learning target:
1. Master the basic configuration of Layer 2 and Layer 3 networks
2. Master the basic configuration of ACL
3. Master the use of ACL policies
Learning Content:
1. What is ACL?
First of all, let's understand ACL. ACL is an access control list, so what does it do?
(ACL) access control list is an access control technology based on packet filtering, which can filter data packets on the interface according to the set conditions, allowing them to pass or discard.
Access control lists are widely used in routers and Layer 3 switches. With the help of access control lists, users' access to the network can be effectively controlled, thereby ensuring network security to the greatest extent.
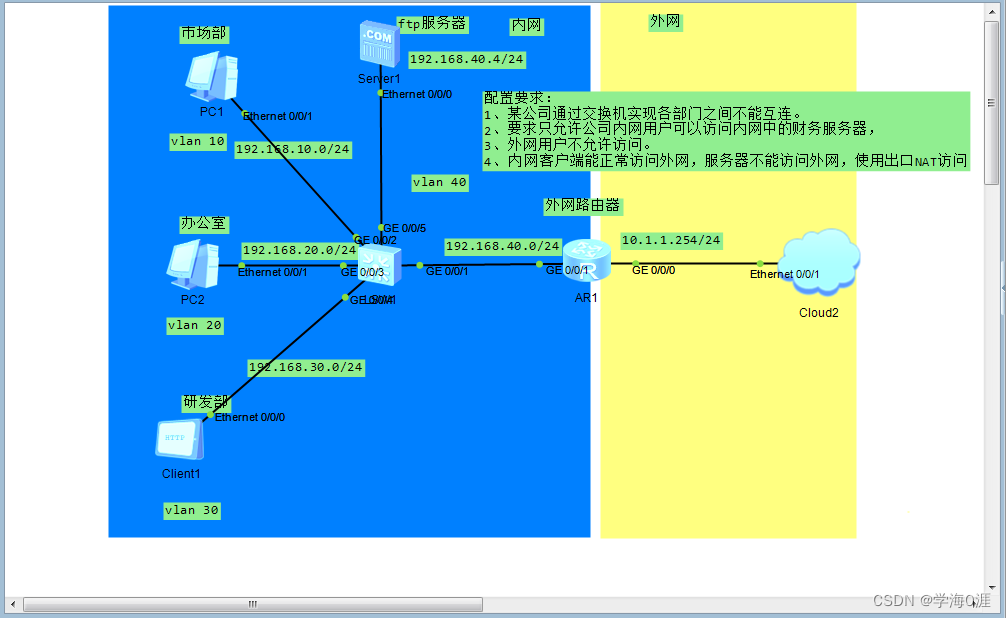
Configuration requirements:
1. A company realizes that various departments cannot be interconnected through switches.
2. It is required that only users of the company's intranet can access the financial server in the intranet.
3. Users of the external network are not allowed to access.
4. The intranet client can access the external network normally, but the server cannot access the external network. Use egress NAT to access
Note: The external network uses the virtual network card address of the local brain.
Topology:
Core switch configuration:
基本配置:
sy
sys SW1
v b 10 20 30 40
dhcp en
int v 10
ip add 192.168.10.1 24
dhcp sel int
int v 20
ip add 192.168.20.1 24
dhcp sel int
int v 30
ip add 192.168.30.1 24
int v 40
ip add 192.168.40.1 24
int g0/0/2
po link-type access
po de v 10
int g0/0/3
po link-type ac
po de v 20
int g0/0/4
po link-type ac
po de v 30
int g0/0/5
po link-type ac
po de v 40
int g0/0/1
po link-type ac
po de v 40
静态路由:
ip route-s 0.0.0.0 0 192.168.40.2
ACL访问列表(服务器端口)
1、创建配置访问服务器ACL规则:
acl number 3000
rule 5 permit ip source 192.168.10.0 0.0.0.255 destination 192.168.40.4 0
rule 10 permit ip source 192.168.20.0 0.0.0.255 destination 192.168.40.4 0
rule 15 permit ip source 192.168.30.0 0.0.0.255 destination 192.168.40.4 0
rule 100 deny ip destination 192.168.40.4 0
2、配置流分类:
traffic classifier wu_1
if-match acl 3000
3、配置流行为:
traffic behavior wu_2
permit
4、配置流策略:
traffic policy wu_3
classifier wu_1 behavior wu_2
5、应用流策略:
int g0/0/5
traffic-policy wu_3 outbound
ACL访问列表(终端端口)
1、创建配置各终端ACL互访策略:
acl 3001
acl number 3001
rule 5 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.20.0 0.0.0.255
rule 10 deny ip source 192.168.10.0 0.0.0.255 destination 192.168.30.0 0.0.0.25
5
rule 15 deny ip source 192.168.20.0 0.0.0.255 destination 192.168.30.0 0.0.0.25
5
rule 20 deny ip source 192.168.20.0 0.0.0.255 destination 192.168.100.0 0.0.0.2
55
2、创建流分类:
traffic classifier vlan_1
if-match acl 3001
3、创建流行为:
traffic behavior vlan_2
deny
4、创建流策略:
traffic policy vlan_3
classifier vlan_1 behavior vlan_2
5、应用流策略:
int g0/0/2
traffic-policy vlan_3 outbound
traffic-policy vlan_3 inbound
int g0/0/3
traffic-policy vlan_3 outbound
traffic-policy vlan_3 inbound
int g0/0/4
traffic-policy vlan_3 outbound
traffic-policy vlan_3 inbound
终端在进出方向都不能ACL3001策略流通,即不能访问其他业务部门网关
Egress router configuration:
基本配置:
sy
sys R1
int g0/0/1
ip add 192.168.40.2 24
int g0/0/0
ip add 10.1.1.254 24
nat outbound 2000 出口网络NAT从源地址转换
到各终端回城路由及连接到虚拟网卡的缺省路由
ip route-s 192.168.10.0 24 192.168.40.1
ip route-s 192.168.20.0 24 192.168.40.1
ip route-s 192.168.30.0 24 192.168.40.1
ip route-s 0.0.0.0 0 10.1.1.1
配置nat基本策略
acl number 2000
rule 5 permit source 192.168.10.0 0.0.0.255
rule 10 permit source 192.168.20.0 0.0.0.255
rule 15 permit source 192.168.30.0 0.0.0.255
rule 20 permit source 192.168.100.0 0.0.0.255
rule 100 denyTest device connectivity:
1. Basic configuration of terminal and FTP server




2. Mutual visits between terminals: (no connection)




3. Terminal access server and external network: (communication)




3: The server accesses the external network (no connection)

To sum up, it can be seen that ACL can precisely control the access control of each port and each VLAN, which can greatly improve the security of the device and prevent external network attacks and access to unplanned addresses in the internal network.