P2P network:
Intel: Sharing of computer resources and information through direct exchange between systems
IBM: Consists of a number of interconnected and collaborative computers and has one of the following characteristics: the system depends on the active cooperation of edge devices; each member acts as a client and a server at the same time role; users of system applications can be aware of each other's existence and form a virtual or real group
Nodes are equal to each other, both as providers of services and resources, and as acquirers of services and resources
The blockchain relies on
the scalability and robustness of the P2P network: all peer nodes in the P2P network can provide resources such as bandwidth, storage space, and computing power. With the addition of more nodes, the overall resources and service capabilities of the system will also increase. are expanded synchronously.
Load balancing: The resources of the P2P network are distributed on multiple nodes, which can realize the load balancing of the network.
Decentralization: In the P2P network of the blockchain system, nodes are the sender and receiver of information, and they jointly maintain the blockchain.
4 topological forms:
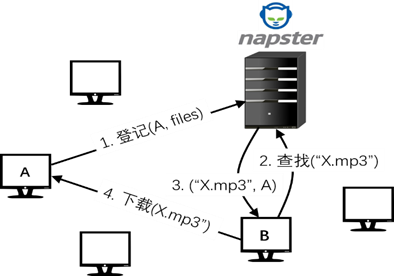
1. Centralized topology
Consists of a central index server and multiple client nodes, not a pure P2P network. The
central index server is used to store the address information of access nodes and provide address index services to other nodes
Features:
The separation of file query and file transfer is realized, and the maintenance is simple.
Once the central index server fails, the entire network will not work properly
When a user needs to search for a certain music file, he first needs to search the music file through the central index server to obtain the information of other users who own the music file, and then he can directly connect to the resource owner according to the search result to realize file transfer and shared.
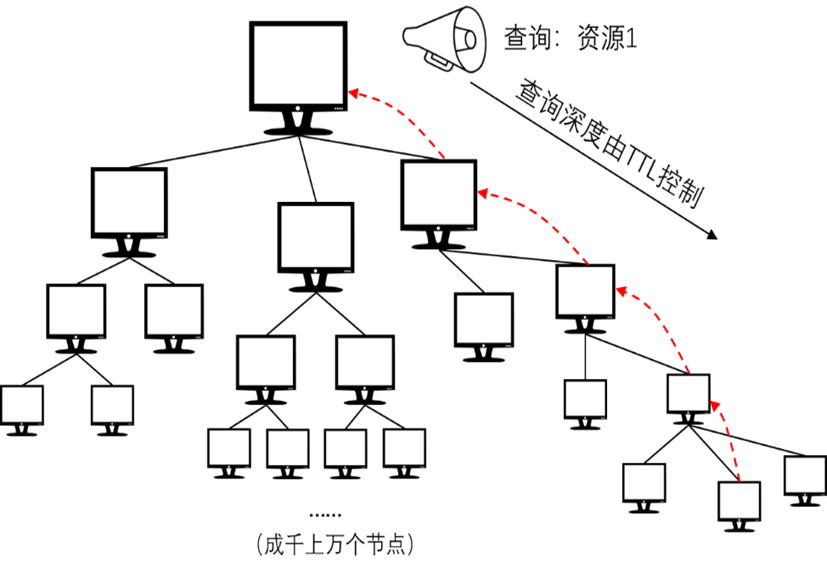
2. Fully distributed unstructured topology
does not use a central index server, and its nodes have true peer-to-peer relationship
flooding (Flooding) data broadcasting, that is, nodes will forward received messages to neighbor nodes until all nodes have received The message or the depth of message propagation reaches a certain limit.
Features:
There may be a broadcast storm
to achieve fast message dissemination and resource search
First, a node will send a query request to its neighbors according to the resource key. If its neighbor has this resource, it will establish a connection with the node that initiated the query request to transmit the resource; otherwise, the neighbor will continue to spread to its neighbors. The query requests until such a resource is found.
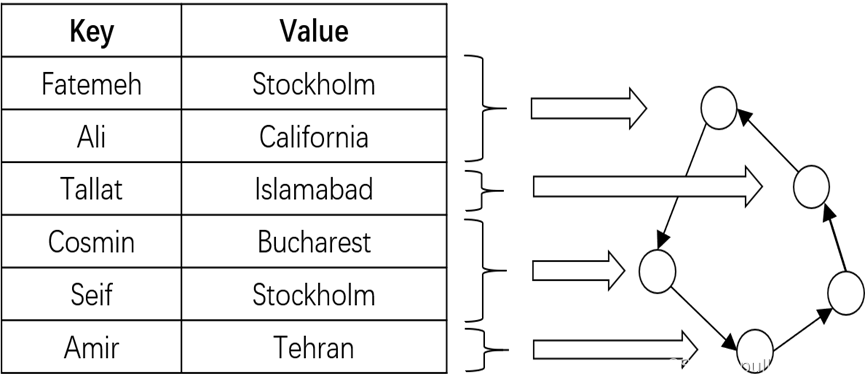
3. Fully distributed structured topology
Distributed Hash Tables (DHT for short) are used to realize the addressing and storage of the entire network, thereby structured address management.
The distributed hash table divides the hash table storing all resource information in the network into many discontinuous small blocks, which are stored scatteredly on multiple nodes.
Features
Complicated maintenance mechanism
Good robustness, scalability and dynamic adaptability
When a node needs to request a certain resource, it first finds the node where the hash table containing the corresponding resource keywords is located, obtains the address information corresponding to the resource from the node, and finally connects the corresponding node according to the address information to realize resource request and transmission .
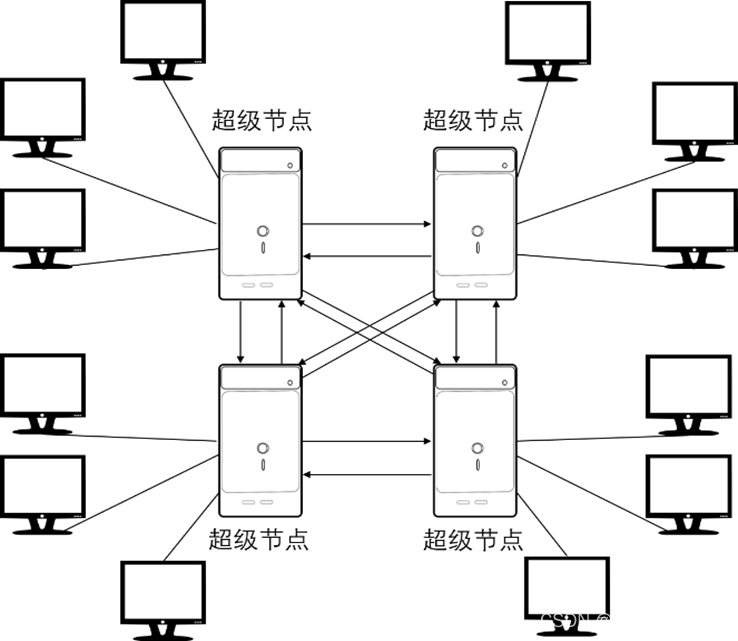
4. Semi-distributed topology
The machines with higher performance in the network are used as super nodes. Each super node stores the file information of other nodes in the system, and performs maintenance of addresses and file indexes of these nodes.
A high-speed forwarding layer is formed between the super nodes, and an autonomous cluster is formed with the connected ordinary nodes, and a central topology P2P network is used in the cluster.
Features Eliminate the hidden danger of network congestion, and have certain advantages in performance and scalability High dependence on super nodes
For the resource search on the semi-distributed topology, it will first be carried out in the cluster where the ordinary node is located. If the super node in the cluster finds that the resource is on the leaf node adjacent to the super node, the super node will forward the query request to The corresponding node; otherwise, limited flooding will be performed between super nodes, and the query of this file will continue via other super nodes.