undertow remote WWW service supports TRACE request vulnerability fix
1 Vulnerability description and reproduction
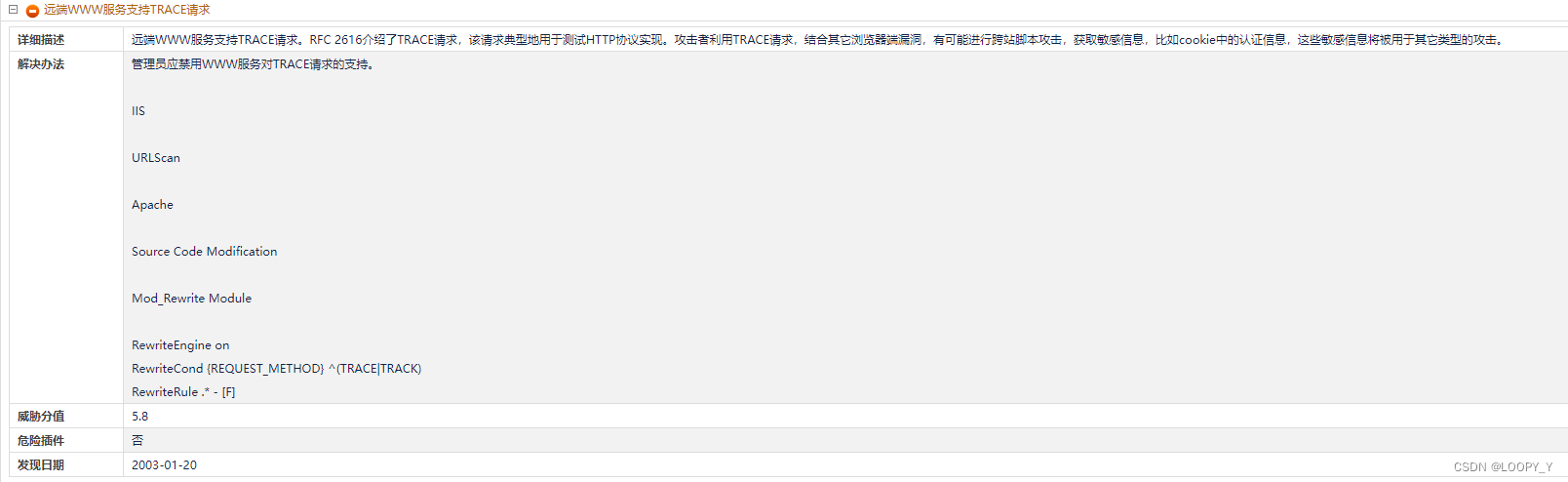
1.1 Vulnerability description
1.2 Vulnerability recurrence
Execute the command curl -v -X TRACE IP:PORT and you can see a 200 response, indicating that a trace vulnerability exists.
[root@vxdfbdbgggsd ~]# curl -v -X TRACE 192.168.21.237:8081
·······省略以上·······
> TRACE HTTP://192.168.21.237:8081/ HTTP/1.1
> User-Agent: curl/7.29.0
> Host: 192.168.21.237:8081
> Accept: */*
> Proxy-Connection: Keep-Alive
>
< HTTP/1.1 200 OK (这里的状态为200)
< Content-Type: message/http
< Content-Length: 216
< Date: Wed, 10 May 2023 01:28:03 GMT
< X-Cache: MISS from adadavfbbbf
< Via: 1.1 adadavfbbbf(squid/4.15)
< Connection: keep-alive
<
·······省略以下·······
[root@vxdfbdbgggsd ~]#
2 Bug fixes
When springboot embeds the undertow container, there are undertow related dependencies in the pom:
<dependency>
<groupId>org.springframwork.boot</groupId>
<artifactId>spring-boot-starter-undertow</artifactId>
</dependency>
Add a new configuration class:
import io.undertow.server.HandlerWrapper;
import io.undertow.server.HttpHandler;
import io.undertow.server.handlers.DisallowedMethodsHandler;
import io.undertow.util.HttpString;
import org.springframework.boot.web.embedded.undertow.UndertowServletWebServerFactory;
import org.springframework.boot.web.server.WebServerFactoryCustomizer;
import org.springframework.context.annotation.Configuration;
@Configuration
public class UndertowWebServerCustomizerConfig implements WebServerFactoryCustomizer<UndertowServletWebServerFactory>{
@Override
public void customize(UndertowServletWebServerFactory factory){
factory.addDeploymentInfoCustomizers(deploymentInfo ->{
deploymentInfo.addInitualHandlerChainWrapper(new HandlerWrapper(){
@Override
public HttpHandler wrap(HttpHandler handler){
HttpString[] disallowerHttpMethods = {
HttpString.tryFromString("TRACE"),HttpString.tryFromString("TRACK")
};
return new DisallowedMethodsHandler(handler,disallowerHttpMethods );
}
});
});
}
}
Just restart the service.
3. Verification after vulnerability repair
As you can see, there are no more 200 responses.
[root@vxdfbdbgggsd ~]# curl -v -X TRACE 192.168.21.237:8081
* About to connect() to proxy 192.168.21.238 port 3128 (#0)
* Trying 192.168.21.238...
* Connected to 192.168.21.238 (192.168.21.238) port 3128 (#0)
> TRACE HTTP://192.168.21.237:8081/ HTTP/1.1
> User-Agent: curl/7.29.0
> Host: 192.168.21.237:8081
> Accept: */*
> Proxy-Connection: Keep-Alive
>
< HTTP/1.1 405 Method Not Allowed
< Content-Length: 0
< Date: Wed, 17 May 2023 10:44:33 GMT
< X-Cache: MISS from adadavfbbbf
< Via: 1.1 adadavfbbbf (squid/4.15)
< Connection: keep-alive
<
* Connection #0 to host 192.168.21.238 left intact
[root@vxdfbdbgggsd ~]#