Zero. Hash table
The hash table is a hash function set H (key) and the conflict method maps a set of keywords to a limited address range, and as a keyword in the address interval is stored as records in a table position, which is called a hash table or hash table, the resulting memory location called a hash or a hash address address
.Hash algorithm for constructing a need to think about
1. How to construct cut less conflict?
2. Post-conflict, how do we solve?
Two .hash algorithm constructor
1. Direct addressing method: a case for continuous

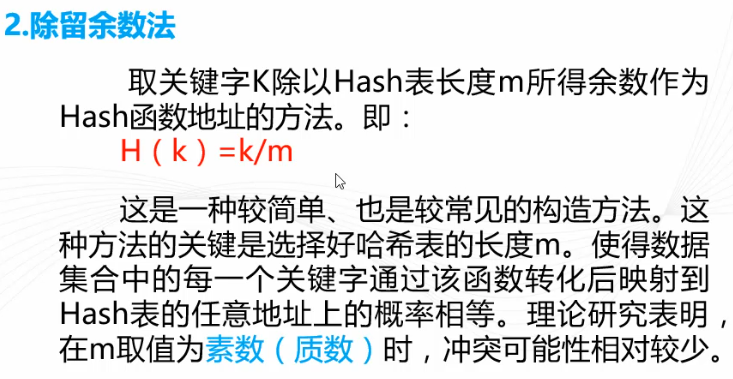
2. In addition to specimens Conormal

3. square excess number method

4. Folding Method

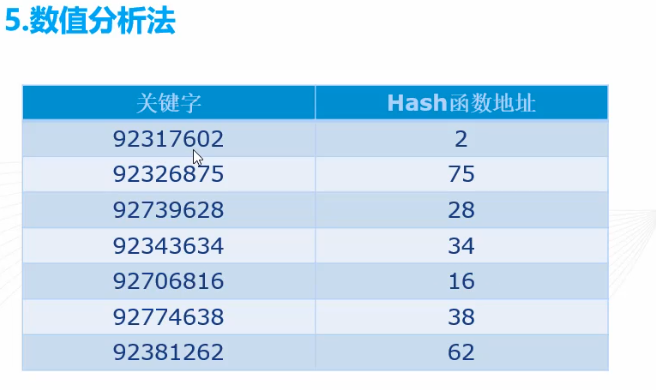
5. Numerical Analysis

III. How to deal with conflict
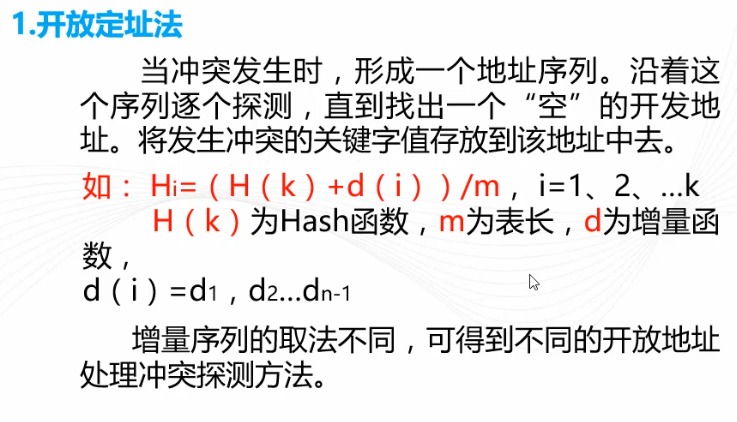
1. Open-addressable
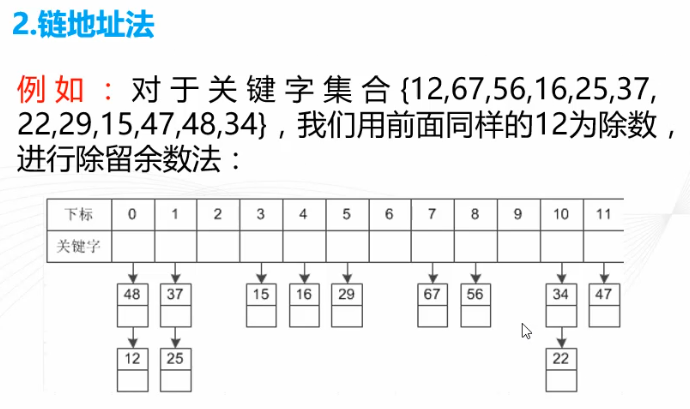
2. The chain address law
IV. A typical hash algorithm
md5
sha-1
digital signature