Configuring an IPSec VPN on an ASA firewall is not very different from a router, and the principles are the same. Refer to the previous article for the working principle of VPN, and will not repeat them here.
Experimental case
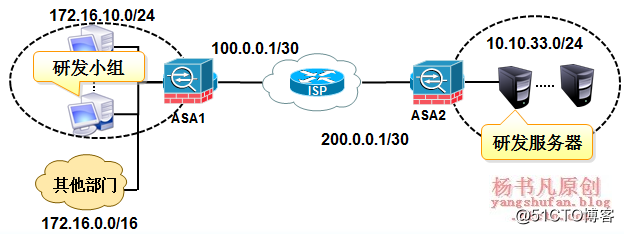
In order to reduce personnel costs, a software development company has established branch companies in small and medium-sized cities. However, the data uploaded by the branch companies to the head office is generally the key business data of software development. If it is stolen, it may bring unpredictable losses to the company. As the network administrator of this branch company, the following design requirements are put forward to the network.
Description of Requirement:
1) The development project team can access the R&D server of the head office through VPN, but cannot access the Internet
2) Other clients of the branch can access the Internet
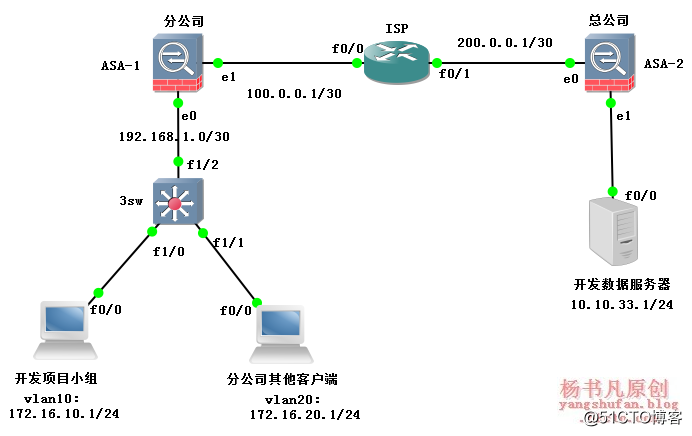
The experimental topology on GNS3 is as follows:
The specific configuration is as follows:
1. Configuration on 3sw
3sw#vlan database #Create VLAN 3sw(vlan)#vlan 10 3sw(vlan)#vlan 20 3sw(vlan)#exit 3sw#conf t 3sw(config)#int vlan 10 #Configure VLAN address 3sw(config-if)#ip add 172.16.10.254 255.255.255.0 3sw(config-if)#no sh 3sw(config-if)#int vlan 20 3sw(config-if)#ip add 172.16.20.254 255.255.255.0 3sw(config-if)#no sh 3sw(config-if)#int f1/0 3sw(config-if)#no switchport 3sw(config-if)#ip add 192.168.1.2 255.255.255.252 3sw(config)#int f1/1 3sw(config-if)#switchport access vlan 10 3sw(config-if)#int f1/2 3sw(config-if)#switchport access vlan 20 3sw(config-if)#exit 3sw(config)#ip route 0.0.0.0 0.0.0.0 192.168.1.1 #Configure routing
2. Configure on the branch ASA-1
ASA-1# conf t #Configure the interface address ASA-1(config)# int e0/0 ASA-1(config-if)# nameif inside ASA-1(config-if)# security-level 100 ASA-1(config-if)# ip add 192.168.1.1 255.255.255.252 ASA-1(config-if)# no sh ASA-1(config-if)# int e0/1 ASA-1(config-if)# nameif outside ASA-1(config-if)# security-level 0 ASA-1(config-if)# ip add 100.0.0.1 255.255.255.252 ASA-1(config-if)# no sh ASA-1(config)# route outside 0 0 100.0.0.2 #Configure route ASA-1(config)# route inside 172.16.0.0 255.255.0.0 192.168.1.2 ASA-1 (config) # nat-control # 配置 NAT ASA-1(config)# nat (inside) 1 0 0 ASA-1(config)# global (outside) 1 int ASA-1(config)# access-list nonat extended permit ip 172.16.10.0 255.255.255.0 10.10.33.0 255.255.255.0 ASA-1(config)# nat (inside) 0 access-list nonat #Configure NAT exemption ASA-1(config)# crypto isakmp enable outside #启用ISAKMP/IKE ASA-1(config)# crypto isakmp policy 1 #Configure ISAKMP policy ASA-1(config-isakmp-policy)# encryption aes #Configure encryption algorithm ASA-1(config-isakmp-policy)# hash sha #Configure digital signature ASA-1(config-isakmp-policy)# authentication pre-share #Use pre-shared key ASA-1(config-isakmp-policy)# group 1 #Specify DH key group
Note: There are two ways to configure the pre-shared key. The first configuration is the same as that of the router. The second is a new feature of version 7.0 and above. Generally, the tunnel group is used to configure the key in versions above 7.0.
The first configuration: the same as the router configuration
ASA-1(config)# crypto isakmp key vpn-key address 200.0.0.1
The second configuration: use the tunnel group configuration, the configuration is as follows
ASA-1# tunnel-group 200.0.0.1 type ipsec-l2l ASA-1(config)# tunnel-group 200.0.0.1 ipsec-attributes ASA-1(config-tunnel-ipsec)# pre-shared-key vpn-key
You can choose one of the pre-shared keys. The next configuration is as follows:
ASA-1(config)# access-list vpn extended permit ip 172.16.10.0 255.255.255.0 10.10.33.0 255.255.255.0 #ACL ASA-1(config)# crypto ipsec transform-set vpn-set esp-aes esp-sha-hmac #Configure IPSec transform set ASA-1(config)# crypto map vpn-map 1 match address vpn #应用ACL ASA-1(config)# crypto map vpn-map 1 set peer 200.0.0.1 #Configure IPSec peer device ASA-1(config)# crypto map vpn-map 1 set transform-set vpn-set #Apply IPSec transform set ASA-1(config)# crypto map vpn-map interface outside #map it to the interface
3. Configure on the ISP
ISP#conf t ISP(config)#int f0/0 ISP(config-if)#ip add 100.0.0.2 255.255.255.252 ISP(config-if)#no sh ISP(config-if)#int f0/1 ISP(config-if)#ip add 200.0.0.2 255.255.255.252 ISP(config-if)#no sh
4. Configure on the head office ASA-2
ASA-2 # conf t ASA-2(config)# int e0/0 ASA-2(config-if)# nameif outside ASA-2(config-if)# security-level 0 ASA-2(config-if)# ip add 200.0.0.1 255.255.255.252 ASA-2(config-if)# no sh ASA-2(config-if)# int e0/1 ASA-2(config-if)# nameif inside ASA-2(config-if)# security-level 100 ASA-2(config-if)# ip add 10.10.33.254 255.255.255.0 ASA-2(config-if)# no sh ASA-2(config)# route outside 0 0 200.0.0.2 ASA-2(config)# crypto isakmp enable outside ASA-2(config)# crypto isakmp policy 1 ASA-2(config-isakmp-policy)# encryption aes ASA-2(config-isakmp-policy)# hash sha ASA-2(config-isakmp-policy)# authentication pre-share ASA-2(config-isakmp-policy)# group 1 ASA-2(config)# crypto isakmp key vpn-key address 100.0.0.1 ASA-2(config)# access-list vpn extended permit ip 10.10.33.0 255.255.255.0 172.16.10.0 255.255.255.0 ASA-2(config)# crypto ipsec transform-set vpn-set esp-aes esp-sha-hmac ASA-2(config)# crypto map vpn-map 1 match address vpn ASA-2(config)# crypto map vpn-map 1 set peer 100.0.0.1 ASA-2(config)# crypto map vpn-map 1 set transform-set vpn-set ASA-2(config)# crypto map vpn-map interface outside
Difference Between Firewall and Router
Due to its own IOS, the firewall is different from the router in configuration commands, but it is not very obvious. Two aspects are highlighted here:
1. The difference between the default configuration
In the process of establishing a management connection, the cisco asa firewall and router use different parameters by default.
The parameters used by the Cisco asa firewall are as follows:
ASA-1(config)# show run crypto
The parameters used by the router are as follows:
Router#show crypto isakmp policy
The firewall does not support the show crypto isakmp policy command. To view the default parameters of the management connection, you need to enable the isakmp policy in the initial configuration, and then run the show run command to observe. Compared with the router, the default encryption algorithm becomes 3DES, the default DH group uses 2, the default device authentication method becomes the pre-shared key, and the default HASH algorithm and lifetime remain unchanged.
The ASA firewall adopts more secure default settings, which is a manifestation of the technological innovation of cisco's equipment. It should be noted that if the ipsec peer is dual-mode ASA firewall and cisco router, then the connection cannot be established using the default ISAKMP policy.
In addition, during the data connection establishment process, the ASA firewall only supports the ESP protocol. Therefore, if the router uses the AH protocol to implement the data authentication function, it will not be able to successfully establish a data connection with the ASA.
2. Whether IKE negotiation is enabled by default
By default, IKE negotiation is turned on in the router and turned off in the ASA firewall. Therefore, the command crypto isakmp enable outside must be used in the ASA firewall to enable IKE negotiation.
3. The introduction of tunnel group features
Strictly speaking, this is not a configuration difference between a firewall and a router. The new feature introduced by the firewall upgrade from version 6.x to version 7.0 is mainly used to simplify the configuration and management of ipsec sessions. In addition, the ASA firewall still supports the command to configure the shared secret key (crypto isakmp key key-string address peer-address) on the router.
4. The impact of interface security level on ipsec traffic.
Firewalls have a limitation that if traffic comes in from one interface, it cannot go out from a port of the same security level. That is, traffic cannot be transmitted between ports with a unified security level. This is a feature set mainly from the perspective of security, but it may have a certain impact on ipsec traffic.
If the ASA firewall is located at the central node of the network (such as the company headquarters), in order to achieve unified management of branch network traffic, it is required that the access traffic between branches must pass through the head office. This will cause the above situation to occur, resulting in the inability to communicate between the branches. Then you need to use the following command to achieve.
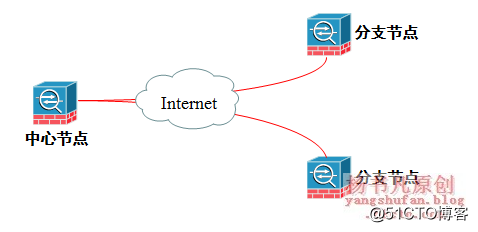
ASA-1(config)# same-security-traffic permit {intra-interface | inter-interface}
The difference between the last two parameters of the above command:
The Intra-interface parameter allows traffic to enter and leave the same interface, which is mostly used for central equipment in L2L sessions;
The inter-interface parameter allows traffic to enter and leave two different interfaces with the same security level, and is mostly used for Easy VPN gateways in remote access VPN sessions.