3.2.1 Users and user groups
1) Concept description
There are three types of linux system: root user, system user, and ordinary user. These users are distinguished and managed by the internal ID number of the system. UID is the ID number of the user and GID is the ID number of the user group. The root user is also the root user, also known as the super administrator, with a UID of 0 and has all the operating rights of the system. The system user is the default fixed user of the system service. The UID range is between 1 and 499. This type of user cannot log in to the system and is limited to operating startup, upgrade, and execution of corresponding system services. Ordinary users are restricted users created by root execution, with UID between 500-65534, and can be used to manage specified applications and log in to the machine through authorization. When a user is created, the system will create a user group with the same name by default, and add the user to the group. When the user group is authorized with a certain permission, all users in the group share the permission.
2) Interpretation of information files
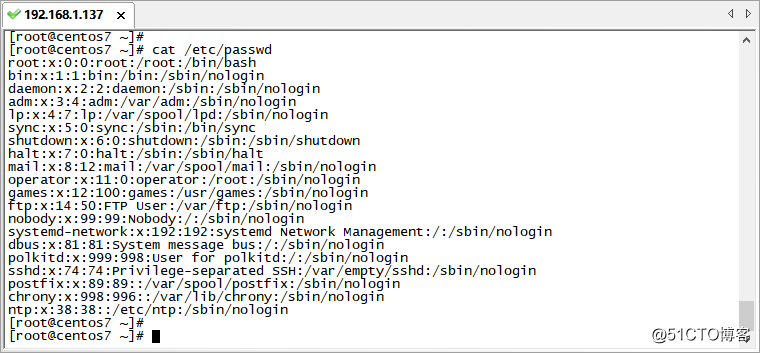
1. The user information file /etc/passwd (the content is shown in the figure below), which stores the basic information of all accounts. The content is separated by colons. There are 7 items of information: the first item is the user name; the second item is the password account. Bit (when the value is x, it means there is a password, when it is empty, it means there is no password); the third item is UID; the fourth item is GID; the fifth item is user information description; the sixth item is the user's home directory; the seventh item is User shell type, /bin/bash means login is allowed, /sbin/nologin means login is forbidden.
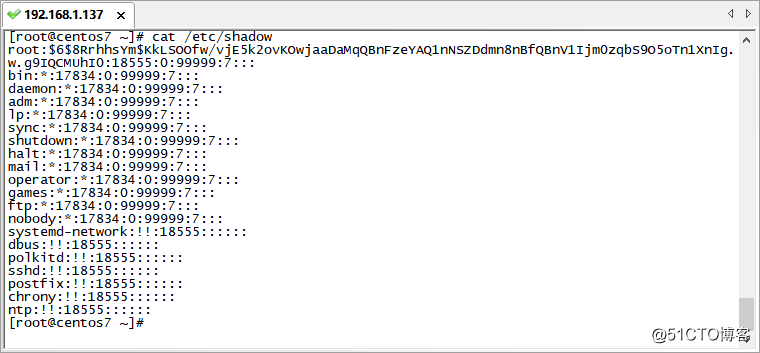
2. The user password file /etc/shadow (as shown in the figure below), which stores the password information of the account. The content is divided by colons. There are nine items in total: the first item is the user name; the second item is the encrypted password ; The third item is the time when the password was last modified; the fourth item is the minimum time interval for changing the password, 0 means unlimited, if the number is 8, it means that no further changes are allowed within 8 days after the change; the fifth item is the password validity period, 99999 represents permanent validity. If the number is 90, it represents a 90-day validity period; the sixth item is the expiration advance warning time, such as the number 7, which means a warning that the password needs to be changed seven days before expiration; the seventh item is after the password expires The grace period; the eighth item is the password expiration date; the ninth item is reserved for use.
3.2.2 Account management commands
1)useradd
Role: Create a new account
Parameters: -d sets the user's home directory; -e specifies an account expiration date in the format YYYYY-MM-DD; -f specifies the account expiration date; -g specifies the GID or group name of the user login group; -G specifies one or more Additional group; -m creates the user's home directory; -M does not create the user's home directory; -p specifies the default password for the user account; -s specifies the login shell type; -u specifies a unique UID for the account.
Example:
[root@centos7 ~]# useradd user001 #Create user user001
[root@centos7 ~]# useradd -g test user002 #Create user user002, specify the group as test
[root@centos7 ~]# useradd -u 1100 -g test user003 # uid and create user-specified groups
[the root centos7 @ ~] # the useradd -g -G test1 user004 Test # Create a user-specified group and the additional set of
[@ centos7 the root ~] # the useradd -s / sbin / nologin -M user005 # Create Users who have no home directory and cannot log in
Tip: The grouping of ordinary users should be clear, or else use the same name group by default to avoid management confusion.
2)userdel
Role: delete user
Parameters: -r delete user and home directory.
Example:
[root@centos7 ~]# userdel user001 #Delete user user001 and keep the home directory
[root@centos7 ~]# userdel -r user002 #Delete user user002 and home directory
3)groupadd
Role: Create user group
Parameters: -g specifies the GID.
Example:
[root@centos7 ~]# groupadd test #Create test user group
[root@centos7 ~]# groupadd -g 1200 test1 #Create user group test1 with GID 1200
4) groupdel
Role: Delete user group
Example:
[root@centos7 ~]# groupdel test #Delete the test user group
5)passwd
Function: Set user password, change account status
Parameters: -l lock user; --stdin read password from file or pipe; -u unlock user; -d quickly clear password.
Example:
[root@centos7 ~]# passwd -l tomcat #锁定用户
[root@centos7 ~]# passwd -u tomcat #解锁用户
[root@centos7 ~]# passwd -d tomcat #清空用户密码
[root@centos7 ~]# echo "123456" |passwd --stdin tomcat #设置tomcat的密码为123456
[root@centos7 ~]# passwd tomcat #修改密码,需两次输入新密码
提示:在大部分环境中,不要使用--stdin的方式,该命令中有密码会留存在历史记录里。
6)usermod
作用:变更账户信息
参数:-u 变更账户UID;-d 修改家目录;-g 修改所属用户组;-e 设置失效日期;-s 变更用户登录shell类型。
[root@centos7 ~]# usermod -u 2001 user001 #修改user001的uid为2001
[root@centos7 ~]# usermod -e 2022-11-11 user002 #修改用户user002的失效日期
[root@centos7 ~]# usermod -d /home/user007 user002 #变更用户user002的家目录
[root@centos7 ~]# usermod -g test1 user003 #变更user003的用户组为test1
[root@centos7 ~]# usermod -s /sbin/nologin user004 #设置禁止user004登录
提示:使用-d命令后,家目录的属主未变,是无写入权限的,需要自行用chown修改属主信息。
3.2.3 文件目录权限解析
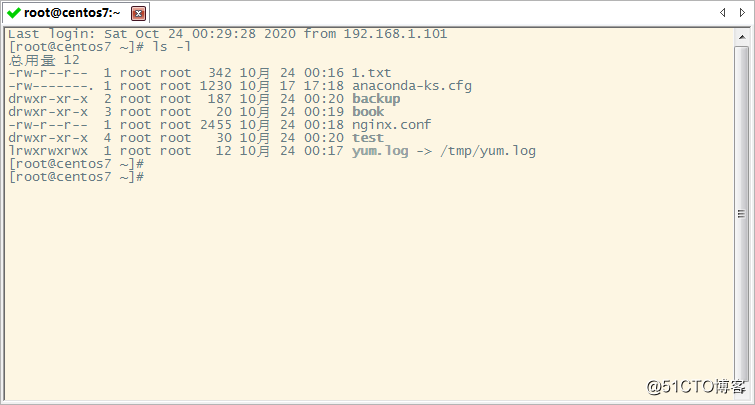
linux文件目录主要有读、写、执行是三种权限,通过 ls -l 可以查看文件目录信息(如下图所示),其中显示的r为读权限、w为写权限、x是执行权限,分别对应数字为4、2、1。图示中第一列中有十个字符,第一个字符指示文件类型:- 代表文件,d 代表目录,l 代表链接文件。从第二个字符到第十个字符代表权限,三位一组,从左到右分别是用户权限、用户组权限、其他用户权限。例如rwxr--r--表示所属用户具有读写执行三个权限,属组有只读权限,其他用户也是只读权限,用数字表示该文件权限是744。第二列是子目录数量;第三列为所属用户;第四列是所属组,第五列是文件大小,第六列是最近一次修改的月份,第七列是日期,第八列是时间,第九列是文件目录名称。
3.2.4 文件目录权限管理命令
1) chmod
作用:修改文件目录权限
参数:-R 将权限递归应用到子目录文件。该命令使用中会用到一些特定意义的字母和数字,u代表所属用户,g代表所属用户组,o代表其他用户,a代表所有人;r(=4)代表读权限,w(=2)代表写权限,x(=1)代表执行权限。权限的数字表达释义:
例如文件的权限是 -rwxrw-r-x ,数字表达为765
r=4,w=2,x=1 r是读权限,w是写权限,x是执行权限
rwx属性,则4+2+1=7; 代表所属用户可读可写可执行
rw- 属性,则4+2=6; 代表所属组可读可写不可执行
r-x 属性,则4+1=5; 代表其他用户可读可执行不可写
示例:
[root@centos7 ~]# chmod u+x 1.txt #给文件增加可执行权限,改后为rwxr--r--
[root@centos7 ~]# chmod a=rx 1.txt #变更文件权限后为r-xr-xr-x
[root@centos7 ~]# chmod u=rwx,g=rx,o=rx 1.txt #修改文件权限为rwxr-xr-x
[root@centos7 ~]# chmod g-x,o-x 1.txt #去掉组和其他用户的执行权限
[root@centos7 ~]# chmod 755 oprn.sh #修改文件权限为rwxr-xr-x
[root@centos7 ~]# chmod 777 /home/ #修改目录的权限为rwxrwxrwx
[root@centos7 ~]# chmod 755 /home/backup -R #修改backup及其子目录权限为rwxr-xr-x
提示:文件目录权限应严格控制,谨慎使用777权限。
2) chown
作用:修改文件目录的所有者或所属组
参数:-R 递归修改目录文件
示例:
[root@centos7 ~]# chown nginx:nginx /www #将www目录的用户和组改为nginx
[root@centos7 ~]# chown mysql.mysql /data -R #将data及子目录文件全改为mysql属主
3) chattr
作用:指定文件特殊属性权限,防止删除
参数:i 设定不可修改、删除文件;a 可以追加内容到文件尾,不可删除;+ 增加权限;- 去除权限;lsattr 查看权限。
示例:
[root@centos7 ~]# chattr +i nginx.conf #增加i权限
[root@centos7 ~]# chattr -i nginx.conf #取消i权限
[root@centos7 ~]# chattr +a 1.txt #增加a权限
[root@centos7 ~]# chattr -a 1.txt #取消a权限
[root@centos7 ~]# lsattr nginx.conf #查看文件是否有特殊权限
提示:当发现文件不可修改或删除时,先用lsattr查看,然后再用chattr取消权限即可编辑删除。
The content of this section is about the security management of accounts and permissions. It involves the security of the system. When adding users, you must strictly control the scope of permissions used by ordinary users, control the permissions of file directories, and prevent ordinary users from unauthorized operations. In the daily work of future operation and maintenance, the most commonly used file permission management is the chmod and chown commands to set the file directory permission size, and set the operable users and user groups. Be sure to master the usage methods. Operation and maintenance must adhere to a strict and rigorous work attitude. The more rigorous the authorization management, the safer the system.