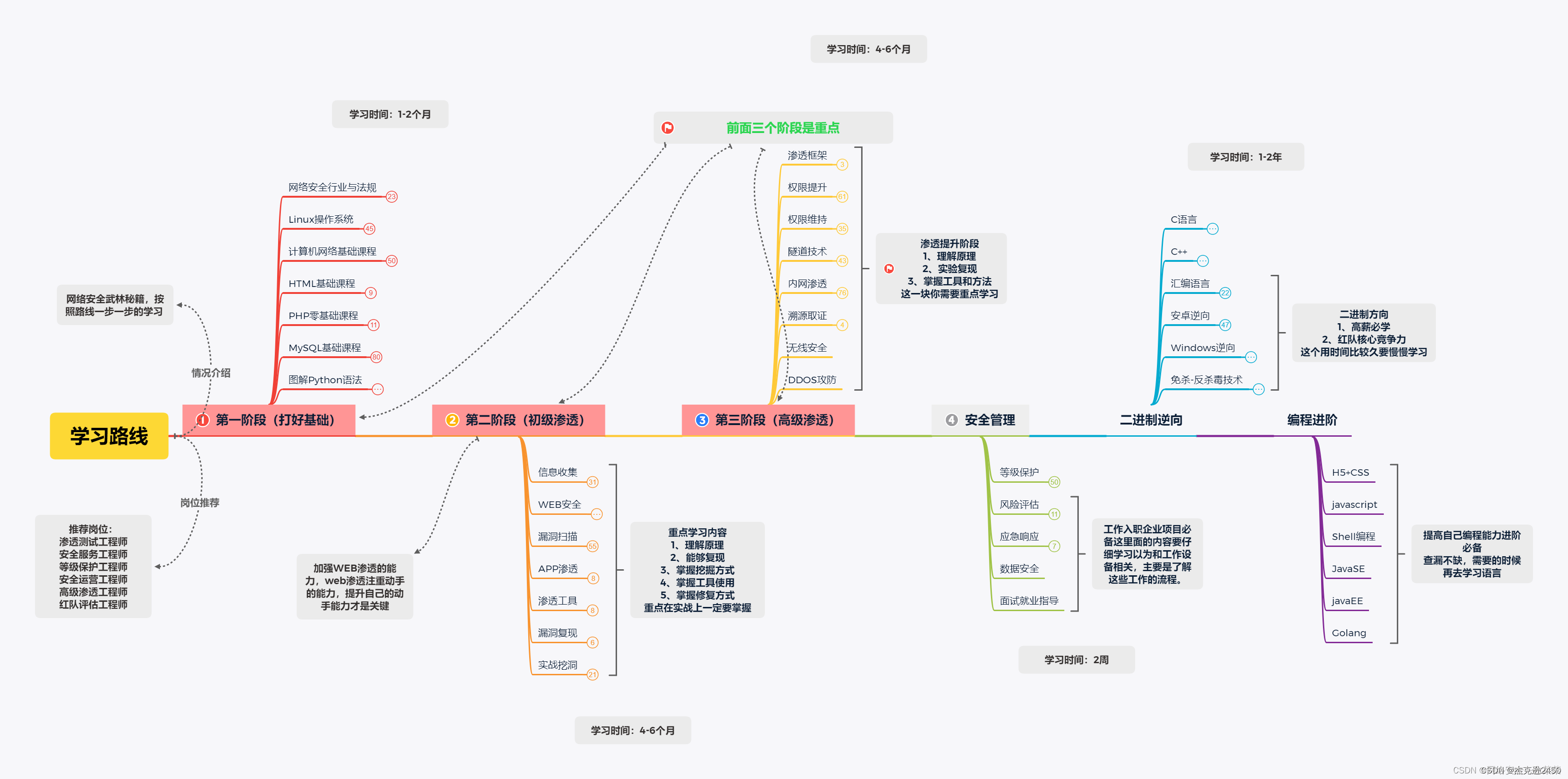
Part I: Security Basics
1.1. Network Security Industry and Regulations
1.2. Linux Operating System
1.3. Computer Network Basics
1.4. HTLM Basics 1.5
. JavaScript Basics 1.6
. PHP Introduction
1.7. MYSQL Basics
1.8. Python Programming
Part Two: Web Security
2.1. Information Gathering 2.2
. SQL Injection Vulnerabilities
2.3. CSRF Vulnerabilities
2.4. XSS Vulnerabilities
2.5. File Upload Vulnerabilities 2.6
. File Inclusion Vulnerabilities 2.7.
SSRF Vulnerabilities
2.8. XXE Vulnerabilities
2.9. Remote Code Execution Vulnerabilities
2.10. Passwords Brute Force Guessing and Defense
2.11. JWT Penetration and Defense
2.12. Logical Vulnerability
2.13. Redis Unauthorized Access Vulnerability
2.14. Deserialization Vulnerability Penetration and Defense 2.15.
AWVS Vulnerability Scanning
2.16. Appscan Vulnerability Scanning 2.17
. Nessus Vulnerability Scanning
2.18. Burp Sui te From entry to actual combat
Part 3: Penetration Combat
3.1. CVE Vulnerability Reappearance
3.2. Vulnhub Range Combat Series
3.3. Vulnerability Digging Project Combat
3.4. Practical Vulnerability Digging Experience Sharing
3.5. 2023HW Practical Topic
3.6. Network Security Interview Employment Guidance Course
Part IV: Enterprise Security System Construction
4.1. Level Protection
4.2. Emergency Response
4.3. Code Audit
4.4. Risk Assessment
4.5. Security Inspection
4.6. Data Security
Part V: Post-infiltration
5.1. MSF-Metasploit Framework
5.2. CS-CobaltStrike
5.3. Intranet penetration
5.4. System privilege escalation penetration and defense
Part VI: Code Audit
6.1. MSF-Metasploit Framework
6.2. CS-CobaltStrike
6.3. Intranet penetration
6.4. System privilege escalation penetration and defense
Part VII: Binary Security
7.1. Assembly Language Programming
7.2. Introduction to C Language Programming
7.3. Introduction to C++ Programming 7.4
. Windows Reverse Advanced Edition
7.5. Antivirus Antivirus Technology
7.6. Android Reverse
7.7. Web Js Reverse
Part Eight: Protocol Vulnerabilities
8.1. DOS and DDOS Penetration and Defense
8.2. Wireless Related Penetration and Defense
8.3. ARP Penetration and Defense
Part IX: Advanced programming
9.1.HTML5+CSS3 zero basics to actual combat
9.2.Shell programming
9.3.Golang grammar intensive
Part 10: CTF
10.1. CTF Capture the Flag
10.2. Cryptography and Network Security
In general, you only need to study 10 parts for 4-6 months to get a job!
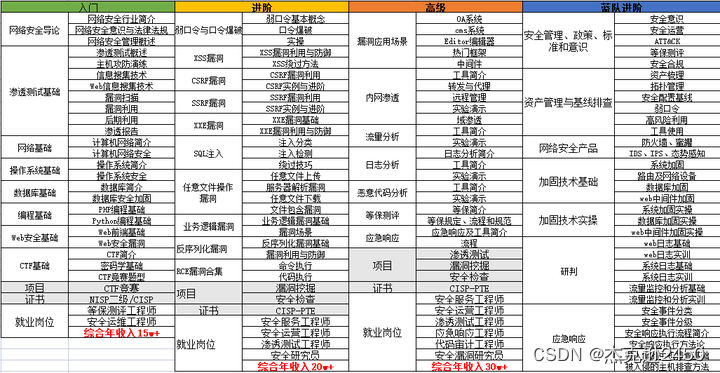 Recommended learning method: video tutorials + books
Recommended learning method: video tutorials + books
Because I was self-taught in network security at the beginning, I have worked in security for nearly ten years now, and my current position in the company is a penetration test engineer, so I still have a good understanding of this aspect. The best way to learn with zero foundation should be "video tutorials" with some books on principles to learn. Video tutorials are relatively easy to understand, while books focus on theoretical understanding, which allows you to understand the knowledge points at each stage in principle. A deeper understanding.
Video supporting materials & domestic and foreign network security books, documents & tools

Interview Questions
We study network security to find a high-paying job. The following interview questions are the latest interview materials from Baidu, Jingdong, 360, Qi Anxin and other first-line Internet companies, and some experts have given authoritative answers. After reading this set of interview materials, I believe everyone can find a satisfactory job.

Hacking Tools Collection

Learning plan:
It is recommended to devote at least 3 hours a day to study, learn new knowledge points for 2 hours, and practice for the remaining 1 hour. Watch the video tutorial every day, and then practice all the actual combat in the video to deepen your impression. Then read the corresponding book chapters, deepen the understanding of theoretical knowledge for the knowledge points learned today, and practice all the actual combat in the book. Generally, the course will be equipped with today's homework, and all the homework should be completed independently. If you can persist in studying every day, this process will last about four to five months. The length of the cycle depends on your learning ability and how much time you can spend every day. In the end, you must master the main technical points. Whether you can succeed in the end depends on whether you can survive the various difficulties you encounter in the process, solve each difficulty, and get a high salary.
Here are two ways to quickly solve the problem:
Baidu & Google
As a network security learner, you must use a good search engine at the beginning. Problems have been encountered by seniors. Many problems can be found by searching on Baidu, and you will find the answers you want. Try to solve problems independently, and gradually form a habit. After a long time, your ability to solve problems will improve rapidly. .
Ask the boss
Although Baidu has huge data, there are some problems that Baidu cannot solve. At this time, we must seek a more intelligent weapon, that is, "people". If you have a friend doing development around you, you can send your questions to your friends and classmates, and ask him to answer you, or a teacher, which will greatly improve our problem-solving efficiency.

Summarize
The above are some of my analysis of network security learning and research on the learning route. I hope it will be of some help and inspiration to you.