Recently, cybersecurity researchers have discovered a new post-exploitation persistence technique in iOS 16, which can be used to quietly access the victim's Apple device even if it is offline.
In a report shared with The Hacker News, researchers Hu Ke and Nir Avraham of Jamf Threat Labs said: This method tricks victims into thinking that their device's airplane mode is working, when in fact attackers are successfully exploiting the device. A fake artificial airplane mode has been implanted, which edits the user interface to display an airplane mode icon and cuts off internet connections for all but the attacker's app.
Airplane mode allows the user to turn off the wireless functionality in the device, effectively preventing the device from connecting to Wi-Fi networks, cellular data and Bluetooth, as well as sending and receiving calls and text messages.
In short, Jamf designed this method to give users the illusion that "airplane mode" is on, but at the same time allow malicious actors to quietly connect to the cellular network for malicious applications.
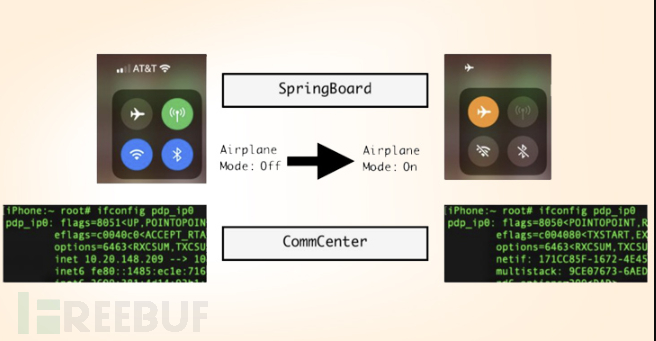
The researchers explained: When the user turns on the airplane mode, the network interface pdp_ip0 (cellular data) will no longer display the ipv4/ipv6 ip address. The cellular network is disconnected and unusable, at least it seems to the user.
While low-level changes are performed by CommCenter, user interface (UI) modifications, such as icon transitions, are handled by SpringBoard.
Therefore, the goal of the attack is to engineer an artificial flight mode that keeps the UI changes intact but preserves the cellular connection for malicious payloads installed on the device by other means.
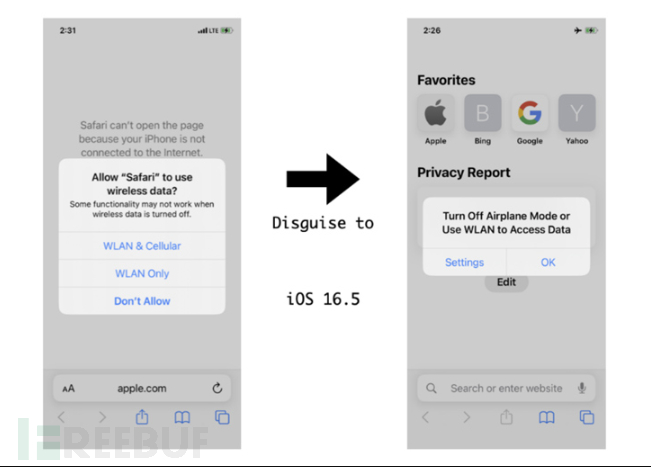
When Airplane Mode is enabled without a Wi-Fi connection, users will think that opening Safari will show that there is no Internet connection, the researchers said. A notification window will then pop up, prompting the user to turn off airplane mode.
To achieve this scenario, the CommCenter daemon is used to block cellular data access for specific applications and disguise them as Airplane Mode via a hook function that changes the alert window to appear as if Airplane Mode has been set was opened.
It is worth noting that the operating system kernel notifies CommCenter through a callback routine, and CommCenter notifies SpringBoard to display the pop-up window.
Closer inspection of the CommCenter daemon also revealed the presence of an SQL database that records each app's cellular data access status (aka bundle ID) and if an app is blocked from accessing cellular data, the database will set the flag value to "8".
Using this database of installed application bundle IDs, the following code can be used to selectively block or allow applications to access Wi-Fi or cellular data.
When combined with the other techniques above, this fake 'Airplane Mode' looks just like the real 'Airplane Mode', except that the internet ban doesn't apply to non-application processes, such as backdoor Trojans.