1.1 The network protocol
enables multiple computers to be connected through a computer network. Computers in the same network need to abide by certain rules when connecting and communicating, just like a car driving on the road must obey the traffic rules. In computer networks, these rules of connection and communication are called network communication protocols, which uniformly stipulate the data transmission format, transmission rate, transmission steps, etc., and both parties must abide by them to complete data exchange.
There are many kinds of network communication protocols, the most widely used currently is TCP/IP protocol (Transmission Control Protocol/Internet Protocol/Internet Protocol), which is a protocol including TCP protocol and IP protocol, UDP (User Datagram Protocol) ) protocol and some other protocol groups, first understand the hierarchy of the TCP/IP protocol group before learning specific protocols.
During data transmission, the sent data is required to be exactly the same as the received data. At this time, it is necessary to add a lot of information to the original data to ensure that the data format is completely consistent during the transmission process. The hierarchical structure of the TCP/IP protocol is relatively simple and is divided into four layers, as shown in the figure. 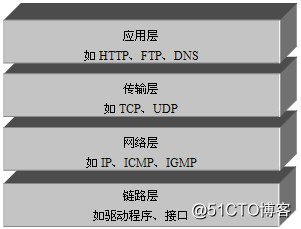
Figure 1-1 TCP/IP network model
In the above figure, the four layers in the TCP/IP protocol are the application layer, the transport layer, the network layer and the link layer. Each layer is responsible for different communication functions. layers are explained in detail.
Link layer: The link layer is used to define a physical transmission channel, usually a driver protocol for some network connection devices, such as drivers for optical fibers and network cables.
Network layer: The network layer is the core of the entire TCP/IP protocol. It is mainly used to group the transmitted data and send the grouped data to the target computer or network.
Transport layer: It mainly enables network programs to communicate. During network communication, TCP protocol or UDP protocol can be used.
Application layer: mainly responsible for the protocols of the application, such as HTTP protocol, FTP protocol, etc.
1.2 IP address and port number
In order to enable the computers in the network to communicate, each computer must be assigned an identification number, which is used to designate the computer that receives data or the computer that sends data.
In the TCP/IP protocol, this identification number is the IP address, which can uniquely identify a computer. Currently, the widely used version of the IP address is IPv4, which is represented by a 4-byte binary number, such as: 00001010000000000000000000000001 . Since the IP address expressed in binary form is very inconvenient to memorize and process, the IP address is usually written in decimal form, each byte is represented by a decimal number (0-255), and the numbers are separated by a symbol ".", such as " 192.168.1.100".
With the continuous expansion of the scale of computer networks, the demand for IP addresses is also increasing. IPV4, an IP address represented by 4 bytes, is facing exhaustion, so IPv6 came into being. IPv6 uses 16 bytes to represent IP address, the address capacity it has is about 8 × 1028 times that of IPv4, reaching 2128 (including all zeros), which solves the problem of insufficient network address resources.
You can connect to a specified computer through an IP address, but if you want to access an application on the target computer, you also need to specify a port number. In a computer, different applications are distinguished by port numbers. The port number is represented by two bytes (16-bit binary number), and its value range is 0~65535. Among them, the port number between 0~1023 is used for some well-known network services and applications. Common applications need to use port numbers above 1024 to avoid port numbers being occupied by another application or service.
Next, a legend is used to describe the role of IP addresses and port numbers, as shown in the following figure. 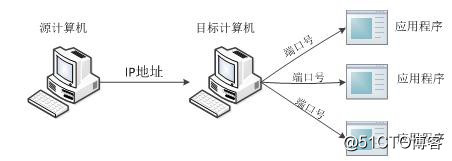
As can be clearly seen from the above figure, one computer in the network can access another computer through the IP address, and access an application in the target computer through the port number.
1.3 InetAddress
Knowing the role of IP addresses, let's look at the InetAdderss class provided in JDK, which is used to encapsulate an IP address and provides a series of methods related to IP addresses. The following table lists some of the InetAddress classes. common method.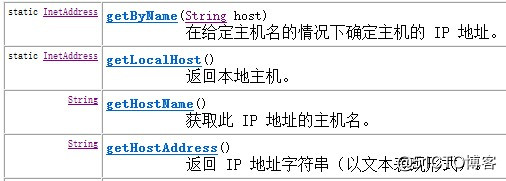
1.3.1 Case code 1:
package com.itheima_01;
import java.net.InetAddress;
import java.net.UnknownHostException;
/*
* InetAddress:此类表示互联网协议 (IP) 地址。
*
*/
public class InetAddressDemo {
public static void main(String[] args) throws UnknownHostException {
//static InetAddress getByName(String host)
//InetAddress address = InetAddress.getByName("itheima");
InetAddress address = InetAddress.getByName("192.168.1.107");//ip地址是唯一的
//System.out.println(address);//itheima/192.168.1.107 ipconfig
String hostAddress = address.getHostAddress();//192.168.1.107 返回IP地址
String hostName = address.getHostName();//itheima 返回主机名
System.out.println(hostAddress);
System.out.println(hostName);
}
}