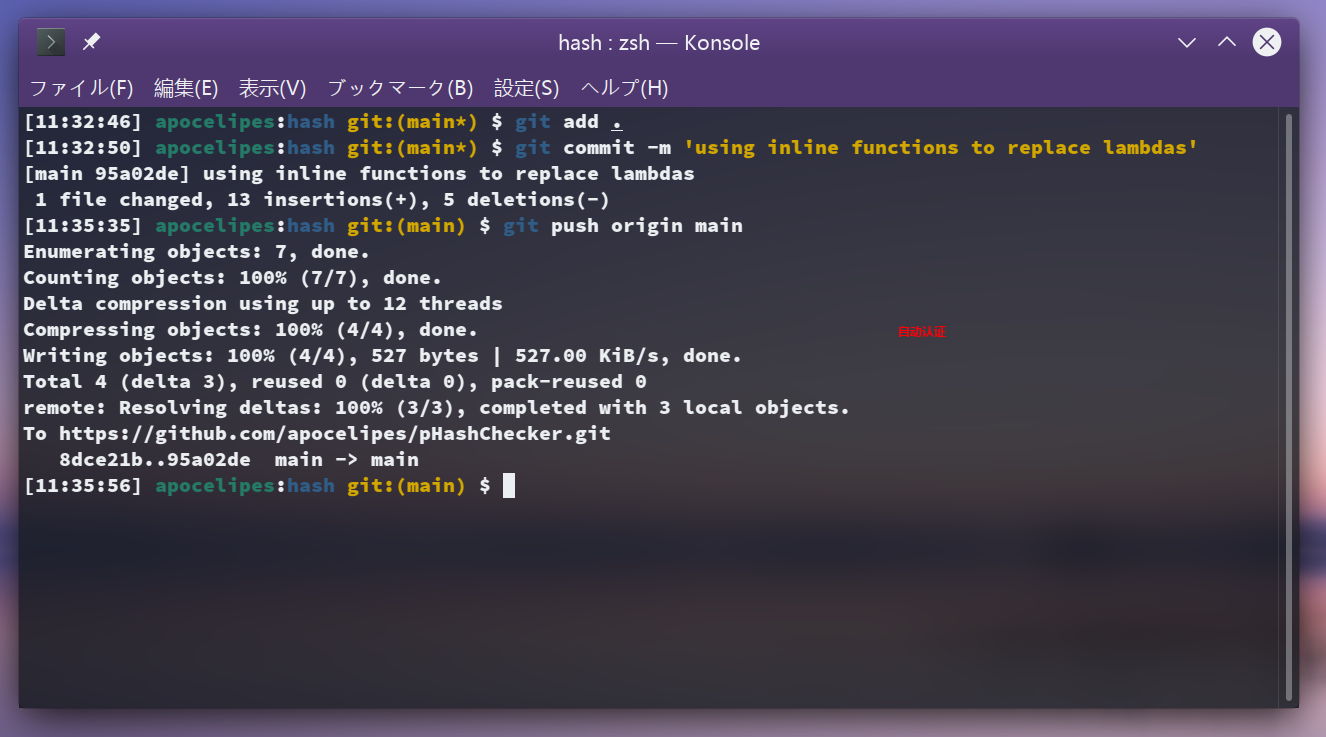
Record the automatic verification when configuring git to operate a remote warehouse, the effect is as follows:
This article describes the configuration under Linux. Credential storage and automatic verification are enabled by default on Windows (rely on wincred implementation, and GCM-Core will be used in the future ).
Ready to work
First, dbus or gnome-keyring (depending on dbus) needs to be installed on the Linux system. If possible, libsecret needs to be installed, which is a more modern library for credential management. Because we need to use dbus service to achieve credential storage:
# Ubuntu
sudo apt-get install libsecret-1-0 libsecret-1-dev gnome-keyring
# Arch Linux
sudo pacman -S libsecret gnome-keyring
Secondly, you need git 2.11+, once make, pkg-config, gcc and other compilation tools, you can install it with the following command:
# Ubuntu
sudo apt install build-essential git pkg-config
# Arch Linux
sudo pacman pkg-config make gcc g++ git
Finally, we need to obtain personal ACCESS TOKEN, because GitHub will abolish password verification during git operations at the end of 2021. All password verification needs to be converted to TOKEN verification, and the password can only be used to log in to the account itself.
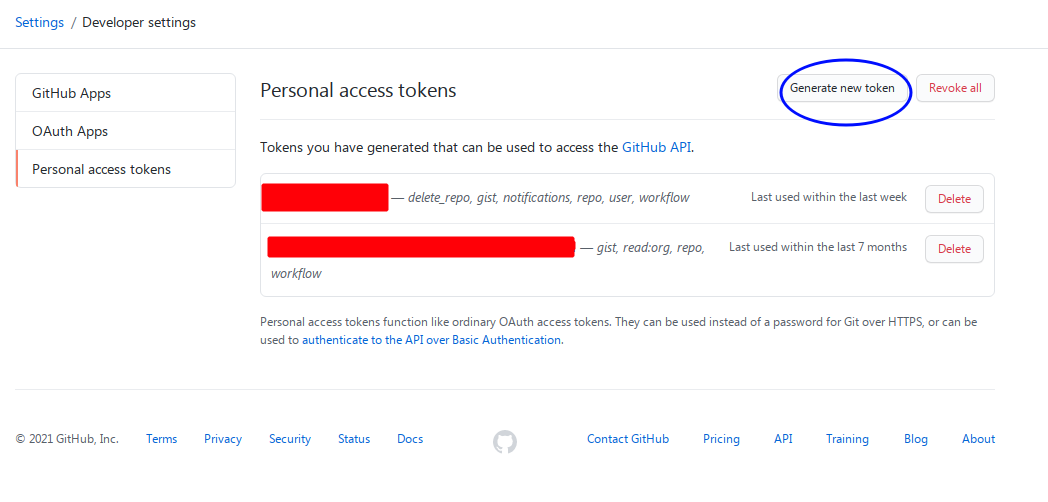
First of all, we have to enter the setting interface, first open github.com, and then follow the steps in the picture:
Then click the developer settings in the red circle:
You will see this interface with the created tokens and create/delete buttons listed above:
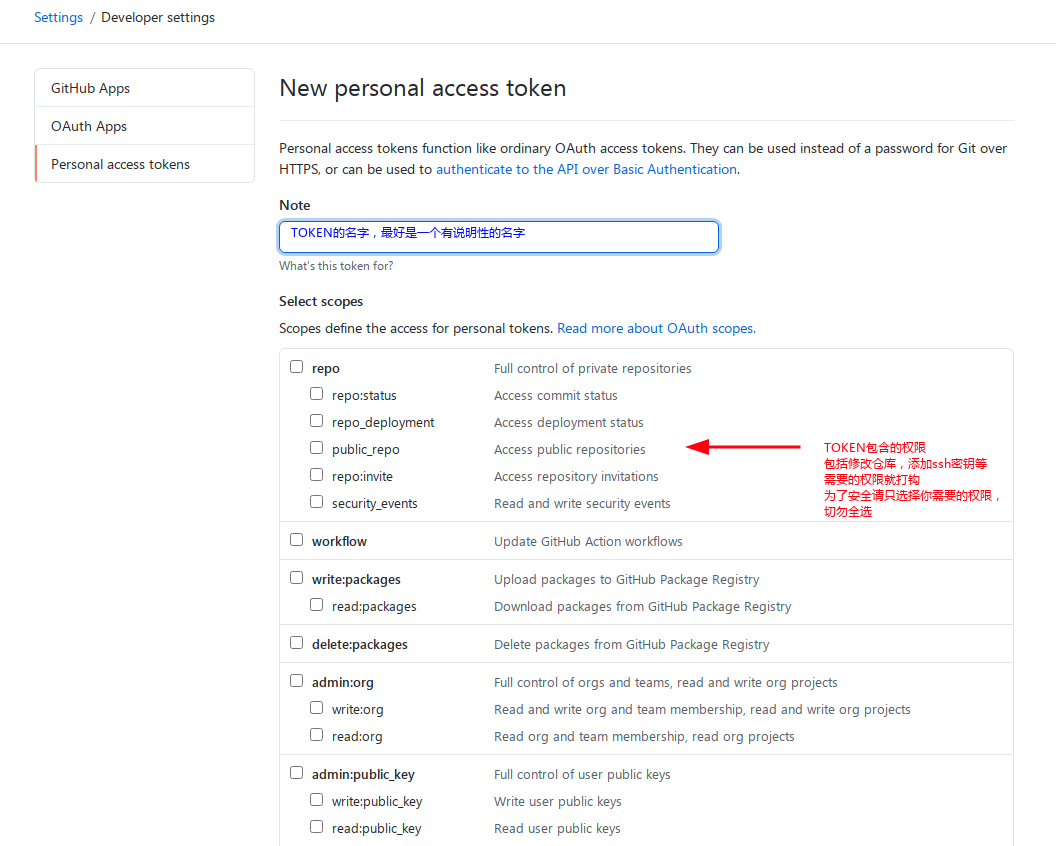
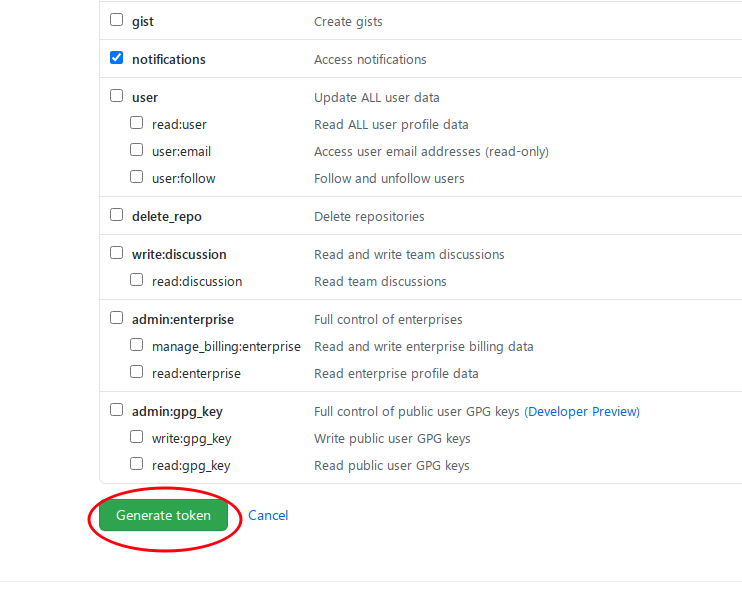
The following is how to create a token. It is recommended to only check the permissions you need, such as submitting a commit, etc. The more permissions are not the better:
After the creation is complete, the token will be displayed to you in plaintext, and you must save it properly, because once the page is closed/refreshed, only you will know this string of tokens:
Once the token is lost or useless, it must be deleted in time. For example, the token I just created for the demonstration will be useless at the end of the demonstration, so delete it:
With the access token, you can configure automatic login authentication below.
What is credential storage
Literally, the password or token is stored in a certain way, and these stored credentials can be obtained when needed.
Git has built-in support for credential storage, through configuration:
git config --global credential.helper xxx
If it is not set, it will not be stored by xxxdefault . This default has 2 options:
- store stores the credentials in the $HOME directory in plain text, it is recommended not to set it for safety
- cache stores the credentials in the memory for 15 minutes and deletes them after 15 minutes
In addition, third-party applications that comply with interface specifications are also supported:
git config --global credential.helper your-tool
git config --global credential.helper /path/to/your-tool
For the first form, git will $PATHlook for the named git-credential-your-toolprogram in it, and there is no need to write the prefix when setting it. The second type will directly call the program specified by the absolute path.
The reason for choosing third-party tools is security: these tools usually encrypt your credentials and store them in a place that is not easy to cause malicious access. In addition, they can be integrated with system functions.
So where to find such a good third-party management program? Don't worry, git comes with it.
On Ubuntu systems, git stores the source code of these programs in: /usr/share/doc/git/contrib/credential/here. On Arch Linux it is /usr/share/git/credential:
The picture above is the situation on Arch Linux. Gnome-keyring, libsecret and netrc are tools that can be used on Linux.
Because they are all source codes, we have to compile them first.
Configuration
We choose libsecret because gnome-keyring will be obsolete in the future.
Use the following command to compile, taking Ubuntu as an example:
cd /usr/share/doc/git/contrib/credential/libsecret
sudo make
# 如果目录所在的文件系统是ext4,xfs,btrfs,还可以用下面的命令禁止对程序的任何修改
sudo chattr +i git-credential-libsecret
You can add this directory to $PATH, and then specify credential.helper:
echo '$PATH=$PATH:/usr/share/doc/git/contrib/credential/libsecret' >> ~/.bashrc
git config --global credential.helper libsecret
Or if you don't want to modify $PATH, you can configure it like this:
git config --global credential.helper /usr/share/doc/git/contrib/credential/libsecret/git-credential-libsecret
This is done.
run
In order to test, we randomly choose a project of our own, first clone to the local, and then make some modifications and commit.
Credential verification is only performed when modifying the remote warehouse, such as push. The usual process is this:
$ git push origin dev
Username for 'https://github.com': apocelipes
Password for 'https:/[email protected]':
Although the prompt text still uses the password, the input should be the access token we created earlier.
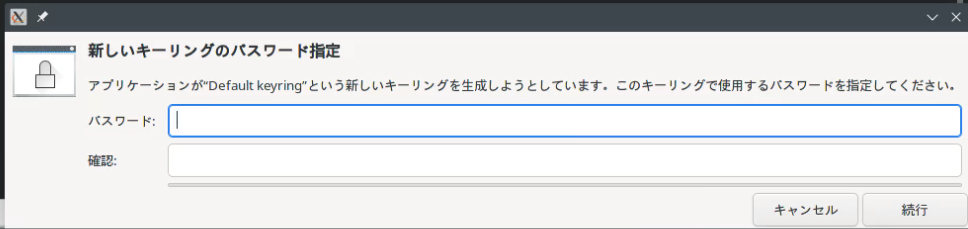
After the verification is passed, the changes will be pushed to origin, but after the automatic verification is configured, the credentials are still required for the first time, and now it will be like this:
You need to configure a separate password for your key ring. You can also choose the user's default password. After the configuration is complete, the credentials will be stored securely.
Next time push will not verify the username and credentials again, and the effect is the same as in the picture at the beginning of the article.
This completes the configuration of automatic login authentication.