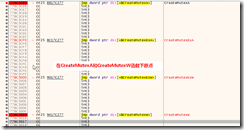
1. First, determine how to open a micro letter put more determined, more anti-Most programs are open to use mutex to complete, so we create from start to start the mutex API (CreateMutexA / CreateMutexW)
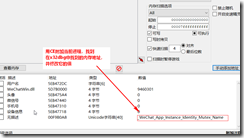
You can see the name mutex created
General procedure to open anti-zhong is the name of the judge to determine whether the same mutex, so we do an experiment to validate our guess is correct
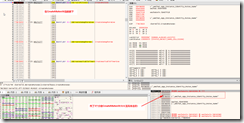
(Using x32dbg directly modify the memory effect is the same)
Run directly modify the value, and then open a micro channel, the following results
Open double the results, that we guess is correct, so the direct use apiHook, Hook CreateMutexW function, modify chau into the third parameter, you can micro-channel anti had lost more open, dll code is as follows
HookAPI void ()
{
// Get CreateMutexW function address
Addr = the GetProcAddress (of LoadLibraryA ( "Kernel32.dll"), "CreateMutexW");
// save the original instruction of
the memcpy (OldOpcode, Addr,. 5);
// calculate partial jumps shift
DWORD Offset = (DWORD) HookCreateMutexA - (DWORD) Addr - 5;// new combination of the Opcode
* (DWORD *) & JmpOpcode [. 1] = Offset;
}
WINAPI HookCreateMutexA HANDLE (
LPSECURITY_ATTRIBUTES lpMutexAttributes,
BOOL bInitialOwner,
LPCSTR lpName
)
{
HANDLE the Handle = 0;
// Create a mutex calls CreateMutexW different names of
the Handle = CreateMutexW (lpMutexAttributes, bInitialOwner, L "bbbbbbbb23333333");
return the Handle;}
EnableHook void (BOOL the Enable = TRUE)
{
DWORD OldProtect = 0;
// change the memory page attributes, read and write
the VirtualProtect (Addr,. 5, PAGE_EXECUTE_READWRITE,, & OldProtect);
// new filling the Opcode
the memcpy (Addr, the Enable JmpOpcode:? OldOpcode , 5);
// attribute tab reduction target address belongs
the VirtualProtect (Addr, 5, OldProtect, & OldProtect);
}