1, the basic description
In a production environment using k8s later, most applications have achieved high availability, not only reduces maintenance costs, but also simplifies application deployment costs a lot, but it also brings many problems. For example, developers may want to check their application status, connection information, log, execute commands.
After use K8S, Pod units in business applications, unlike in the previous unit of the server, may be directly related to the operation log in the server. When using k8s business application deployment, k8s official dashboard Although you can view the log, perform basic operations such as command, but as the operation and maintenance personnel, operations, or do not want to see the development of Pod outside the scope of their own, then we should be using RBAC permissions related configuration.
This article mainly on two issues:
- Use Username Password Log in Dashboard
- Permissions of the logged in user configuration, can only achieve their own Namespace operation of Pod, you can not enter into other unauthorized Namespace
2, change the authentication Dashboard
In order to facilitate the development and operation and maintenance personnel to log Dashboard, Dashboard will need to login user name and password authentication (user name and password Token can be turned on at the same time).
Use the deployment of Ratel kubernetes-dashboard of --authentication-mode can be changed to basic, Ratel is not installed kubectl edit can be used to make changes, the changes are complete will automatically restart.
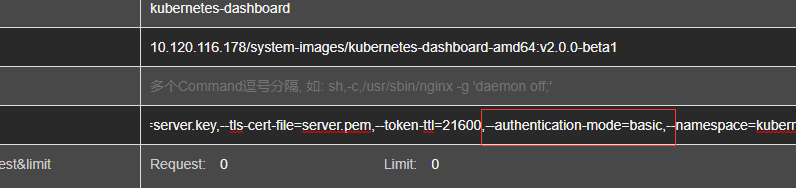
After changing the configuration kube-apiserver add --basic-auth-file = / etc / kubernetes / basic_auth_file
basic_auth_file file storage account password in the following format:
xxx1_2019,xxx1,3,"system:authentication" xxx2_2019,xxx2,4,"system:authentication" xxx3_2019,xxx3,5,"system:authentication" xxx4_2019,xxx4,6,"system:authentication"
Followed by password, user name, ID number, user groups, as the following will be authorized for the logged in user, so the group became the setting system: authentication, demand change.
3, add the default permissions
First configure a system: authentication group allows queries namespace list (because the entry to the specified namespace, you must be able to list namespace of the cluster):
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: annotations: rbac.authorization.kubernetes.io/autoupdate: "true" labels: kubernetes.io/bootstrapping: rbac-defaults rbac.authorization.k8s.io/aggregate-to-edit: "true" name: ratel-namespace-readonly rules: - apiGroups: - "" resources: - namespaces verbs: - get - list - watch - apiGroups: - metrics.k8s.io resources: - pods verbs: - get - list - watch --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: ratel-namespace-readonly roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: ratel-namespace-readonly subjects: - apiGroup: rbac.authorization.k8s.io kind: Group name: system:authentication
Create a view namespace resource permissions
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: ratel-resource-readonly rules: - apiGroups: - "" resources: - configmaps - endpoints - persistentvolumeclaims - pods - replicationcontrollers - replicationcontrollers/scale - serviceaccounts - services verbs: - get - list - watch - apiGroups: - "" resources: - bindings - events - limitranges - namespaces/status - pods/log - pods/status - replicationcontrollers/status - resourcequotas - resourcequotas/status verbs: - get - list - watch - apiGroups: - "" resources: - namespaces verbs: - get - list - watch - apiGroups: - apps resources: - controllerrevisions - daemonsets - deployments - deployments/scale - replicasets - replicasets/scale - statefulsets - statefulsets/scale verbs: - get - list - watch - apiGroups: - autoscaling resources: - horizontalpodautoscalers verbs: - get - list - watch - apiGroups: - batch resources: - cronjobs - jobs verbs: - get - list - watch - apiGroups: - extensions resources: - daemonsets - deployments - deployments/scale - ingresses - networkpolicies - replicasets - replicasets/scale - replicationcontrollers/scale verbs: - get - list - watch - apiGroups: - policy resources: - poddisruptionbudgets verbs: - get - list - watch - apiGroups: - networking.k8s.io resources: - networkpolicies verbs: - get - list - watch - apiGroups: - metrics.k8s.io resources: - pods verbs: - get - list - watch
Creating Pod execute permissions
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: ratel-pod-exec rules: - apiGroups: - "" resources: - pods - pods/log verbs: - get - list - apiGroups: - "" resources: - pods/exec verbs: - create
Creating Pod delete permissions
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: ratel-pod-delete rules: - apiGroups: - "" resources: - pods verbs: - get - list - delete
Authority to bind the corresponding user after the authority is created, corresponding to only need to implement different users achieve different permissions on different namespace.
RBAC unfamiliar to refer https://www.cnblogs.com/dukuan/p/9948063.html
Or reference books Chapter II "no longer step on the pit Kubernetes practical guide."
4, configure permissions
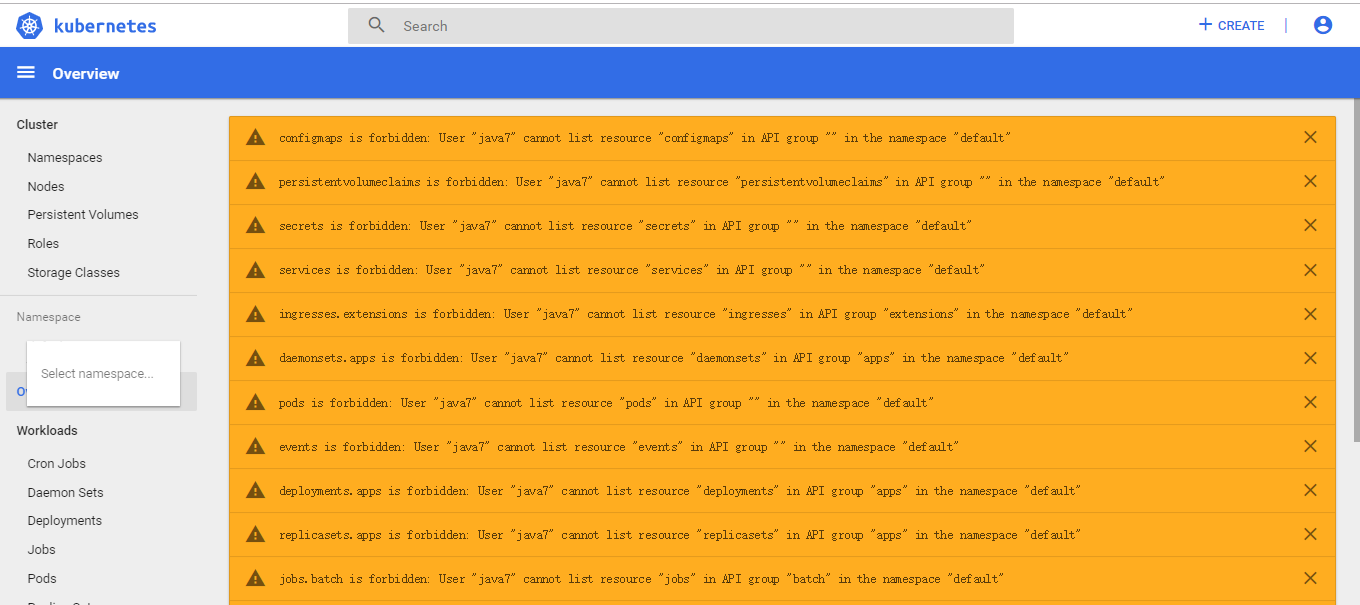
Example: Suppose a user named java7, need access to resources default namespace, you can execute commands and view the log in a container
Before adding permissions can not view any information:
Configure permissions:
Method 1: Use Ratel a key configuration, select the corresponding cluster, Namespace, user name, click Create to check permissions. 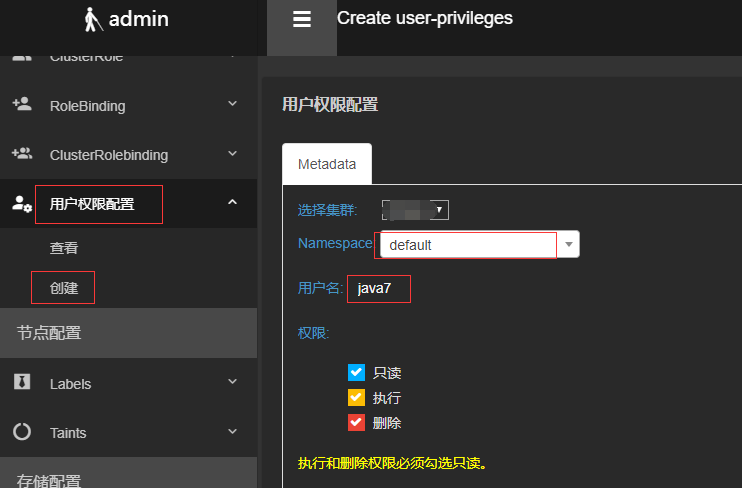

创建成功后再次登录,即可查看该Namespace的信息
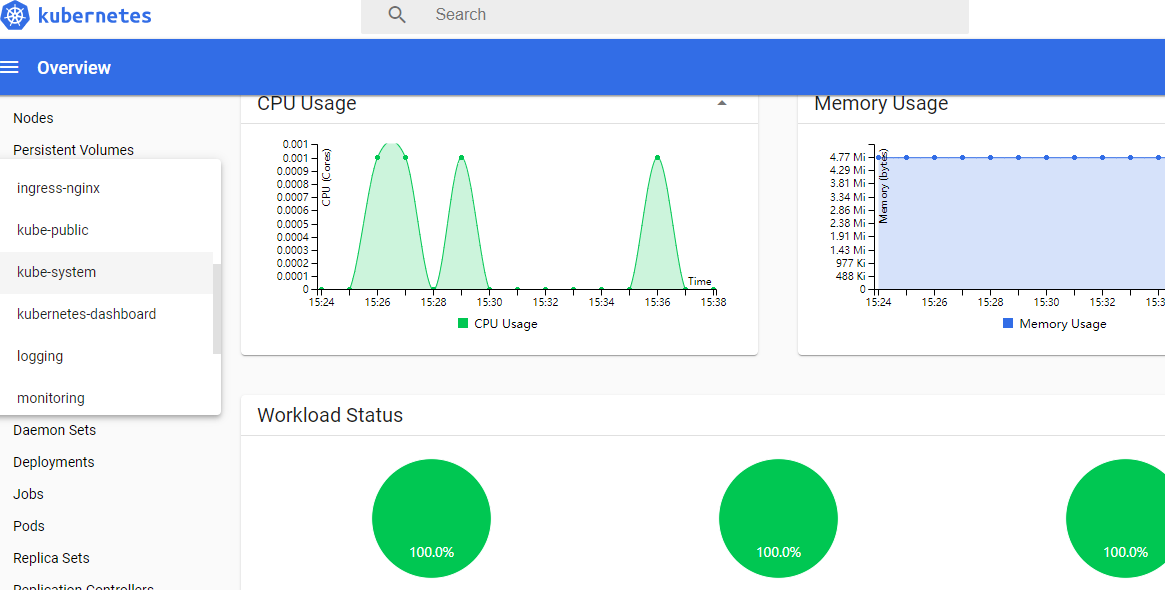
查看日志:
执行命令:

同时也不能查看其他namespace的资源

方式二:使用yaml文件配置
使用Ratel进行权限配置,在配置权限后在对应的namespace下创建对应的RoleBinding,如下:
[root@k8s-master01 ~]# kubectl get rolebinding NAME AGE gitlab 112d ratel-pod-delete-java7 11m ratel-pod-exec-java7 11m ratel-resource-readonly-java7 11m
内容如下:
ource-readonly-java7 -o yaml apiVersion: v1 items: - apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: creationTimestamp: "2019-12-03T07:34:24Z" name: ratel-pod-delete-java7 namespace: default resourceVersion: "35887290" selfLink: /apis/rbac.authorization.k8s.io/v1/namespaces/default/rolebindings/ratel-pod-delete-java7 uid: 547f5d42-159f-11ea-b1b5-001e674e3dd6 roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: ratel-pod-delete subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: java7 - apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: creationTimestamp: "2019-12-03T07:34:24Z" name: ratel-pod-exec-java7 namespace: default resourceVersion: "35887289" selfLink: /apis/rbac.authorization.k8s.io/v1/namespaces/default/rolebindings/ratel-pod-exec-java7 uid: 547c5768-159f-11ea-b1b5-001e674e3dd6 roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: ratel-pod-exec subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: java7 - apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: creationTimestamp: "2019-12-03T07:34:24Z" name: ratel-resource-readonly-java7 namespace: default resourceVersion: "35887288" selfLink: /apis/rbac.authorization.k8s.io/v1/namespaces/default/rolebindings/ratel-resource-readonly-java7 uid: 5476577f-159f-11ea-b1b5-001e674e3dd6 roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: ratel-resource-readonly subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: java7 kind: List metadata: resourceVersion: "" selfLink: ""
在没有安装Ratel的情况下,可以使用上述yaml内容直接创建至对应的namespace下即可完成权限配置。
上述只是实现了对常用资源的权限控制,其他权限控制类似。
Kubernetes多集群资源管理平台Ratel安装可以参考:https://github.com/dotbalo/ratel-doc
