Write directory title here
1. Jenkins user management
Jenkins is a multi-user system.
Jenkins can use other plug-ins to allow different users to access different functions of the system.
Users can register or administrators can add, delete, modify and check
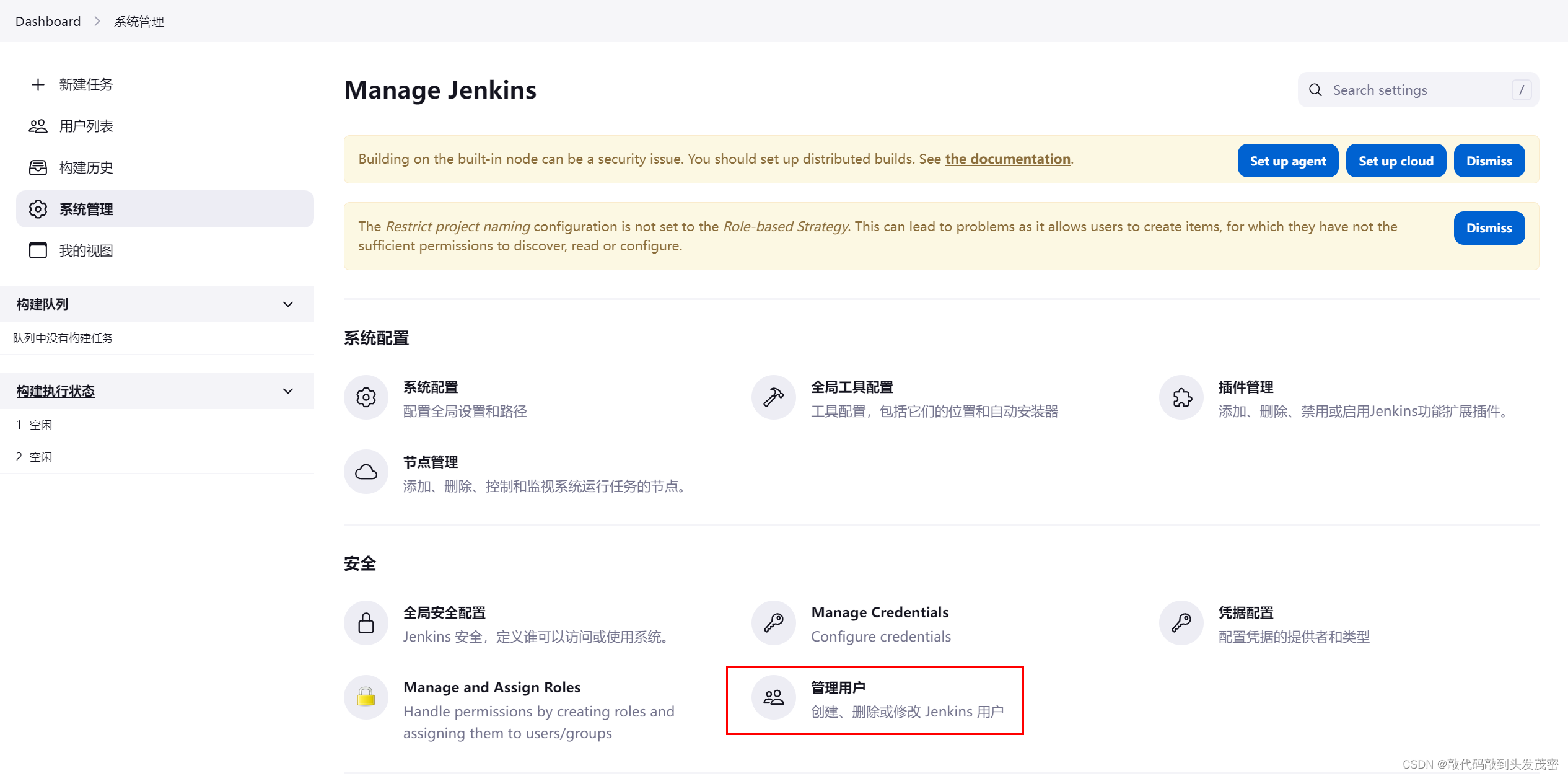
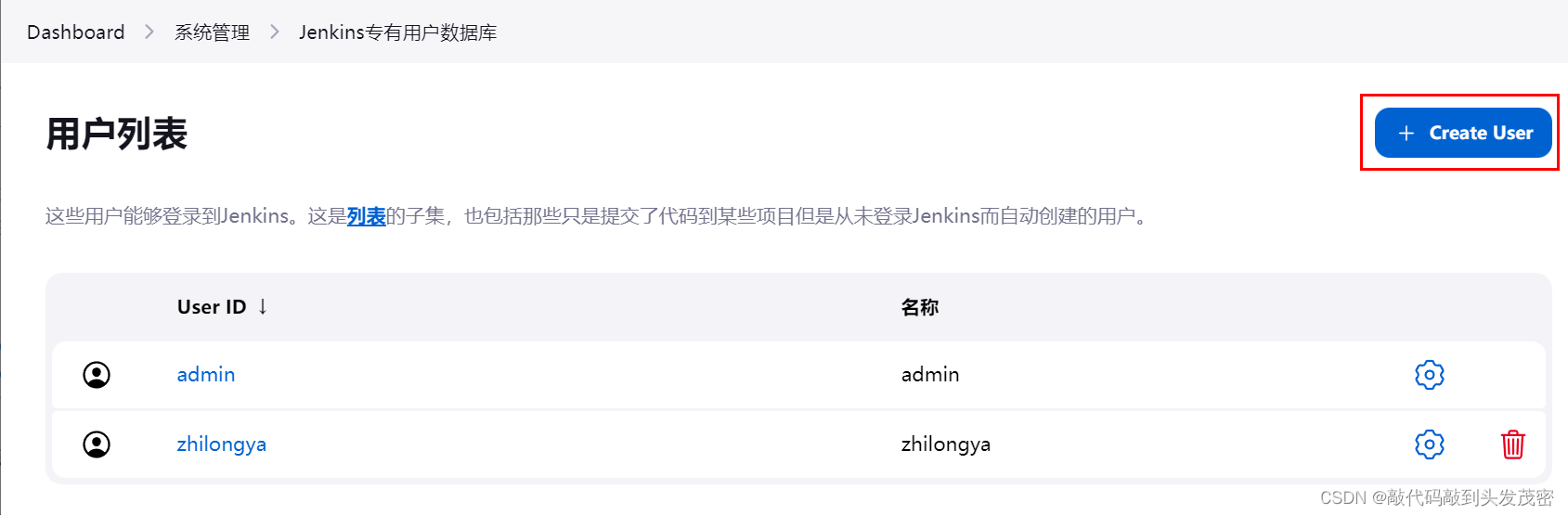
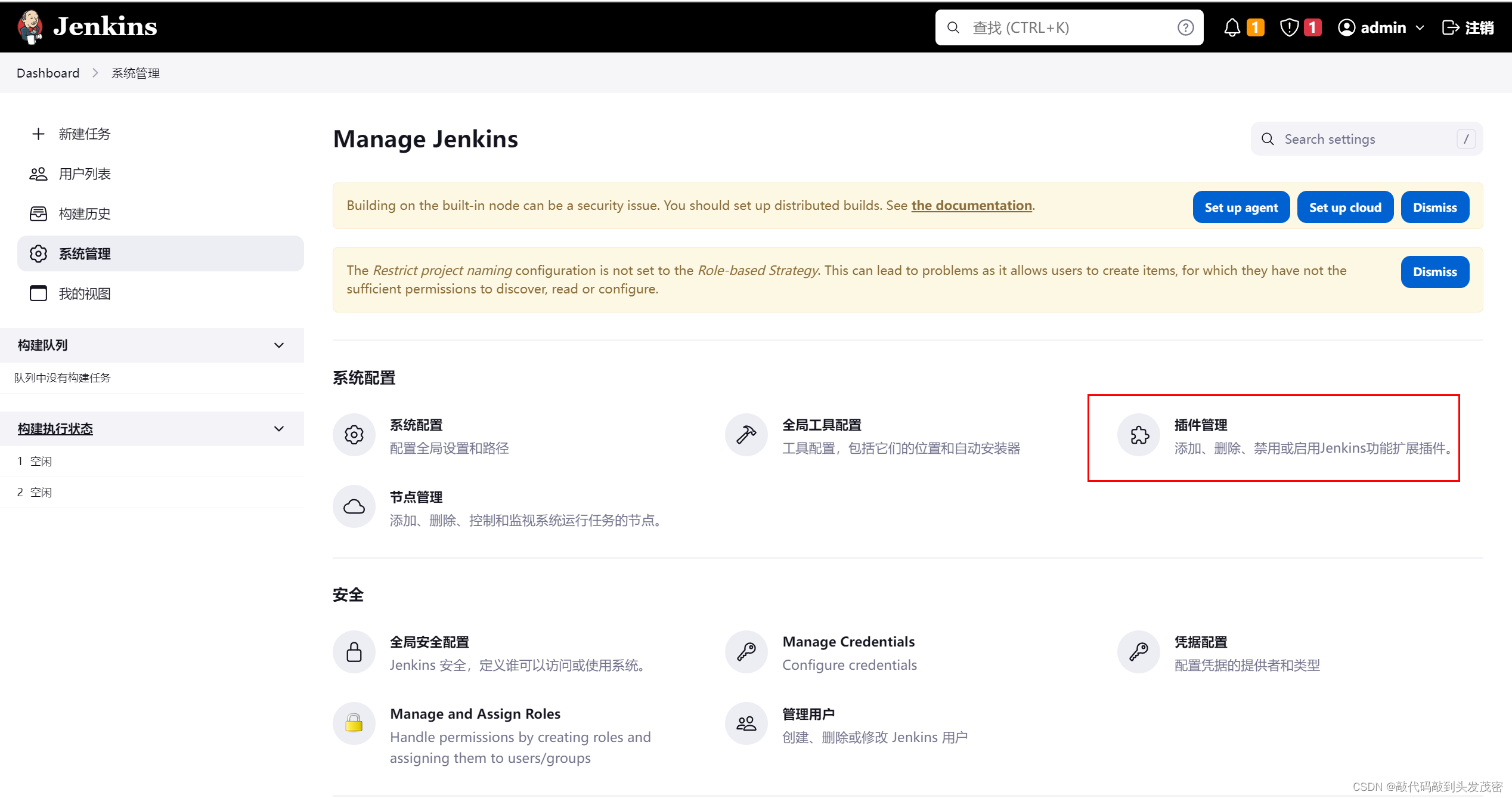
1. Enter the system management interface
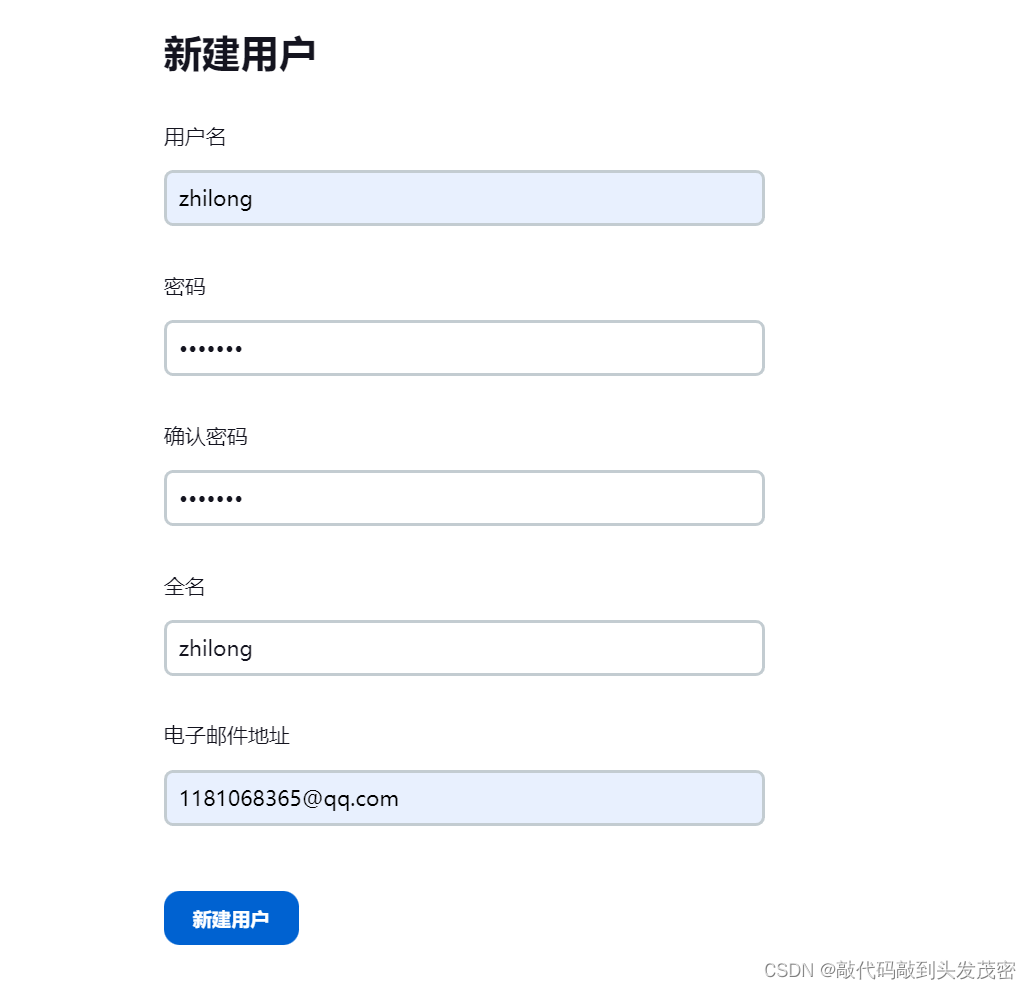
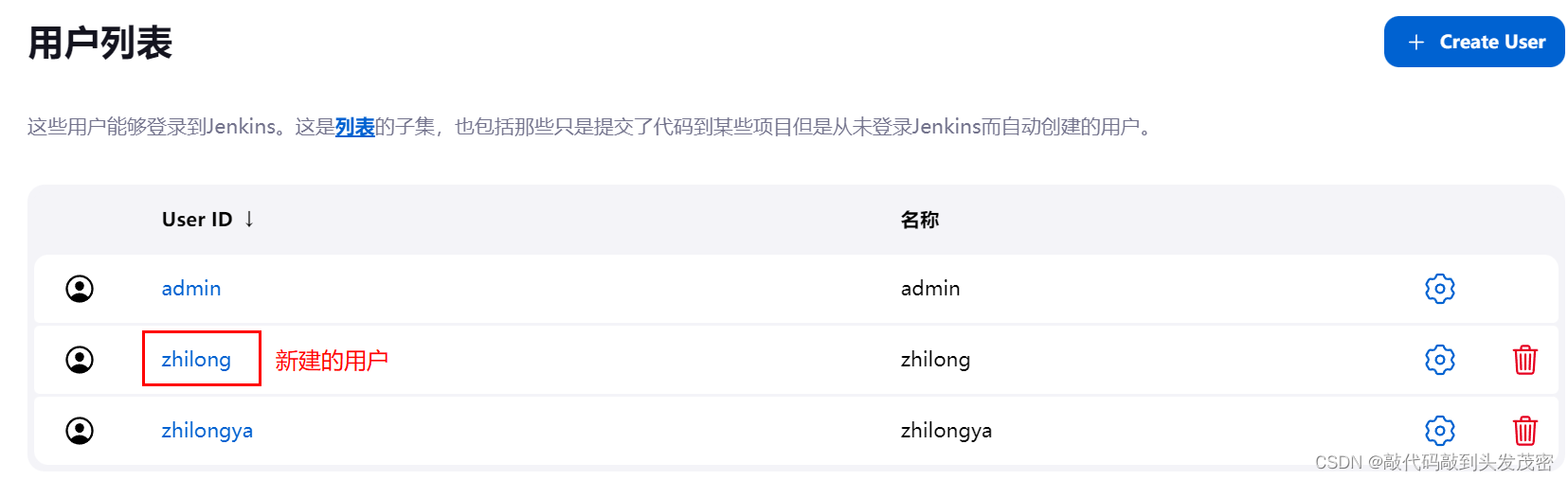
2. Create a user
3. Edit user information
4. Edit user information
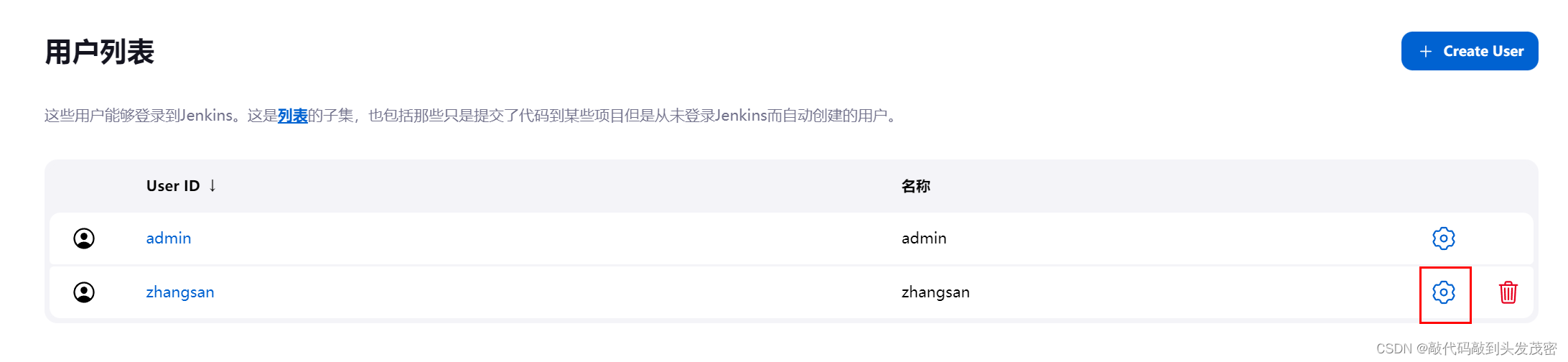
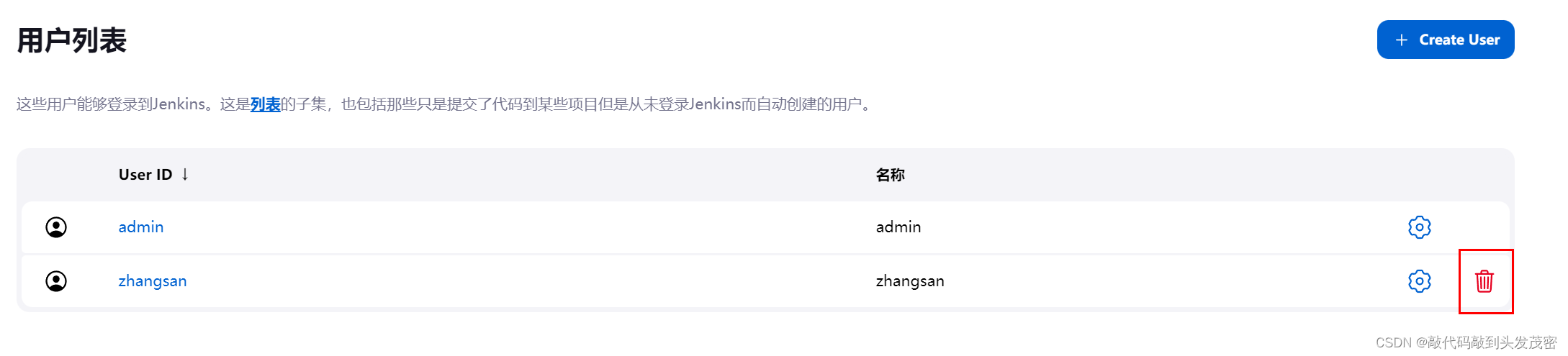
5. Delete user information
2. Jenkins authorization policy configuration
1. Authorization policy plugin
Different users have different requirements for system functions
. For safety considerations, key and important system functions need to be restricted from the use of some users
. For convenience considerations, system functions need to be customized according to different users.
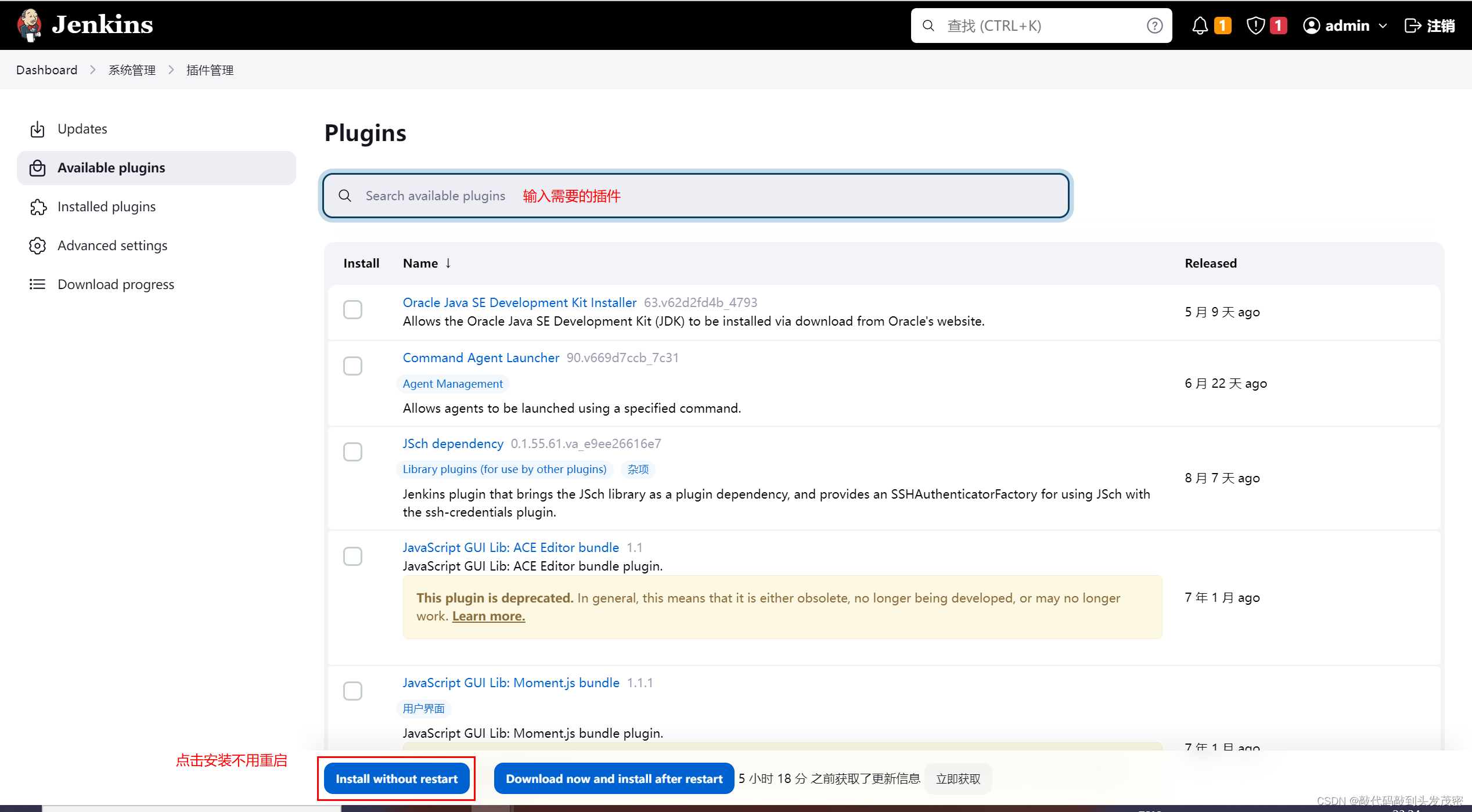
2. Install the plug-in: Role-based Authorization Strategy
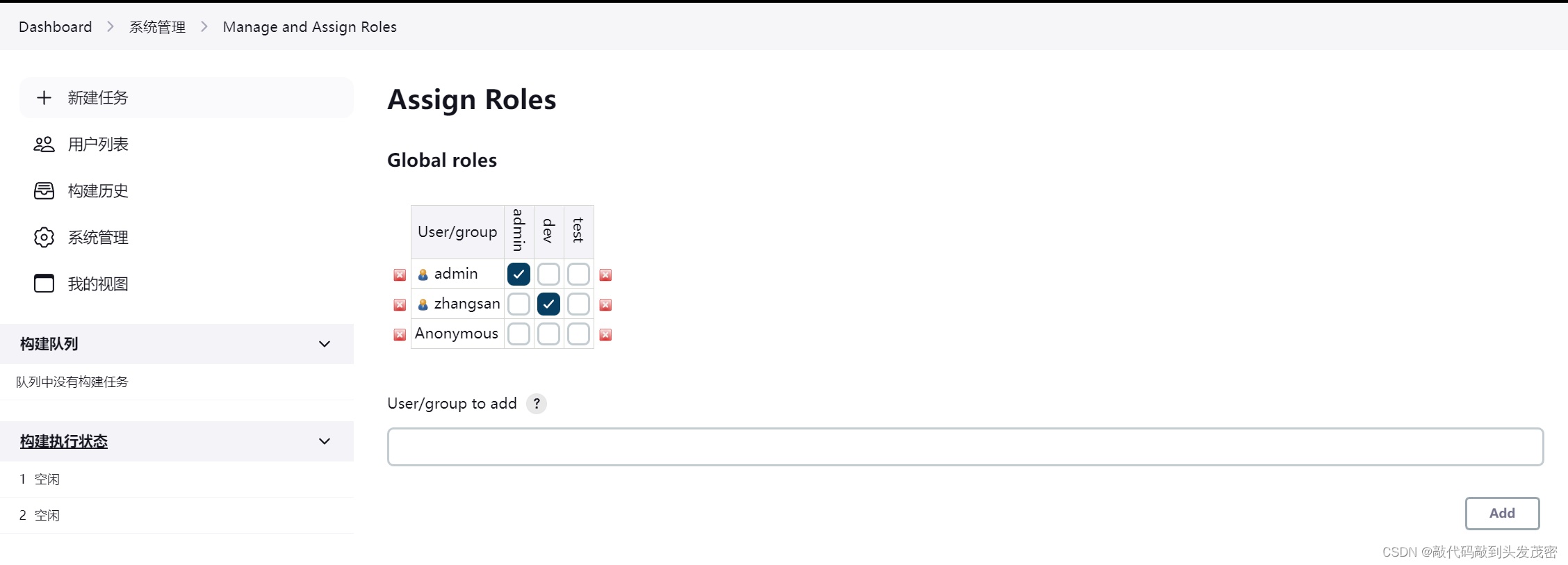
3. Management roles
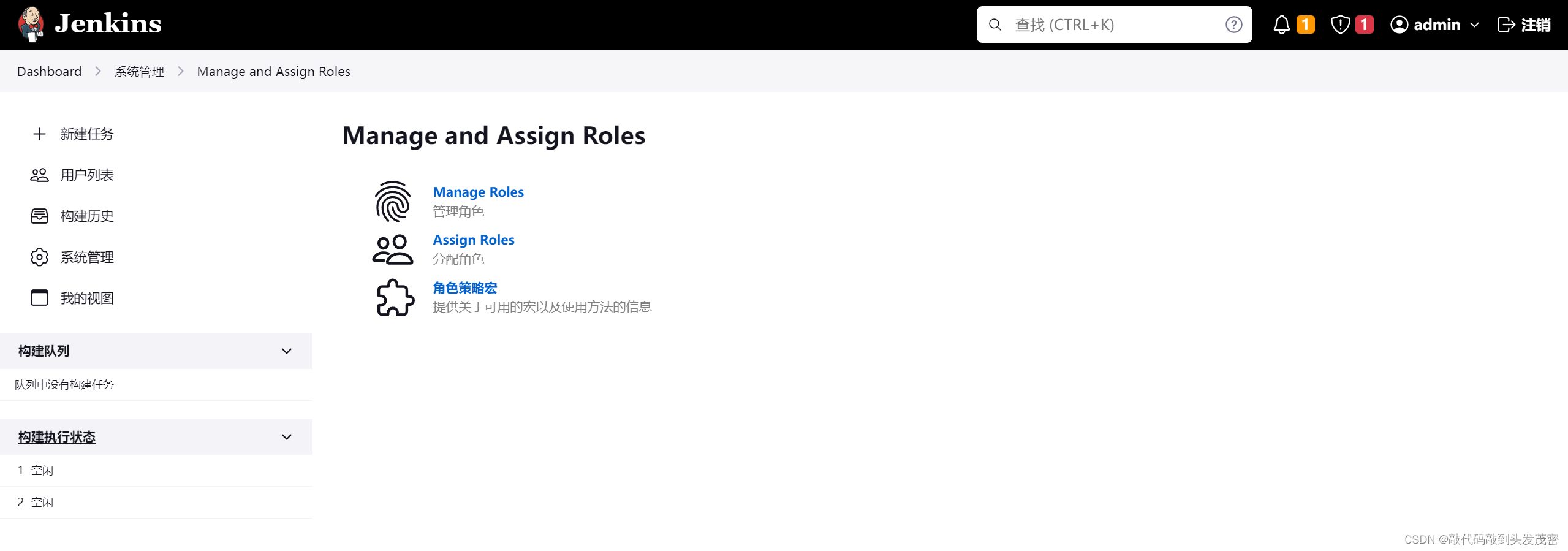
a. Global roles
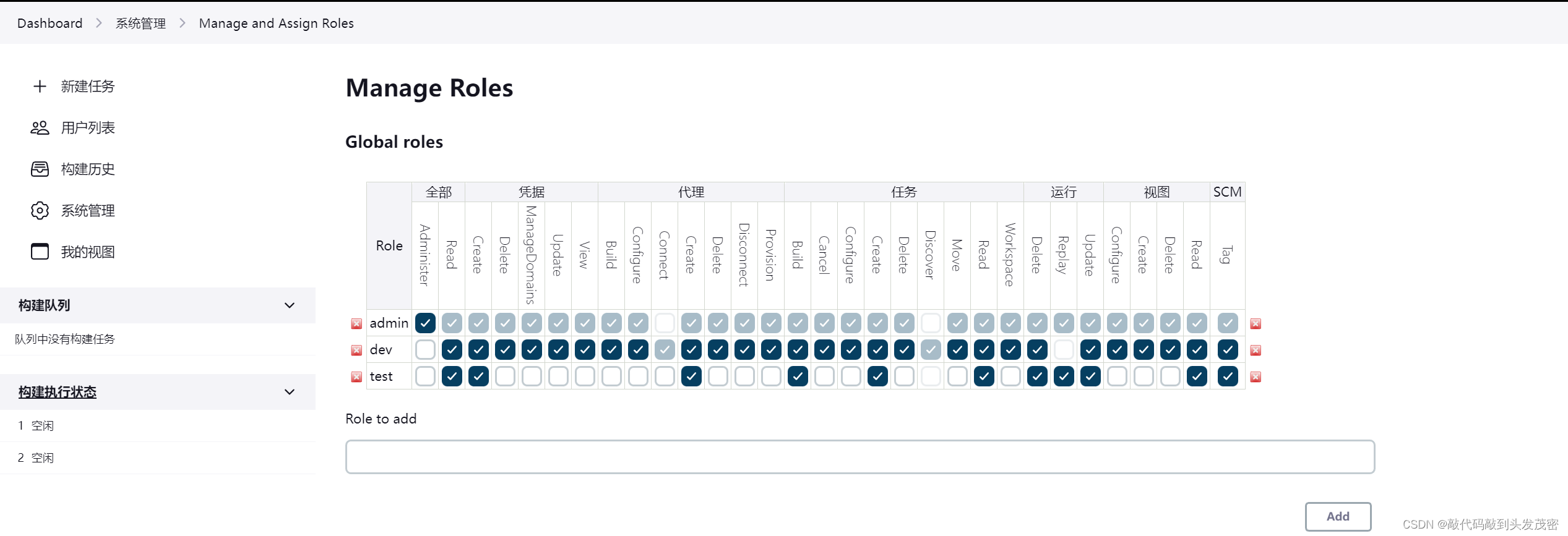
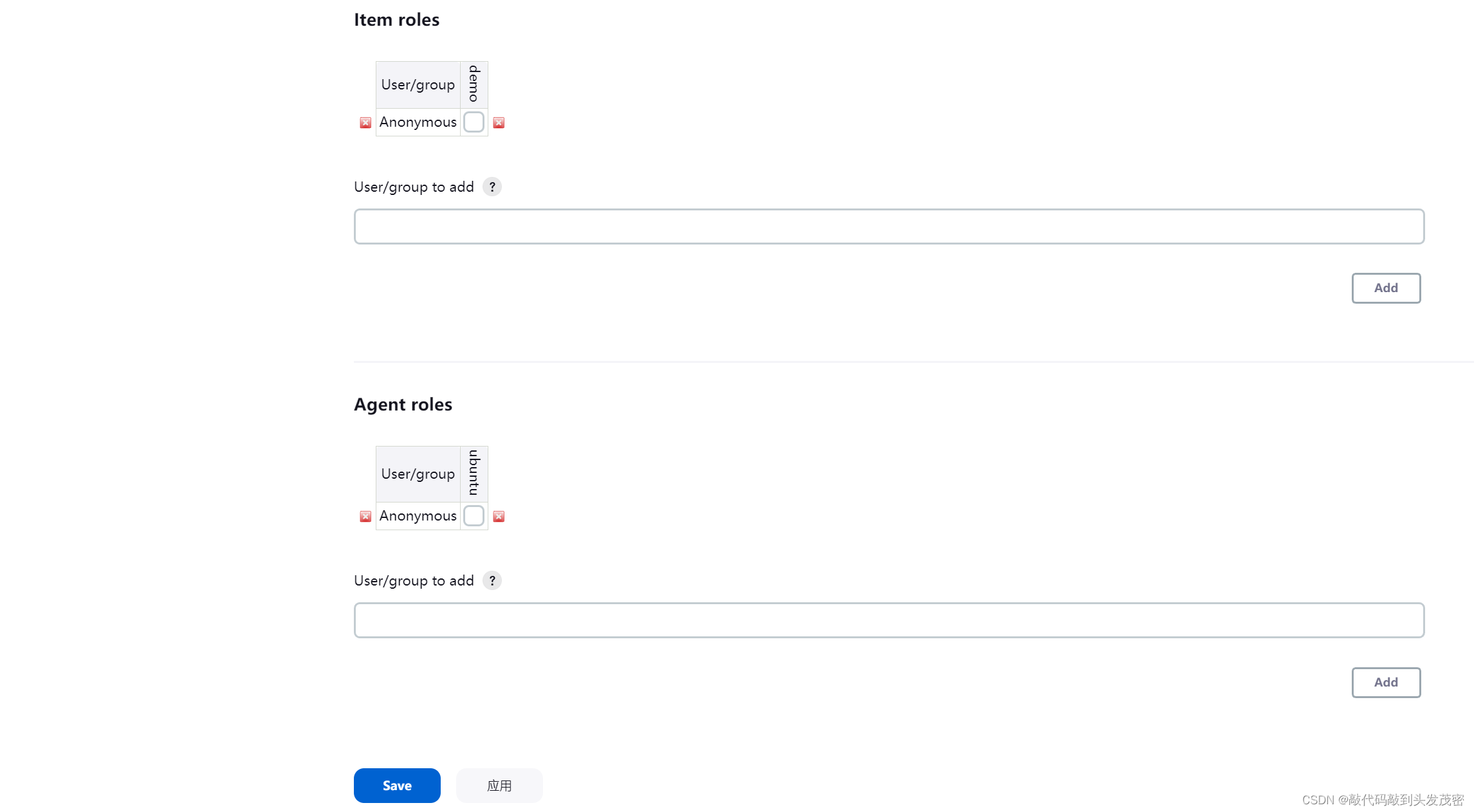
b. Item roles
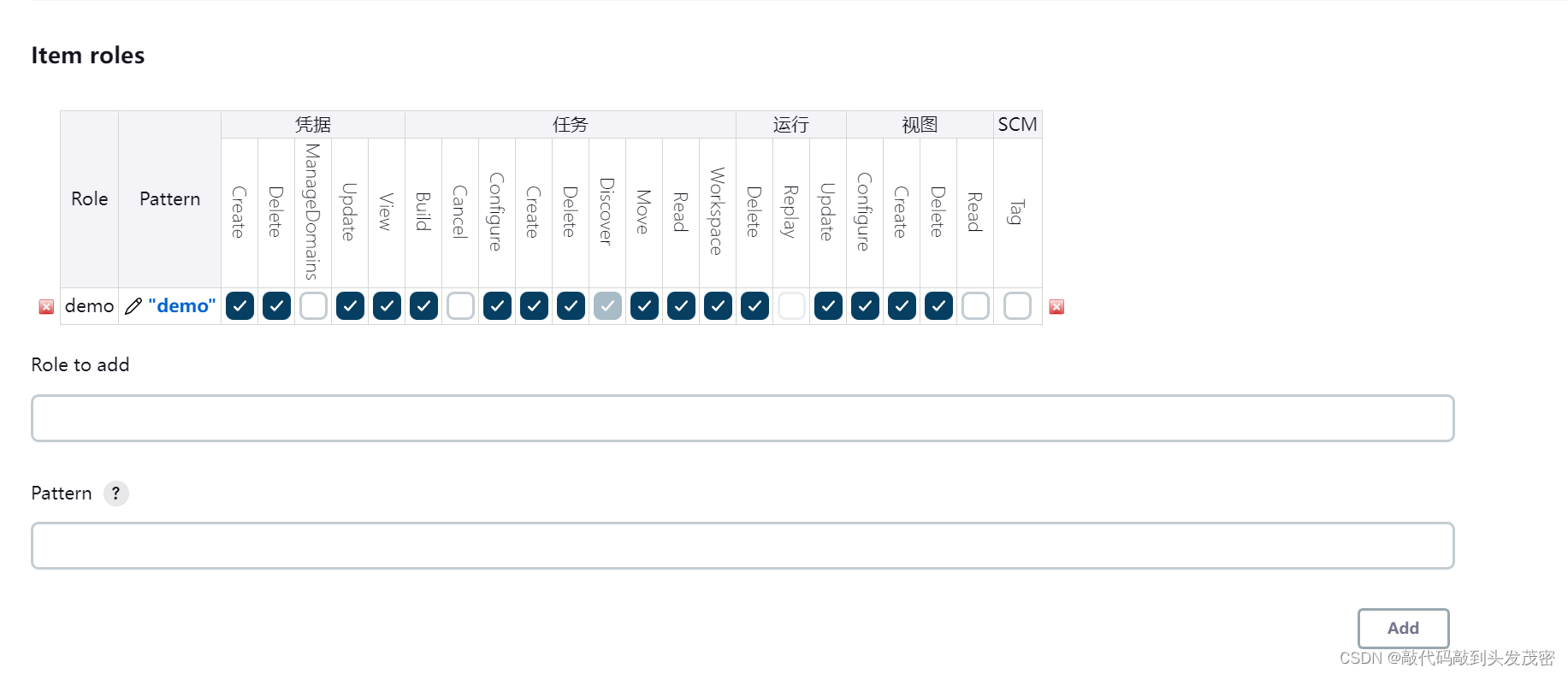
c. Node roles Node roles
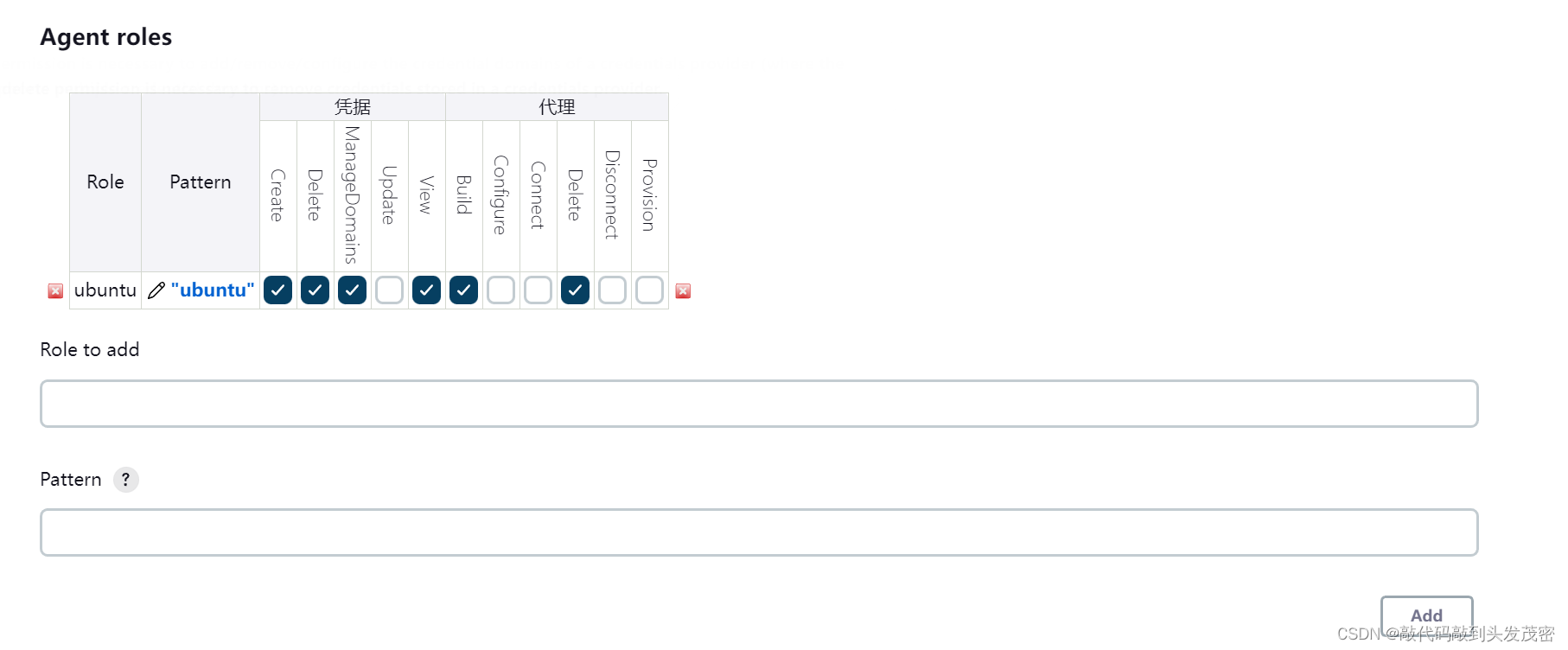
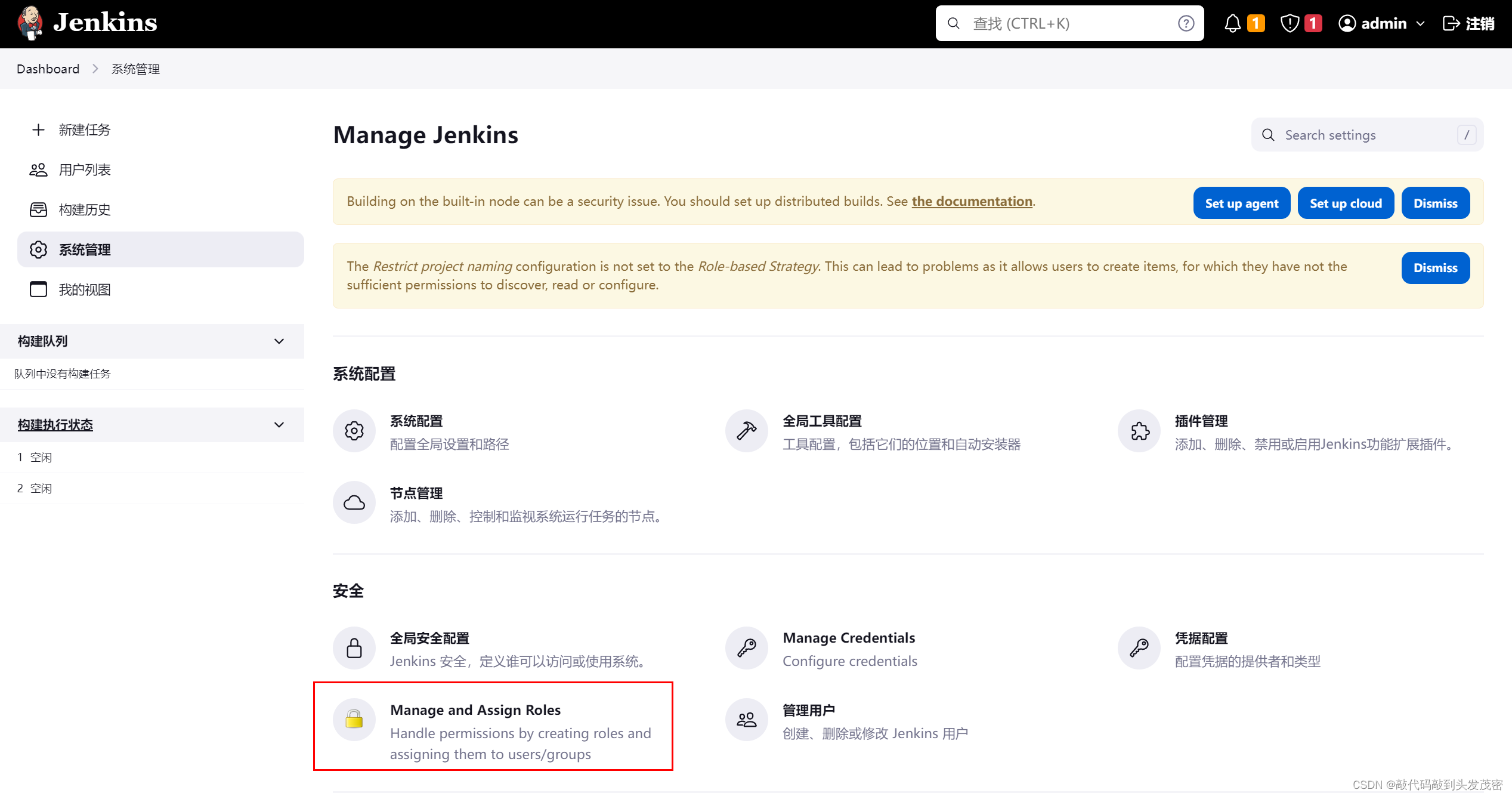
4. Assign roles
3. Jenkins security configuration management
1. Enter the system management interface
2. Introduction to security configuration
Jenkins has good scalability, such as remote execution, interface calls, etc., but it needs to consider network security factors, so Jenkins configures these functions and sets them on demand.
3. Detailed security configuration options
Configuration items:
Authentication
Token Formatter Proxy
Cross
Site Request Forgery Protection (CSRF)
Hidden Security Warning
API Token
SSH Server
Authentication
Don't remember me: If checked, the check box to keep logged in will not appear on the login page
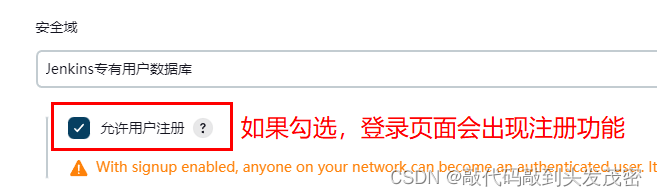
Security DomainJenkins proprietary user database
When the number of users is small, it is not recommended to enable this function, and the administrator can directly create users and assign permissions.
Servlet container proxy
None
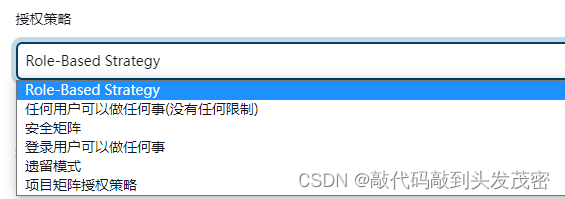
authorization policy
Any user can do anything (no restrictions)
logged in users can do anything
Legacy Mode
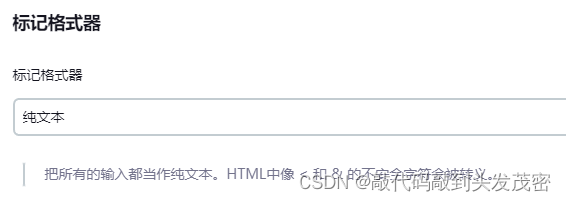
markup formatter
Plain Text
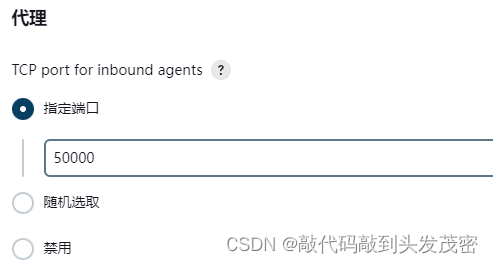
acting
proxy TCP portDesignated port (50000): Port 50000 opened by jenkins to the outside world,
randomly selected
, disabled
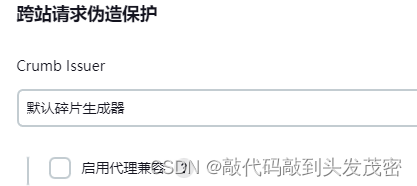
Cross Site Request Forgery Protection
Crumb Issuer: Use the default debris generator by default to
enable proxy compatibility
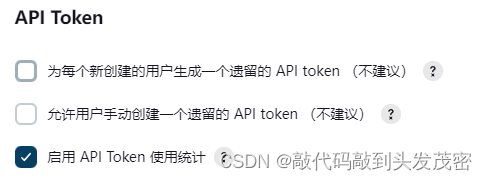
API Token
Generate a legacy API token for each newly created user (not recommended)
Allow users to manually create a legacy API token (not recommended)
Enable API Token usage statistics (recommended)
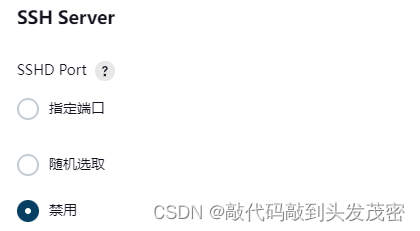
SSH Server
Specified Port
Randomly Selected
Disabled