Monitor file changes in Linux, to prevent the system being black
https://os.51cto.com/art/201912/608702.htm
another day to try
inotify
Operation and maintenance server troublesome problem is that the system is black, reduced chicken or mining machine. In addition to strengthening security baseline configuration, enhance network and port reinforcement, systems and applications bug fixes, other than the IDS / IPS (intrusion detection / prevention system), and the other aspect is the monitoring system, a complete and accurate security monitoring in a timely manner can host level detect intrusion activity, be alert to prepare for timely processing.
- Author: Security Bugs Source: Today's headlines | 2019-12-31 14:00
Operation and maintenance server troublesome problem is that the system is black, reduced chicken or mining machine. In addition to strengthening security baseline configuration, enhance network and port reinforcement, systems and applications bug fixes, other than the IDS / IPS (intrusion detection / prevention system), and the other aspect is the monitoring system, a complete and accurate security monitoring in a timely manner can host level detect intrusion activity, be alert to prepare for timely processing. This article Bugs gave us for that file system change monitoring.

Outline
In * nix system, everything is a file, change the file system tends to react with changes in the system, such as operating activities update, the system of system applications (can be used to determine the safety audit) or the system was hacked. According Bugs years of experience in system maintenance is one of the most obvious features of the black is change the system files, including but not limited to:
/ Bin (replace basic tools as a malicious Trojan horse, such as netstat, ps, etc.)
/ Sbin (replace basic tools as a malicious Trojan horse, such as sshd, lsof, ss, etc.)
/ Usr / bin (replace basic tools as a malicious Trojan horse, such as sshd, lsof, ss, etc.)
/ Usr / sbin (replace basic tools as a malicious Trojan horse, such as sshd, lsof, ss, etc.)
/etc/init.d (modifying startup tasks, add malicious script boot)
/etc/
/etc/cront.d (modify scheduled tasks, add malicious script timed execution)
/ Etc / crontab (modify scheduled tasks, add malicious script timed execution)
~ / .Ssh / directory (public injection)
/ Etc / sysconfig (iptables modified configuration, etc., open network limitations)
/ Etc / ssh / (ssh configuration modification)
web directory (Edit site)
Etc directory files are replaced or added files illegally.
Strengthen the monitoring of these directories and files, it can prevent the system from being black, and the system is black, but can not find the problem to some extent.
find -mtime directory file changes
The easiest and most common way to monitor system changes is to use the find command, had recently expressed its -mtime file changes.
For example, to see the changes through the day / usr / bin directory files can be used
- find /usr/bin -m -1
For more detailed information look at these files, you can use xargs or -exec these changes files are displayed with ls -al, such as:
- find /var -type f -mtime -1 -exec ls -al {} \;
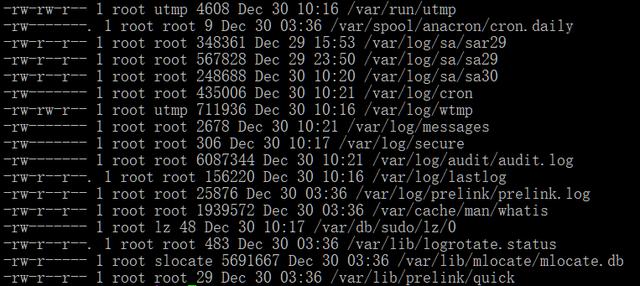
RPM monitoring changes in system files
Linux RPM is an application package, you may use RPM to install the application are all familiar with. RPM is actually a system database package, and the package provides authentication, can be used to find the original installation package changes. RPM package file to verify the application of the basic command is rpm -V. For example, the query validation package nginx nginx can use rpm -V:
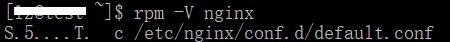
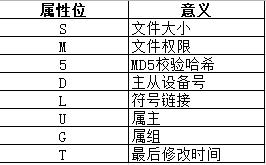
The first few properties to verify that the results of the command. Indicates that the property is normal, there are other signs of change indicates that the property, if the file is deleted, it will prompt "missing ...". Meanings of the following attributes:
The results indicate: nginx package size default.conf files, md5 hashes file modification time has changed.
Note: There is a figure above meditope flag letter c, which represents the standard file attributes, c represents the profile file. There are other signs: d% doc documentation; g% ghost document should not be included, there may be a problem; l% license authorization file; r% readme readme documentation.
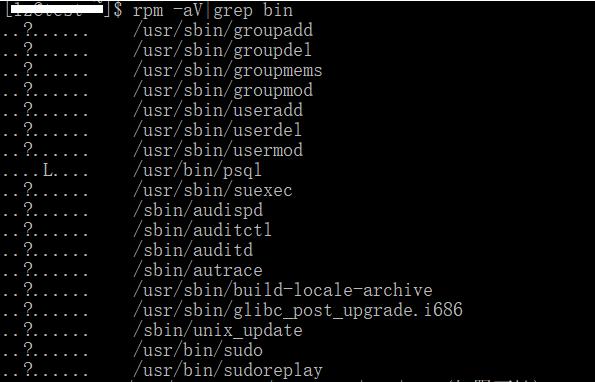
-V选项增加-a就可以列出当前系统中安装后,所有变化过的包文件,可以以此来检查文件包的完整性,安全性等。我们对结果使用grep进一步检查就得到具体的文件,比如要获取bin目录系统文件变化过的文件:
Inotify监控文件变化
另一个比较常用的方法是用Inotify来监控文件变化。Inotify是Linux内核自带(2.6.13)的系统事件监控机制。Inotify优点之一是基于内核事件通知机制,无需定时主动探测文件状态,简单可靠。另一个好处是有文件变化时通知时候,可以记录当时的用户和事件进程。基于Inotify的工具有inotify-tools、sersync和lsyncd等,我们此处简单介绍inotify-tools使用。
inotify-tools安装
安装比较简单,以centos为例,先添加epel源,然后
- yum install inotify-tools
inotify-tools使用
inotify-tools安装后会附带两个工具即inotifywait和inotifywatch。inotifywait工具用来添加文件或目录监控,支持对文件的一些操作事件,比如open、close、delete等,运行后系统处于阻塞状态。inotifywait的参数和对应事件列表如下图所示:
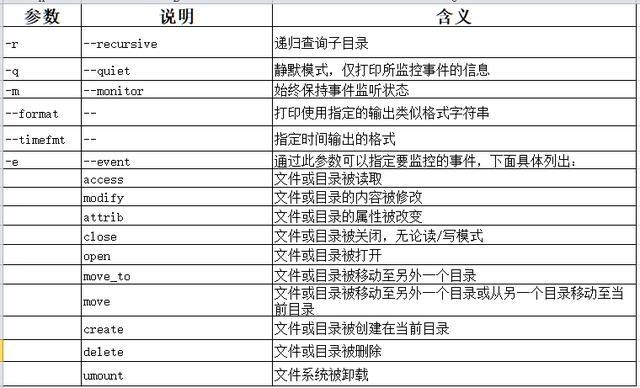
做为安全方面考虑,重点关注文件文件变化和创建时间,即modify和create事件。
inotifywatch工具用来查看所监视的文件发生事件的数据统计。
下面举一个实例来说明,我们用inotifywait来监控/var目录下文件的变化:
- inotifywait -mre modify /var
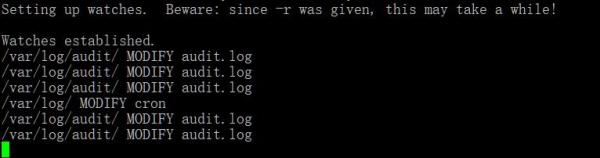
为了便于阅读,我们添加一些日志和时间格式参数:
- inotifywait -mrq --timefmt '%d%m%y %H:%M' --format '%T %w%f' -e modify -e create /var
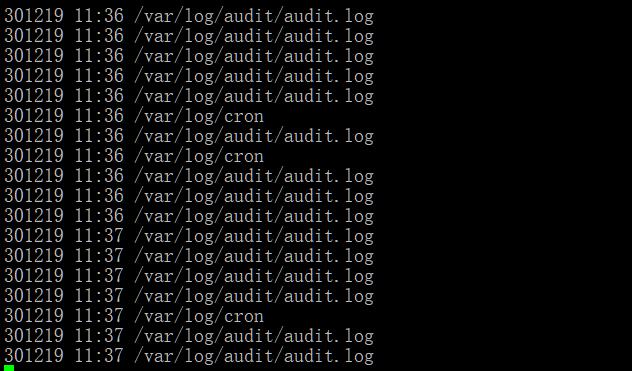
要统计系统内30秒内的变化数据,可以用inotifywatch:
- inotifywatch -v -t 30 -r /proc
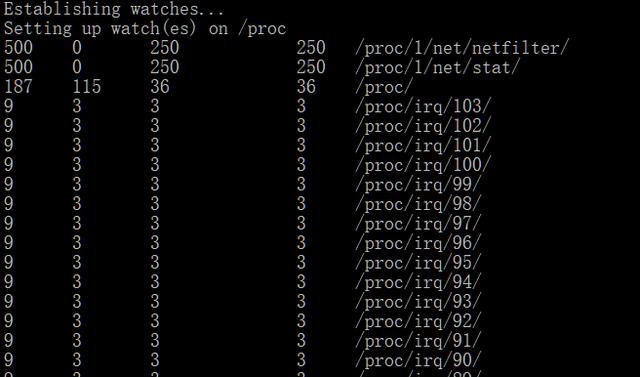
inotifywatch 的使用此处不在详细介绍。
自建编写脚本进行文件Md5监控
还有一个方法就是对特定目录(比如Web目录)开始时候对其计算md5 哈希,以后定时计算md5然后比对,发现md5 哈希不一致了,说明文件已经被篡改了。对此,虫虫之前基于这个原理用Perl写了一个脚本MD5Check(github: /bollwarm/MD5Check),可以直接用来使用或者做参考。
MD5Check安装很简单,有Perl的环境下(依赖Digest::MD5)直接下直接clone文件就可以使用,或者使用cpanm安装
cpanm MD5Check
使用:
使用方法,执行 perl bin/init.pl web目录(自定义),初始化MD5值。
然后使用perl bin/check.pl前一部保存的md5哈希的文件检查。
详细实例,见bin目录下的 init.pl 和 check.pl
cpanm安装后,可以直接用perl单行程序检查使用
初始化:
- perl -MMD5Check -e 'init("/web")' >file
检查:
- perl -MMD5Check -e 'print md5check(file)'
实例:我们举一个wordexpree网站为例子:
- perl init.pl /web >webmd5.20161027
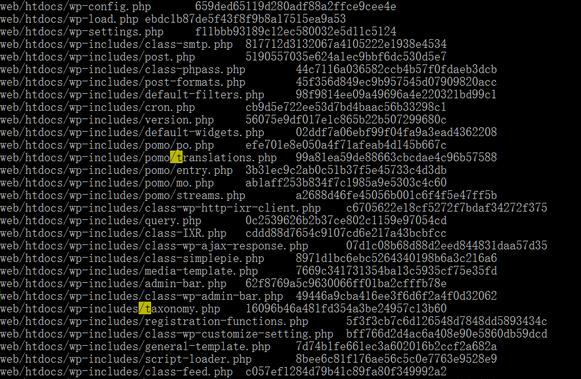
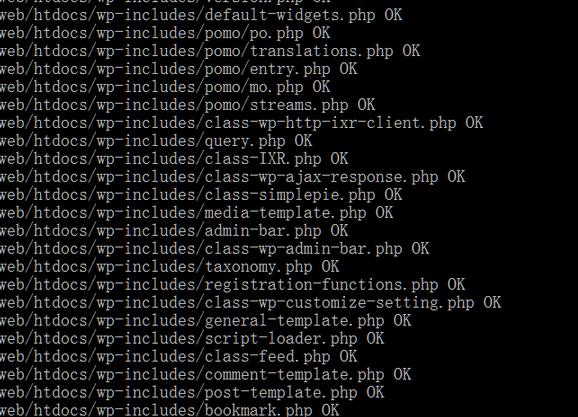
检查:
- perl check.pl webmd5.20161027
总结
In this paper we describe a system to prevent hacked by monitoring changes in the way linux file. find, rpm, Inodify and methods from scripting: describes the method in several common monitoring linux file system monitoring. Of course, these methods need to meet the monitoring system (such as zabbix) in order to achieve timely and comprehensive system that can be used as part of the security monitoring system (including other parts of the process of monitoring, firewall monitoring changes, flow changes) to configure and alarm. About these parts, we have the opportunity to give you about.