https process
client access https://dududu.com
client requests a public key, server certificate issued to a client, this certificate contains a public key
client to verify the correctness of the certificate to obtain the public key
generate a pseudorandom client session secret key, encrypted with the public, issued server
server with the private key to decrypt the session keys obtained
client / server use the session keys encrypt the content transfer, to your partner. The other party decrypted to get the right content.
problem:
server application for a certificate
Public key to a CA, CA will Zuosha? Back to you what?
Certificate authority issued, the applicant generates a pair of public key and asymmetric encryption algorithms (RSA), then the application information (country, domain name, etc.) need to be sent to a certificate authority (CA) along with the public key.
After confirmation CA configuration generates the digest signature M throughout the application information through a message digest algorithm (MD5, SHA), and M and the signature digest algorithm used by the CA itself private key encrypting
After obtaining client certificate how do
The client returned from the server to get the certificate, obtained by reading the issuing authority server certificate (Issuer)
The client operating system to look up the issuing authority of the certificate, if it is not a root certificate to continue to go on recursively until I got the root certificate .
With the public key of the root certificate to the decryption verification on the certificate layer legality , then let the public key certificate to verify the legitimacy of a layer of an upper layer of the certificate; recursion backtracking.
Finally, server-side validation certificate is trusted in.
Hashing and signing certificate is what is the difference?
What signature thumbprint is?
What is included in the certificate?
View certificate cmd> certmgr.msc
The main certificate information (domain name, expiration date and so forth)
Public website
Hash digest
CA private key signature on the organization of a hash digest
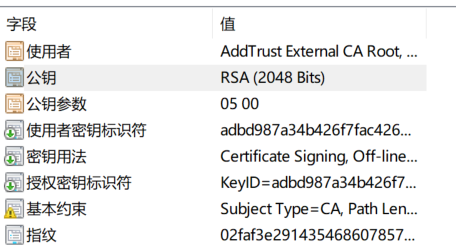
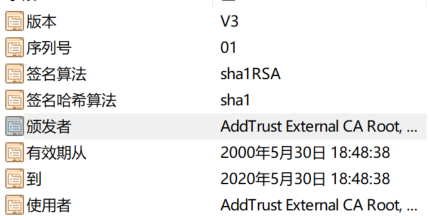
Certificate trust chain
To verify the validity of the certificate, which is the signature verification certificate
We need to use the private key corresponding to the public key to decrypt the signature, and then get the hash value, then they are better than hash value.
Then this private key corresponding to the public key in which, in the browser / computer. The browser will advance deposit certificate number, batch certificate there signature.
Browser only after these trust certificates signed certificate
Pre-installed browser trust certificates, pre-installed certificate trust xx Web site, the browser trust this site xx. This is the chain of trust
What client certificate verification
Whether the validity of the certificate matches the client requests the use of the site, is not in the revocation list CRL inside,
It's on a certificate is valid
appendix:
https://www.cnblogs.com/linianhui/p/security-https-workflow.html