Install snort on XP:
1. Install winpcap:

Can be completed all the way next
Reboot
2. Install snort

Can be completed all the way next
C:\Snort\bin\snort.exe -W
The installation is complete without any error in the command
3. Install mysql

The first step: all the way next

Step 2: Next all the way

Step 3: Next all the way

Step 4: Next all the way

Step 5: Next all the way

Step 6: Finish
The seventh step: cmd
mysql -u root –p --default-character-set=utf8
password
create database snort;
create database snort_archive;
use snort;
source C:/Snort/schemas/create_mysql; (slashes may be problematic)
use snort_archive;
source C:/Snort/schemas/create_mysql; (the slash may be problematic, change it to // / try)
grant all on *.* to "root"@"localhost";
show tables; view table
4. Install and configure mysql_Front
The next installation is complete and run.
log in:

modify

5. Install the Snort rule base

Overwrite decompression
6. Modify Snort configuration
Open C:\Snort\etc\snort.conf
1. Replace ipvar with var
2、
var HOME_NET 192.168.1.0/24 ---- (the network segment where you are)
var RULE_PATH C:\Snort\rules
3、
behind dynamicpreprocessor directory
Change to C:\Snort\lib\snort_dynamicpreprocessor
Behind Dynamicengine
Change to C:\Snort\lib\snort_dynamicengine\sf_engine.dll
Comment out
# dynamicdetection directory /usr/local/lib/snort_dynamicrules
4. Uncomment and modify output database: alert... as follows
output database: alert, mysql, user=root password=your password dbname=snort host=localhost
5、
include classification.config
改为include C:\Snort\etc\classification.config
include reference.config
改为include C:\Snort\etc\reference.config
6、
include $RULE_PATH/local.rules保留
The rest include $RULE_PATH/. . . . Comment out
7、
Comment out the following items:
#preprocessor normalize_ip4
#preprocessor normalize_tcp: ips ecn stream
#preprocessor normalize_icmp4
#preprocessor normalize_ip6
#preprocessor normalize_icmp6
modify
compress_depth 65535 decompress_depth 65535
Save and exit.
6. Write snort rules
打开C:\Snort\rules \local.rules
加入alert ip any any -> any any (msg: "IP Packet detected";sid:1000000;)
# Every IP is warned
7. Install wireshark

All the way next
(Winpcap reinstallation is also possible)
8. Run snort
Add the environment variable C:\Snort\bin in Path;
snort -W look at the number (mine is 1)
snort -c "c:\snort\etc\snort.conf" -l "c:\snort\log" -i 1 -d -e
(The mysql_error: duplicate entry 0 for key primary error will appear, because the primary key is the same, and the data cannot be inserted again.)

Can solve the problem
9. Configure snort rules
Modify local.rules rules, such as adding
![]()
Learn about the rules of the rules, you can successfully detect the Trojan
10. Actual combat
1) Green light remote control:
1. Configuration environment:
Generate an on-line control terminal,
Run the client side under win7, run the server side under xp, and then use the unused port under win7 to control

2. Capture and view
Link package:

Screen capture package:

and many more
3. Configure rules and test
Xp下C:/snort/rules/local.rules
Configure the alarm rule

Cmd中运行snort -c "c:\snort\etc\snort.conf" -l "c:\snort\log" -i 1 -d -e
After performing operations such as login link, screen capture, and system information acquisition:

2) Chongqing hacker remote control
1. Configuration environment:
Listening port 10123

Generate a program to reverse the shell

2. Packet capture analysis:
Screen capture package:

Browse the file package:

and many more
3. Configure rules and test:

3) Red and black remote control:
1. Configure the environment

Run the corresponding program on XP
2. Packet capture analysis
Screen capture:

Process management:

and many more
3. Configure rules and test:

4) Flying Fox remote control
1. Configure the environment

2. Capture and view
Link package:

Screen monitoring:
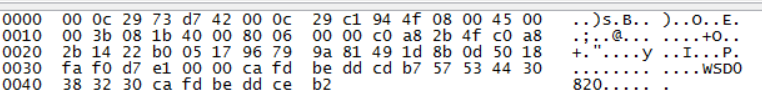
3. Configure rules and test:

5) Magic a remote control:
1. Configure the environment

2. Capture and view
Link package:

cmd link package:

3. Configure rules and test
