In the previous article we network penetration within the artifact frp-- implement telecommuting from home _mac, rdp, windows_ Huangteng Xiao's blog -CSDN blog describes how to use the tcp frp mode, exposure to internal network devices in the public network tcp service. Also based on this technology enables Remote Desktop Services internal network access devices. Today we analyze the existing problems in this way, and solutions can reference.
Frp problem of TCP mode
Here there are two main problems.
The first is safety:
Imagine, frp tcp mode of your device directly exposed to the equivalent of a tcp port to the public network. Any device can try to connect this port. Here it will be a great security risk.
The second problem is a network problem:
All my requests need to be frp server for transit, there is bound to cause relatively large network delays. (Especially in most of our vps are deployed abroad) which will result in a greater impact on our service response speed.
Address security issues (stcp) mode
For security, frp idea is, since these services are likely to be the bad guys attack, and that as long as we restrict certain devices to use this port just fine.
So the question is, how do I know which devices are allowed to use it?
Server configuration? He fell into a problem within the network penetration.
The easiest way is to use key authentication. This is the idea of frp Secret TCP (stcp) mode.
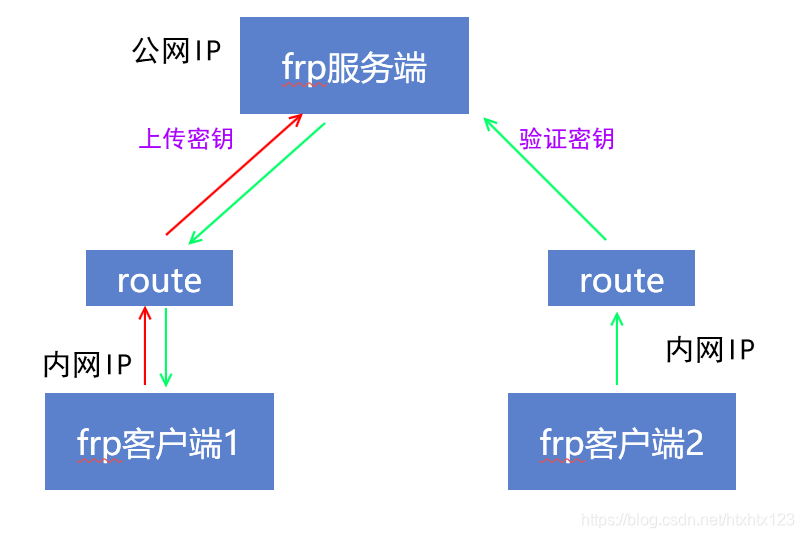
As shown below, frp client 1 needs to be exposed a tcp port. So he at the time of registration to the server, an additional pass a key.
All other devices desire to access this port, you must first verify the key.
As a result, we need to also configure a client on the device frp request initiated by the client initiates a request with the key.
How to configure
- Server: the default configuration is still with the same configuration can be run directly
- Client 1: Configuration type need to stcp, and add a field sk. There is no need distal port, because it is not disclosed
# frpc.ini
[common]
# 你的frp服务器的公网ip
server_addr = x.x.x.x
# 你的frp服务器的默认端口
server_port = 7000
[rdp]
type = stcp
# 只有 sk 一致的用户才能访问到此服务
sk = abcdefg
local_ip = 127.0.0.1
# 远程桌面的本地端口号
local_port = 3389
- Client 2:
# frpc.ini
[common]
# 你的frp服务器的公网ip
server_addr = x.x.x.x
# 你的frp服务器的默认端口
server_port = 7000
[rdp_visitor]
type = stcp
# stcp 的访问者
role = visitor
# 要访问的 stcp 代理的名字
server_name = rdp
# 只有 sk 一致的用户才能访问到此服务
sk = abcdefg
# 绑定本地端口用于访问 远程桌面 服务
bind_addr = 127.0.0.1
bind_port = 6000
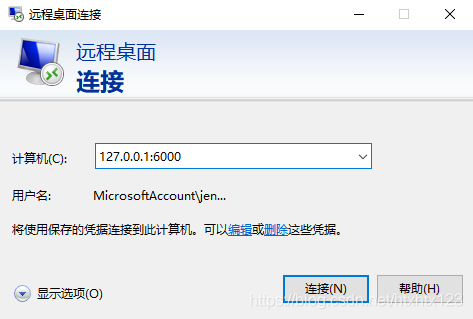
At this point, you are in the client 2, using a remote client to access the service 127.0.0.1:6000 1.
Solve network problems (xtcp) mode
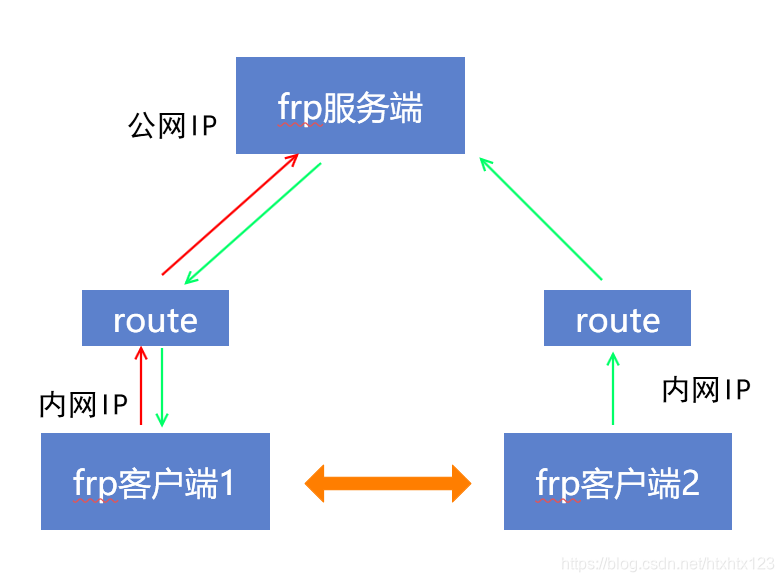
Think about our frp servers main purpose is to solve the case of the two devices recognize each other. In the official running time, actually you do not need the server to do something.
frp客户端就好比两个相亲的对象,frp服务端是媒婆。媒婆介绍完之后,就应该有相亲对象自己聊天了。
这个就是点对点模式(p2p)。在frp中,这个可以通过设置xtcp实现。
如何配置
- 服务端:配置需要增加一个udp端口 7001,增加完之后就是如下
# frps.ini
[common]
bind_port = 7000
bind_udp_port = 7001
- 客户端1:配置需要将type改为xtcp即可
# frpc.ini
[common]
# 你的frp服务器的公网ip
server_addr = x.x.x.x
# 你的frp服务器的默认端口
server_port = 7000
[rdp]
type = xtcp
# 只有 sk 一致的用户才能访问到此服务
sk = abcdefg
local_ip = 127.0.0.1
# 远程桌面的本地端口号
local_port = 3389
- 客户端2:配置需要将type改为xtcp即可
# frpc.ini
[common]
# 你的frp服务器的公网ip
server_addr = x.x.x.x
# 你的frp服务器的默认端口
server_port = 7000
[rdp_visitor]
type = xtcp
# stcp 的访问者
role = visitor
# 要访问的 stcp 代理的名字
server_name = rdp
# 只有 sk 一致的用户才能访问到此服务
sk = abcdefg
# 绑定本地端口用于访问 远程桌面 服务
bind_addr = 127.0.0.1
bind_port = 6000
此时,你在客户端2,使用同样的方式,以127.0.0.1:6000即可访问客户端1的远程服务。
不过需要注意的是,目前frp的p2p服务还不完善,很多nat设备还是不能够穿透的。
此时大家还是需要切换回stcp来使用。
参考文档:
- 2020-1-7-如何使用mac电脑连接你的windows设备 - huangtengxiao
- frp/README_zh.md at master · fatedier/frp
- 2020-1-10-内网穿透神器frp - huangtengxiao
- fatedier/frp: A fast reverse proxy to help you expose a local server behind a NAT or firewall to the internet.
- 内网穿透神器frp——实现在家远程办公_mac,rdp,windows_黄腾霄的博客-CSDN博客
本文会经常更新,请阅读个人博客原文: https://xinyuehtx.github.io/ ,以避免陈旧错误知识的误导,同时有更好的阅读体验。
 This work is Creative Commons Attribution - NonCommercial - ShareAlike 4.0 International License Agreement for licensing. Welcome to reprint, use, repost, but be sure to keep the article signed by Huang Tengxiao (containing links: https://xinyuehtx.github.io/ ), shall not be used for commercial purposes, be sure to publish the same work based on the paper license modification. If you have any questions, please contact me .
This work is Creative Commons Attribution - NonCommercial - ShareAlike 4.0 International License Agreement for licensing. Welcome to reprint, use, repost, but be sure to keep the article signed by Huang Tengxiao (containing links: https://xinyuehtx.github.io/ ), shall not be used for commercial purposes, be sure to publish the same work based on the paper license modification. If you have any questions, please contact me .
