table of Contents
One, inode and block
1.1 Overview of inode and block
■ File data includes original information and actual data.
■ The file is stored on the hard disk. The smallest storage unit of the hard disk is "sector", and each sector stores 512 bytes
■ block
- Eight consecutive sectors form a block
- Is the smallest unit of file access
■ inode (index node)
- Chinese translation is "index node", also called i-node
- Used to store file meta information
1.2 Contents of inode 1-1
■ inode contains the meta information of the file
- File size
- User ID of the file owner (not including the file name)
- Group ID of the file
- File read, write, and execute permissions
- File timestamp
- …
■ Use the stata command to view the inode information of a file
- Example: stat aa.txt''
1.3 The content of the inode 1-2
■ Three main time attributes of Linux system files
- ctime(change time)
- Last time the file or directory (attribute) was changed
- atime(access time)
- Last time the file or directory was accessed
- mtime(modif time)
- The last time the file or directory (content) was modified
1.4 The content of the inode 1-3
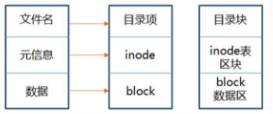
■ The structure of the catalog file
- Directory is also a kind of file
- The structure of the catalog file
| File name 1 | inode number 1 |
|---|---|
| File name 2 | inode number 1 |
| … | … |
Each row is called a directory item
■ Each inode has a number, and the operating system uses the inode number to identify different files.
■ The Linux system does not use the file name, but uses the inode number to identify the file.
■ For users, the file name is just another name for the inode number for easy identification.
1.5 inode number
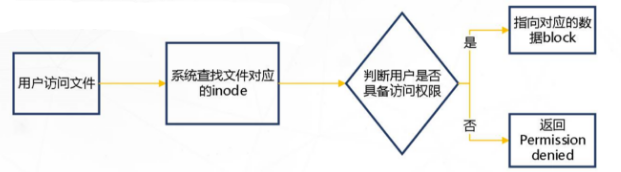
■ When the user opens the file by the file name, the internal process of the system
- The system finds the inode number corresponding to this file name
- Used inode number to get inode information
- According to the inode information, find the block1 where the file number data is located, and read the data
■ How to check iodine number
- ls -i command: View the inode number corresponding to the file name
ls -i aa.txt - stat command: View the inode number in the file inode information
stata aa.txt
1.6 Summary of file storage
■ Structure of the hard disk after partitioning
■ Simple process for accessing files
1.7 Inode size
■ Inode also consumes hard disk space
- The size of each inode
- Generally 128 bytes or
■ Determine the total number of inodes when formatting the file system.
■ Use the df -i command to view the total number of inodes and the used number of each hard disk partition
1.8 The special role of inode
■ Due to the separation of inode number and file name, some Unix/Linux systems have the following phenomena
- When the file contains special characters, the file may not be deleted normally, you can delete the inode directly or delete the file
- When moving or renaming a file, only the file name is changed without affecting the inode number
- After opening a file, the system uses the inode number to identify the file, regardless of the file name
Two, hard link and soft link
2.1 Link file 1-1
■ Create link files for files or directories
■ Link file categories
| Soft link | Hard link | |
|---|---|---|
| Use range | Invalidation | Still available |
| Save range | Can be located in a different file system from the original file | Must be in the same file system (such as a Linux partition) with the original file |
2.2 Link files 1-2
■ Create link files for files or targets
■ Link file classification
- Hard link
ln 源文件 目标位置 - Soft link
ln -s 源文件或目录...链接文件或目标位置
3. Recover accidentally deleted files
3.1 Recover EXT type files
■ Compile and install the extundelete package
- Install dependencies
- e2fsprogs-libs-1.41.12-18.el6.x86_64.rpm
- e2fsprogs-devel-1.41.12-18.el6.x86_64.rpm
■ Simulate deletion and perform recovery operations
3.2 Recover XFS type files
■ xfsdumo command format
xfsdump -f 备份存放位置 要备份的路径或设备文件
■ xfsdump backup level (default is 0)
- 0: safe backup
- 1-9: Incremental backup
■ xfsdump commonly used options: -f, -L, -M, -s
■ xfsdump command format
xfsdump -f 恢复文件的位置 存放恢复后文件的位置
■ Simulate deletion and perform recovery operations
3.3 xfsdump usage restrictions
■ Only the mounted file system can be backed up.
■ You must use root authority to operate.
■ Only the CFS file system can be backed
up. The data after backup can only be analyzed by xfsrestore.
■ Two file systems with the same UUID cannot be backed up.
Fourth, analyze log files
4.1 Log file 4-1
■ Log function
- Used to record various things that happen during the operation of the system and programs
- By reading the log, it is helpful to diagnose and solve system failures
■ Diary asks for your classification
-
Kernel and system logs
- Unified management by the system service rsyslog, the log format is basically similar
-
User log
- Record system user login and logout information
-
Program log
- Log files independently managed by various applications, the record format is not uniform
4.2 Log file 4-2
■ Log storage location
- The default location: /var/log directory
■ Introduction to main log files

4.3 Kernel and System Log 4-3
■ Unified management by the system service rsyslog
- Package: rsyslog-7.4.7-16.el7.x86_64
- Main program: /sbin/rsyslogd
- Configuration file: /etc/rsyslog.conf
4.4 Kernel and System Log 4-4
■ Level of log message
| level | news | level | Description |
|---|---|---|---|
| 0 | EMERG | urgent | Will cause the host system to be unavailable |
| 1 | ALERT | caveat | Problems that must be resolved immediately |
| 2 | CRIT | serious | More serious situation |
| 3 | ERR | error | Run error |
| 4 | WARNING | remind | Events that may affect system functions |
| 5 | NOTICE | note | Will not affect the system but it is worth noting |
| 6 | INFO | information | General information |
| 7 | DEBUG | debugging | Program or system debugging information, etc. |
4.5 Kernel and System Log 4-5
■ General format of log records

4.6 User log analysis
■ Save the user login, logout and other related information
- /var/log/lastlog: recent user login events
- /var/log/wtmp: user login, logout and system startup and shutdown events
- /var/log/utmp: Details of each user currently logged in
- /var/log/secure: security events related to user authentication
■ Analysis tools
-users, who, w, last, lastb
4.7 Program log analysis
■ Independently managed by the corresponding application
- Web service: /var/log/httpd/
access_log, error_log - Proxy service: /var/log/squid/
access_log, cache_log - FTP service: /var/log/xferlog
■ Analysis tools
- Text view, grep filter search, view in Webmin management suite
- Text filtering, formatting and editing tools such as awk and sed
- Webalizer, Awstats and other dedicated log analysis tools
4.8 Log Management Strategy
■ Make timely backups and archives
■ Extend the log retention period
■ Control log access
- Logs may contain various sensitive information, such as accounts, passwords, etc.
■ Centralized management of logs
- Send the server's log file to the unified log file server
- Facilitate the unified collection, sorting and analysis of log information
- Prevent accidental loss, malicious tampering or deletion of log information