2019-2020-1 semester 20,192,415
"Introduction to cyberspace security professionals," the twelfth week learning summary
Chapter X application and learn the history of the password
10.1 The concept and development history
(A) concept
Cryptography consists of two parts:
密码编码学(cryptography):主要研究信息的编码,构建各种安全有效的密码或协议。
密码分析学(cryptanalysis):研究破译密码获得消息,或对消息进行伪造。(B) Development history
The first stage: Ancient → 19 century, classical cryptography password stage of early development
密码算法多采用字符的替代(substitution)和置换(permutation)。The second stage: early 1900s → 1949 years, the development stage of modern cryptography
机械替代手工计算,发明机械密码机、机电密码机,如:ENIGMA转轮机。
但密码算法的安全性仍然取决于对密码算法本身的保密。Phase III: 1949 → 1975 years, the early stages of development of modern cryptography
Shannon发表划时代论文“保密系统的通信理论”Fourth stage: From 1976 until today
Diffie和Hellman发表“密码学的新方向”,提出公钥密码的思想,引发变革,密码学进入公钥密码新时代。
1977,美国制定了数据加密标准,公开密码算法的细节。10.2 cryptographic algorithms
(A) a conventional symmetric cryptographic [password]
The basic features of a symmetric cryptographic algorithm is the same key for encryption and decryption, or relatively easily derived, also known as a single key algorithm.
Symmetric ciphers often divided into two categories:
Block cipher: number (abbreviated number plaintext) sequence of length N is divided into groups (may be viewed as a vector of length N) after the plaintext message encoded representation, respectively, each under the control of a key into the same length digital output (ciphertext abbreviated number) sequence .
Code Example: DES / IDEA / AES / RC5 / MARS / Twofish / CAST-256 and the like.
Stream cipher: using a small number of keys (manufactured arbitrary element) by some complex operations (encryption algorithm) to generate a large number of pseudo-random bit stream for encrypting the plaintext bit stream.
(B) an asymmetric cryptographic public key cryptosystem []
Public-key cryptosystem is based on mathematical functions.
Public-key cryptosystem for both encryption can also be used for digital signatures.
Disadvantages: computational complexity, large resource consumption, resulting in ciphertext becomes long.
(C) Secure Hash password
Hash (the Hash) function is a basic method for message authentication, message integrity, and is mainly used for digital signatures.
Hash function accepts as input a message, called a hash value is generated (also called a hash value, the message digest MD)
output.
h = H(M)
M 变长报文 h 定长的散列值Characteristics of the hash function is applied to data of any length, and can generate a fixed size output.
※ collision hash function? You may get the same hash address for different keywords that k1 ≠ k2 and H (k1) = H (k2 ), a phenomenon known as collision (Collision). Keyword has the same function value of the hash function is known as a synonym.
Solution: https://blog.csdn.net/hotchange/article/details/80159671
10.3 cyberspace security cryptographic applications
Cryptography can solve the following security issues:
(1) Confidentiality Protection: Encryption
(2) Integrity Protection: ※ cyclic redundancy check code https://baike.baidu.com/item/ cyclic redundancy check code / 10168758 fr = aladdin?
(3) identifiability protection: usually through a digital signature
(4) Non-repudiation protection issues: the identity of the authorized persons authorization certificate and the corresponding rights, licenses bundled together
(5) authorization and access control issues
Three common encryption products: basic public facilities (PKI), virtual private network (VPN), Privilege Management Infrastructure
(A) the basis of public facilities (PKI)
Overview: One follows standard, providing technical specifications and security infrastructure platform using public key encryption technology
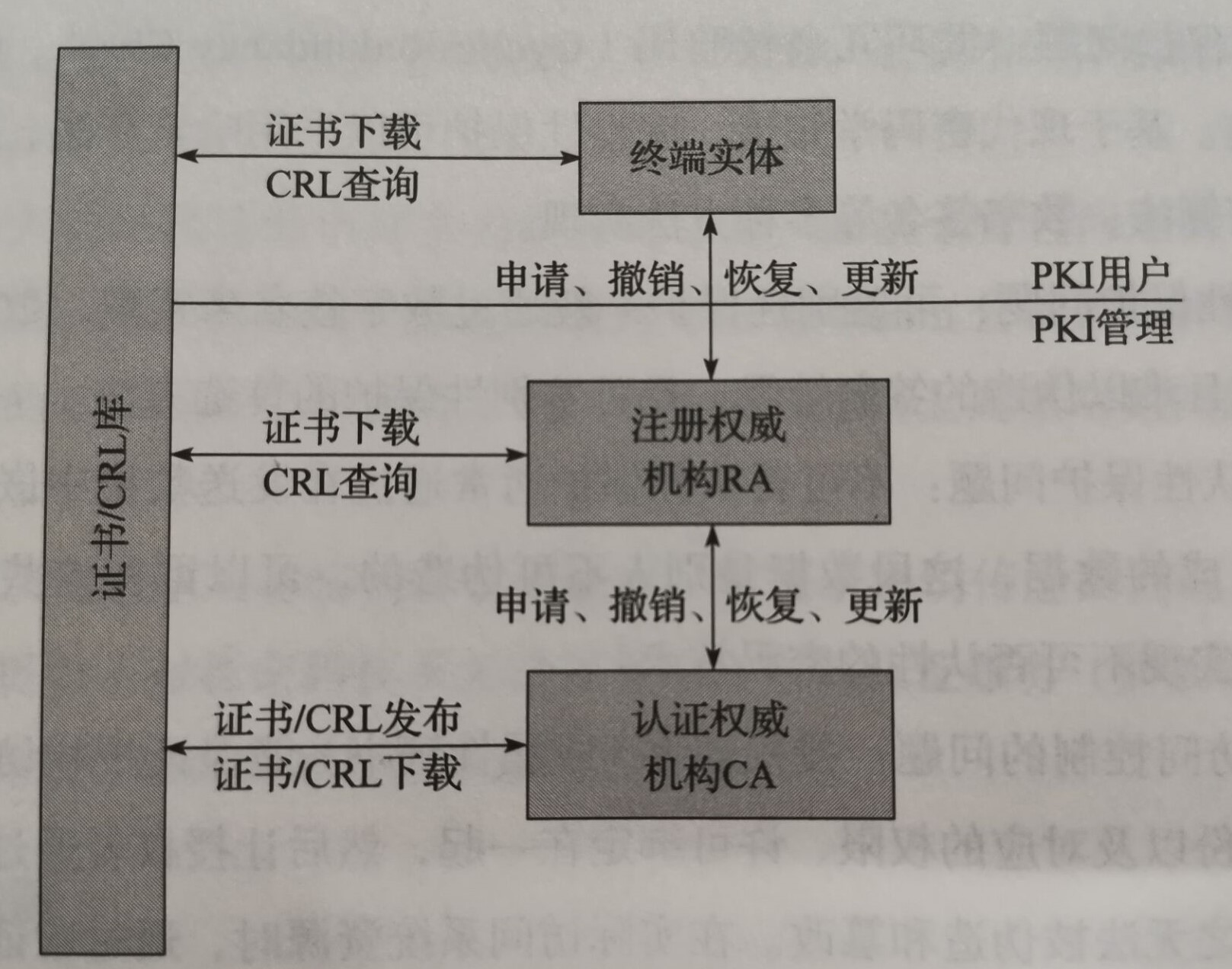
PKI architecture
by CA to the true identity of the user and the user's public key to bind together to produce a digital certificate; digital certificates, users can easily and securely obtain the public key of the other party, offline verify the authenticity of the public key.CA:PKI核心组成部分 主要功能:证书的签发和管理,CRL的签发和管理,RA的设立、审核及管理 RA:CA认证机构的延伸(与CA在逻辑上是一个整体) 主要功能:进行用户身份信息的审核,管理和维护本区域用户的身份安全、数字证书的下载、数字证书的发放和管理、登记黑名单 数字证书:一段经CA签名的、包含拥有者身份信息和公开密钥的数据体,是各实体的身份证明,具有唯一性和权威性。 主要内容:证书体、签名算法、CA签名数据 证书/CRL库:发布、存储数字证书和证书撤销列表,供用户查询、获取其他用户的数字证书为系统CRL所用 终端实体(end entity):拥有公/私钥对和相应公钥证书的最终用户※ end entity can be people, equipment, processes?
PKI interoperability model
trust model describes how to establish a certification path between different certification bodies, as well as to build trust and seek the path of the rule.Common PKI Interoperability Model:
1. 严格层次结构模型——集中式信任模型 A和B必须找到相同的祖先节点(中间根CA或根CA)才可以互相验证 优点:其结构与许多组织或单位的结构相似、容易规划 缺点:不同单位的CA必须在一个共同的根CA下,根CA会导致风险集中 2. 网状信任结构模型——分布式信任模型 每个终端实体都信任其证书签发CA;而CA之间如果信任,则以点对点的方式相互签发证书。 优点:结构灵活、扩展容易,适用动态变化的组织机构 缺点:证书路径的拓展与层次结构比较复杂,选择证书路径比较困难 3. 桥信任结构模型——中心辐射式信任模型 任何结构类型的PKI都可以通过桥CA连接在一起,实现相互信任;每个单独的信任域可通过桥CA扩展到多个CA之间。Application and development of PKI
PKI Application example:
基于PKI技术的IPSec协议已经成为构建VPN的基础 利用PKI,SSL协议支持在浏览器和服务器之间进行加密通信 结合SSL和数字证书,PKI技术可以保证在进行Web交易时多方面的安全需求PKI technology development and changes:
属性证书,漫游证书,无线KPI
(B) virtual private network (VPN)
Virtual Private Network (VPN) usually refers to the public network, establish a temporary, secure network tunnel technology.
虚拟:相对传统的网络专用网络而言 专用/私有:为特点企业或用户所有的,只有经过授权的用户才可以使用- Features: low cost, security, quality of service (different levels), manageability, scalability (easy addition of new network nodes)
Working principle and key technologies, typical application mode
※什么是MAC算法? MAC算法 (Message Authentication Codes) 带秘密密钥的Hash函数:消息的散列值由只有通信双方知道的秘密密钥K来控制。此时Hash值称作MAC。
(三) 特权管理基础设施
概述
能够提供一种独立于应用资源,用户身份及访问权限的对应关系,保证用户能够获取授权信息。
组成
(1)属性证书AC
PMI使用AC表示权限信息,对权限生命周期的管理是通过管理证书的生命周期实现的。 AC是一种轻量级的数据体,不包含公钥信息。(2)属性权威机构AA
AA是PMI的核心服务节点。
AA主要是应用授权的受理,可以有多个层次。
(3)证书库(AC库)
证书库用于发布PMI用户的AC以及AC撤销列表(ACRL),以供查询。
PMI和PKI一起建设时,也可以直接使用PKI的LDAP作为PMI的AC/ACRL库。
应用的结构
PMI建立在PKI提供的可信的身份认证服务的基础上,采用基于属性证书的授权模式,提供用户身份到应用权限的映射。
实际应用中,PMI大多基于PKI来建设,也和PKI一起为应用程序提供安全支撑。
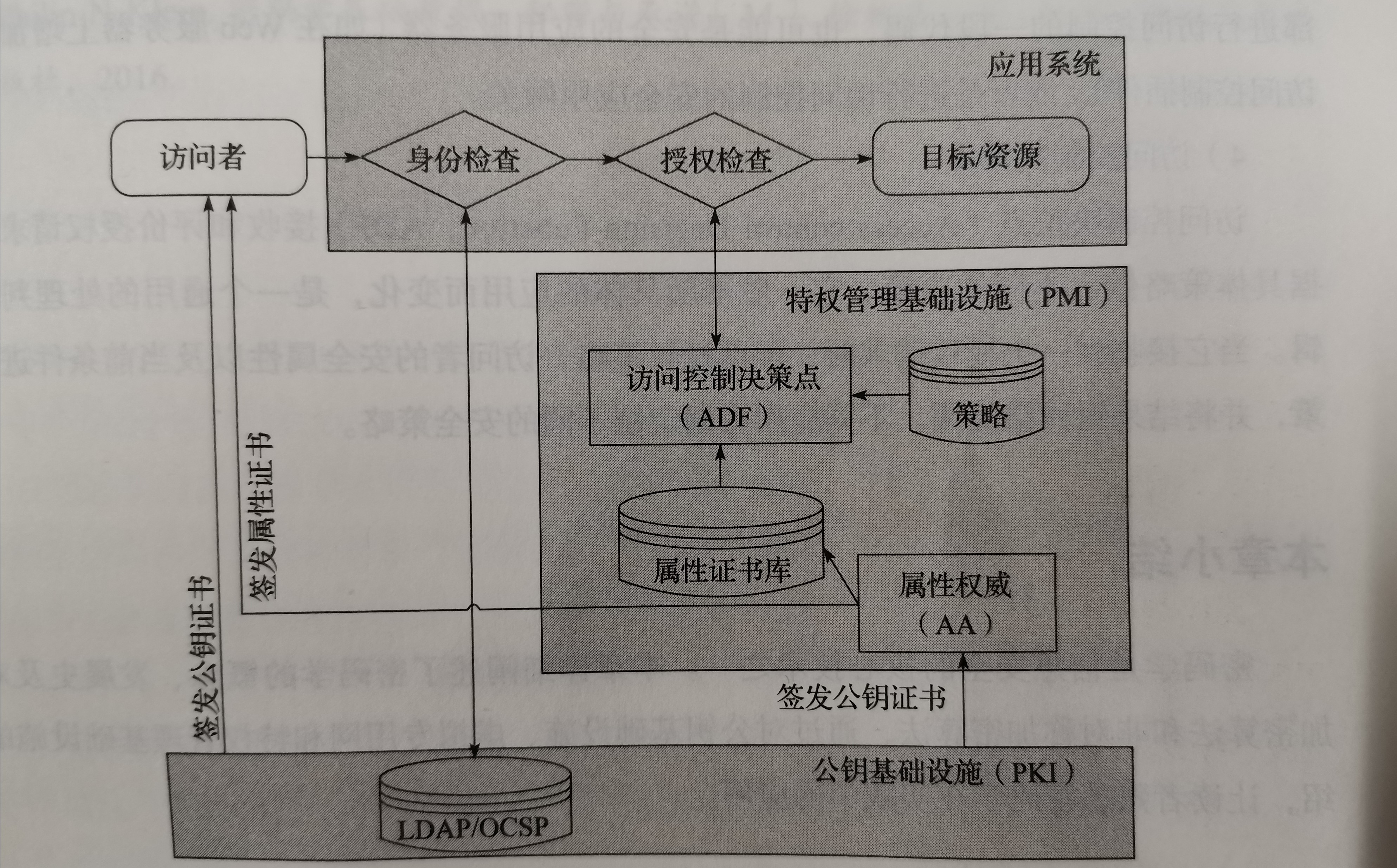
PMI和PKI比较:
主要区别: (1)PMI主要进行授权管理,证明用户有什么权限、能干什么→签证:同一个护照可以有多个国家的签证,能在指定时间进入相应的国家。 (2)PKI主要进行身份鉴别,证明用户身份。→护照:护照是身份证明,可以用来唯一标识个人。 相似之处: (1)为用户数字证书签名的实体被称为CA,签名AC的实体被称为AA。 (2)PKI信任源被称为根CA,PMI的信任源被称为SOA。 (3)CA可以有它们信任的次级CA,次级CA可以代理鉴别和认证,SOA可以授权给次级AA。 (4)如果用户需要废除其签名密钥,则CA将签发CRL.与之类似,如果用户需要废除授权允许(authorization permissions), AA将签发一个AC撒销列表。