
0x1 event background
Zero Hour Technology's blockchain security intelligence platform monitored the news that on May 18, 2022, Beijing time, the Feminist Metaverse smart contract on the Binance chain was attacked by a smart contract. The value of the lost funds exceeded US$550,000, and the security team of Zero Hour Technology analyzed the security incident in a timely manner.

0x2 attacker information
- Attacker wallet:
0xaaA1634D669dd8aa275BAD6FdF19c7E3B2f1eF50
- Attacker contract:
0x0b8d752252694623766dfb161e1944f233bca10f
- Attack transactions:
0xecde3c3742615852abdbd6ec5d75ae982b5c29f810e140e5cd822667d6f7b848
- FmToken contract:
0x843528746F073638C9e18253ee6078613C0df0f1
0x3 attack analysis
By analyzing the attacker's attack transaction on the BNB Chain, the attacker's main transaction process is as follows:
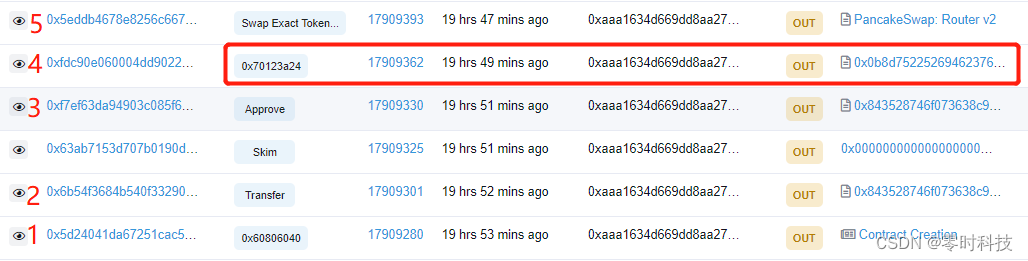
- The attacker deploys the attack contract;
- The attack wallet sends 10 FM to the attack contract to prepare for subsequent calls;
- The attacker authorizes the maximum value of FM funds in his wallet to the PancakeSwap.Router v2 contract to facilitate subsequent token exchange;
- The attacker officially starts to call the attack contract to attack, transfer funds to the attacker's wallet by calling Fmtoken.transfer through the attack contract, and then withdraw a large number of FM tokens from SakeSwapPair.skim;
- Exchange the acquired FM tokens into USD and finally into BNB.
Follow up the main attack transaction step 4:
Transaction process
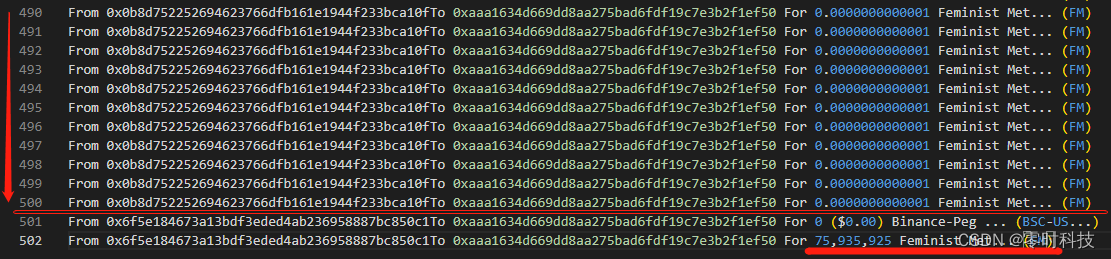
Transaction Details
There are only two operations in the above transaction details: the first is that the attacker contract calls the transfer method in the Fmtoken contract to transfer FM tokens to the attacker’s wallet, and transfers 0.0000000000001 FM each time, a total of 500 transfers; the second is that the attacker The wallet address calls the skim method in the SakeSwapPair contract to transfer 75.93 million FM to itself.
Through the analysis of all transactions, the attacker carried out a total of 16 successful attack transactions, called the transfer method in the Fmtoken contract 8,000 times to transfer funds, and transferred more than 1.1 billion FM from the skim method.
0x4 vulnerability details
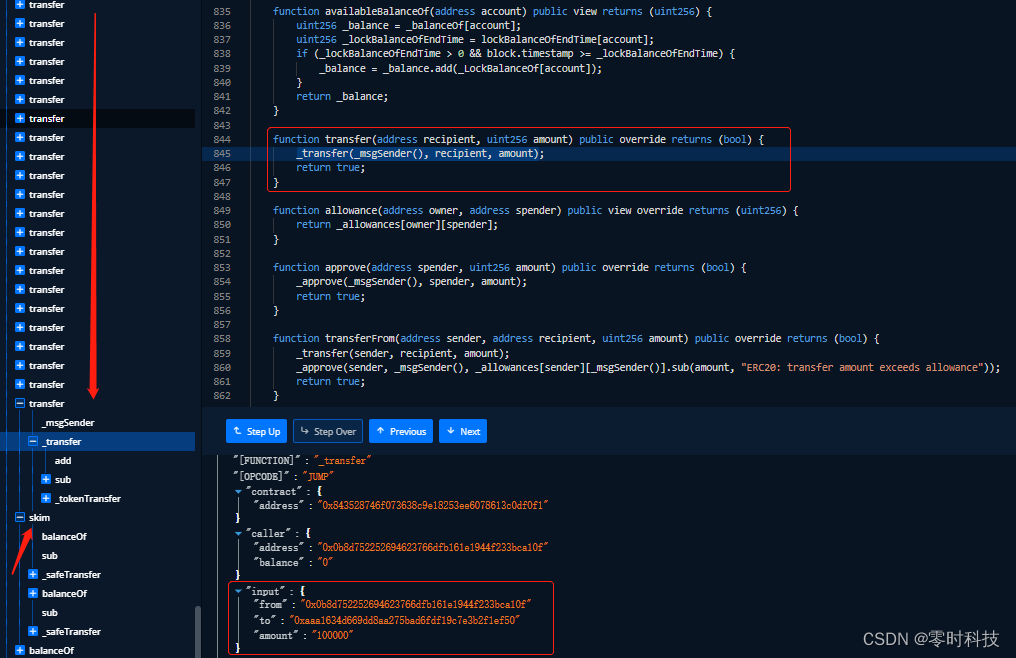
Through the above process analysis, it can be found that the main operation for the attacker to successfully profit is that the attacker contract calls the transfer method in the Fmtoken contract to transfer FM tokens to the attacker’s wallet, and then obtains a large amount of funds. Here is the follow-up of the Fmtoken.transfer method:
Key code display
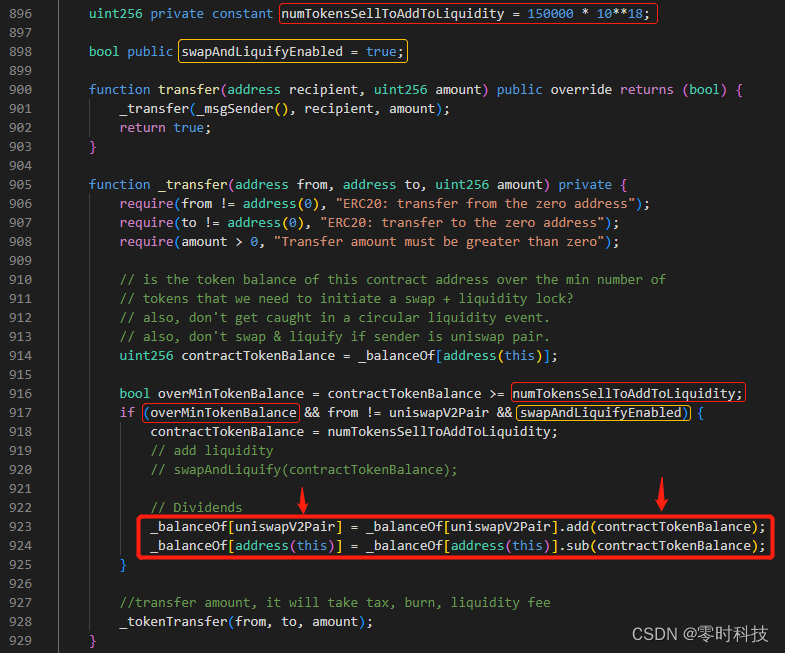
It can be clearly seen from the figure that the attacker finally transfers funds through the transfer method. Since the numTokensSellToAddToLiquidity and swapAndLiquifyEnabled variables have been determined, swapAndLiquifyEnabled is satisfied among the three conditions of the if judgment of the transfer method, and the from != uniswapV2Pair condition is also satisfied because the attacker calls it. The judgment condition can be met, so the attacker can perform the operation of updating the uniswapV2Pair address balance and address(this).
Because when the funds here are added to uniswapV2Pair, the funds are not transferred by adding liquidity, but directly added to uniswapV2Pair. When the attacker performs multiple transfers, that is, the attacker transfers the funds of the contract to uniswapV2Pair multiple times.
after
The skim method, anyone can call this method to transfer additional assets in the contract.

The attacker calls the skim method in the SakeSwapPair contract to transfer funds and successfully makes a profit.
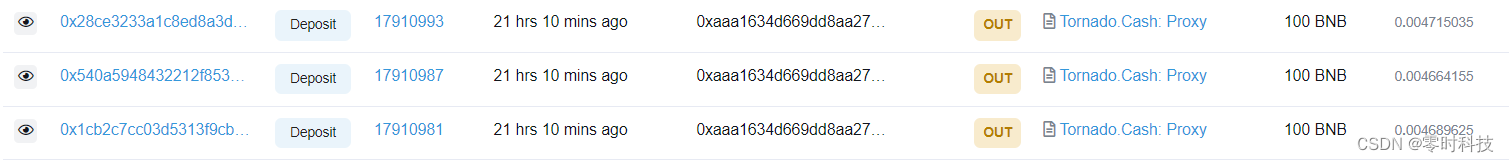
0x5 Fund source and destination
The source of the attacker's funds comes from the Tornado.Cash mixed currency platform, and the amount is 1 BNB. At present, all the attacker's profit funds have been converted into 1838.3 BNB and transferred to the Tornado.Cash currency mixing platform.
0x6 Summary
Judging from this attack, the Fmtoken._transfer method did not correctly operate the funds added to the SakeSwapPair contract, causing the attacker to transfer the original funds in the contract to the SakeSwapPair contract through multiple round-robin transfers in one transaction. Funds are thus withdrawn through the skim method. For the correctness verification of Fmtoken contract fund transfer, after the contract code development is completed, it can be completely avoided through code security audit.
0x7 Security Advice
- The contract fund transfer logic should be strictly checked;
- Before the smart contract goes online, a complete and detailed test should be carried out to ensure that the contract logic is normal;
- Before the smart contract goes online, a comprehensive security audit should be carried out to conduct a comprehensive investigation of the risks of the smart contract.