First, what is XSS? How did it happen?
XSS (Cross site scripting) called the cross-site scripting attacks , it is the most common web application vulnerabilities. Attacker embedded in web pages client-side scripting (eg Javascript), when a user browses this page, the script will be executed on the user's browser, so as to achieve the purpose of the attacker. For example, to obtain the user's cookie, navigate to a malicious Web site, carrying the Trojan horse virus.

Second, the classification XXS vulnerabilities
XXS vulnerabilities in different attacks using the technique, there are three types:
Type A, the local use of loopholes: this vulnerability exists in the client page in the script itself. The attack process is as follows:
Alice to Bob to send a maliciously constructed web of the URL.
Bob click and view this URL.
Malicious page Javascript has opened a loophole in the HTML page and install it on Bob computers.
It has loopholes HTML page contains Javascript Bob performed in the local computer.
Alice malicious script that can execute commands under the privileges held by Bob on Bob's computer.
Type B, reflective vulnerability: This vulnerability and the type A somewhat similar, except that the web server using a client-side script to generate the page provides data users, if user data is unverified contained in the HTML page without the entity code, client code will be able to inject into the dynamic page. The attack process is as follows:;
Alice often visit a Web site, this site is owned by Bob. Alice Bob's site is running with user name / password to log and store sensitive information (such as bank account information).
charly found Bob's site contains reflective XSS vulnerabilities ground.
charly write a URL exploit, and pretending to send mail from Alice to Bob's.
After landing in Alice to Bob's site, the browser URL charly provided.
Embedded in the URL of the malicious script in Alice's browser to perform as if it directly from Bob's server is the same.
This script steal sensitive information (authorization, credit cards, account information, etc.), and then sends the information to charly web site in the case of Alice totally unaware of.
Type C, storage-type vulnerabilities: This type is the most widely used and may affect their own web server security vulnerabilities. Hackers will attack the script uploaded to the web server so that all users access the pages are facing the possibility of information leakage, including the administrator of the web server. The attack process is as follows:
Bob has a web site that allows users to publish information / browse the published.
charly noted that Bob's site has the type C XSS vulnerabilities.
charly released a hot message to attract other users have read.
Bob or any other person, such as Alice browse the information that the session cookie or other information will be charly stolen.
Type A direct threat to the individual user, and the object type B and type C are threatened by enterprise-class web applications.
Three, XSS defenses
Principle: do not believe the data entered by the customer
Note: The attack code is not necessarily in the <script> </ script> in
1. important cookie is marked as http only, so in JavaScript document.cookie statement can not get to the cookie
2. We expect only allows users to enter data. For example: textbox age, only allows the user to enter numbers, and characters other than numbers are filtered out.
3. The data processing HTML encode
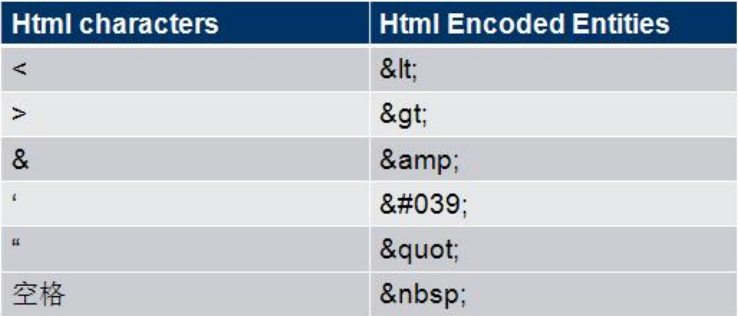
4. Filter or remove special HTML tags, for example: <script>, <iframe>, & lt; for <, & gt; for>, & quot for
5. Filter JavaScript event tag, e.g. "onclick =", "onfocus" and the like.
Fourth, the test XSS vulnerability
方法一:查看代码,查找关键的变量,客户端将数据传送给web服务器。一般通过三种方式Querystring,From表单,以及cookie。例如在ASP的程序中,通过request对象获取客户端的变量。
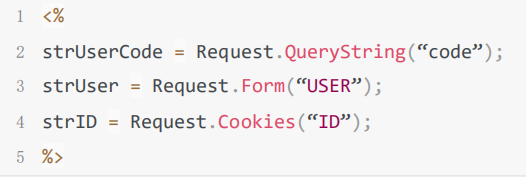
假如变量没有经过HTMLEncode处理,那么这个变量就存在一个XSS漏洞。
方法二:准备测试脚本
在网页中的textbox或其他能输入数据的地方,输入这些测试脚本,看能不能弹出对话框,能弹出的话,说明存在XSS漏洞。
在URL中查看有哪些变量通过URL把值传给了web服务器,把这些变量的值退换成我们测试的脚本。然后看我们的脚本是否执行。
方式三:自动化测试XSS漏洞
现在已经有很多XSS扫描工具了。实现XSS自动化测试非常简单,只需要用HttpWebRequest类。把包含XSS测试脚本,发送给web服务器,然后查看HttpWebResponse中,我们的XSS测试脚本是否已经注入进去了。