I. Introduction
In early 19, online discloses two Thinkphp5 of RCE vulnerability, the vulnerability is very easy to use, leading many attacker network scanning with the scanner. We consistently observed attack traffic extensive use of these loopholes batch getshell by ips equipment, this paper from the perspective of a brief analysis of the flow and use of thinkphp full network scanning attacks and getshell traffic signs.
Two, Thinkphp RCE vulnerability scanning and flow
2.1 Principle vulnerability review
2.1.15.0.x version loophole
Thinkphp key principle that is handling requests Request (thinkphp / library / think / Request.php), the class may be achieved in some settings of the HTTP request
Support Thinkphp Configuration "disguised form variable", the default value of the variable _method, so method (), you can override any class implementation calls the function performed by the variable "variable disguised form", and as a function of $ _POST the parameter. May be configured to achieve coverage request Request class attribute values, for example, covering properties filter (filter function for a global property contains filtering), thereby achieving code execution.
2.1.25.1.x-5.2.x version loophole
Version 5.0.x and similar vulnerability, the vulnerability points are present in Request (thinkphp / library / think / Request.php) class, wherein:
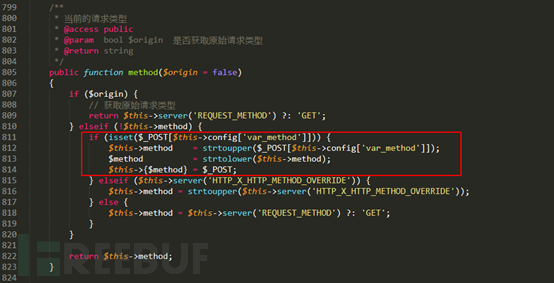 $ Method variables are $ this-> method, which is equivalent to "_method" POST parameter values may be utilized to cover the attribute value of $ filter (filter property contains functions for global filtration), to achieve code execution.
$ Method variables are $ this-> method, which is equivalent to "_method" POST parameter values may be utilized to cover the attribute value of $ filter (filter property contains functions for global filtration), to achieve code execution.
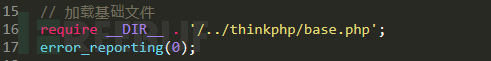
There will be a warning level when the vulnerability is triggered resulting in abnormal program termination, an exception in this case needs to be set to ignore, configure error_reporting in public / index.php (0) ignore the exception to continue running the code, as shown below:
2.2Thinkphp vulnerability scan the whole network
From the traffic point of view, the use of loopholes that send a Thinkphp http package. We found that a hacker scanner is to write a simple sentence as a fingerprint, follow-up and then access the file to see if the return fingerprint information, visit successfully explain shell has been successful, it is to send two basic http package, written under the scanner successful note sites into the shell and url ip with a kitchen knife and then manually connecting, subsequent operations.
From IPS manual verification and logging equipment, comprising the step of attackers Step 2: 1, exp transmission network scanning, whether getshell The fingerprint recognition; 2, chopper connected for remote control;
2.2.1 Network Scanning Send exp
Usually scan log segment B or C are traversing period, and time intensive, a scanner segment is recorded as log,
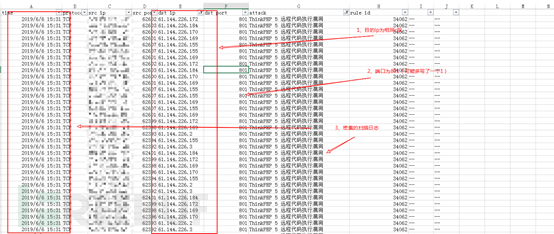 It includes three features: 1, or for the purpose of segment B ip same C section, 2, relatively fixed port, very dense scanning time 3
It includes three features: 1, or for the purpose of segment B ip same C section, 2, relatively fixed port, very dense scanning time 3
Send confirmation shell scanner has been successfully written to the message, using a dedicated fingerprint scanner, so ips is no such detection rules.
2.2.2 chopper connection
When connecting compromised site attacker manual chopper, it will be detected ips, traceable to the context associated with the vulnerability as a breakthrough thinkphp attacker. Select a few typical cases was recorded:
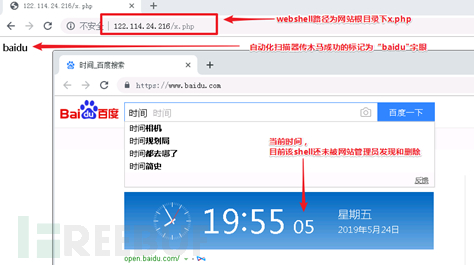
Zhengzhou compromised server 1 (122.114.24.216):
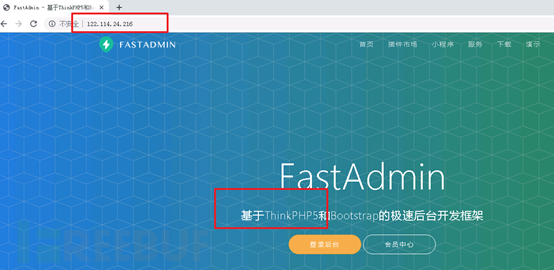 The site really is thinkphp5 hair open, then webshell Trojan still on the server is not deleted. Hackers can access the server by uploading the Trojans, fingerprint information is baidu, with the fingerprint scanner to automatically determine and record the success getshell url.
The site really is thinkphp5 hair open, then webshell Trojan still on the server is not deleted. Hackers can access the server by uploading the Trojans, fingerprint information is baidu, with the fingerprint scanner to automatically determine and record the success getshell url.
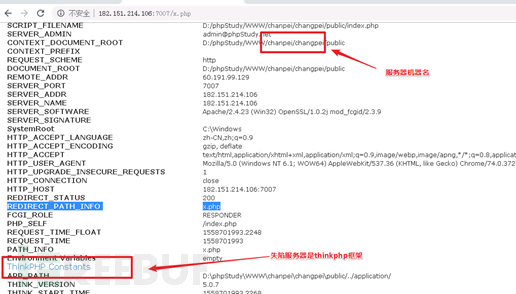
 Sichuan compromised server (182.151.214.106):
Sichuan compromised server (182.151.214.106):
Sichuan compromised server (182.151.214.106):
This case is cleared, although the Trojans, but can still communicate with the server when the server is thinkphp framework, users suspected chanpei
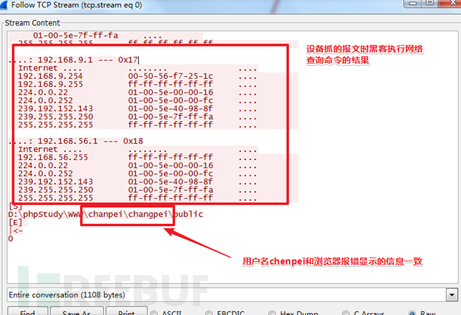
 Equipment recorded the message when the hacker network connection Trojans and execute the query command, the information obtained is consistent with the above error message. And also see which server to a machine within the network, the network comprising at least a screenshot see 192.168.9.0 and 192.168.56.0 two subnets, as shown below:
Equipment recorded the message when the hacker network connection Trojans and execute the query command, the information obtained is consistent with the above error message. And also see which server to a machine within the network, the network comprising at least a screenshot see 192.168.9.0 and 192.168.56.0 two subnets, as shown below:
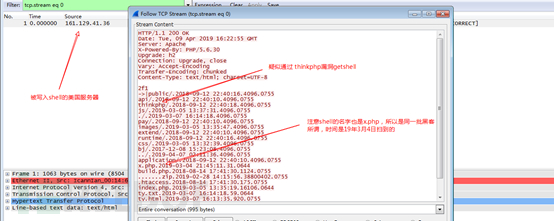
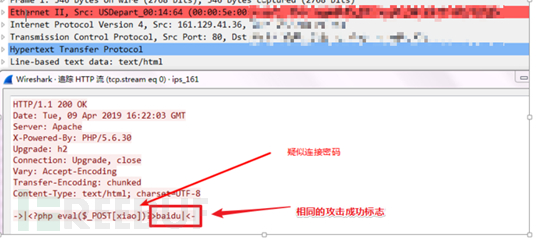
 American compromised server (161.129.41.36):
American compromised server (161.129.41.36):
US webshell on this server were cleared out by the device packet capture and found that hackers use the same webshell Trojan that x.php, suspected to be the same group of hackers.
 When hackers x.php (webshell) file content on US server browser, the device records the x.php password for xiao, and the flag is baidu.
When hackers x.php (webshell) file content on US server browser, the device records the x.php password for xiao, and the flag is baidu.
 It can be seen using the two high-risk Thinkphp RCE vulnerabilities, it was swept into a large number of server vulnerability.
It can be seen using the two high-risk Thinkphp RCE vulnerabilities, it was swept into a large number of server vulnerability.
Third, the summary
In this paper, the principle Thinkphp history of vulnerability, found that the use of shared vulnerability Thinkphp success stories. Currently the device detects a maximum daily log is weblogic, struts2, thinkphp such direct getshell log or log brute force ssh rdp. Many attackers Once you find the latest exp equipment to their network scanner while sweeping above all, the day is probably several shell. Therefore, after the emergence of high-risk vulnerabilities patched in time we recommend that users, configure the security device policy, from a practical point of view a few cases, the scanner has been at risk. If you can configure the website ban ip direct access, can ease the threat to some extent. As limited, welcome to point out errors in the text and exchange advice
References: