Article Directory
- TCP/IP
- TCP and UDP
- TCP
- Full-duplex
- TCP three-way handshake
- TCP four wave
- Why is the time to establish a connection of three-way handshake, and close the connection time is four
- Why up a client sends a confirmation request to enter TIME_WAIT to wait 2MSL
- How TCP to ensure reliable transmission
- Difference between TCP and UDP
- HTTP 和 HTTPS
- DNS
- MAC address, IP address,
- TCP congestion control and flow control
- Socket
- Cookie / Session Technology
#The internet
TCP/IP
TCP / IP protocol (Transmission Control Protocol / Internet Protocol) is not a simple protocol, but a set of special protocols, including: TCP, IP, UDP, ARP, etc. These are referred to as sub-protocol. In these agreements, the most important, most notably TCP and IP. Therefore, most network administrators say the entire protocol suite is "TCP / IP"
Seven Network
Four network
TCP and UDP
TCP
TCP protocol, one end initiate a request to the called client , one end of the connection is called a passive server . Because full-duplex, either the client or server, TCP connection can send and receive data after the establishment.
- SYN: synchronization packets
- ACK: acknowledgment message
- FIN: terminate the message
Full-duplex
- Full-duplex (Full Duplex) communication is a transmission term. Data communication allows simultaneous transmission in both directions, which is equivalent to combining the two in a simplex communication ability. Full-duplex bidirectional transmission means can simultaneously (instantaneous) signal of the (A → B and B → A). Refers to A → B while B → A, instantaneous synchronized.
- Simplex is the only party allowed to transmit information to the Party, and the Party can not be transferred to Party. (One-way car analogy.)
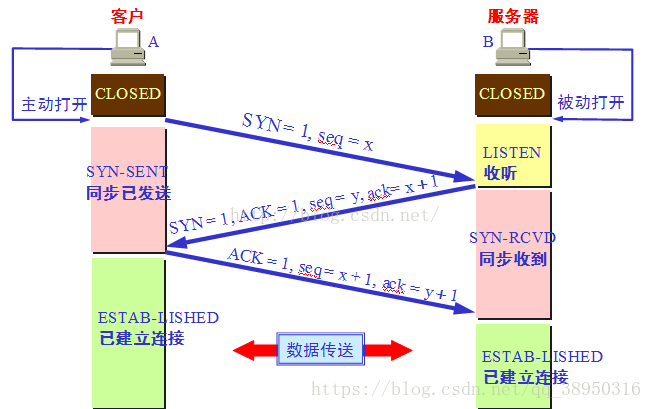
TCP three-way handshake
Why can not two-way handshake to establish a connection
- Assuming that the client does not receive ACK packet when the service end, would have been sending a SYN packet to the server;
- At a time when the server received SYN packet to the initiating client ACK packet, the client waits after a period of time, such as SYN packet is not received it that the client has received the ACK packet
- But this time there will be a situation that the service side of SYN and ACK packets sent by the client are dropping again, and this time the client sees no connection is established, and the client thinks the connection is established, it will cause confusion.
Therefore it requires a minimum of three-way handshake
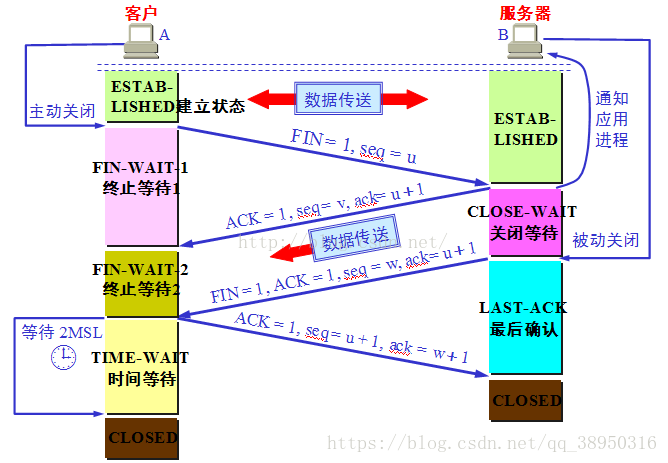
TCP four wave
Why is the time to establish a connection of three-way handshake, and close the connection time is four
Because TCP is full duplex, when the client sends a termination request, not only on behalf of the client data is sent to the server, and the server may also send the data is not complete. At this time, the server can send a confirmation message to tell the client has received the message, such as the server sending the message to all, will be sending a termination message to the client. So is the four wave.
Why up a client sends a confirmation request to enter TIME_WAIT to wait 2MSL
Because the network is not reliable, we have to assume that the ACK transmission may be lost. If the server does not receive ACK packet, it will continue to send FIN messages to the client. If the client received FIN again, it shows ACK packet is lost. 2MSL is waiting to confirm whether the client actually received the message. MSL is a message sent from the client to the server time, waiting for 2MSL is just a back and forth.
How TCP to ensure reliable transmission
flow control
Difference between TCP and UDP
- Connection-oriented TCP, UDP connectionless
- TCP reliable data transmission, UDP is not reliable data transmission
- TCP slow data transmission, UDP fast speed
- TCP overhead large (20-byte header), small UDP overhead (header of 8 bytes)
- Suitable for transmitting small amounts of data TCP, UDP for transmission of large amounts of data
- TCP guarantees the sequential transmission, UDP does not guarantee
- TCP security slightly lower, UDP safe Some
- TCP congestion control, UDP no congestion control
- TCP connection can only point to point, UDP support one to one, one to many, many-to-many communication and interaction
HTTP 和 HTTPS
HTTP
Hypertext transfer protocol, application layer protocol, based on TCP / IP
- Stateless: No state storage to customers
- No connection: Each request needs to establish a TCP connection
- Initiated by the client request, the server response
- Simple, fast
- Using plaintext communication integrity, the request and response will not confirm the communicating party, the data can not be protected
HTTP status code
- 1xx: means that the server has received the client request, the client may continue to send the request
- 2xx: means that the server request has been successfully received and processed
- 200 OK: success represents a client request
- 3xx: Redirection means that the server requires the client
- 4xx: represent the client's request illegal content
- 400 Bad Request: Request that the client has a syntax error, it can not be understood by the server
- 401 Unauthonzed: indicates unauthorized request, the status code must be used with the WWW-Authenticate header field
- 403 Forbidden: indicates that the server receives the request, but is refusing to provide services, usually gives reasons for not providing services in the response body
- 404 Not Found: The requested resource does not exist, for example, have entered the wrong URL
- 5xx: indicates that the server could not handle the client's request normal and unexpected error
- 500 Internal Server Error: Indicates that the server unexpected error occurred, making it impossible to complete the client's request
- 503 Service Unavailable: Indicates that the server is not currently able to handle the client's request, after a period of time, the server may return to normal
HTTPS
Based on the HTTP protocol to provide encrypted data through SSL or TLS, verify each other's identity and data integrity protection.
- Content encryption: hybrid encryption technology, among those who can not view the plain text content directly
- Authenticate: accessed through a client certificate authentication is own server
- Data integrity protection: preventing transmission of content are tampered with or posing as an intermediary
SSL
- SSL (Secure Socket Layer Secure Sockets Layer) is encrypted based on a protocol layer below the HTTPS.
- At first because HTTP is used when data is transmitted in clear text (on the report when the body can not see Although the data submitted by the POST, but still can steal through packet capture tool) is not safe, in order to solve the hidden dangers Netscape introduced SSL secure sockets layer.
- SSL is a protocol layer below HTTP based on the TCP.
- HTTPS launch has been welcomed by many people in the SSL updated to 3.0, IETF has standardized on SSL3.0, and added a few mechanisms (SSL3.0 but almost no difference), it was renamed after the IETF standardization TLS1. 0 (Transport Layer security Transport Layer security), we can say TLS new version is the SSL 3.1
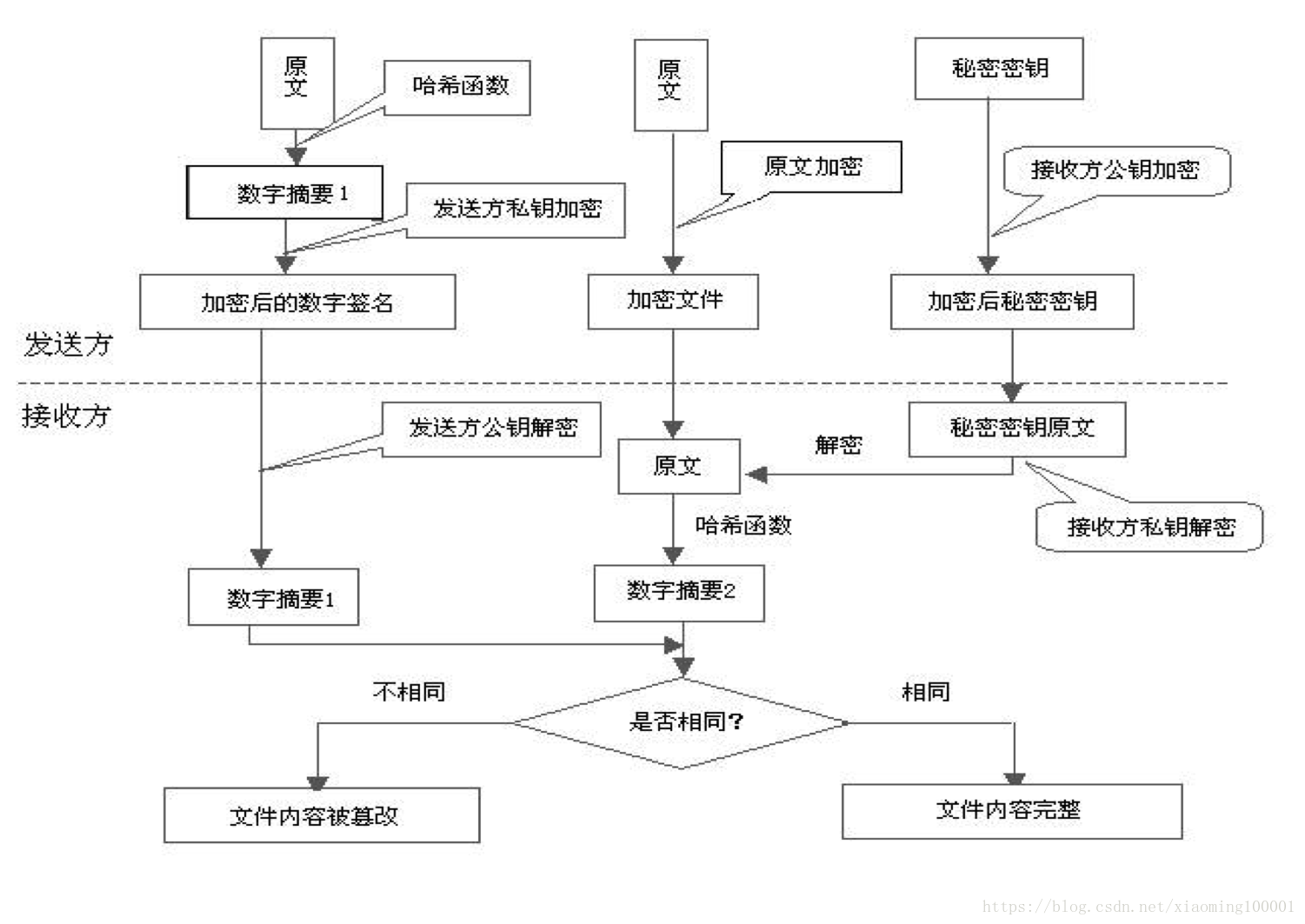
Encryption
-
Hybrid Encryption : binding asymmetric encryption and symmetric encryption techniques. After the client generates a symmetric encryption key to encrypt data, and then using the public key of an asymmetric encryption of the secret key and then encrypted, the data is transmitted over the network the secret key encrypted ciphertext encrypted with the public and the secret key, so even if intercepted by hackers, because there is no private key to encrypt the plaintext can not get the keys, you can not get to the plaintext data.
-
Abstract numbers : one-way hash function is performed by the original hash, the need to encrypt plaintext "summary" into a string of fixed length (e.g. 128bit) ciphertext, different plaintext into ciphertext summary of the results which are not always the same, the same the summary must be consistent with its plain text, and even if they know can not digest the introduction of anti-plaintext.
-
Digital signature technology : digital signatures based on public key encryption scheme based on public key encryption technology is another type of application. It is a public key cryptography and digital digest combine to form a practical digital signature technology.
Get and Post differences
- GET parameters passed via the URL (only with URL encoding parameters are thus directly exposed to the URL, it is not safe), POST request body placed in
- TCP sends a GET request, POST request sends two TCP (there are exceptions: Firefox sent once)
- GET request parameters will be stored in the historical data in, POST will not
- GET request URL has a length limit (associated with the browser), POST no
DNS
DNS translates domain names into IP addresses.
MAC address, IP address,
- Each host at the factory has a unique MAC address, the assigned IP address is a network topology, the routing scheme is ensured based on the underlying network topology in which the position, rather than the equipment manufacturer
- More convenient to use the IP address of the data transmission. Move data packets between these nodes are responsible for ARP protocol maps IP addresses to MAC addresses up to complete.
TCP congestion control and flow control
- Congestion control: in the network routing and link transmission the speed limit, to avoid network overload; comprises four processes: slow start, congestion avoidance, fast retransmission and fast recovery
- Flow Control: between points and points / sender and recipient for speed matching, because the application does not necessarily read speed of the receiver is very rapid, and the limited cache, it is necessary to avoid sending too fast; related art: TCP sliding window protocol needle rollback N
TCP sliding window flow control and congestion window
-
The recipient does not receive the sender sends back ACK, it can not slide to the right. Assuming that send to the recipient made ABCD to slide, as long as the other party did not receive the A, it can not slide, then both of sync situation occurs.
-
Sliding window to improve channel utilization, TCP segments are transmitted in units of packets, each made if one would have to wait the ACK packet, then for large data packets, waiting time is too long. As long as the message transmitted in a sliding window which, without waiting for each ACK can slide back to the right. In the present embodiment, the receiving terminal starts empty AB, only the CD, can not slide at this time; after receiving the EF and H, two right sliding directly, without having to wait G in place.
-
Window size can not be greater than one half the size of the sequence number space. The purpose is to prevent two overlapping window, such as the total size of 7, the window size are 4, the receiving window should slide 4, but only 3 number, resulting in two overlapping windows.
-
There is a case of no-show: ABCD sender sent, then the receiver can receive the slide to the right, but the full reply ACK packet lost. The sender does not receive any of the ACK, the retransmission timeout will ABCD, this time by the recipient to confirm the cumulative principle, only after receiving the retransmitted ACK D ABCD, and slides to the right after the sender receives
Sliding window is received and the synchronization control data range, the range of the transmission end notification data received at present, for flow control, receiving end. Congestion window is a transmission rate is controlled to avoid excessive hair, sender uses. Because tcp is full duplex, so that on both sides of the sliding window.
Maintains two independent windows, sliding window feedback mainly by the recipient buffer to maintain the situation, the congestion window main network congestion degree is detected by the algorithm congestion control sender determined.
Socket
Socket application layer and the intermediate software TCP / IP protocol suite to communicate abstraction layer, which is a set of interfaces. In design mode, Socket is actually a facade pattern, it is the complexity of TCP / IP protocol suite is hidden behind the Socket interface for users, a simple interface is all set, let Socket to organize data in order to comply with the specified protocol