Preface:
In recent years, micro-services can be described as popular. In the business model is imperfect, in the case of very large scale impact of traffic, many companies have abandoned the traditional single architecture, embrace micro services. This model with independent development, independent of deployment, scalability, reusability of the advantages, but also brings the question: development, increase the complexity of the operation and maintenance. Some people feel better and convenient service micro-management.
abstract:
This book is a project called EagleEye of the main line, introduced the concept of cloud services, as well as micro-Spring
the Boot and SpringCloud Spring and many other projects, and describes how EagleEye
project step by step from monomers constituting the micro Services Architecture architecture, in turn the project is split into a number of micro-services, so that they run in their Docker containers, to achieve continuous integration continued to deploy special, and eventually deployed automatically to the cloud (Amazon
) in. For typical problems encountered in the reconstruction process will face a variety of micro-services development (including development, testing and operation and maintenance and so on), this book introduces the core mode to solve these problems, and how to select a specific Spring in actual combat
Cloud subprojects or other tools to solve these problems.
Recently we put together a set of micro-service real documents, explaining very thorough. Share with you today. This information is particularly suitable for the following groups:
■ have Java developers to build distributed applications experience (1-3 years).
■ have the knowledge background of Spring (over 1 year) technical staff.
■ learning Building a Technician micro-based applications and services of interest.
■ the use of micro-service technicians to build interest in cloud-based applications.
■ want to know whether Java and Spring are used to build skilled in the relevant art based on the application of micro-services.
■ are interested in learning how to deploy to the application of micro-based service technicians on the cloud.
This book describes:
● the core design principles of micro-services.
● Use Spring Cloud Config configuration management.
● Use Spring, Hystrx and Ribbon achieve client resilience.
● Use Netfix Zuul intelligent routing.
● deploy Spring Cloud applications.
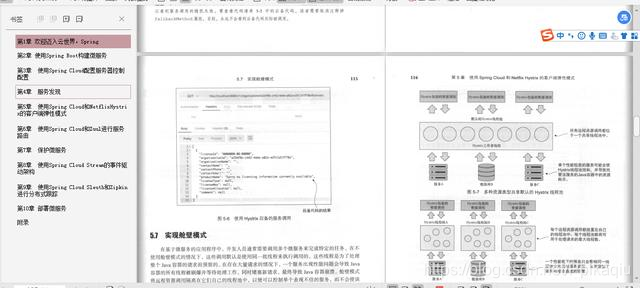
Specific chapters of this book are:
* Chapter 1: ** welcomed into the cloud world, the Spring
** Chapter 2: ** Use Spring Boot to build micro-services
** Chapter 3: ** Use Spring Clou home server control configuration
* Chapter 4: service discovery **
** Chapter 5: ** use Spring Cloud and NetflixHystrix client elastic mode
** Chapter 6: ** use Spring Cloud services and Zu1l be routed
** Chapter 7 : ** protection microService
** Chapter 8: ** Spring Cloud Str e am using event-driven architecture
* Chapter 9: ** Use Spring Cloud s1 euth and distributed Zipkin track
** CHAPTER 10: ** deploying Micro Services
Appendix
of this the book contains 10 chapters and 2 appendices:
■ Chapter 1: Why will introduce the micro-architecture is a service to build applications, particularly important related methods of cloud-based applications.
■ Chapter 2: guide the reader learn how to use Spring Boot to build the first of a microprocessor-based REST service. This chapter explains how to look at the micro-services through the perspective of architects, engineers and application DevOps engineers. 
■ Chapter 3: I will explain how to configure Spring Cloud Confg use micro-management services. Spring Cloud Config can help developers ensure that the configuration information services centralized in a single repository, and all service instances are version control and repeatable. .
■ Chapter 4: Introducing the first micro-service routing a service discovery mode. In this chapter, the reader will learn how to use Spring Cloud and Netlix of Eureka service, location services abstracted from the customer's use.
■ Chapter 5: discuss consumer protection service of micro-off or in a degraded state when one or more micro service instance. This chapter will demonstrate how to use Spring Cloud and Netlix Hystrix (and Netlix Ribbon) to achieve load balancing client calls, breaker mode, backup mode and bulkheads mode. 
■ Chapter 6: Micro will introduce a service gateway service routing mode. Use Spring Cloud and Netlix of Zuul server, developers will create a single entry point for all micro-services. We will discuss how to build a strategy can be enforced for all services to flow through the services gateway using Zuul filter API.
■ Chapter 7: Spring Cloud Security describes how to use and implement service OAuth2 authentication and authorization. We'll show you how to set OAuth2 services to protect the service, and how to use JSONWeb token (JSONWeb Tokens, JWT) in OAuth2 implementation.
■ Chapter 8: Discussion of how to use Spring Cloud Stream and Apache Kafka pass asynchronous message to the micro-service. 
■ Chapter 9: describes how to use Spring Cloud Sleuth and Open Zipkin to achieve log correlation, log aggregation and tracking of common 8 logging mode.
■ Chapter 10: This book is the cornerstone of the project. Readers will use the service to build in this book, and deploy it to Amazon Elastic Container Service (Amazon Elastic Container Service, ECS) . We will also discuss how to use the TravisCI tools such as automated build and deploy micro-services. 
■ Appendix A: Describes how to set the desktop development environment, so that all the code examples in this book can be run. This appendix describes how local build process works, and how you want to start local Docker when you run the sample code locally. 
■ Appendix B: is OAuth2 additional information. OAuth2 is a - kind of a very flexible authentication model, this appendix briefly OAuth2 be used in different ways to protect applications and their corresponding micro-services. 
Due to space limitations, only a small series where the actual information contained in this document are all show out. 
And there will be the following interview questions include :()